Human Error and Cybersecurity: 11 Ways People Cause Incidents
Human error from employees is one of the greatest causes of data breaches. The actions of careless staff members can lead to many different violations of government regulations. Here are 11 ways that human error can lead to cybersecurity incidents.

When you think of cybersecurity, you might picture a hacker in a dark room trying to break through your computer’s firewall. While attackers do try to hack healthcare systems, the causes of cybersecurity incidents are often close to home.
Human error from employees is one of the greatest causes of data breaches. The actions of careless staff members can lead to many different violations of government regulations.
Here are 11 ways that human error can lead to cybersecurity incidents.
Granting Incorrect Access
This accidental error is preventable with more attention, caution and by implementing a best-in-class VPN. It might be a long day and whoever is granting permissions isn’t quite focused. Because of this, they grant access to the wrong person.
They might give access or send personally identifiable information (PII) to the wrong person. And while the recipient of this access might not even abuse the data, it’s still a violation.
It’s even worse to send PII or other sensitive data to someone outside of the company because there’s an even greater loss of control. The account won’t have the same level of protection, and the receiver has no obligation to protect the information.
Again, this individual might not abuse the data. But if their account doesn’t have protection and a hacker gets into it, then they could steal and use the information.
Uploading the Wrong Files
Not only do incidents occur from employees sending data to the wrong individual. But employees might send the wrong file altogether.
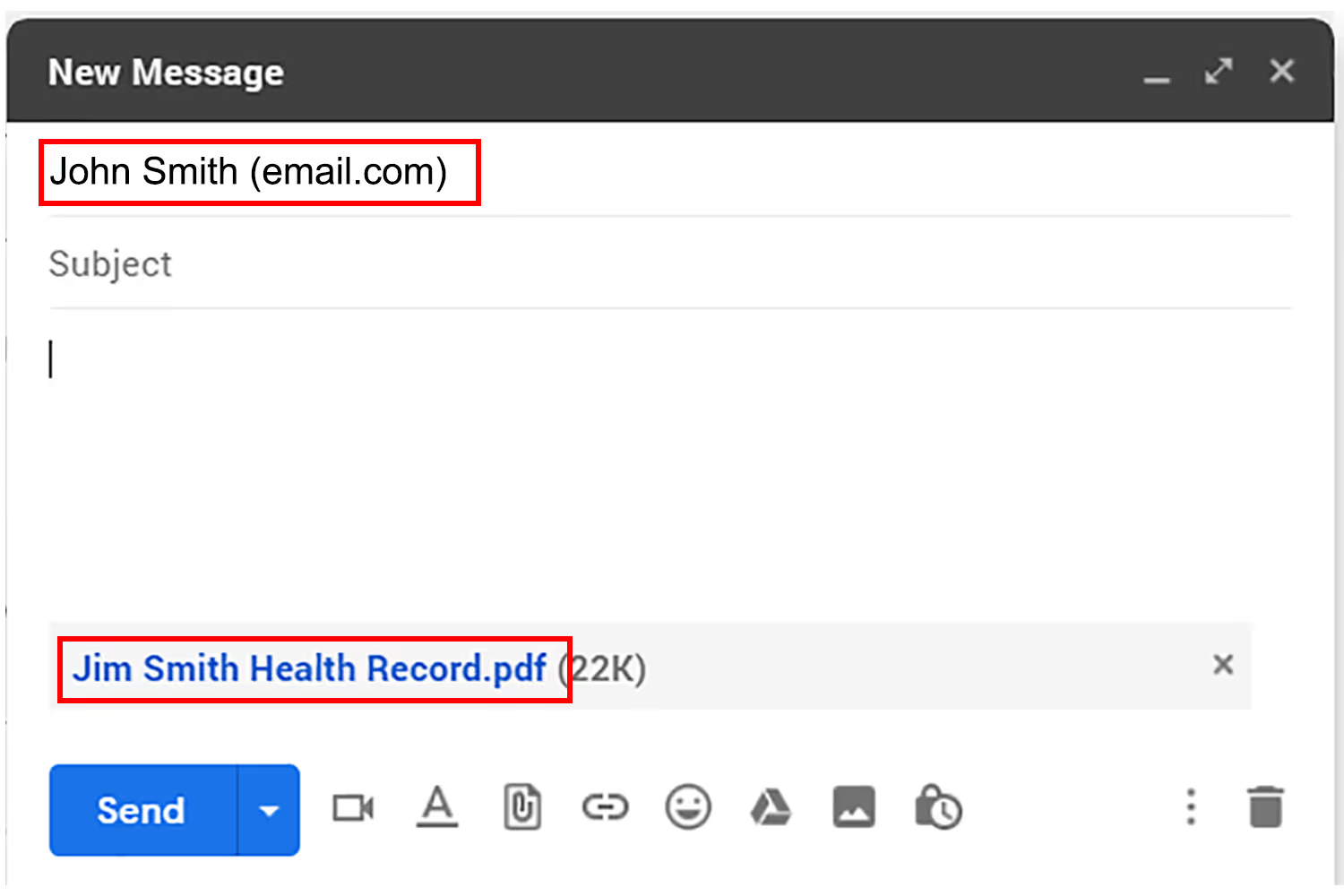
For example, employees might upload an incorrect file to an email. Always double-check that any attached files don’t contain information that the recipient shouldn’t have access to. And make sure that the file uploaded is the correct one before clicking send.
Sending Unencrypted Data
Your organization should always encrypt sensitive data, especially when sending it. Encryption scrambles the information, and it requires a key to decrypt. This way, if unauthorized individuals intercept or receive the data, it’s useless without the key.
Sharing Passwords
The purpose of a password is to protect accounts. Employees should never share their account passwords, especially with those who shouldn’t have access to sensitive data. But this applies even to coworkers who have access to the same information.
The more people who have access to an account, the more risk associated with it. There’s less control over signing out of the account if it’s on many devices. It also poses a higher risk if a device gets lost or stolen.
Activity with Phishing Attempts
This error occurs when employees are negligent with the emails they receive. Hackers disguise themselves as trusted individuals to make an email look legitimate. They do this to trick employees to send sensitive information that they can use for personal gain.
Or, they include links and attachments that the employee believes are safe. But once clicked, it leads to harmful downloads such as viruses or malware that the hackers use to get into the systems and steal data.
Kalamazoo College was victim to a phishing scam that led to the leak of 1,600 IRS W2 forms. A college employee received a phishing email that appeared legitimate requesting these forms. The employee then attached and sent the W2s of students, faculty, and staff.
This is why employees need training on how to handle phishing attempts. They should always look at the sender’s email address to confirm that the sender isn’t impersonating a trusted individual. Employees should also check the URL to make sure it’s safe before clicking it. They should never download an attachment that they weren’t expecting.
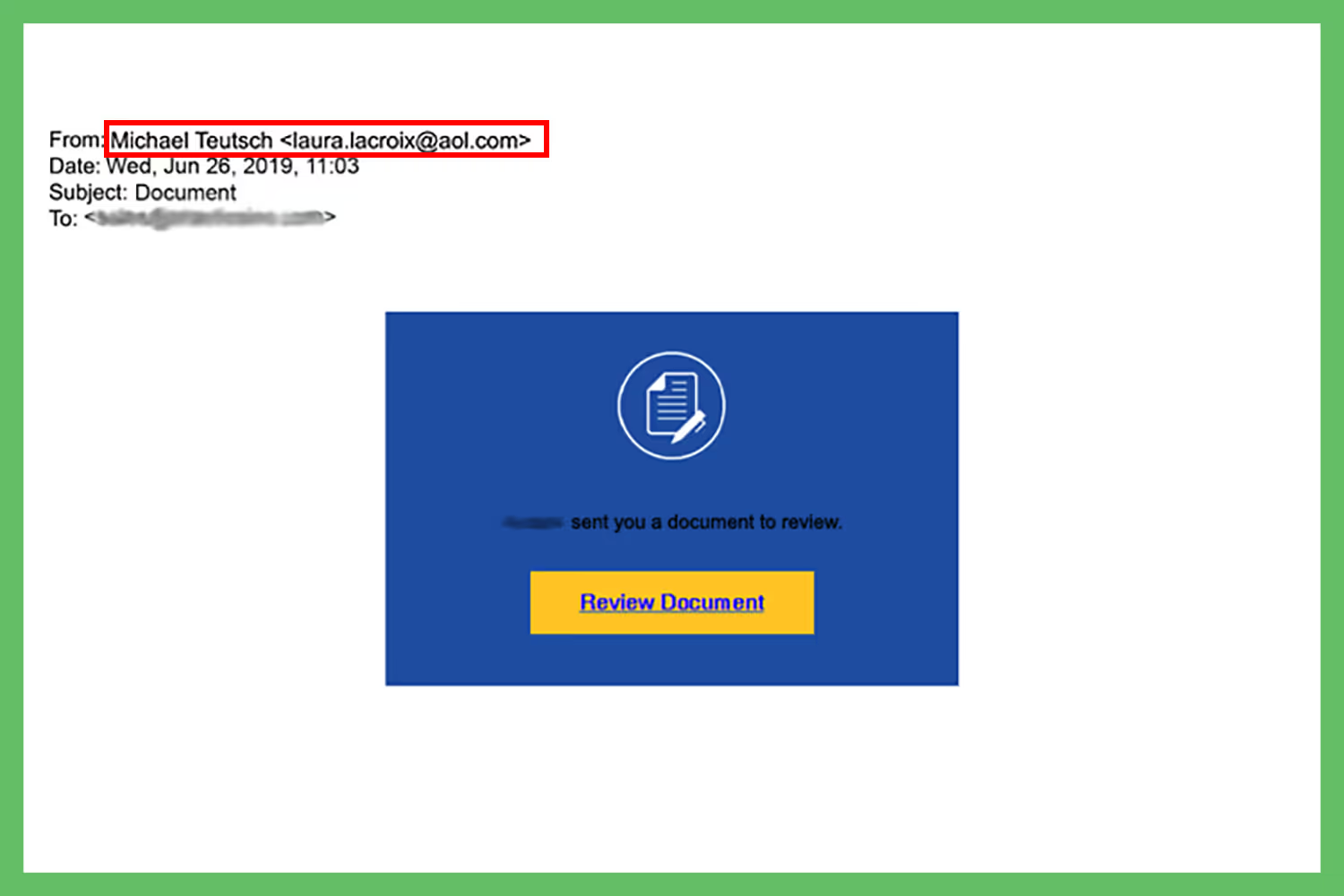
Always mark these emails as spam and report them to management. Hackers may try to phish multiple employees in hopes that one of them will fall for the bait. But making everyone aware of these attempts warns employees to be cautious of incoming emails.
Neglecting Updates
Every so often, your company will need to make updates to systems and software. Some systems may stop working, no longer protecting against hacks unless updated.
It’s important to improve outdated systems immediately. Hackers want to exploit any and all vulnerability, so organizations are more likely to suffer a breach the longer they wait.
The major 2017 Equifax breach occurred when the company failed to apply a patch that would protect against a vulnerability in the system. As a result, hackers breached the information of over 145 million Americans.
Staying on top of system updates is necessary to avoid potential attacks. Hackers know that there are vulnerabilities, so they’re watching for them. If you’re quick to update systems, then there’s a less likely chance for a breach. This is why it’s so important to send risk assessments to pinpoint vulnerabilities so your practice can resolve them.
Lost or Stolen Devices
It’s difficult to prevent a stolen device, and accidents happen that lead to lost devices. So put safeguards in place to prevent theft of information from in both of these scenarios.
All hardware and software should require passwords as the first level of protection. Sign out of all accounts on devices so that no one can steal information from them. If you stay signed in but your device goes missing, someone could use your account to request information from another employee.
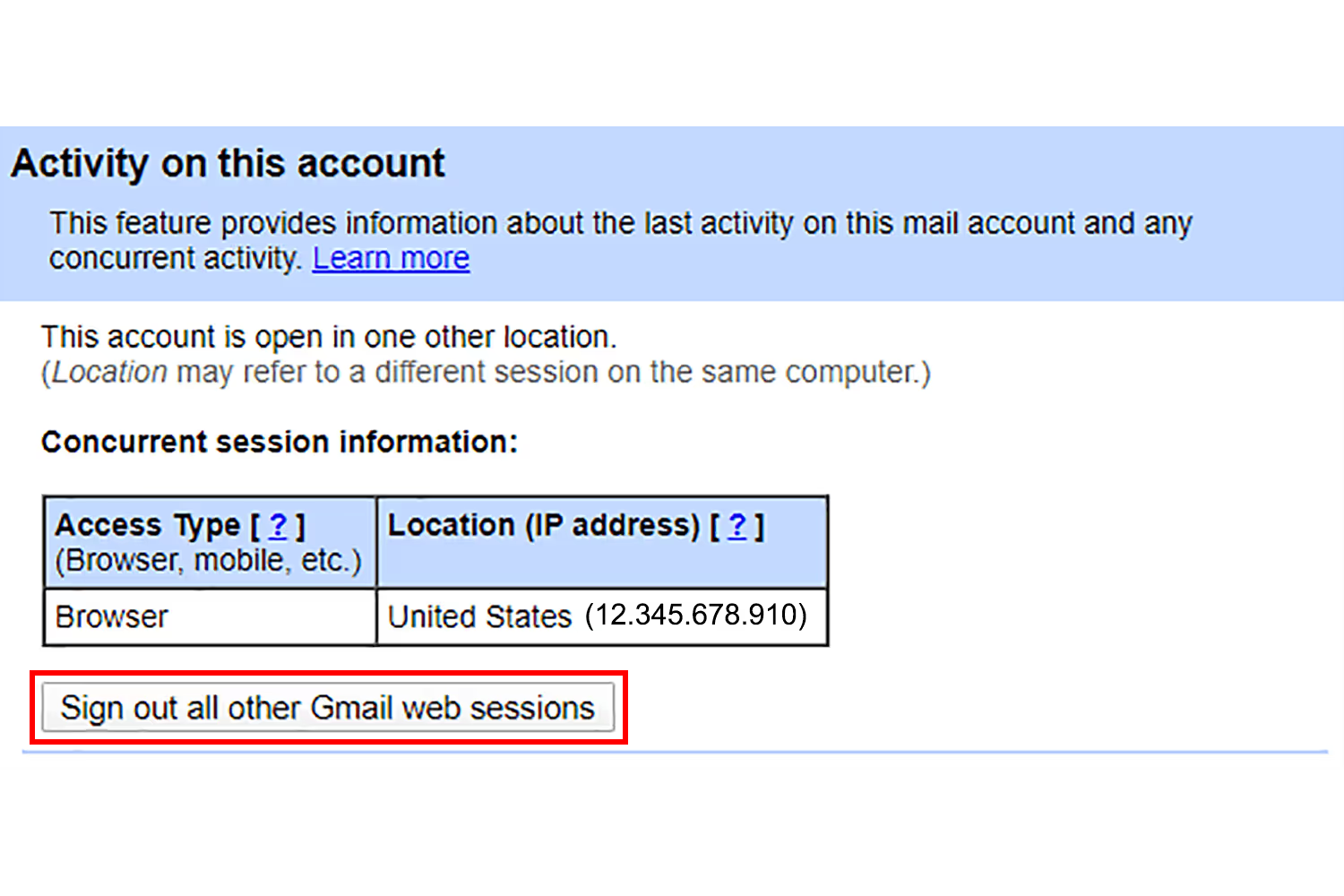
Beyond signing out, if your device goes missing you should also change your passwords as an extra precaution.
This is another instance where having encryption is important. It’ll be impossible for anyone to access or steal information from your device if the data requires a key. By taking precautions before a cybersecurity incident even happens, you’ll save yourself when it does.
Improper Disposal of PII
To protect PII, paper and electronic information needs disposed of properly. Destroying all information to the point where it’s unreadable is the only way to ensure that no one else can access it after disposal.
This means shredding or burning any paper records and destroying the hard drives of electronic devices. While the device might no longer turn on, the hard drive could be in perfect shape and containing plenty of data that someone could steal.
Luckily, many government offices define guidelines and requirements for disposing of sensitive information. As an example, the U.S. Department of Health and Human Services spells this out for healthcare organizations.
Mishandling Data
We already mentioned mishandling data by sending information to the wrong person or from losing devices. But there are other ways that data can fall into the hands of those without authorization.
Paper records could end up misplaced in an exam room or left on a desk where anyone could access them. Always put papers away such as in a locked filing cabinet so not just anyone can get ahold of them.
The same applies to electronic devices containing sensitive information. Employees should never leave a computer unlocked if they leave the immediate vicinity. Anyone who walks by could access their account, which also makes it difficult to know who compromised the data. If it happens under the employee’s credentials, it will seem that they accessed the data. But if they were away from their desk, then it could have been anyone.
Abusing Privilege
A lot of incidents occur simply from abusing the privilege of having access to sensitive information. Individuals may only access information if they have the authorization to do so. But some employees don’t follow this and still access it anyway just because it exists.
One reason this happens is curiosity. A good example of this is when a celebrity patient checks into a hospital. When this happens employees sometimes access records out of interest.
They may have no intention to use the information, but only want to know the details of the patient’s condition. This is still a violation if they don’t have a legitimate reason for accessing the data. Employees may tell family, friends, or other coworkers about a patient’s condition after looking at records.
Even if you trust the person, you should never abuse the power of having this information since you don’t know who they might tell.
Some employees may not know what isn’t permissible for accessing information. They might not realize the criteria for proper authorization to access records. They also may not know that it’s a violation to share sensitive information.
But some intentionally abuse their privilege. If employees lose their job, they could expose PHI out of spite against the practice. This is why it’s important to immediately remove a terminated employee’s access to accounts.
Another serious abuse of privilege is selling PHI for personal gain. This could be from selling information on the dark web or selling to tabloids especially for celebrity patients.
Bring-Your-Own-Device
Some organizations have a policy where employees can use personal laptops, phones, or tablets at work. Without proper security, this poses so many risks.
Devices without proper protection make it easier for hackers to enter the network and compromise data. They’re also more susceptible to someone stealing data if lost or stolen.
It’s also a risk since the devices are traveling back and forth from the office. Taking home devices that contain PII is a risk once it’s on a different network without the same level of protection.
While these policies can save time and money, it’s important to consider any vulnerabilities. That way, proper security measures are in place for all devices and your practice mitigates risks.
Conclusion
Hackers will always try to attack organizations, but many security incidents are the result of human error. We’re all human and make mistakes, they’re inevitable.
This could be due to improper training, carelessness, or abusing power. Whatever the reason, organizations must do all they can to mitigate the risks since human error is more difficult to control.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)