NIST SP 800-171A Rev 3 Mapping to Rev 2 Assessment Objectives: A Thorough Guide
In May 2024, the NIST published revision 3 of Special Publication (SP) 800-171. Revision 3 supersedes Revision 2 published in early 2020 and updated in early 2021. Let’s breakdown a mapping of this revision to revision 2.

In May 2024, the NIST published revision 3 of Special Publication (SP) 800-171. Revision 3 supersedes Revision 2 published in early 2020 and updated in early 2021.
The Defense Federal Acquisition Regulations Supplement (DFARS) has driven the adoption of these requirements. The DFARS safeguarding requirements apply to contractors and suppliers handling covered defense information. The term covered defense information is synonymous with DoD-controlled unclassified information (CUI). The DFARS 252.204-7012 clause applies when an information system handles this information. Handling involves processing, storing, or transmitting information. The DFARS always invoked the requirements in SP 800-171 in effect at the time of the solicitation.
In May of 2024, the OUSD issued a class deviation. This memo directed contractors to continue complying with the requirements of revision 2. This class deviation will remain in effect until rescinded. The DoD is still working through Title 32 and 48 rule-making efforts. Title 32 defines the Cybersecurity Maturity Model Certification (CMMC) program. Title 48 requires contractors to have a certificate as a condition of contract award.
The applicability of NIST SP 800-171 extends to all Federal agencies. DoD was the first to adopt these requirements for their non-federal partners. A larger, government-wide initiative stems from Executive Order 13556 issued in November 2010. In May 2024, the Office of Management and Budget (OMB) received the proposed FAR CUI rule. This rule would define the safeguarding requirements of CUI for all Federal agencies. Those following these developments believe these requirements may invoke NIST SP 800-171. If so, the requirements may point to the updated revision 3.
Evolution of Revision 3
NIST announced their intent to update SP 800-171 on July 19, 2022.
Some of their goals included:
- Eliminating the distinction between basic and derived security requirements.
- Updating requirements and families to reflect updates in NIST SP 800-53 revision 5
- Increase specificity to remove ambiguity and improve effectiveness
- Eliminate the non-federal organization control tailoring category
- Introduce organization-defined parameters (ODP) to increase flexibility
- Remove outdated and redundant security requirements
Initial Public Draft (IPD)
NIST published the initial public draft (IPD) of revision 3 in May of 2023.
Some key takeaways from the IPD included:
- Reduction of security requirements from 110 to 109
- Removed 3 requirements deemed not related to protecting CUI confidentiality
- Removed 1 requirement that was technology-specific
- Incorporated 23 requirements into other requirements
- Proposed 26 new requirements
- Increase of families (domains) from 14 to 17
- Reduction of non-federal organization controls from 61 to 25
At the time, NIST did not publish a corresponding assessment guide for Revision 3. Based on our crosswalk of the IPD to NIST SP 800-53A, we estimated 510 assessment objectives.
Final Public Draft (FDP)
NIST published the final public draft (FPD) of revision 3 in November of 2023. Some key takeaways from the FPD included:
- Reduction of security requirements from 109 to 95
- Removed 3 requirements addressed by other related controls (ORC)
- Incorporated 3 requirements into other security requirements
- Removed 10 of the proposed security requirements in the IPD
- Added 2 new security requirements
- Increase in the number of assessment objectives from 320 to 445
- Categorized 56 objectives as an organization defined parameters
- Eliminated the non-federal organization tailoring category
Sp 800-171 Rev. 3
NIST published SP 800-171 Rev. 3 in May of 2024. Some key takeaways from the final publication include:
- Increase in the number of security requirements from 95 to 97
- Separated the incident response plan from the incident-handling capability.
- Recategorized risk response from ORC to CUI when creating 03.11.04.
- Increase in the number of assessment objectives from 445 to 509
- Categorized 88 objectives as organization-defined parameters
The Role of NIST SP 800-53
The basic and derived labels from SP 800-171 identified the requirement's source. NIST derived basic requirements from FIPS 200. Derived requirements came from a tailoring of the moderate SP 800-53 Rev 4 baseline. Revision 3 eliminates this distinction. NIST derived all criteria from the moderate control SP 800-53 Rev 5 baseline.
This presents a unique challenge when mapping work between revisions. Mapping basic requirements to controls from the SP 800-53 catalog is challenging. Practitioners with experience using the mapping table may already understand this challenge.
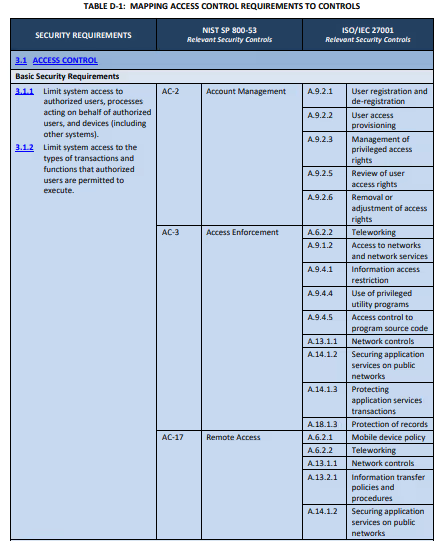
Mapping revision 2 to SP 800-53 Rev 5 enables a more accurate crosswalk from revision 2 to revision 3. You can download our mapping resource here. In this crosswalk, we drill down to the nearest objectives from both publications. We trained claude.ai to check the nature and strength of each relationship based on NIST IR 8477.
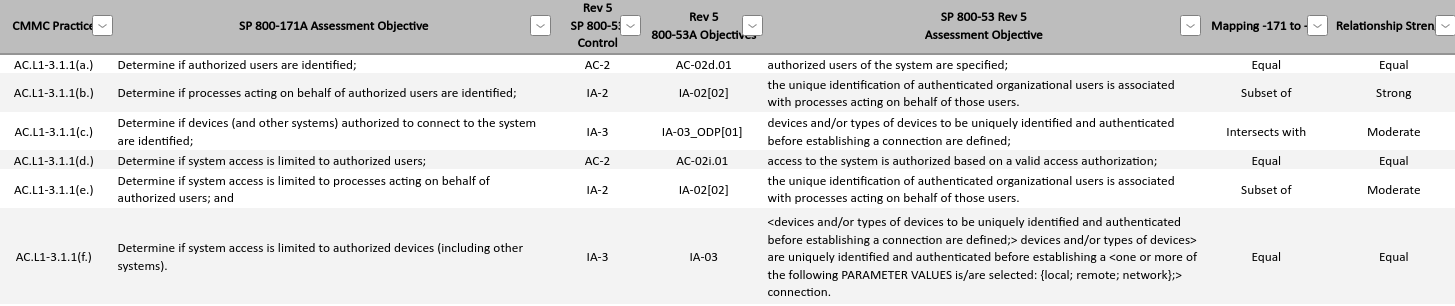
The SP 800-171 Rev 3 publication identifies the underlying SP 800-53 Rev 5 control(s). This mapping only connects requirements to controls. We refined these references to map objectives from SP 800-171A Rev 3 to objectives within SP 800-53 Rev 5.
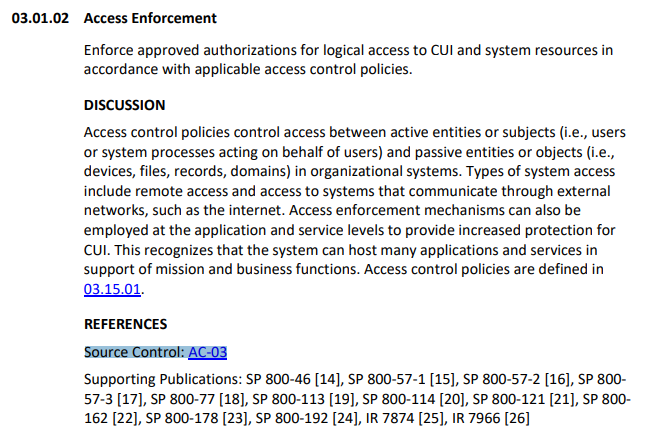
Mapping Objectives Between Revisions
We had the following goals mapping Revision 2 and Revision 3:
- Crosswalk work done under Rev 2 into future requirements with Rev 3
- Identify new objectives in Rev 3 that were not present in Rev 2
- Identify objectives within Rev 2 that are no longer required in Rev 3
- Incorporate organization defined parameters from the FedRAMP baseline
Let’s use requirement 3.1.1 as an example. Under revision 2, this requirement included 6 objectives. Here is how these objectives map to revision 3 requirements:
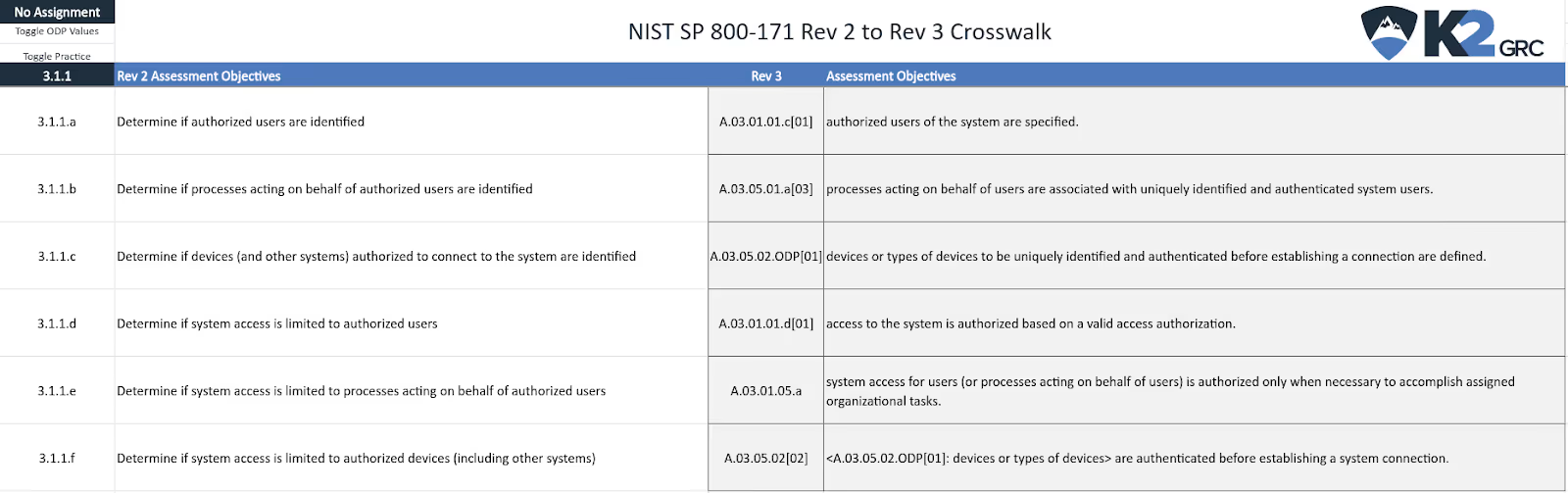
In this example, NIST derived 3.1.1 from FIPS 200. The SP 800-53 Rev 5 mapping indicates these objectives map to more than one control and more than one family. The Rev 3 crosswalk reveals that half the objectives map to the access control family. The other half maps to requirements within the identification and authentication family.
Here is the mapping of the first part of 3.1.1:
- Identify authorized users. (SP 800-171 Rev 2 - 3.1.1(a))
- Specify authorized users of the system. (SP 800-53 Rev 5 - AC-02d.01)
- Specify authorized users of the system. (SP 800-171 Rev 3 - A.03.01.01.c[01])
It gets more difficult to map the second part of 3.1.1:
- Identify processes acting on behalf of authorized users. (SP 800-171 Rev 2 - 3.1.1(a))
- Associate identification of authenticated organizational users with processes acting on their behalf. (SP 800-53 Rev 5 - IA-02[02])
- Associate processes acting on behalf of users with identified and authenticated system users. (SP 800-171 Rev 3 - A.03.05.01.a[03])
Now consider looking at it from the perspective of Rev 3. Here is a list of the requirements for 03.03.05 and their related objectives from Rev 2:
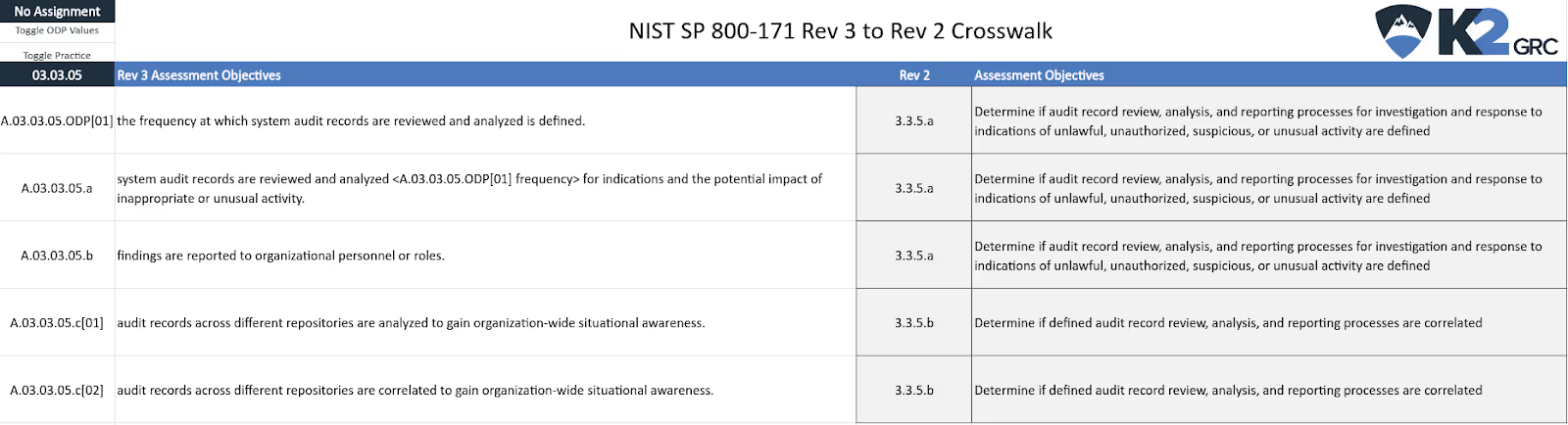
In this example, NIST derived 3.3.5 from AU-6(3) within NIST SP 800-53 Rev 4. The SP 800-53 Rev 5 mapping indicates that part (a) maps to part of the base control from AU-6. Part (b) maps to the control enhancement AU-6(3). The Rev 3 crosswalk confirms this mapping.
Here is the logic of the first objective from 3.3.5 within NIST SP 800-171 Rev 2:
- Define the audit record review, analysis, and reporting processes for investigation. Define the response to indications of unlawful, unauthorized, suspicious, or unusual activity. (SP 800-171 Rev 2 - 3.3.5[a])
This part maps to AU-6a. and AU-6b. from NIST SP 800-53 Rev 5 which contains three ODPs:
- Define the frequency to review and analyze system audit records. (SP 800-53 Rev 5 - AU-06_ODP[01])
- Define inappropriate or unusual activity (SP 800-53 Rev 5 - AU-06_ODP[02])
- Define personnel or roles to receive findings from reviews and analyses. (SP 800-53 Rev 5 - AU-06_ODP[03])
- Review system audit records <frequency>. Analyze for indications of <inappropriate or unusual activity>. Analyze the potential impact of the inappropriate or unusual activity. (SP 800-53 Rev 5 - AU-06a.)
- Report findings to <personnel or roles>. (SP 800-53 Rev 5 - AU-06b.)
The first part of 3.3.5 maps to the first three parts of 03.03.05 from SP 800-171 Rev 3:
- Define the frequency to review and analyze system audit records. (SP 800-171 Rev 3 - A.03.03.05.ODP[01])
- Review system audit records <frequency>. Analyze for indications and the potential impact of inappropriate or unusual activity. (SP 800-171 Rev 3 - A.03.03.05.a)
- Report findings to organizational personnel or roles. (SP 800-171 Rev 3 - A.03.03.05.b)
In this example, we can see some of NIST's tailored actions. NIST condensed part (a) of AU-6 when defining A.03.03.05.a. They also removed two organization defined parameters. Defining inappropriate or unusual activity is a prerequisite to analyzing audit records. Defining personnel or roles to receive findings is a prerequisite to reporting. Using SP 800-53 identifies tailoring actions that may lead to less adequate implementations.
Incorporating FedRAMP ODPs
There is a high degree of overlap between SP 800-171 and SP 800-53. The Federal Risk and Authorization Management Program (FedRAMP) uses SP 800-53 controls. Section D within the DFARS 7012 clause references the FedRAMP moderate baseline. This establishes some reciprocity between standards for protecting CUI. FedRAMP Moderate baseline parameter assignments may meet derived requirements from SP 800-171.
We’ll use the previous example of 03.03.05 from SP 800-171. Using the drop down in Cell A1 we selected the FedRAMP Moderate baseline. If FedRAMP defines the same ODP found in SP 800-171 Rev 3, then the value appears next to the ODP. The displayed text also updates to incorporate this value.
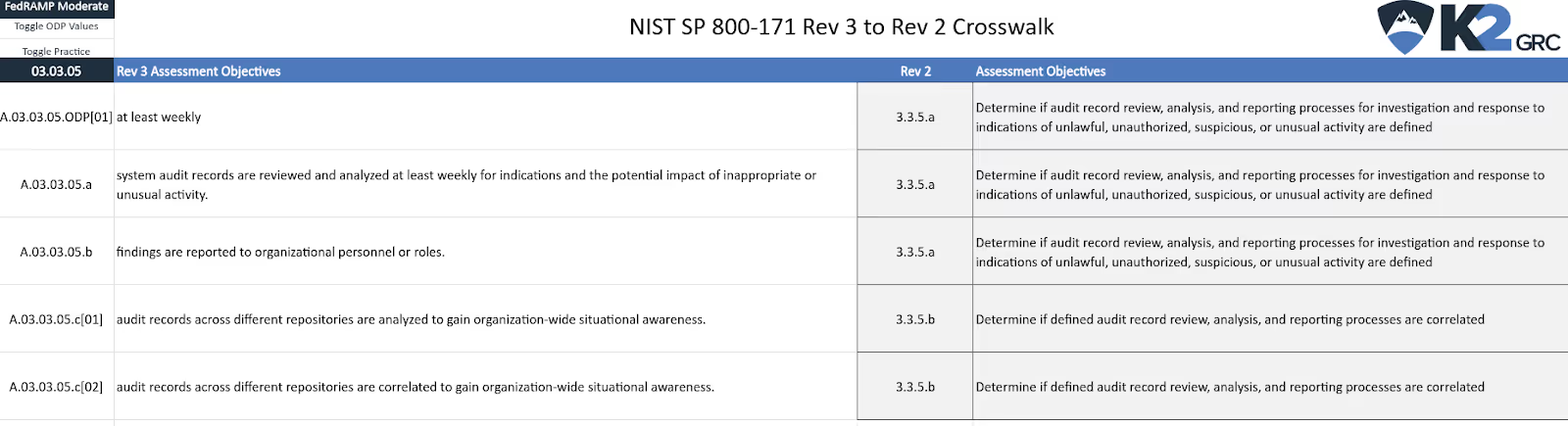
Here is the logic of this mapping for A.03.03.05.ODP[01]:
- ODP: Define the frequency to review and analyze system audit records. (SP 800-171 Rev 3 - A.03.03.05.ODP[01])
- Define the frequency to review and analyze system audit records. (SP 800-53 Rev 5 - AU-06_ODP[01])
- FedRAMP Moderate defined assignment/selection parameter: AU-6 (a)-1 [at least weekly]
Conclusion
There are currently no contractual requirements to use SP 800-171 Rev 3. DoD has stated its intent to maintain Rev 2 as the standard for its proposed CMMC program. Other agencies may adopt Rev 3 as the standard within the proposed CUI rule.
We developed this resource to assess changes that NIST made to this standard. Mapping these standards together can better prepare organizations for meeting future requirements.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




