The Go-To CMMC Policy Templates According to NIST
Organizations should identify the roles assigned to each statement within the policy. Mapping policy commitments to requirements and roles creates a shared responsibility matrix.

Information security policies describe what the organization expects from its security operations. NIST provides guidance on policy writing within SP 800-53. Writing a CMMC Level 1 policy requires an understanding of the 15 basic requirements. Organizations should identify the roles assigned to each statement within the policy. Mapping policy commitments to requirements and roles creates a shared responsibility matrix.
The purpose of this blog is to:
- Outline information security policy section headings.
- Provide a CMMC Level Information Security Policy
- Assign ownership of each policy statement to an organizational role.
- Map the provided policy statements to NIST SP 800-171 assessment objectives.
- Use the policy as the basis for creating a shared responsibility matrix.
- Provide best practices for establishing and implementing governance.
Section Headings
We derived the section headings for our policy from NIST SP 800-53 Rev 5. NIST titles the first control within each domain "Policy and Procedures". For example, here is the control for AC-1:

From this guidance, we derived the following section headings:
- Purpose
- Scope
- Coordination Among Entities
- Compliance
- Revision and Review History
- Management Commitment
We reserved Section 3 for the policy statements. We wrote a single policy that addressed all requirements within the CMMC Level 1. We titled section 3 Information Security Policy. For CMMC Level 2, you may choose to separate this policy into 14 domain-level policies. In that case, you may title section 3 Access Control.
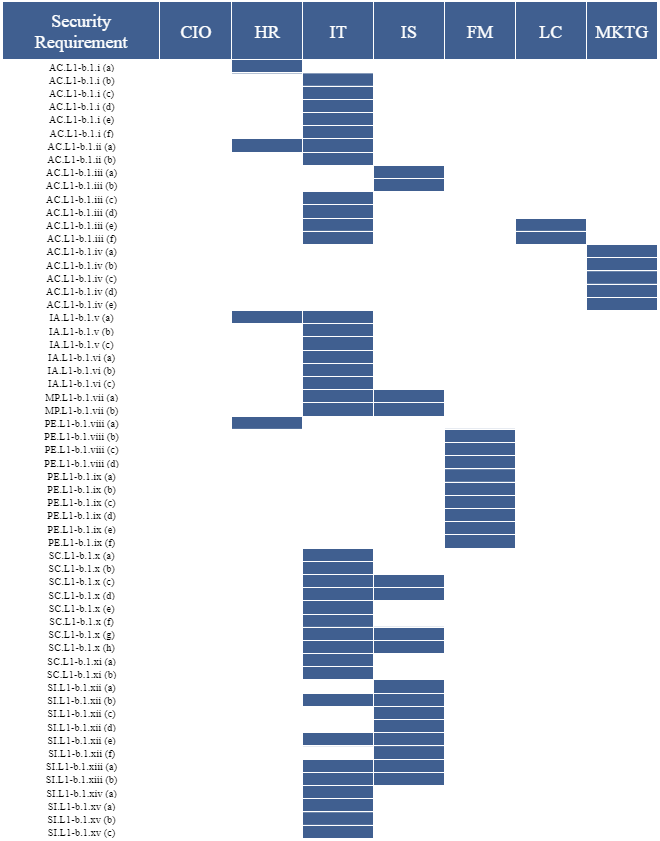
Section 8 assigns responsibilities for each policy statement to a role. Section 9 establishes traceability from our policy statements to the requirements. Section 10 uses the assignments and traceability to establish a shared responsibility matrix.
Section Subheadings
The only section with subheadings is section 3. In our policy, we defined the subheadings as the domains or control families. If you were to use a similar approach for Level 2, you may group related practices into capabilities.
Sample CMMC Level 1 Information Security Policy
This section will provide some content from our CMMC Level 1 policy. Feel free to download the whole policy as a word document here:
1. Purpose
The purpose of this policy is to safeguard sensitive information from unauthorized access.
2. Scope
This policy applies organization-wide, encompassing all systems, users, and facilities.
3. Information Security Policy
3.1 Access Control
- We document all authorized user credentialing activities. We maintain accurate records of authorized users from on-boarding to termination. Defined job requirements form the basis of granting access to systems, data, and non-public spaces.
- We maintain a list of authorized processes, documenting who granted permission for each.
- A centralized identity provider (IdP) limits system access. The IdP limits access to authorized users, processes and domain-joined devices.
- We revoke system access when employees leave the organization.
- We disable accounts that have been inactive for 30 days.
- Role-based access controls restrict access to systems, data, and functions.
- Contracts establish terms and conditions for handling sensitive information with external entities.
- Only authorized individuals can post content to websites and social media. Authorized and trained individuals review drafted content for nonpublic information. They also conduct quarterly reviews of existing websites and social media content. Authorized personnel remove nonpublic information discovered during these reviews.
3.2 Awareness and Training
- We train individuals authorized to post content to identify nonpublic information.
- Individuals with assigned sanitization responsibilities for digital media complete annual training. This training covers the latest techniques and best practices for data sanitization.
- We train all employees on how to safeguard sensitive information. This training focuses on identifying threats and protecting organizational systems and information.
- All members of the IT team take annual training on malware prevention. This training covers how malware infects hosts and spreads.
4. Coordination Among Entities
Effective coordination among roles maintains consistent control measures aligned to security objectives.
5. Compliance
All activities must follow the Federal Acquisition Regulation (FAR 52.204-21) requirements.
6. Revision and Review History

7. Management Commitment
Management commits to establishing a culture of security. Management will provide the necessary resources to ensure the implementation of security measures.
The responsible party for this policy is the CIO. The responsible party has the authority to enforce this policy within the organization. This includes administering disciplinary actions for non-compliant employees and contractors.
The CIO may grant exceptions to this policy. The organization will track any exceptions and review them on an annual basis.
Signature X_______________________
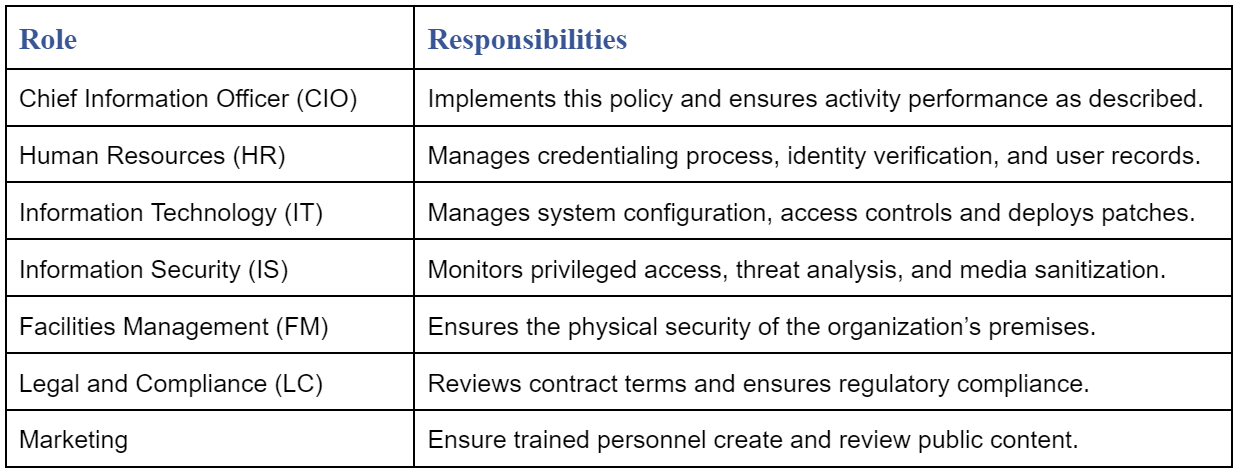
8. Roles and Responsibilities Matrix
We identified all policy subsections and created column headings for roles. The Roles and Responsibility Matrix shows assignment of each subsection to a role.

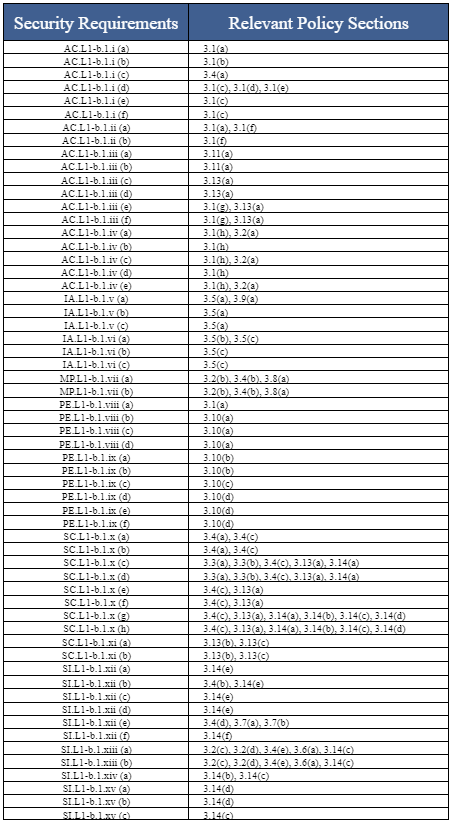
9. Policy Traceability Map
We inventoried all assessment objectives within the 15 security requirements. In Section 9, we identified the relevant policy sections that governed the objectives.
10. Shared Responsibility Matrix
Combining the roles and policy traceability map creates our shared responsibility matrix.
Governance Best Practices
KISS (Keep it simple, stupid)
You should strive to keep policies as simple as possible. Let’s review the discussion from NIST SP 800-53 under AC-1:

Organizations should refrain from stating control language within their policies. Consider your audience for the information security policy. The executive leadership team should review and approve this policy. Other departments may have assigned roles within the policy. Write policies in clear language for non-technical audiences.
Consolidating policies where possible
The Level 2 CMMC Assessment Guide references 38 different policies. Using 38 policies would create a lot of work to review and update them on an annual basis. The most common approach to CMMC Level 2 we’ve seen is 14 domain level policies.
There is a trade-off with consolidation, which is the length of the policy. Having one policy for CMMC Level 1 is workable since it only covers 15 controls. Our CMMC Level 1 policy is six pages. There are two other pages for the traceability and shared responsibility matrices.
Define Parameters
NIST SP 800-171 contains requirements to define parameters. Keep an eye out for requirements that include the verbs identify, define, and specify. For example, the first practice requires identifying authorized users, processes, and devices:
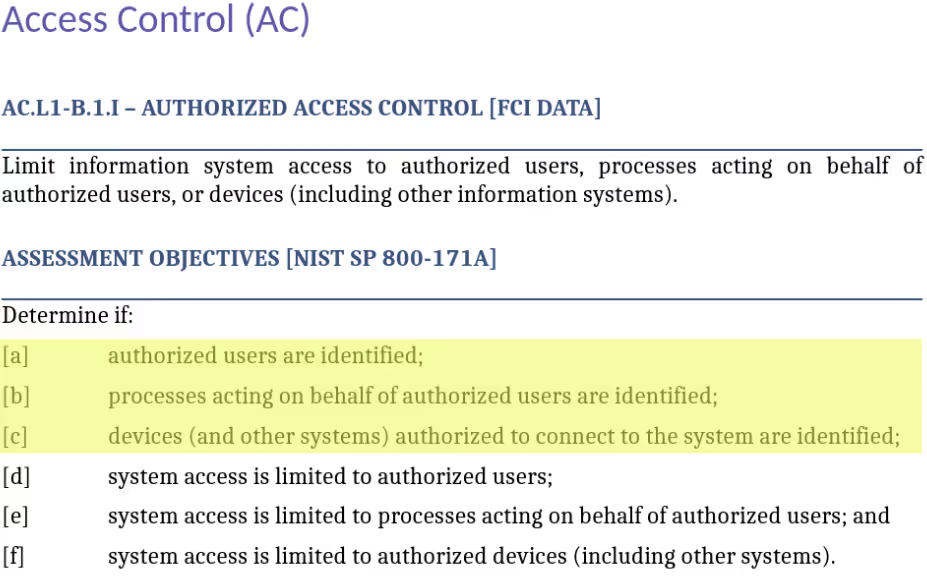
In our policy, we address identifying authorized users and processes under Access Control.

We address identifying authorized devices under Configuration Management.

Understand the Requirements
Organizations should recognize that NIST SP 800-171 encapsulates many other supporting NIST publications. For example:
- Identification and Authentication practices reference SP 800-63-3
- Media Protection practices reference SP 800-88
- System and Communications practices reference SP 800-41
- System and Information Integrity practices reference SP 800-40 and SP 800-83
NIST SP 800-53 is a broader catalog of controls sitting atop a library of other NIST publications. The derived SP 800-171 requirements originated from an underlying SP 800-53 control. Having a mapping of the two publications helps in three ways:
- Practitioners can review the full control; not the parts tailored to address confidentiality.
- SP 800-53 shows related controls. This helps practitioners write more complete policy statements that achieve the desired goal.
- The FedRAMP Moderate baseline defines some parameters for controls applicable to CMMC. DoD recognizes these parameter definitions as adequate. These defined parameters can serve as a starting point for defining your own values.
Read the supporting publications and leverage their guidance to write informed policy statements. If you do this, you’ll start to meet some of the level 2 requirements when addressing the level 1 practices. For example, you cannot remediate flaws if you don’t have a system inventory.
Authorizing the Policy
Policies have a signature line for a reason. The owner of the policy should sign it. In doing so, they commit the organization to the statements contained within it.
Track Exceptions
You may have exceptions to policy statements. Only the authorizing official should approve exceptions. Develop a plan of action for exceptions that violate underlying regulatory requirements. Remember that there are no acceptable limited deficiencies within CMMC Level 1 requirements. All systems handling federal contract information (FCI) must meet the 15 basic requirements.
Carrying out the Policy
You’ll find many commitments in the policy. You should track that responsible roles carry out these commitments. You can use a shared calendar or spreadsheet. Our GRC platform incorporates continuous monitoring tasks to keep you on track. It also organizes artifacts that show completion of the tasks.
Distribute and Track Policy Acceptance
You should distribute the policy to relevant stakeholders on an annual basis. You should track that policy stakeholders have received and reviewed all relevant policies. Our GRC platform allows organizations to distribute and track policy acceptances.
Conclusion
Crafting a comprehensive information security policy is essential for meeting CMMC requirements. Write policy statements that are clear and concise. Map policy statements to the responsible roles and regulatory requirements. Use policy maps as the basis for creating a shared responsibility matrix. Establish a strong policy foundation around CMMC Level 1 before moving on to Level 2. Download our free CMMC Level 1 policy template to jump-start or verify your efforts. Our GRC platform establishes traceability to both through an intuitive interface.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




