NIST SP 800-171 Rev 3 FPD Crosswalk of Assessment Objectives (XLSX Included)
This blog will focus on the following topics; crosswalk methodology, key changes in the update to NIST SP 800-171 Rev 3, organizational defined parameters (ODPs), and applicability.

We have an updated version of this blog that talks about the recent changes to NIST SP 800-171 Rev 3.
The National Institute of Standards and Technology (NIST) publishes Federal cybersecurity standards. Special Publication 800-171 is the standard for protecting regulated data in non-federal systems.
NIST released the initial public draft (IPD) of Revision 3 in May of 2023. They published a final public draft (FDP) on November 9. That same day, they published the IPD of the new assessment guide.
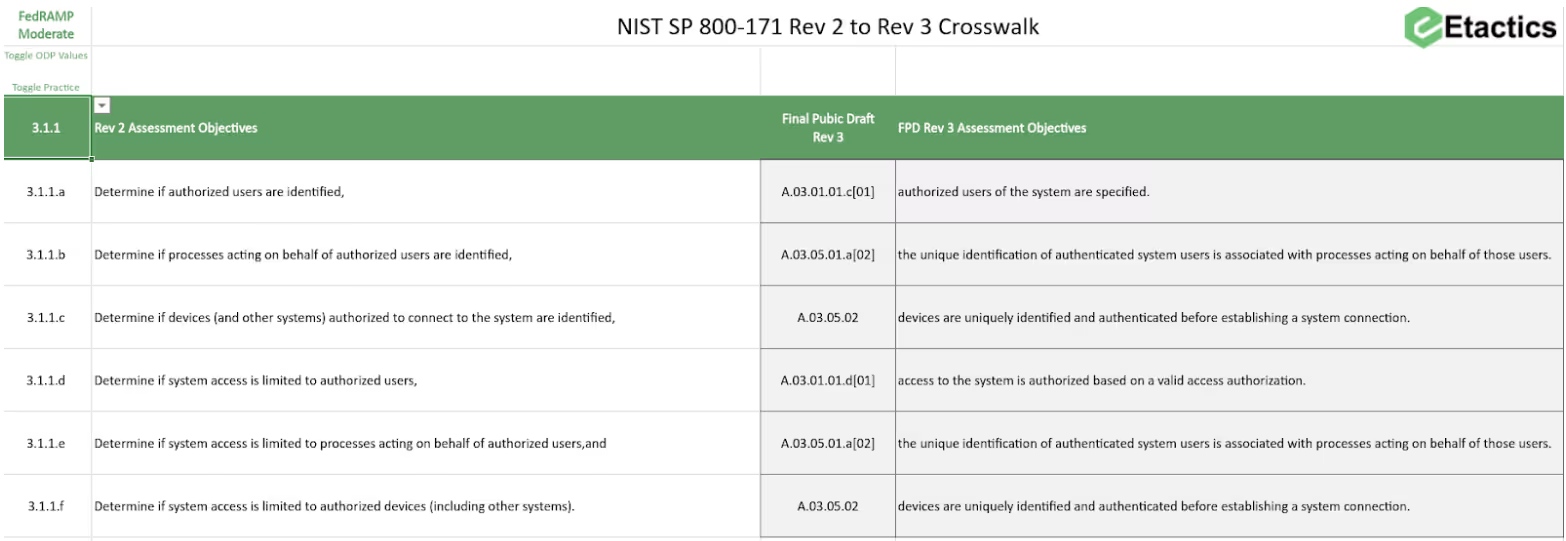
We’ve created a free Rev 3 Crosswalk Calculator. It identifies how the current assessment objectives correspond to the proposed assessment objectives.
Crosswalk Methodology
We published the methodology for creating this crosswalk back in June of 2023. We related the assessment objectives from SP 800-171Ar2 to SP 800-53Ar5. The IPD of Rev 3 maps all security requirements to SP 800-53 controls.
By comparing the control statements of both publications, we derived potential assessment objectives. We have updated the objectives to match those listed in the IPD of the assessment guide.
Key Changes in The Update
Some key changes to note:
- The total number of security requirements decreased by 14% from 110 to 95
- The total number of assessment objectives increased by 40% from 320 to 445
- 291 of the current 320 assessment objectives meet or contribute to Rev 3 objectives
- 29 of the current 320 assessment objectives are now categorized as ORC or NCO
- There are 224 new assessment objectives not traceable to existing objectives
Removed Security Requirements
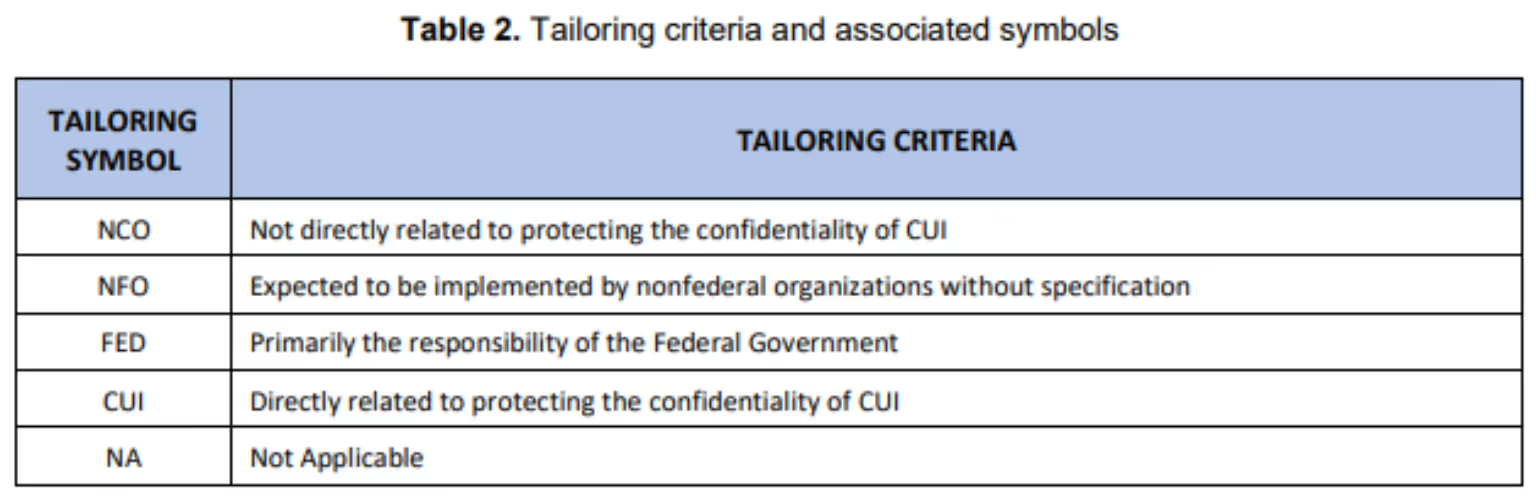
NCO identifies requirements not related to protecting the confidentiality of CUI. The IPD used the NCO tailoring criteria to remove three existing security requirements. NIST removed one other requirement that was technology-specific.
- 3.5.6 Disable identifiers after a defined period of inactivity. (NCO)
- 3.5.8 Prohibit password reuse for a specified number of generations. (NCO)
- 3.7.1 Perform maintenance on organizational systems. (NCO)
- 3.13.14 Control and monitor the use of VoIP technologies. (Technology-specific)
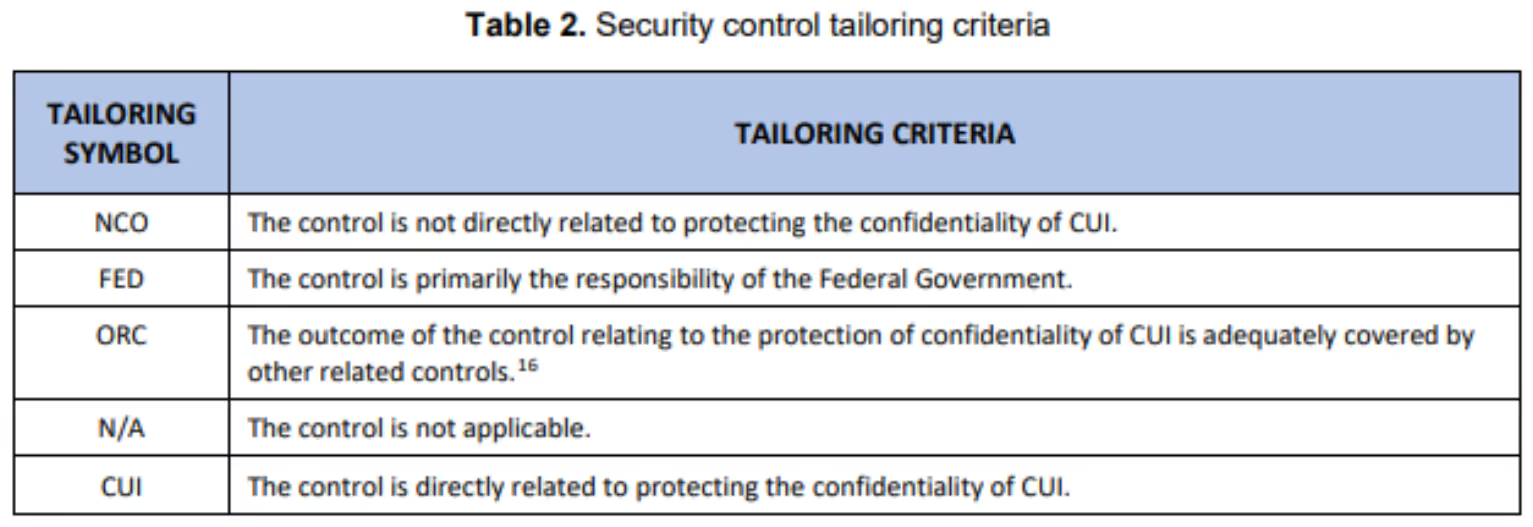
The FPD introduced a new tailoring category called ORC. ORC identifies requirements addressed by other related controls (ORC). NIST removed three existing security requirements using this tailoring category:
- 3.4.9 User-Installed Software (ORC)
- 3.13.3 Separation of System and User Functionality (ORC)
- 3.13.7 Split Tunneling (ORC)
Consolidated Security Requirements
The initial public draft incorporated 23 existing security requirements into other requirements:
3.1.13 Incorporated into 3.1.12.
3.10.3 Incorporated into 3.10.7.
3.1.14 Incorporated into 3.1.12. 3.10.4 Incorporated into 3.10.7.3.1.15 Incorporated into 3.1.12. 3.10.5 Incorporated into 3.10.7.3.1.17 Incorporated into 3.1.16.* 3.11.3 Incorporated into 3.11.2.3.1.19 Incorporated into 3.1.18.
3.12.4 Incorporated into 3.15.2.
3.4.7 Incorporated into 3.4.6.3.13.2 Incorporated into 3.16.1.**3.5.9 Incorporated into 3.5.7.3.13.5 Incorporated into 3.13.1.3.5.10 Incorporated into 3.5.7.
3.13.16 Incorporated into 3.13.8.
3.7.2 Incorporated into 3.7.4 and 3.7.6.3.14.4 Incorporated into 3.14.2.3.7.3. Incorporated into 3.8.3.3.14.5 Incorporated into 3.14.23.8.6 Incorporated into 3.8.5.3.14.7 Incorporated into 3.14.63.8.8 Incorporated into 3.8.7.
* NIST tailored 3.1.17 out as ORC in Rev. 3 FPD
** NIST tailored 3.13.2 out as NCU in Rev 3 FPD
The final public draft incorporates another three existing security requirements into other requirements:
- 3.1.21 External Systems – Restrictions on Authorized Use (Incorporated into 03.01.20)
- 3.2.3 Advanced Literacy Training (Incorporated into 03.02.01)
- 3.3.9 Audit Information Access (Incorporated into 03.03.08)
New Security Requirements
The initial public draft proposed 26 new requirements. The final public draft removed 10 of these proposed requirements.
- 3.1.23 Account Management – Inactivity Logout (removed as ORC in FPD)
- 3.4.10 System Component Inventory
- 3.4.11 Information Location
- 3.4.12 System and Component Configuration for High-Risk Areas
- 3.5.12 Authenticator Management
- 3.6.4 Incident Response Training
- 3.9.3 External Personnel Security (removed as ORC in FPD)
- 3.10.7 Physical Access Control
- 3.10.8 Access Control for Transmission and Output Devices
- 3.11.4 Risk Response (removed as ORC in FPD)
- 3.12.5 Independent Assessment (removed as NCO in FPD)
- 3.12.6 Information Exchange
- 3.12.7 Internal System Connections (removed as NCO in FPD)
- 3.13.17 Internal Network Communications Traffic (removed as ORC in FPD)
- 3.13.18 System Access Points (removed as ORC in FPD)
- 3.14.8 Spam Protection (removed as ORC in FPD)
- 3.15.1 Policy and Procedures
- 3.15.2 System Security Plan
- 3.15.3 Rules of Behavior
- 3.16.1 Security Engineering Principles (removed as NCO in FPD)
- 3.16.2 Unsupported System Components
- 3.16.3 External System Services
- 3.17.1 Supply Chain Risk Management Plan
- 3.17.2 Acquisition Strategies, Tools, and Methods
- 3.17.3 Supply Chain Controls and Processes
- 3.17.4 Component Disposal (removed as ORC in FPD)
The final public draft added two new security requirements:
- 3.16.1 Acquisition Process
- 3.14.8 Information Management and Retention
Security Requirement Summary
Here is a summary of how we went from 110 to 95 security requirements over the course of these drafts:
110 Security Requirements in Rev 2
- 4 requirements removed from the IPD
- 23 requirements consolidated in the IPD
+ 26 requirements added to the IPD
109 Security Requirements in Rev 3 IPD
- 3 requirements removed in the FDP
- 3 requirements consolidated in the FDP
- 10 new IPD requirements removed in FPD
+ 2 requirements added in the FDP
95 Security Requirements in Rev 3 Final Public Draft
Between both drafts, NIST consolidated about 24 requirements. Another 24 requirements had objectives added based on the tailoring of SP 800-53. So although the number of requirements decreased, there are 40% more assessment objectives.
Organizational Definied Parameters (ODPs)
Although the term organization-defined parameter (ODP) is new to NIST SP 800-171, the concept is not. ODPs use assignment and selection operations to specify parameter values. There are 56 organization-defined parameters within the 445 assessment objectives. NIST eliminated ODPs when they did not impact the security requirements.
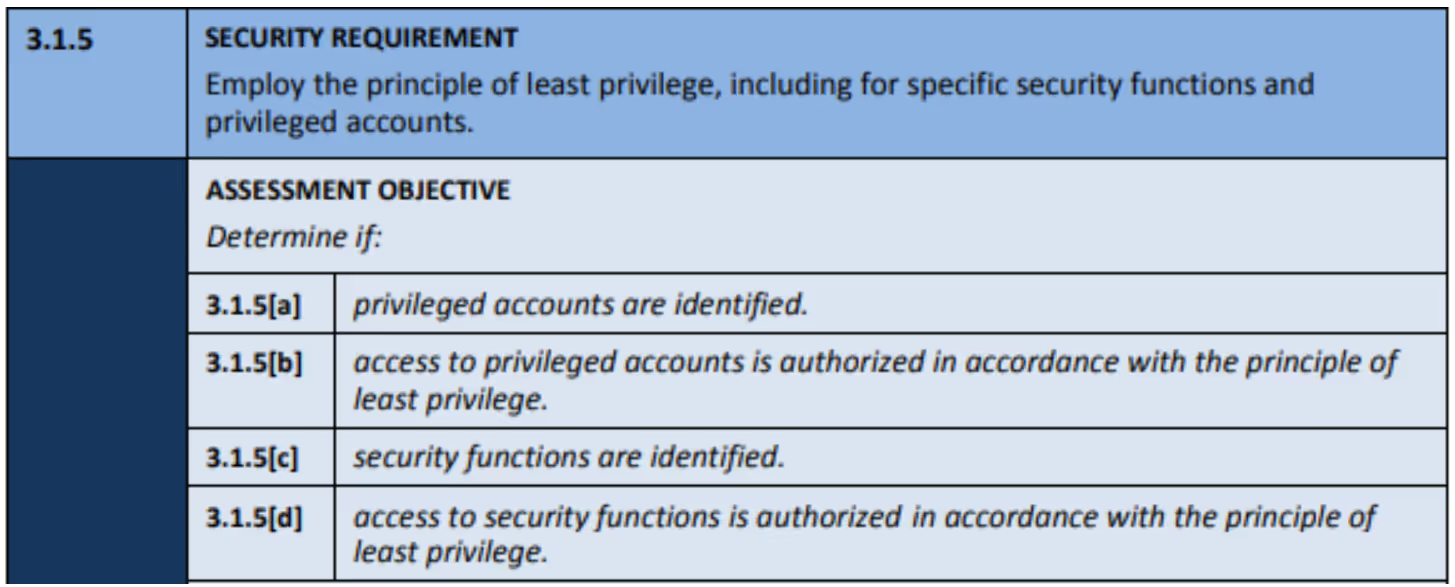
Roughly half (26) of the FPD ODPs align with existing assessment objectives. For example, A.03.01.05.ODP[01] requires defining security functions for authorized access.

The existing assessment objective 3.1.5.c requires the identification of security functions.
If we use the crosswalk from SP 800-171 to SP 800-53, we can define 23 of 56 ODPs using the FedRAMP Moderate Baseline. The FedRAMP High Baseline defines two more ODPs not defined in the Moderate Baseline. We included the ability to incorporate either FedRAMP baseline into our crosswalk calculator.


It is possible that Federal agencies may specify some ODPs. For example, 3.13.11 currently requires the use of FIPS-validated cryptography. The FPD proposed changing this to have two parts. The first part is an ODP that defines the required type of cryptography. The second part determines the implementation of the defined type of cryptography. The FedRAMP Moderate baseline defines this ODP as NSA-approved or FIPS-validated cryptography.
Applicability
The alignment of SP 800-171 to SP 800-53 harmonizes federal and non-federal standards. The timing of a Rev 3 release is its biggest threat. Many organizations implementing SP 800-171 are within the defense industrial base. They are anticipating a proposed rule for the Cybersecurity Maturity Model Certification (CMMC). CMMC may bring third-party assessment requirements to the NIST SP 800-171 standard.
Currently, the rule resides within the Office of Management and Budget (OMB). Within OMB, the Office of Information and Regulatory Affairs (OIRA) reviews proposed regulations. On November 17, they completed their review of supporting CMMC documents. If CMMC moves forward, when will the DoD update the requirements to Rev 3?
We reviewed the history of DFARS 252.204-7012 and SP 800-171. On December 30, 2015, the DoD updated the DFARS clause. They provided contractors with two years to implement NIST SP 800-171. At the time, SP 800-171 only had 109 security requirements. NIST published Rev 1 in December 2016. In September of 2017, the DoD issued a memo stating:

NIST forecasts publishing the final version of Revision 3 in the first half of 2024. The final CMMC rule is not expected until the second half of 2024. Revision 3 will be the standard by the time CMMC requirements enter solicitations. Does that mean CMMC requirements will reflect Rev 3 immediately?
We doubt it. The significant lift going from Rev 2 to Rev 3 will likely provide a grace period. If ever there was a takeaway from this FPD, it is that work towards Rev 2 will largely translate into Rev 3.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)