CMMC-AB December Town Hall: Key Takeaways
Here are the biggest takeaways from the CMMC-AB’s last Town Hall meeting in 2021.

Changing of The Guard
December’s CMMC-AB Town Hall event ushered in a changing of the guard within the accreditation body's board of directors. Karlton Johnson, the previous Chairman of the Board, turned over his chairman position to the vice-chairman, Jeff Dalton.
Mr. Johnson was the first Chairman elected at the CMMC-AB in January 2021. His tenure came to an end in December 2021 after stating that he would not seek a second term. Paul Michaels has become the vice-chairman, taking the position vacated by the new Chairman, Jeff Dalton.
Documentation
Following Karlton Johnson’s farewell address, Matt Travis, the CMMC-AB CEO, reviewed some of the guidance recently released by the CMMC Project Management Office (PMO).
These documents included…
- A model overview
- A spreadsheet that crosswalks the old practice numbers with the new practice numbers
- A CMMC glossary
- Scoping guides for Level 1 and Level 2
- Updated assessment guides for Level 1 and Level 2
- An artifact hashing guide.
Scoping Guide
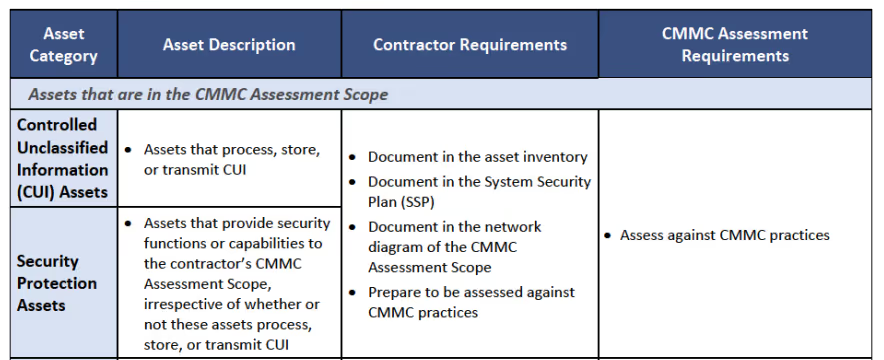
Matthew Travis briefly walked through the Level 2 Scoping Guidance document. It categorizes assets into five groups.

Before we talk about the five categories of assets, it's important to mention the Level 2 Assessment Guide. It uses a broad definition for the term organizational asset:

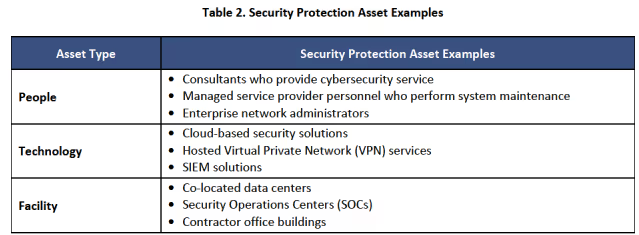
A supporting table in the Level 2 Scoping Guide lists three specific types of security protection assets…
- People
- Technology
- Facilities
Asset Types will all apply to all Asset Categories and not just security protection assets. That's our deduction based on the broad definition of organizational assets.
The purpose of the scoping guide is to establish a boundary for the assessment.
The full breadth of CMMC practices applies only to CUI Assets and Security Protection Assets. Understanding these definitions and identifying this boundary is critical. They help ensure the assessment scope is properly defined.
NIST SP 800-53A, the underlying framework of NIST SP 800-171, identifies items assessed within the assessment boundary as Assessment Objects. Assessment objects can be organizational assets (as described above) or processes and activities performed by an organization relevant to assets within the CMMC Assessment Scope.

An assessment procedure will apply an assessment method (examine/interview/test) to an assessment object during the evaluation of an assessment objective. Assessment objectives can be relevant to one or more types of assessment objects.
For example, AT.L2-3.2.1 (c) and (d) would be relevant to the scope of managers, systems administrators, and users (people) of organizational systems and their training (processes & activities). But, AT.L2-3.2.1 (a) and (b) would be relevant to identifying risks and enforcing policies (processes).
Now that we’ve identified assessment objects, let’s look at the specific categories provided in the Level 2 Scoping Guide.
Controlled Unclassified Information (CUI) Assets
Looking at the first category, CUI Assets process, store, or transmit CUI.
The examples provided during the Town Hall included computers, data files, and employees.
CUI when Stored
CUI stored is at rest. If the CUI is digital, then the electronic media or system memory storing the data is a CUI asset. If the CUI is physical, then the paper document is a CUI asset.
CUI when in Process
When CUI is in process, it is being used. If the CUI is digital, then the systems accessing the data, such as a computer, server, application, user, printer are CUI assets. If the CUI is physical, then the user viewing or editing the data are CUI assets.
Transmitting CUI
When transmitting CUI, it’s moving from one location to another.
If it’s digital, then systems sending, receiving, and facilitating the transfer are all considered CUI assets.
If it’s physical, the sender, receiver and potentially the transporter (if they have access to the information) are CUI assets.
Security Protection Assets
Security Protection Assets provide security functions to the CMMC Assessment Scope.
The examples provided during the town hall included the…
- People working at the service providers who support OSCs
- Cloud-based solutions that you use
- Third-party security operations centers (SOC)
NIST Special Publication (SP) 800-171 introduced the concept of security protection assets. Initially, this definition focused only on assets providing security to CUI Assets.

The new CMMC Assessment Scope Level 2 Version 2.0 defines security protection assets as providing security to any assets within the CMMC Assessment Scope, irrespective of whether or not they process, store, or transmit CUI. The key difference here is that now we are looking at assets protecting the CMMC Assessment Scope and not just CUI assets.

The CMMC Assessment Scope includes the majority of assets. It doesn't include those that are physically or logically separated from CUI assets. Those cannot process, store or transmit CUI.

This expanded definition will now include assets that provide security. This includes CUI Assets and contractor risk-managed assets and specialized assets as well.
Going back to the general definition of organizational assets as anything that has value. Under this guidance, OSCs will need to incorporate locks, cabinets, and similar security protection assets for CUI. These need to exist in their asset inventory, facility diagram and system security plan (SSP).
This brings us to a discussion that occurred on LinkedIn regarding the implications of this decision.
The first concern raised was the new requirement to expand the scope of assets inventoried.
The second concern is that cloud-based security tools must be compliant with all CMMC Level 2 practice requirements.
Developers of SaaS tools and hosted solutions may decide it’s not worth the investment to achieve CMMC themselves. Some of the tools I’m specifically referring to are…
- Remote monitoring and management (RMM)
- Security information and event management (SIEM)
- Anti-virus (AV)
- Security operations centers (SOCs)
Software-as-a-service (SaaS) creates an increased risk for compliant security to degrade actual security.
We anticipate that the DoD and CMMC-AB have some work to do on finalizing how to assess security protection assets. But for now, the guidance published is that all CMMC practices will apply to security protection assets.
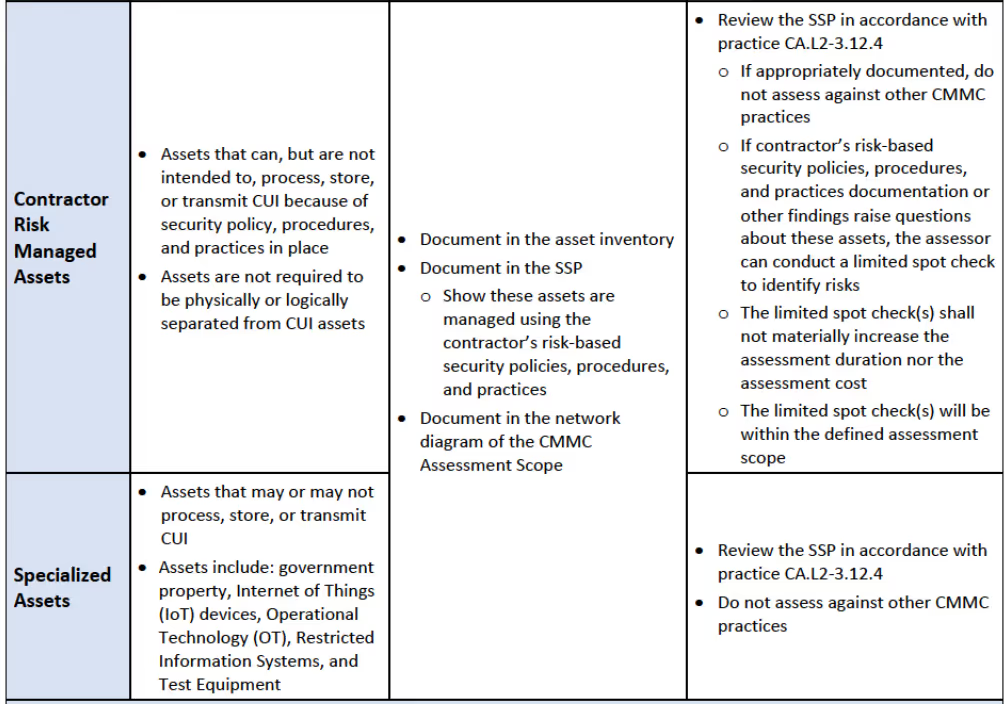
Contractor Risk Managed Assets (CRMA)
Assets that don’t process, store, or transmit CUI because of policy, procedure, or practice but are not physically or logically separated from CUI Assets are contractor risk managed assets (CRMA).
CMMC 2.0 generated some discussion regarding the removal of maturity processes. These included documenting written policies, procedures and resourced plans for each domain.
We discussed a popular opinion in a previous blog post. In a nutshell, it was that the removal of these requirements from CMMC didn’t negate the requirement to have these. NIST SP 800-171 Rev 2 still requires them under Appendix E.
For those who heed this advice, your reward is the ability to now remove assets from the more rigorous assessment scope. This happens by classifying assets as contractor risk managed through policy and procedures.
Amira Armond, one of the provisional CMMC instructors, has been publishing scoping scenarios. She's been doing so since the release of the scoping guidance.
In scenario 6, she posed an example with an email server and cell phone that, by policy, should not contain CUI. The scenario explores a situation wherein the Government sends CUI to the email server of the OSC. In turn it synchronizes automatically with the OSC’s cell phone.
Even though the assets in this example processed and stored CUI, she categorized them as CRMA. They’re CRMA because, by policy, neither asset should have CUI. She goes on to list what the OSC should do to remove the CUI and prevent this from happening again. But, the scenario illustrates a big takeaway. Just because an asset can or does process, transmit or store CUI, doesn’t mean you should automatically categorize these as CUI Assets.
The benefit for an OSC to categorize assets as CRMA is that instead of assessing these assets to the full rigor of NIST SP 800-171, they would only need to appropriately document them in the system security plan (SSP).
If the assessor has questions about these assets after reviewing the policy, procedure, and practice documentation, they’ll define a limited spot check in the assessment scope.
Specialized Assets
Specialized assets may or may not process, store, or transmit CUI but they aren’t assessed by all CMMC requirements.
The OSC should…
- Inventory these assets
- Document them in the SSP and network diagram
- Detail security policies, procedures and practices for managing these assets
The scoping guide lists several types of specialized assets and we will discuss each in more detail.
Government Furnished Equipment (GFE) is equipment owned by the government but made available to a contractor. Since the government provided the equipment, it should be set up according to a security technical implementation guide (STIG) authorized by the DoD.
Internet of Things (IoT) are devices that contain the hardware, software, firmware, and actuators that allow the devices to connect, interact, and freely exchange data and information. This category of assets includes devices like wireless inventory trackers, wearable technology, connected appliances, the list goes on. NIST has released guidance and standards for the IoT landscape.
Operational Technology (OT) includes programmable systems or devices that interact with the physical environment. This would include computer numerical control (CNC) systems, scientific equipment, transportation systems, etc. An interesting article by Gartner from July 2021, predicted that by 2025 cyber attackers will have weaponized OT environments.
Restricted Information Systems include systems configured by government requirements and used to support a contract. Examples from the Scoping Guide include…
- Fielded systems
- Obsolete systems
- Product deliverable replicas
Test Equipment includes hardware or components used in the testing of products, system components, and contract deliverables. Examples from the Scoping Guide include…
- Oscilloscopes
- Spectrum analyzers
- Power meters
- Special test equipment
Other Scoping Guide Issues
Matt Travis mentioned the Level 2 Scoping Guide’s discussion of logical and physical separation techniques. He also mentioned use cases when FCI and CUI might be within the same or different assessment scopes and considerations for external service providers. Unfortunately, Matt did not spend much time on these portions so we’ll explore each here with a little more detail.
Separation Techniques
To categorize an asset as Out-of-Scope, it must be logically or physically separated from CUI Assets. The Scoping Guide points to section 1.1 of NIST SP 800-171 Rev 2 for creating a separate security domain:

Logical Separation occurs when software configuration prevents data from flowing along a physically connected path. Examples of mechanisms provided by the Scoping Guide include firewalls and Virtual Local Area Network (VLANs).
Data is physically separated when the only way to transfer it is manually using human controls (e.g. USB drive).
Examples of mechanisms that control physical access provided by the Scoping Guide include…
- Gates
- Locks
- Badge access
- Guards
Use Cases
The first use case assumes the OSC is processing, storing, or transmitting federal contract information (FCI) and CUI within the same assessment scope.
However, looking at the CMMC Self-Assessment Scope Level 1, we find the following cautionary statement: “Because FCI is a broad category of information, the contractor will likely focus the self-assessment on their entire environment”.
In this scenario, the OSC would define a single assessment scope. An assessor would certify the implementation of Level 1 and 2 practices to the assets within it. Although not explicitly stated, we assume if this Level 2 certification allows for self-attestation, the OSC could self-assess Levels 1 and 2 for this single scope as well.
A second, more likely scenario posited that FCI and CUI have separate assessment scopes. Here, the OSC may conduct two separate CMMC activities…
- OSC performs a self-assessment for the Level 1 practices against the Level 1 Scope that includes only those assets that process, store or transmit FCI.
- Based on the bifurcation of the OSC’s contract, the Level 1 and 2 practices are either assessed by a certified assessor or self-assessed against the Level 2 Scope, which includes CUI assets and security protection assets. The OSC would inventory contractor risk-managed assets and specialized assets and document them in the SSP and network diagram.
External Service Providers
The CMMC Self-Assessment Scope Level 1 defines external service providers (ESPs):

An ESP is within the Level 1 scope if it meets FCI Asset criteria (process, store, or transmit FCI). An ESP is within the Level 2 scope if it meets CUI Asset criteria (process, store, or transmit CUI) or if it provides security functions to any OSC assets within the CMMC Assessment Scope.
For example, an ESP providing security information and event management (SIEM) services may not process CUI. Although it’s logically separated from CUI Assets, it’s still within scope as a security protection asset because it provides security functions to CMMC Assessment Scope assets.
The Level 2 Scoping guide lists several special considerations regarding ESPs…
- OSCs may inherit sufficiency for practice objectives from ESPs. A shared responsibility matrix identifies practice objectives provided by the ESP and practice objectives that are the responsibility of the OSC to implement.
- Relevance of accreditations held by the ESP (FedRAMP, SOC 2, and CMMC). At this time, only CMMC accreditations are relevant since no reciprocity exists with other frameworks.
- Consider the agreements in place, including service-level agreements, memoranda of understanding, and contracts that support the OSC’s security objectives.
Q&A Session
The AB took the time to answer some pre-submitted questions ahead of December’s meeting...
- Question: Could you provide an overview of the rulemaking process and how they can follow it?
- Answer from Matt Travis: Rulemaking is a function of executive branch agencies to provide details of regulating new policies. The process entails the government officials (in this case the DoD Office of the Chief Information Office, Project Management Office, the Office of Information and Regulatory Affairs (OIRA), the Office of Management and Budget (OMB), and potentially departments who may also look to ultimately CMMC as a standard for their supply chain. The outcome of this process will be an interim rule. This rule will then allow for a period of public comment, followed by a congressional review before the final rule.
- Question: If rulemaking does take two years, does that mean that CMMC is on hold for two years?
- Answer from Matt Travis: No, the DoD recognizes that cyber threat actors are not waiting for rulemaking. So, assessments will be open for business from those C3PAOs authorized prior to rulemaking.
- Question: Some OSCs are moving forward with CMMC version 1.0 until the rules come out for version 2.0. Is that a reasonable approach?
- Answer from Matt Travis: No, CMMC version 1.0 is no longer valid, refer instead to the updated 2.0 documentation.
- Question: Has there been any new consideration for internationally owned certification bodies who wish to participate from their American division?
- Answer from Matt Travis: I’m not going to speak for the DoD, I know that’s one of the issues they’re looking at but I have no news to provide.
- Question: In the Certified CMMC Professional (CCP) training class, the CMMC Assessment Process (CAP) was to only be available to a C3PAO under a non-disclosure agreement (NDA), will you provide CCPs with a copy of the CAP?
- Answer from Matt Travis: The CAP is still in draft form and we will publish it as a public document once approved by the DoD.
- Question: When do you anticipate the release of the updated CAP?
- Answer from Matt Travis: Shortly after the holidays (early 2022)
- Question: What should OSCs be doing right now to prepare for CMMC?
- Answer from Matt Travis: OSCs should engage the CMMC ecosystem and get started. If anything, 2.0 emphasizes that this is moving forward. Use this time to get engaged and start preparing:
- Step 1: Make sure you understand what is on your network, what are those assets you’ll want to protect and what are those assets that are in play.
- Step 2: Engage the Registered Practitioners (RPs) and Registered Provider Organizations (RPOs) to get help.
- Step 3: Engage a C3PAO to get assessed.
- Question: Can you discuss the roles the RPs and RPOs will be playing in CMMC 2.0?
- Answer from Matt Travis: They're critical when you think about what is at stake. Your ability to bid on defense contracts and your ability to partner with primes. These are the coaches, advisors, and consultants who will help OSCs navigate the assessment of NIST SP 800-171 and how best to prepare.
- Question: Will C3PAOs be performing the Level 2 assessments before DIBCAC performs the assessment of the NIST SP 800-172 enhancements for Level 3?
- Answer from Matt Travis: Not speaking for the department but my understanding is that for Level 3, C3PAOs will conduct the assessments for Level 2 before the DIBCAC assesses the remaining practices from Level 3.
- Question: When will you require RPs to renew?
- Answer from Kyle Gingrich: RPs are on an annual schedule, so a year from when they initially became an RP. The CMMC-AB will be providing free online delta training in early Q1. It will exist for any RP or CCP trained by a Licensed Training Partner (LTP) to get everyone up to date on CMMC 2.0.
- Question: What is the status regarding FedRAMP moderate equivalency?
- Answer from Matt Travis: The defense federal acquisition regulation supplement (DFARS) permits the use of cloud services providers (CSP) and managed services providers (MSP) not FedRAMP moderate certified if they demonstrate equivalency to FedRAMP moderate. I do know that when assessing a C3PAO, the DIBCAC did accept a sponsored third-party review showing FedRAMP moderate practices implemented by their cloud provider. The ability for an assessor to determine FedRAMP moderate equivalency is a policy issue that the CIO’s office has taken the lead on.
- Question: When do you expect the DIBCAC assessments of C3PAOs to resume?
- Answer from Jon Hanny: We’re still working out a few items, as far as the implications of 2.0. But we've rescheduled the C3PAO candidates that were in flight when the pause happened for the end of January. The expectation is that we will have everything worked out by mid-January and assessments will resume. New C3PAOs are being added into the queue as they are ready.
- Question: When do you expect C3PAOs to begin assessments?
- Answer from Matt Travis: The DoD will ultimately have to give the green light. But we're still working on some documentation and administrative items. (CAP, dispute resolution finalization, FedRAMP equivalency, emass administrative requirements)
Question From The Dialog Box
- Question: Will the CMMC-AB need to obtain ISO certification before certifying additional C3PAOs?
- Answer from Jeff Dalton: We have a 2-year window to achieve ISO 17011 certification. We are able to authorize C3PAOs to conduct valid assessments in the interim period.
- Question: How can we volunteer? Any special requirements?
- Answer from Jeff Dalton: If you want to volunteer for a working group, we put calls out whenever we are starting one. We already have over 200 people participating. Send me an email at jdalton@cmmcab.org if you’d like to do so.
A Look Ahead to 2022
Matt Travis expects 2022 to start with great news when the first voluntary assessments get started.
But, he affirmed his commitment to more proactive communications from the AB to promote OSCs getting certified.
The rulemaking process (9 to 24 month period) shouldn’t stop any OSC from going ahead and getting assessed now. He believes DoD will reward early movers. Lastly, the CMMC-AB plans on updating its website in early 2022 with a brand refresh and enhanced marketplace.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




