CMMC-AB February Town Hall: 7 Key Takeaways
Here the key takeaways from the CMMC-AB’s February 2022 town hall.

In addition to the monthly CMMC-AB Town Hall, the Department of Defense (DoD) also held their own Town Hall in February.
The DoD Chief Information Security Officer (CISO), David McKeown, hosted the event. It provided insight into the role CMMC plays in a larger cybersecurity program for the defense industrial base (DIB).
As CMMC nears finalization, the strategic vision for improving DIB cybersecurity is more clear.
Yet, the logistics involved with setting up a scalable ecosystem remains the largest hurdle.
Strategic Vision for DIB Cybersecurity
In 2013, the Presidential Policy Directive (PPD) 21 established the DIB as one of 16 critical infrastructure sectors.
The USD(P) (Under Secretary of Defense for Policy) is the DIB Sector Risk Management Agency (SRMA). It brings together resources from different departments within DoD. These resources include acquisition, engineering, cybersecurity, intelligence, security, etc.
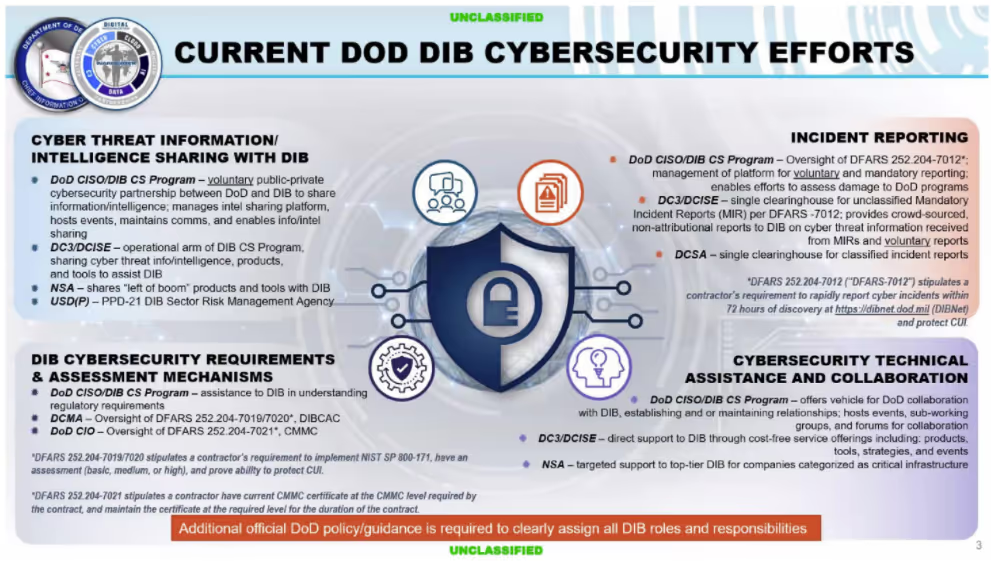
As the CISO for the DIB, Mr. McKeown has identified four lines of focus for implementing cybersecurity in the DIB:
- Cyber Threat Information Sharing - voluntary and confidential, two-way sharing of cyber threat information between DoD and participating DIB companies that has successfully thwarted a good number of attacks. Participation isn’t mandated by DFARS or CMMC. Yet, DoD recommends any DIB companies not participating visit dibnet.dod.mil to apply.
- Incident Reporting - DFARS 7012 requires DIB companies to report cyber incidents within 72 hours. The Defense Cyber Crime Center (DC3) conducts damage assessments for any compromised unclassified systems. The Defense Counterintelligence and Security Agency (DCSA) handles any classified incidents.
- Cybersecurity Technical Assistance and Collaboration - DC3 and the National Security Agency (NSA) have resources (e.g. Cybersecurity Collaboration Center and the DIB Collaborative Information Sharing Environment) available to the DIB to harden their networks and protect covered defense information.
- DIB Cybersecurity Requirements and Assessment Mechanisms - Currently, on a limited basis. The Defense Contract Management Agency (DCMA) performs National Institutes of Standards and Technology (NIST) Special Publication (SP) 800-171 assessments through the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) under DFARS 7019/20. CMMC will serve to enhance DIBCAC assessments through DFARS 7021.
CMMC Implementation Tactics
The DoD only knows the cybersecurity programs of around 1,500 companies in the DIB. That's out of the total 220,000 organizations.
DoD estimates that around 140,000 companies only have access to Federal Contract Information (FCI). That leaves around 80,000 companies that have access to controlled unclassified information (CUI). DoD still plans on completing CMMC rulemaking within the next 24 months. The CMMC contract language will be in all DoD contracts subsequent to rulemaking.
CMMC Level 1 is for organizations that only have FCI. DoD will not require them to obtain a third party assessment of their cybersecurity program.

Instead, DoD expects these organizations to…
- Fulfill 17 practices out of NIST 800-171
- Perform a self-assessment
- Have a C-Suite executive sign off on an assessment uploaded into a DoD provided portal annually
CMMC Level 2 is for organizations that also have access to CUI. With the introduction of CMMC 2.0, DoD suggested bifurcating this group into those…
- Allowed to self-attest
- That would have a third party assessment based on the type of CUI associated within the contract
After additional review, DoD now believes that “probably all” will have to get a Level 2 assessment. This assessment has to come from Certified Third Party Assessor Organization (C3PAO).
CMMC Level 3 is for companies that have the most critical CUI. DoD estimates that around 500 to 600 companies will become certified at this level. The DIBCAC will conduct assessments for Level 3 based on controls from NIST SP 800-172.
The CMMC-AB previously stated that C3PAOs will conduct the NIST SP 800-171 assessments. These happen before an organization seeking certification (OSC) scheduling anything for Level 3.
Disseminating messages about worldwide threats to the DIB has been a challenge for the DoD CISO. Right now, DoD can only effectively reach DIB companies that have already partnered with the NSA and DC3.
CMMC should solve this problem. All DIB companies will register within a central system and provide their contact information.
CMMC Implementation Logistics
The DoD has tasked the CMMC-AB with the logistics challenge of assessing these requirements in the DIB.
During the February Town Hall, the CMMC-AB provided a candid snapshot of the current ecosystem it is creating.

There has been significant progress over the past 12 months by the CMMC-AB. But, there is still a lot of work left before achieving the scale required to fulfill its mission.
Documentation for Interim Voluntary Period
DoD released updated assessment guides under CMMC 2.0 for Level 1 and Level 2. However, we continue to hear that the NIST SP 800-171 framework may soon have an updated version.
According to McKeown, the DoD is in discussions with NIST. The goal of these talks is to add practices and maturity model requirements removed under CMMC 2.0 into a new revision of SP 800-171.

Prior to starting any voluntary assessments, the CMMC-AB and DoD will publish the CMMC Assessment Process (CAP). The DoD has already reviewed an initial draft of this document. The CMMC-AB is in the process of adjudicating their responses.
The DoD Project Management Office (PMO) is still working on some policy guidance around…
- Plans of Action & Milestones (POA&Ms)
- Waivers
- Incentives
But, CMMC-AB CEO Matt Travis expects publication of this document in the next couple of weeks.
Accelerated Implementation
Starting with the endpoint in mind, DoD expects all contracts post rulemaking to include CMMC requirements.
Rulemaking is still expected to take between 9 and 24 months from the announcement of CMMC 2.0 in November 2021. That roughly equates to a time between July 2022 and December 2023.

DIB entities awarded DoD contracts need a CMMC 2.0 certification post rulemaking. This is an accelerated timeline compared to the initial phased implementation.
The old approach would have gradually increased the number of contracts with CMMC requirements. In this model, eventually all contracts included this requirement in FY2026.
Ecosystem Capacity
Let’s take a look at some of the early DoD assumptions. If there are roughly…
- 500 DoD contracts per year
- 100 suppliers on average per contract
- 36% of suppliers (80/220) handle CUI
Those numbers would mean that roughly 18,000 DIB companies would need a Level 2 certification by the end of 2023.
Is the CMMC-AB capable of standing up an ecosystem to support that scale?
The CMMC-AB provided an interesting slide and discussion around what they have been able to accomplish over the past 12 months.
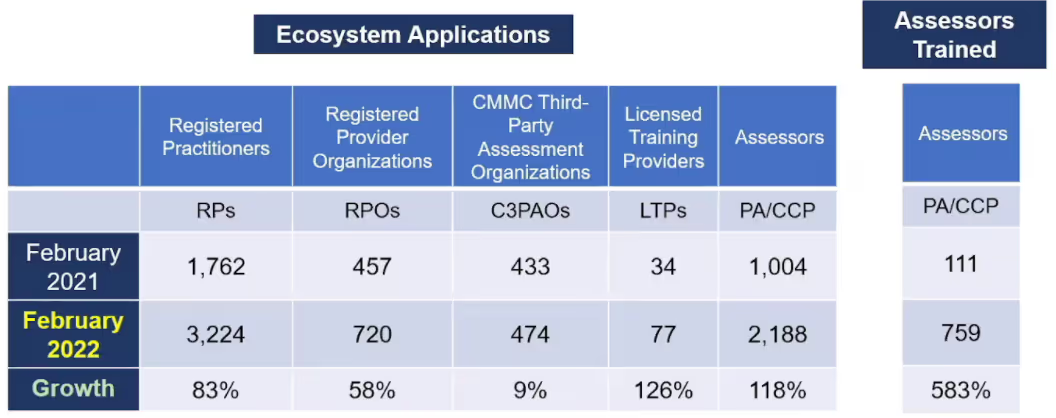
Registered Practitioners (RP) saw an increase of 83%. Meanwhile, the number of Registered Provider Organizations (RPO) has grown 58%.
However, when you filter to see only those active individual consultants listed on the Marketplace, we found 1,934 RPs and 494 RPOs.
The CMMC-AB showed that the number of Third Party Assessor Organizations (C3PAOs) had grown 9% from 433 to 474.
Again, the numbers listed in the marketplace were significantly different. It displayed only 202 C3PAOs pending a CMMC Level 2 Assessment, and 6 authorized.
It’s possible that the CMMC-AB has a backlog of organizations not yet in the marketplace. There’s also the potential that their figures include organizations with lapsed membership dues. Those organizations aren’t listed on the public marketplace.
According to the CMMC-AB, the number of Licensed Training Providers (LTPs) grew 126% from 34 to 77. We found this was closer to the number of 61 LTPs listed in the marketplace.
LTPs have been instrumental in growing the number of trained CMMC Professionals. But, since the exam isn’t yet available, we can’t call these individuals performing services “certified” yet.
The CMMC-AB lumped together any individual who had applied to become a Certified CMMC Professional (CCP) with a count of Provisional Assessors. They said that this group had grown 118% from 1,004 to 2,188. They also refined this count to say that of this group, 759 received training by February 2022 vs the 111 that had received training by February 2021.
The marketplace doesn’t include a category for CMMC professionals in training. But, they do list the number of provisional assessors.
Based on the known number of 146 provisional assessors, we can estimate that the LTPs have trained at least 613 CMMC professionals.
Using the CMMC-AB provided metrics, we can make some assessment capability assumptions.
Let's say 18,000 OSCs will need a Level 2 certification assessment. If that's the case, each of the 474 C3PAOs would need to complete 38 assessments.
That number certainly sounds attainable, but there are only 6 authorized C3PAOs listed in the Marketplace today. So, we have a long way to go before the assessing capability matches the capacity mentioned above.
Back to Bifurcation?
A key part of the February CMMC-AB Town Hall was when Matt Travis discussed bifurcation rumors.
Matt’s perspective was that bifurcation was mostly a mechanism to manage capacity.
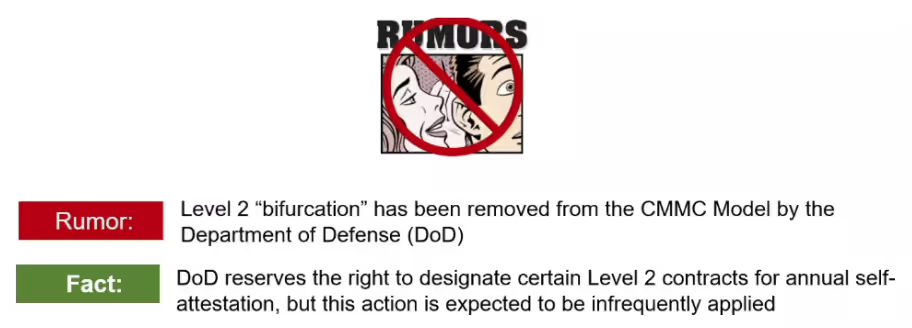
He explained that the day after rule-making, the ecosystem is likely not going to be big enough to accommodate every contract.
Matt also believes DoD still reserves the right to designate some Level 2 contracts for self-attestation. But, he does believe that it will be rare and reserved for a case by case basis.
Conclusion
It was encouraging to hear the strategic vision from the CISO at the DoD Town Hall meeting.
In the next coming months, DoD and the CMMC-AB should resolve the remaining tactical issues related to the CMMC Assessment Process. It’s also possible that voluntary assessments may begin.
Getting over 80,000 contractors and suppliers in the DIB to increase their cybersecurity practices comes at a critical time.
Securing critical infrastructure and protecting critical information is paramount to DoD’s mission. It helps deter war and protect the security of our nation.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




