All CMMC Version 2.0 Changes and Their Impact
On November 4, 2021, the Acquisition and Sustainment Office of the Under Secretary of Defense (OUSD A&S) announced a new strategic direction for the Cybersecurity Maturity Model Certification (CMMC) framework. Here are all of its changes.

On November 4, 2021, the Acquisition and Sustainment Office of the Under Secretary of Defense (OUSD A&S) announced a new strategic direction for the Cybersecurity Maturity Model Certification (CMMC) framework.
The launch of CMMC 2.0 comes after an internal DoD review of the program that began in March 2021 based on industry feedback of the interim DFARS rule.
These changes will have far-reaching implications throughout the CMMC ecosystem. They'll also greatly impact the defense industrial base (DIB). This blog will assess these changes and discuss their impacts.
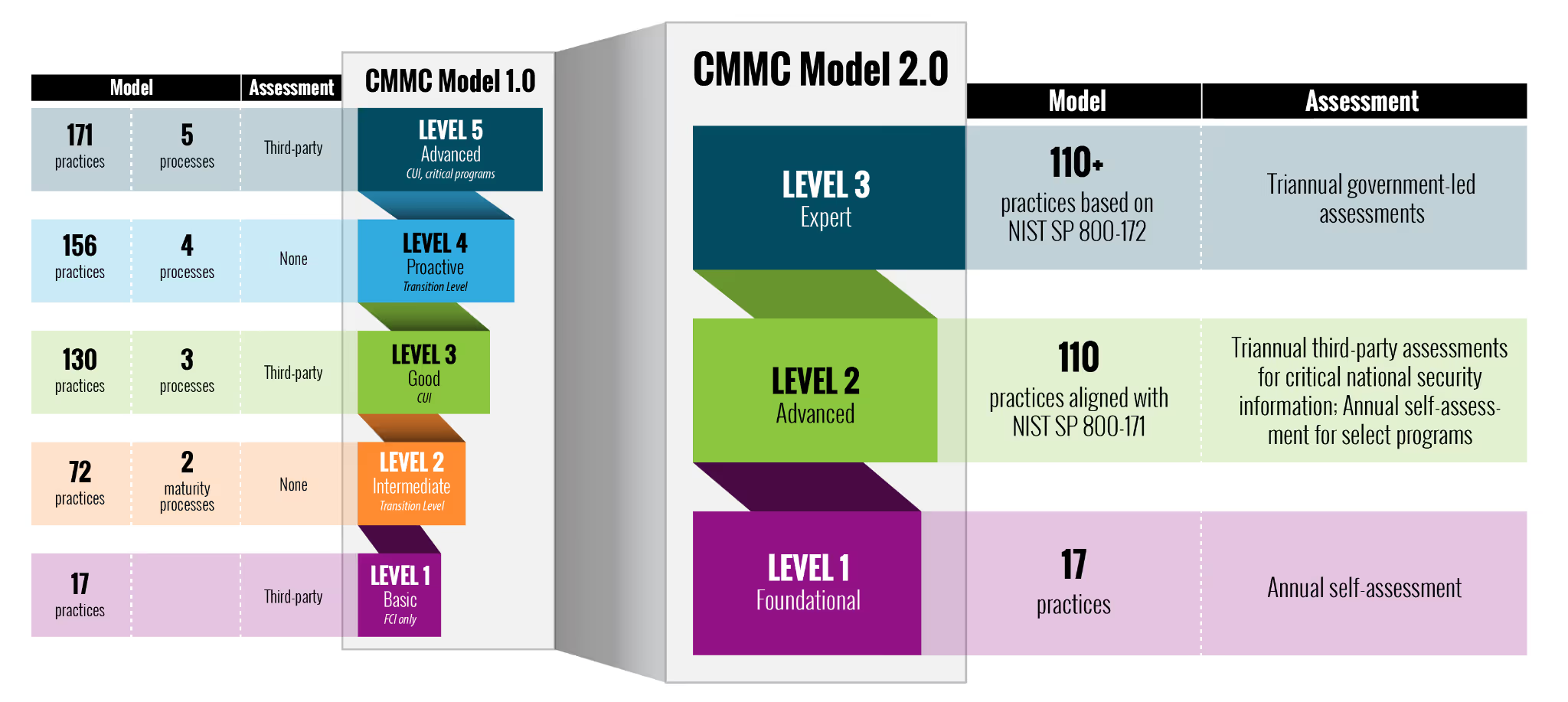
Change 1: Steamlines the model from 5 to 3 compliance levels
The previous model (V1.02) had five maturity levels and the new model contains only three.
The new model removed Levels 2 and 4. Maturity Level 1 remained unchanged. It still has 17 practice requirements that align with the 15 cybersecurity practices in FAR 52.204-21.
The new Maturity Level 2 takes the place of the previous Maturity Level 3. But, without the delta 20 practices, aligning this level with the 110 practices of NIST SP 800-171.
The new Maturity Level 3 is still under development based on a subset of NIST 800-172. It takes the place of the previous Maturity Levels 4 and 5.
Impact 1: Removal of Delta 20 practices
The CMMC-AB assumed under V1.02 that most organizations wouldn’t attempt to achieve certification at Maturity Level 2. In this version, this level was an intermediate step for those who plan on achieving certification to handle CUI.
Only a few dozen of the largest prime contractors would’ve attempted certification for Maturity Levels 4 and 5.
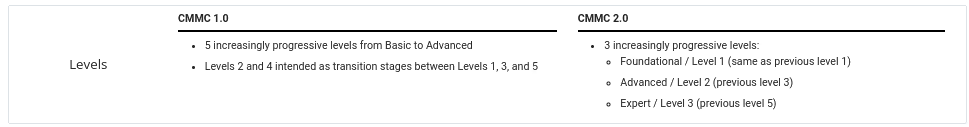
The biggest impact was the removal of the delta 20 practices from the new Maturity Level 2.
This brings the requirements of handling CUI back in line with the current obligations under NIST 800-171.
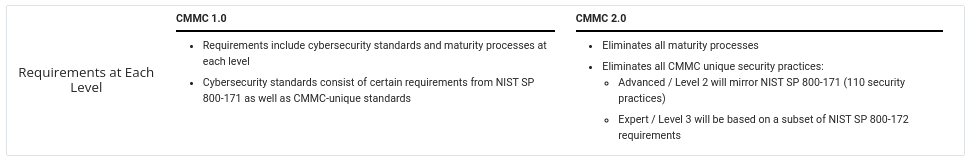
Change 2: Eliminates all maturity processes
The previous model had five maturity processes. These progressed from performed to documented, managed, reviewed, and optimized.
Like the title of this blog post says, CMMC 2.0 eliminates all maturity processes.
But, this doesn’t remove the obligation to have written processes and policies for those who want a Level 2 certification.
NIST 800-171 Revision 2 derives requirements from FIPS 200 and NIST SP 800-53. NIST tailored these previous requirements and controls to protect CUI in nonfederal information systems.
The tailoring wasn’t an endorsement for the elimination of requirements and controls and NIST cautioned that “organizations should not assume that satisfying those particular requirements (NIST 800-171) will satisfy the security requirements and controls in FIPS 200 and (NIST) SP 800-53.”
Impact 2: Removal of resourced plans
Appendix E of NIST 800-171 details the tailoring of both FIPS 200 and NIST SP 800-53 for application to protect the confidentiality of CUI in nonfederal systems.
For example, NIST tailored AC-1 from NIST 800-53 was as an NFO - expected to be routinely satisfied by nonfederal organizations without specification.
AC-1 from NIST 800-53 requires organizations to develop and document an access control policy. It also requires that procedures exist to facilitate the implementation of that policy.
NIST listed these policy and procedure requirements from NIST 800-53 as NFO controls for all 17 domains.
The CMMC V1.02 resourced plan requirements are not found in either NIST 800-53 or FIPS 200. CMMC 2.0 appears to remove these processes for the new Maturity Level 2.
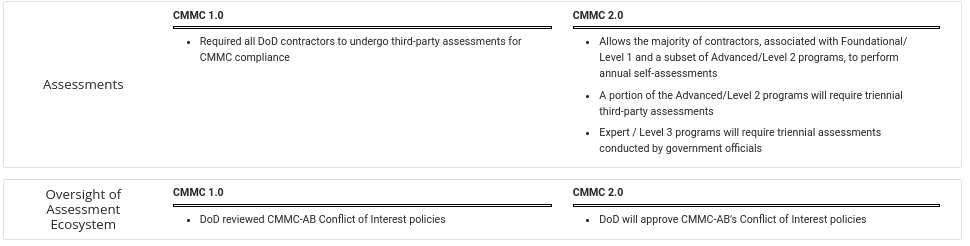
Change 3: Assessment for Organizations Seeking Certification (OSCs)
Maturity Level 1 certifications will now allow self-assessments.
Certified Third-Party Assessor Organizations (C3PAOs) will assess a subset of OSCs seeking Maturity Level 3. The type of contracts will determine the subset of suppliers and contractors assessed by C3PAOs.
Third-party assessments will apply only to those OSCs handling contracts with information deemed critical to national security. Other OSCs with CUI may self-assess if their contracts aren’t deemed critical to national security.
Government officials will assess Maturity Level 3 certification. Most likely, the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
A slight deviation of the assessment process was also made. After an assessment under V1.02, the C3PAO would submit an assessment report to the CMMC-AB. The CMMC-AB would then provide a final review and issue a certification determination or mediate disputes.
Version 2.0 now has the C3PAO providing its assessment report to the DoD.
Impact 3: Fewer Third-Party Assessments and more Self-Assessments
Enabling Maturity Level 1 certification through self-assessment is directly related to cost. With this change, the majority of the DIB won’t have to pay for a third-party assessment.
Bifurcating the Maturity Level 2 certifications further reduces the number of organizations that will require a third-party assessment. In other words, there will much less work for C3PAOs under the CMMC 2.0.
The extent of organizations allowed to self-assess is unknown at this time.
It appears the DoD is refining the scope of CUI they want to focus on protecting with the limited resources available.
Change 4: Inclusion of Plan of Action and Milestones (POA&Ms)
Before CMMC, organizations were able to delay the implementation of NIST 800-171 requirements.
All they had to do was demonstrate that they planned on implementing those controls at a date in the future.
CMMC V1.02 removed the ability to have a POA&M for any practice requirements at the assessed Maturity Level.
CMMC 2.0 has brought back the ability to use a POA&M on a limited basis.
The highest weighted requirements (based on the SPRS point scale) must be fully implemented at the time of the assessment. DoD also intends on publishing a minimum SPRS score that would support certification with POA&Ms.

Impact 4: More flexibility for OSCs implementing some controls
The inclusion of POA&Ms is a retreat from the pass/fail model that was CMMC V1.02.
OSCs will now have the flexibility to pass a certification assessment without implementing all required practices. All that's required is that they use POA&Ms under further guidance not yet released.
The higher weighted requirements tend to be the more expensive and difficult controls to implement. So, although helpful, only a portion of the requirements will allow the use of POA&Ms.
Change 5: Waivers
Under CMMC V1.02 there wasn’t an allowance for waivers. The scheduled roll-out over five years intended for an increasing number of contracts to contain the CMMC DFARS clause each year.
Before the award of a contract with the CMMC DFARS clause, an OSC would need their certification.
Flow-down of CUI from contracts with the CMMC DFARS clause couldn’t occur unless those subcontracts had their CMMC certification enabling them to receive the CUI. CMMC 2.0 introduces the concept of a waiver.
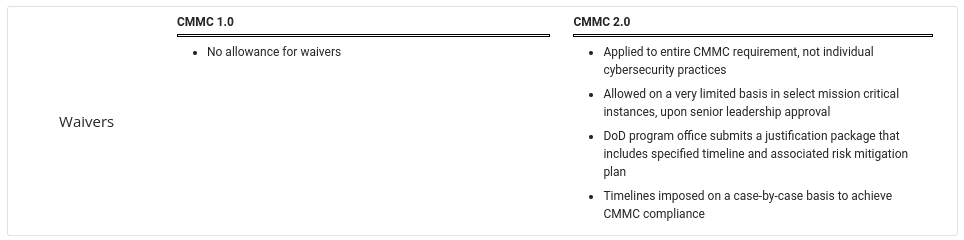
Impact 5: Limited basis for mission-critical instances
Waivers would exclude an OSC from the CMMC 2.0 requirements completely.
Waivers aren’t based on individual practices but rather exclusion from the model itself. The limited guidance provided indicates that DoD reserves the right to grant waivers with senior leadership approval for mission-critical instances.
This provision grants DoD authority to exempt any OSC from these cybersecurity requirements.
Change 6: Accrediting C3PAOs, Assessors and Instructors
The CMMC-AB will continue to be the accreditation body for…
- C3PAOs
- CMMC Assessors
- CMMC Assessor Instructor Certification Organization (CAICO)
But, the AB must achieve compliance with the ISO/IEC 17011 standard first.
C3PAOs are also required to comply with ISO/IEC 17020 and the CAICO needs to comply with the ISO/IEC 17024 requirements.
Under CMMC 2.0, the DoD will approve all CMMC-AB conflicts of interest within the ecosystem.
Impact 6: C3PAO accreditation on hold and DoD assumes bigger role
In March 2020 the Memorandum of Understanding, the CMMC-AB agreed to achieve and maintain ISO/IEC 17011.
The CEO Matthew Travis acknowledged that the pursuit of ISO/IEC 17011 was a priority for the CMMC-AB as recently as the September Town Hall.
We don’t expect to see any further C3PAOs certified or the creation of a CAICO until the CMMC-AB receives their ISO certification.
Conclusion
The DoD has been reviewing CMMC for the past eight months.
The goals of the initial program were ambitious. But, implementation of V1.02 would have been expensive and forced many smaller businesses out of the DIB.
The compromises communicated in the release of CMMC 2.0 demonstrate a refocusing. More specifically on CUI that DoD has deemed worth the investment of time and resources protecting.
It also yields the management of key frameworks back to NIST by aligning the maturity levels with SP 800-171 and SP 800-172.
Although rulemaking may not occur for another 9 to 24 months, the requirements of CMMC 2.0 exist for the most part today in DFARS 252.204-7012 (Maturity Level 2) and FAR 52.204-21 (Maturity Level 1).
It’s not known what will become of the CMMC-AB and the role DoD decides they will play in the certification of an assessment ecosystem. But, the justification for third-party assessments hasn’t changed.
The failures of self-attestation and self-assessment were the main drivers behind the creation of CMMC.
The introduction of CMMC 2.0 is the result of a risk mitigation effort. Its purpose is to direct the available resources to protect only the most critical information.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




