8 Cybersecurity Questions Every Healthcare Company Should Ask Itself
When evaluating the current state of your cybersecurity environment, healthcare companies need to ask themselves specific questions to evaluate themselves.

If you’re the owner of medical practice, you’ve gone through a decade of schooling, taken oaths, and continue to hone your craft.
You’re already stretched thin between treating your patients and managing your revenue cycle. But everywhere you look you see headlines reading the latest breaches and attacks.
You notice that most of them happen to be other healthcare companies; hospitals, pharmacies, and other small practices.
Mixing in data security with what you already have on your plate as a physician may seem impossible.
You may have a few practices in place, but you wouldn’t know without asking yourself these cybersecurity questions…
Does my practice have a reasonable cybersecurity budget?
There’s no such thing as an impenetrable system, it’s more about making “reasonable efforts.” That’s why you need to define a clear, concise cybersecurity budget for your healthcare company before you begin buying any services.
According to Black Book Research, 88% of hospitals' healthcare IT security budgets haven’t changed since 2016. This stagnation mixed with hacker’s increased desire for medical information is a huge problem.
This type of budget gives you an immediate, clear guide to your biggest gaps. The is the step before you even dip your feet into the vendor evaluation process.
If you’re in a similar situation to the hospitals mentioned above, it’s time to re-evaluate. While you’re updating this budget, take a look at how much other sectors spend. For example, some financial service firms spend roughly $2,300 per employee on cybersecurity annually.

Start with your budget but keep in mind, money doesn’t solve everything.
Who do I involve when evaluating cybersecurity vendors?
After you’ve created or updated an IT security budget, it’s time to look at vendors. The purchasing process can be long and arduous, there are thousands of different tools out there.
But you don’t have time for short cuts when it comes to data security, especially in healthcare. As a doctor, your first responsibility involves helping your patients’ well-being. Your second responsibility is to protect their data. If you fail to protect it, you’ll do permanent damage.
While you’re evaluating vendors, involve managers and other employees. They’ll bring in different perspectives from the ground level that will help guide the process. Assign them solutions to evaluate to encourage autonomy within the workplace.
When the evaluation process ends, add those employees to an evaluation committee. After a few months, have them look at the effectiveness of what you purchased.
As it stands today, more than 80% of companies fail to include business users in cybersecurity purchasing decisions.
Oftentimes cybersecurity’s kept at the C-Suite level. Involving more employees encourages a better environment.
Are my existing vendors trustworthy?
If you don’t properly evaluate your vendors, you could get into some serious trouble. As a healthcare company, you already know that your vendors need to sign Business Associate Agreements (BAAs). But according to HIMSS, 70 percent of healthcare vendors experienced a significant security event within the last 12 months.
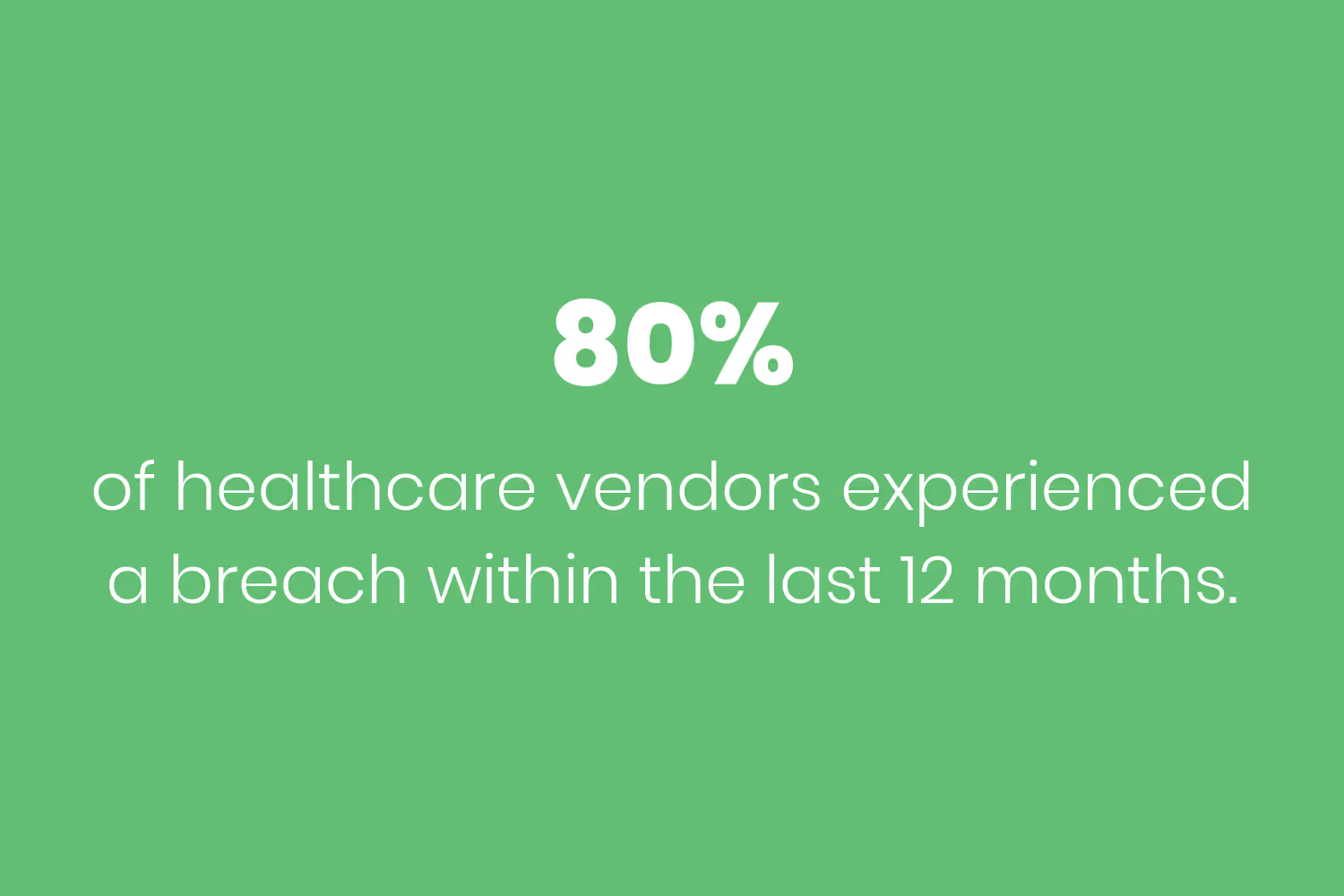
Imagine reaching out to your patients to tell them that one of your vendors exposed their sensitive data. That’s a PR disaster. First, you’ll have to explain to them why the vendor handled their personal health information (PHI). Second, they’ll lose all trust in you. Third, you may have to pay a fine.
I’m not saying you shouldn’t outsource certain services, some devices need outside vendors. That’s an unreasonable request. Especially since 98% of hospitals are either actively considering or already outsourcing certain services. But evaluate them beforehand (see above) and look into the ones you’re already using.
Can I trust my medical staff?
As a C-Level executive at a hospital or the lead doctor at a practice, you’ll naturally want to trust your staff. Your staff is the most essential resource in your practice. If you don’t trust them, it would lead to a hostile environment. No one wants to work at a place where their managers don’t trust them.
When it comes to trust in cybersecurity, it’s a two-way street. You need to be able to trust that your employees know how to keep patient data safe. They need to know that you trust them as their manager.
Your employees are great. But they’re also the main source of breaches. There’s been a 26% increase in security incidents involving employees since 2016.
What’s worse is 18% of healthcare employees are willing to give access to their accounts for a price. If one of your employees sold their information, how much sensitive information would the buyer have access to? More importantly, how long would it take to figure out that they sold their information in the first place?
On the flip side of that statistic, 82% of workers aren’t willing to accept money in exchange for access to medical records. That’s still a passing grade.
Is my staff trained enough?
Google anything about cybersecurity training and every source will say the same thing, “make sure its ongoing.” They all agree on this because of one thing. The most successful cyberattacks happen as a result of human error.
To put it into perspective, 91% of data breaches on the cloud happen due to social engineering according to Kaspersky. A simple or threatening email in your employees’ inboxes could be just enough to cost your organization millions.

Even though experts urge companies to do ongoing training, they’re efforts haven’t worked successfully. Only about 50% of all companies commit.
Those who don’t commit to ongoing training take shortcuts. They take the simple route, using one-time efforts like training during orientation and posting policies for review. That might change if they knew that 78% of employees are aware of the risks of unknown links but click on them anyway.
Those who approach cyber training proactively witness results. Investing in user awareness and ongoing training reduces risks by 45%. Finding out that your security environment is in better hands now that you’ve implemented those employee education seminars should make it easier to sleep tonight.
Sure you’re training your employees on data security, but is it enough?
When's the last time I updated my medical equipment?
We live in an exciting time. It feels like every day there’s a breakthrough due to advancements in medical technology.
But the majority of healthcare providers aren’t updating their equipment.
A jaw-dropping 71% of healthcare organizations still run off of legacy Windows devices. What makes this such a scary statistic is that Microsoft’s pulling support for these systems on January 14, 2020.
When this date comes, IT folks will refer to legacy Windows devices as “End-of-Life” (EOL). In a nutshell, this means that Windows will no longer patch, upgrade, or support them. Their product lifecycle is complete.
It also means no more security fixes. So those who don’t update their systems by then put their entire infrastructure at risk.
It’s unrealistic to expect that you’ll update your medical equipment every year, it’s expensive. But at some point, the cost of using out-dated, vulnerable technology far outweighs upgrading your system.
Do I have the right policies in place?
The healthcare compliance environment is growing ever more complex. It’s a living, breathing environment that changes with the advancements occurring. But it’s not something to be afraid of.
Healthcare compliance and risk management are there to ensure that you’re protecting yourself and your patients. Oftentimes, a solid compliance environment leads to great cybersecurity and vice-versa.
But it all starts with your policies.
Few industries have more defined regulations than healthcare. But that’s not a bad thing. It means that the government has done most of the work for you. They’ve defined what you need to do, it’s just a matter of you following through. After all, you’re liable for what you haven’t implemented.
As an example, medical establishments across the nation continue to adopt bring your own device (BYOD) policies. These policies help establish trust with out-of-network doctors and they’re convenient for everyone. However, as you introduce more external devices, you also increase your risk of getting attacked. That’s where compliance helps.
You can introduce an exciting new BYOD policy to your organization to motivate workers. But layer it with management, security, and education policies. That way you’ll always be on top of your environment.
Do I have a response plan for my practice and patients?
Sometimes, no matter how much time or money companies spend on data security they’ll still experience a breach or attack. Some experts believe that experiencing a cyber-attack is inevitable.
With that mindset, you’ll need to have a response plan in place. It’s always a good practice to prepare for a worst-case scenario.
As a healthcare entity, transparency is your friend if you experience a breach. After all, you’ll have to report it to the U.S. Department of Health and Human Services (HHS) within 60 days if it affected 500 or more patients.
But if you contain the breach in less than that time, you’ll save a lot of money that you’d otherwise lose. According to IBM, companies who contained a breach within 30 days saved more than $1 million compared to those who didn’t.
The hardest part of experiencing a breach of any kind in the healthcare space is admitting it to your patients. Admitting weakness to them is difficult, especially if they’re public figures. But you owe it to them. Their data likely was what was most affected by the breach. The proper response plan can restore a patient’s faith in your organization.

As an example, let’s look at Nordstrom’s 2018 breach. Although it’s outside of healthcare, many commended how the retail company responded. In a nutshell, a contractor handled the company’s data improperly. The breach exposed their employee’s most sensitive information.
As soon as Nordstrom noticed the breach, their security team notified law enforcement and their employees immediately. This kicked off an investigation and allowed their employees to respond. The company also gave employees free identity protection software for 24 months.
Again, Nordstrom isn’t a healthcare company but their breach exposed sensitive data that’s similar to PHI.
A cyber-attack will happen at some point, ensure you have a response plan.
Conclusion
This blog piece is not a one-time checklist, it’s ongoing. Approach it similarly to the question about employee training. To do cybersecurity the right way, you need to check and re-check.
That’s the only way to stay as prepared as possible to prevent and/or respond to an attack.
As a healthcare entity, you have a lot of responsibility on your shoulders. Take your cybersecurity efforts as seriously as performing treatment on your patients.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)