Password Security: Understanding the NIST Password Guidelines
Today, we will be looking into a few key NIST recommendations when it comes to password management.

According to The U.S. Department of Health and Human Services (HHS) Office of Civil Rights (OCR), there was a 264% increase in healthcare ransomware attacks from 2019 to 2024. Before you shrug your shoulders and go on with your day, consider the following. Regardless of the industry, the average cost of a data breach in 2024 was 4.88 million USD.
As a business owner in today’s technologically advanced society, a strong cybersecurity system is key. No matter the industry you work in, keeping your information safe and your password secure is a best practice. Whether you are safeguarding protected health information (PHI) or your personal information, making sure your password strength is high is essential for everyone.

That is why the National Institute of Standards and Technology (NIST) provides technical guidelines for choosing a strong password. As well as overall enhancing cybersecurity and avoiding user error.
Today, we will be looking into a few key NIST recommendations when it comes to password management. These standards and guidelines cover such topics as password complexity and length, password change policies, and how to implement NIST into your organization.
What Are the NIST Password Guidelines?
So what exactly is NIST? Under the Federal Information Security Management Act of 2014, this government organization develops information security and privacy standards. It is a federal agency under the U.S. Department of Commerce that helps promote innovation and industrial competitiveness.
This non-regulatory agency provides security guidelines to help strengthen cybersecurity standards. NIST has established password recommendations that focus on improving security.
While also simplifying password management best practices. They regularly update these Digital Identify Guidelines (DIG), which include topics such as:
- Enrollment and Identity Proofing.
- Authentication and Lifecycle Management.
- Federation and Assertions
- Risk Management and Identity Models
You can find the current NIST password guidelines in the NIST SP 800-63 series of documents. Let's go over some of those now!
Updated NIST Recommendations on Password Security
Over the years, NIST has continuously updated its password security guidelines to better protect federal and public entities from cyberattacks. Changes first introduced in SP 800-63B come from studies and research following previous cyberattacks and password breaches.

Let's take a look at some of these NIST password guidelines that are subject to such updates:
- Password length. The minimum password length for user-selected passwords is 8 characters. However, the recommendation from NIST is that a password should have at least 15 characters.
- Password complexity. The complexity of a password often includes at least one upper and lowercase, numeric, and special character.
- Character sets. All printing characters allowed are the American Standard Code for Information Interchange (ASCII) and UNICODE.
- Forget password “hints” and authentication questions. Questions along the lines of, "What was your first car?" or "What was your childhood best friend's name?" can actually hurt your security efforts. These “knowledge-based authentication” (KBA) methods rely on personal information that is usually easy to guess or find. Giving an open line for experienced hackers to access your information.
- Check for “known bad” passwords. Software refers to a blocklist of common or previously used passwords when creating a new password.
- Throttling. A requirement for compliance, throttling to limit failed authentication attempts is key.
- Password expiration. Passwords do not need updating at defined intervals, however, organizations must force a password change in the case of a known compromise.
- Using SMS for MFA. NIST “discourages” the use of SMS as an out-of-band authenticator. They also don't recommend email and voice-over-internet protocol (VoIP). Instead, they suggest stronger multi-factor authentication (MFA) alternatives. Such as time-based one-time passwords generated by mobile apps, hardware tokens, or biometric verification.
- Help in choosing a password. When it comes to choosing a strong password, guidance is often required. Especially if a user chooses a password off of the blocklist. This is then rejected so the user can try again.
- Password managers. A compliance requirement under NIST includes permitting the use of password managers. It suggests organizations allow the paste functionality to facilitate and encourage the use of password managers.
Complexity Requirements vs. Length and Complexity
When it comes to NIST’s new guidelines for passwords, there is one in particular that covers the primary factor in characterizing password strength. Which is password length rather than complexity. It used to be that password complexity was the number one security factor. It emphasized special characters and frequent password resets.

But password creation policies now focus on having user's password choices that are instead based primarily on password length. Analyses of breached password databases reveal that the recommendation for stored passwords is a minimum of 64 characters in length. While user selection can have passwords at least 8 characters in length.
Password Change Policies: What NIST Says
NIST guidelines aim to reduce user frustration as well as weaker password choices by eliminating forced periodic changes. Those who change their passwords frequently are more likely to use the same password or simply add a single letter, number, or special character to the end of it. This is a huge risk when it comes to a security breach. Hackers understand this and will quickly exploit these habits.
Instead of requiring users to change their password every 90 days, they suggest only changing passwords in the event of a security breach. Or every 365 days. Organizations should support session management guidelines that reinforce security without adding unnecessary complexities.

Compromised Passwords: How to Protect Your Accounts
NIST suggests changing your password as soon as you are away from a potential breach. Consider investing in automatic screening of all new passwords to help prevent the use of compromised passwords. These passwords are often compared to lists of breached and frequently used passwords for comparison.
NIST provides technical guidelines for password hashing to further protect user accounts. Password hashing is a way to turn a plain password (like Password 123) into a complex code. Usually, it is a fixed-length string that looks like a mess of letters and numbers and makes no sense. Makes it pretty difficult for hackers to guess.

How to Implement the NIST Password Guidelines in Your Organization
By implementing NIST password guidelines, organizations are more likely to regularly update security policies. All while prioritizing user experience and strengthening breach prevention.
Here are 5 key strategies to keep in mind when aligning your company's security practices with NIST’s new guidelines for passwords.
- Update Your Password Creation Policies. Such as emphasizing password length over complexity and removing regularly forced password expiration policies. NIST recommends shifting focus from complex passwords to ones that are primarily based on password length. Simplify your password management system.
- Use Modern Authentication Methods. Don't rely solely on passwords to keep your organization safe. Using an MFA tool helps to ensure security and protect sensitive data.
- Enforce Password Hashing. Use a suitable password hashing algorithm to help prevent breaches.
- Monitoring analyses of breached password databases. To refine security measures, you should monitor password databases that help to screen your new passwords.
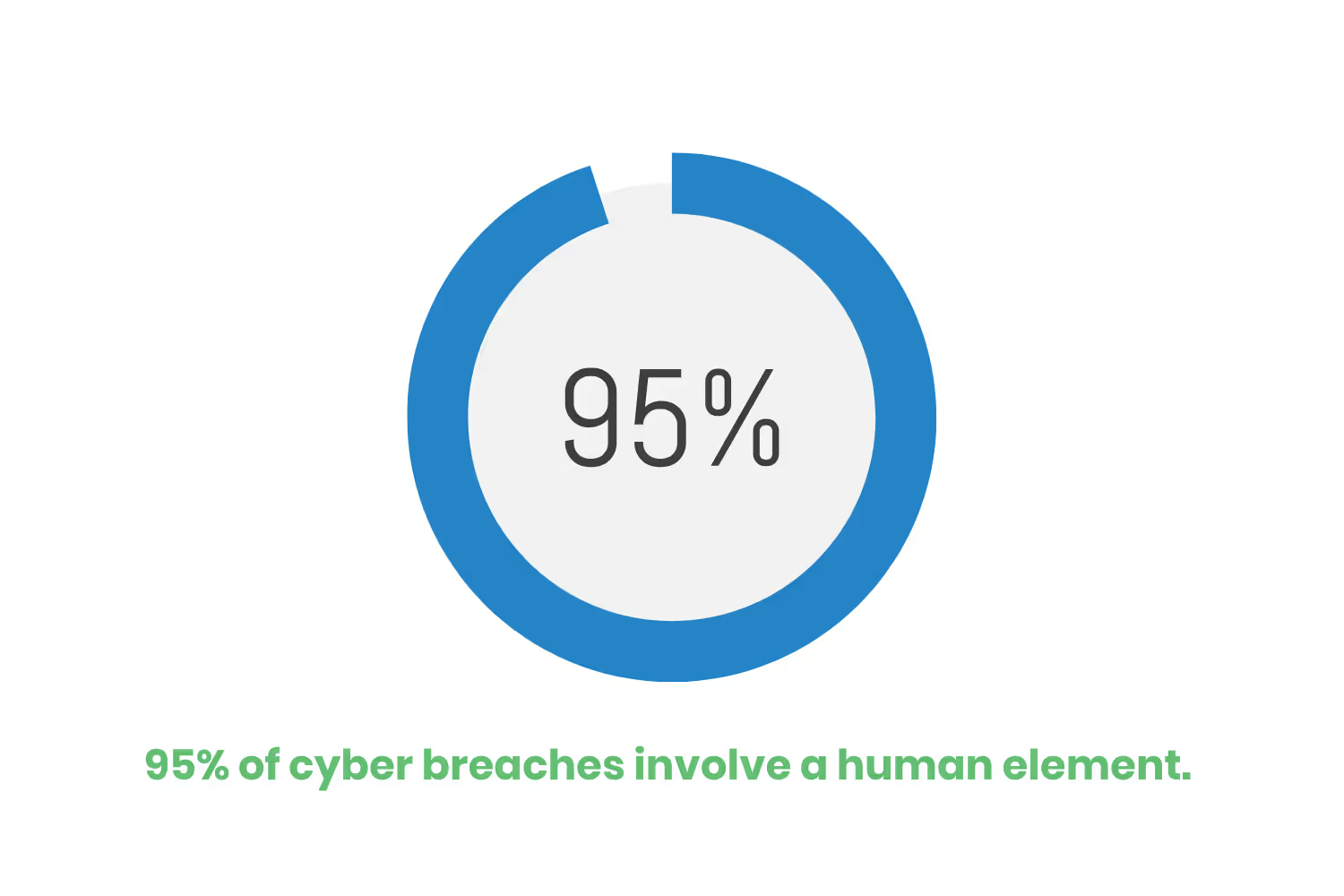
- Educate and train employees. Around 95% of cyber breaches involve a human element. Making sure your team receives proper training can help them make better decisions when it comes to security. Education on how to choose a strong password is vital. Anything that simplifies password management for your team is a big step in the right direction.
Through implementing these strategies, your organization is better equipped to create a secure authentication framework that protects your data. You can instantly reduce reliance on outdated security measures by keeping updated with NIST guidelines.
Conclusion: Why Following NIST Guidelines Matters
Breached passwords remain a constant threat to businesses and individuals alike. Making sure you are following NIST guidelines can help safeguard your important information through secure password creation and adhering to digital identity guidelines. The gold standard for keeping your company secure is ever-evolving. To ensure your compliance, you must have a system in place to detect compromised passwords.
We learned that organizations encourage using a longer password with a minimum length of 8 characters to avoid hackers guessing the password. This, among many other helpful tips, is why NIST remains the number one proprietor for password guidelines.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




