7 Phishing Email Examples From Our Own Inbox
Here are a few phishing email examples and tactics that came straight out of our own inboxes. Luckily, none of these examples led to a breach or malicious attack.
Phishing is an attempt to access sensitive information by using fraudulent emails. Hackers use different social engineering tactics to get a receiver to reply or click a link so that they can gain access to computer systems.
Many of these emails will end up in your spam folder because the sender is outside of your domain, there’s a misleading subject line, or it’s from a sender who you don’t already engage with.
But sometimes these emails don’t filter into spam folders. If your employees engage with these attackers, a few things could happen…
- They’ll get scammed out of a couple of dollars
- They’ll willingly give up their personal information
- The attacker will gain access to their system and inject a ransomware attack
Here are a few phishing email examples and tactics that came straight from our inboxes. Luckily, none of these examples led to a breach or malicious attack.
Simple Requests to Build Trust
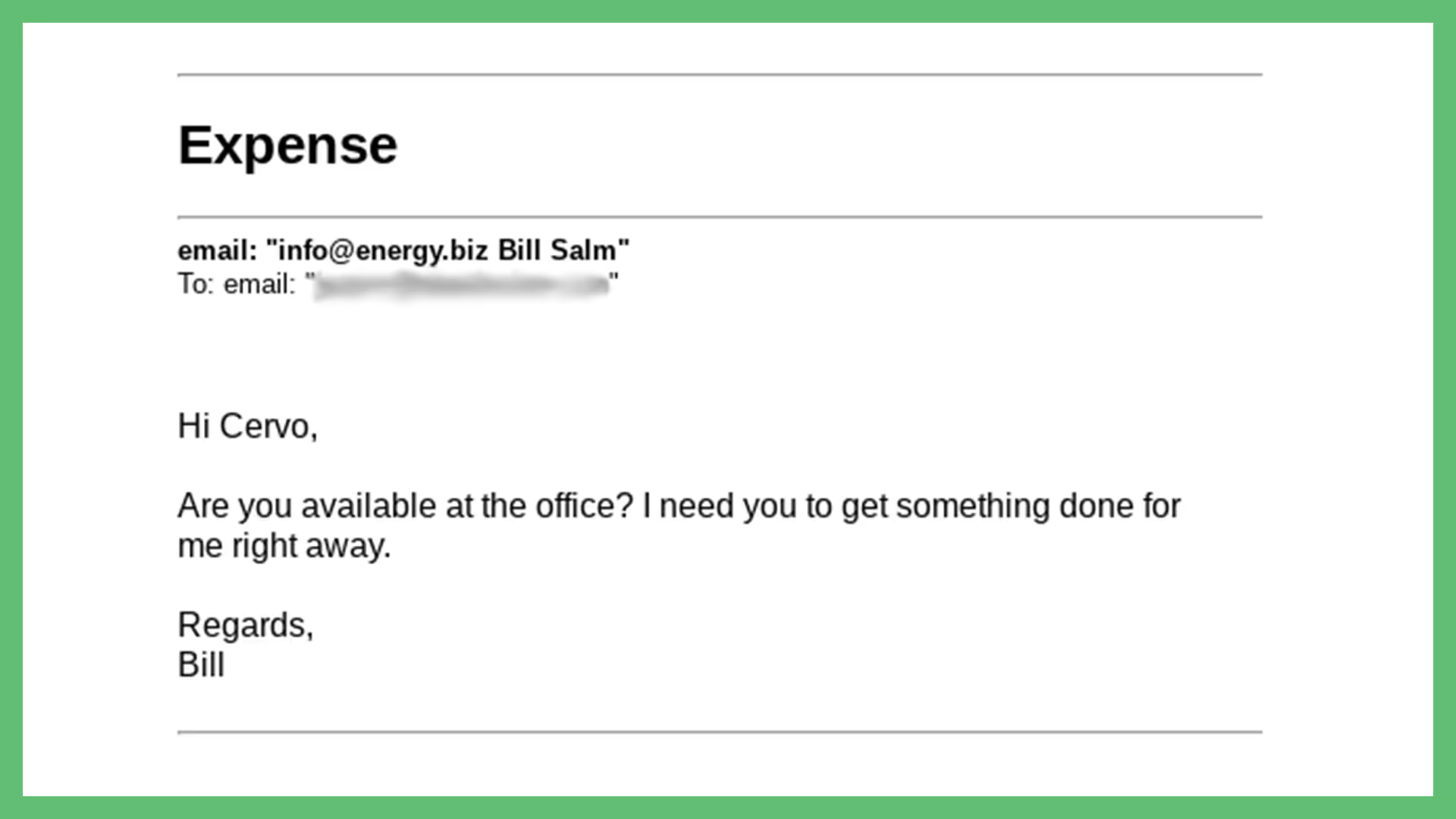
Some hackers attempt to build trust by using the names of your company’s trusted employers. But the email address is different than your employer’s work email address.

This email appeared to be from our CEO when it reached our inbox. It also contained a very generic subject line. Once opened, our users had to look closer to realize that the name didn’t match with the email address.
This was the trickiest phishing attempt we received this year. In some cases, malicious emails contain a lot of typos and grammatical errors. In this example, the email didn’t contain any grammar errors but rather one formatting issue; no space between the comma.
Even with that error, the attacker included the ever-popular “Sent from my iPhone” phrase at the end of the email. They added that phrase to the email so that the recipient was more likely to excuse any formatting problems.
Another interesting takeaway from this example is their initial request. The attacker’s asking for the victim’s personal cell phone number. They’re asking for this to make the attempt more elaborate. Their hope is that the victim doesn’t have their boss’s phone number. Moving the initial conversation away from email makes it harder for the victim to realize it's malicious.
Even if you recognize the sender’s name, always check that the email address is the one you trust, especially if the email is out of the ordinary.
Phishing emails don’t always include malicious links. Oftentimes they’re trying to get potential victims to engage. Both this attempt and the one before it used this social engineering approach.
If the recipients in these examples responded, there wouldn’t be any immediate effect. The attacker would respond impersonating one of our senior managers.
In most cases, these attackers ask for the “favor” of purchasing gift cards and send them the codes. They’ll usually state that they need it to finish a big project to make it seem like you’re contributing to the team.
Email Provider Warning
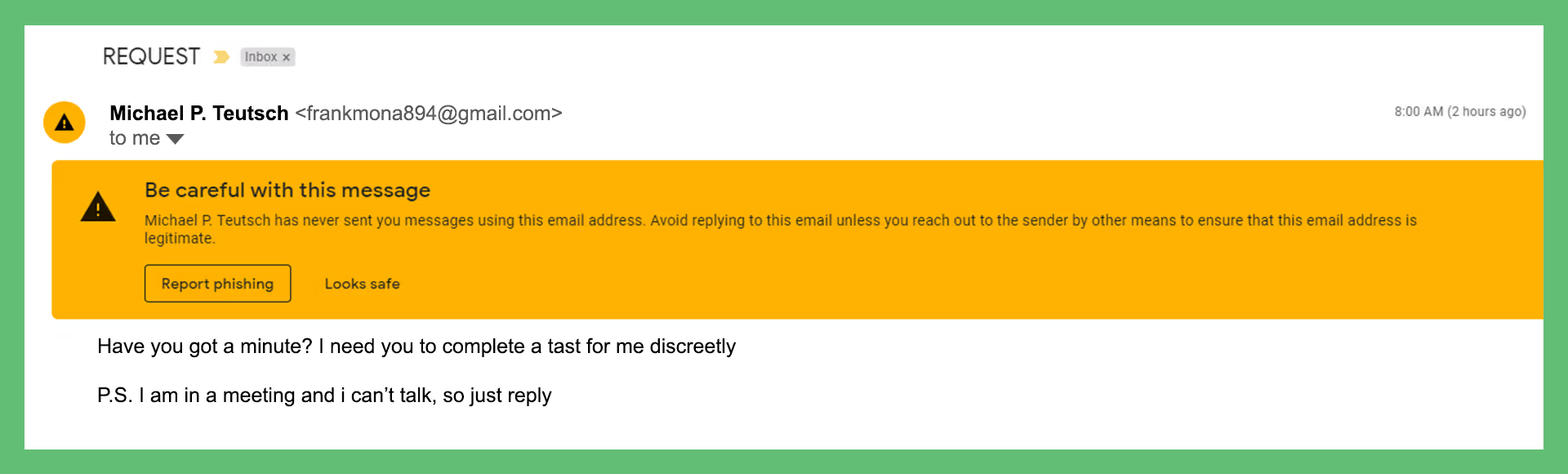
Sometimes your email service will tip you off that an email might be malicious. They do this by displaying a banner a bright-colored banner before the body. This warning banner told our employees to proceed with caution.
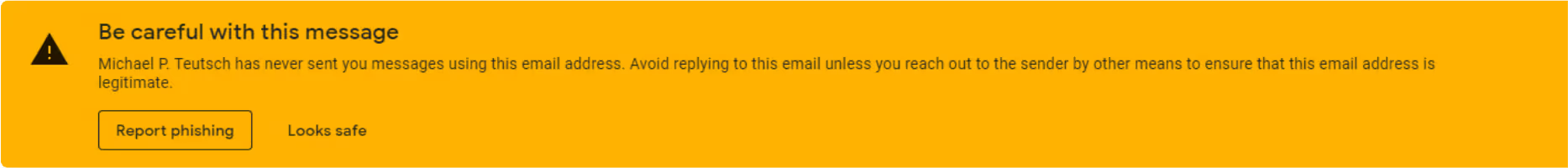
Hackers sometimes pretend that they’ve already communicated with you in the past to generate engagement. It’s hard to remember all the hundreds of emails we receive every day. If they take this approach, they’ll act as if they’re following up from a previous conversation.
Maybe they’ll say that you’re eligible for a deal they’re offering and that you need to contact them for more information. This is one of the most classic plays by attackers.
Malicious Links
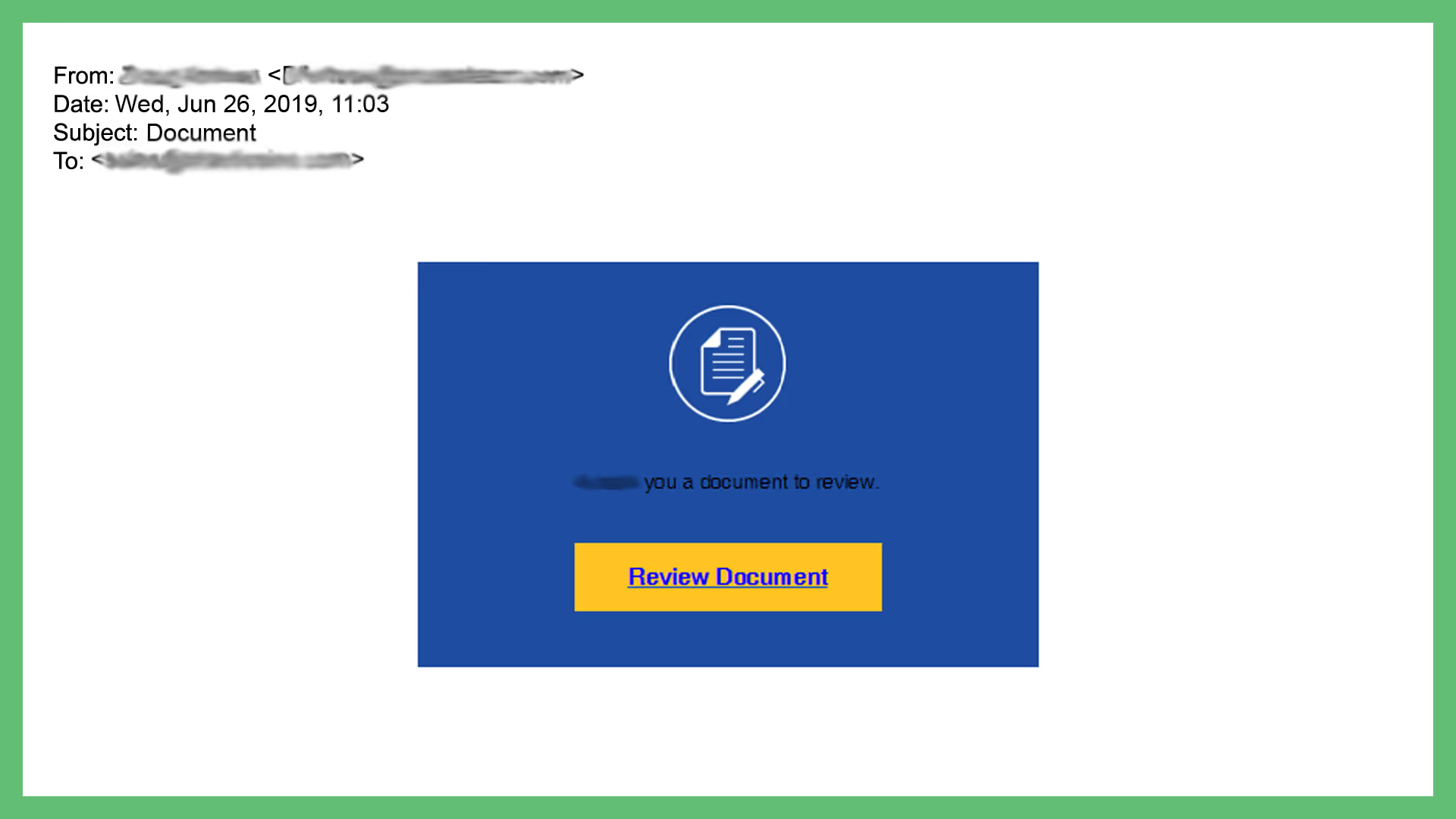
The example above was from a legitimate company. For their sake, we blurred out their contact information.
One of their employee’s email addresses fell victim to a hack. This hack took over their email and sent out more malicious content to their entire list of contacts. The attacker disguised the link as much as possible to make it seem legit.
Clicking on the link led to a fake login form that asked users for their passwords.
A few minutes later, this company’s IT department responded to all recipients.
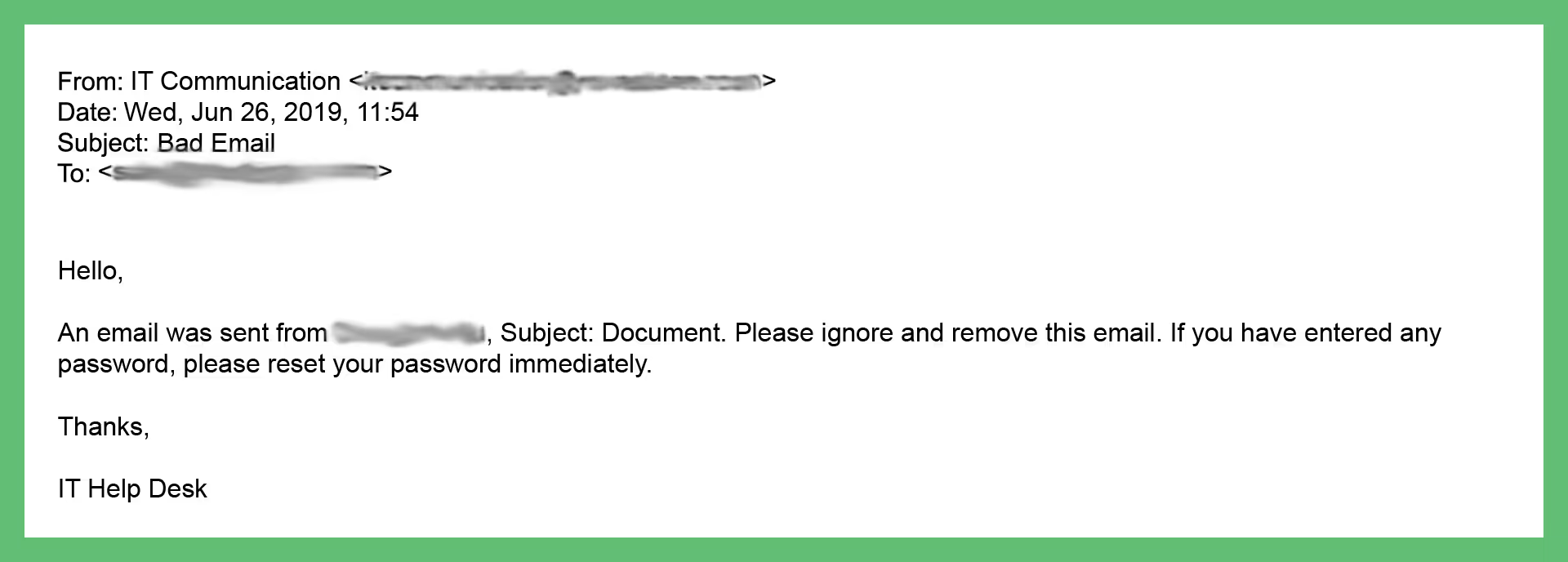
In this instance, the company’s IT department acted fast. Only 51 minutes passed before they realized the attack and responded.
Sometimes, employees mindlessly click on the links within malicious emails without even realizing it. Clicking on the link within a phishing email is a worst-case scenario.
Who knows what’s behind that linked text. It could be…
- A malicious executable file that will lock your system and devices
- A fake survey form that asks you to enter personal information
- A form of spyware that lays dormant and tracks everything you do on your device
Shock Value and Scare Tactics
Sometimes attackers use shock value to try to reach engagement. One popular strategy that they’ll use in this scenario is blackmail.
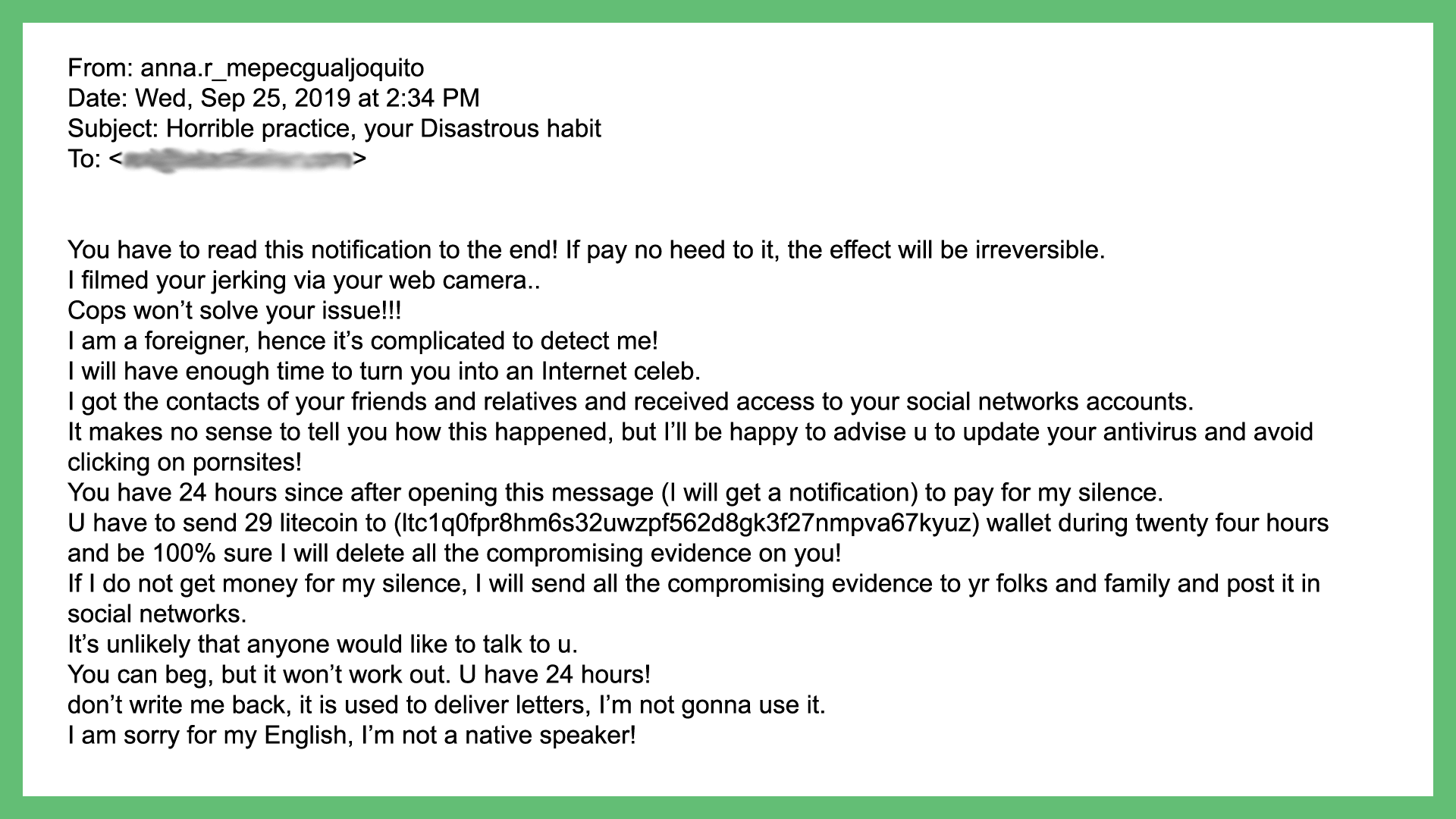
The example above is terribly formatted and threatening. They also tried to make our users feel useless by saying their only option was to pay them. This attempt was sent to one of our general email addresses used by multiple people. It was also highly inappropriate.
Even worse, attackers will use scare tactics that falsely threaten lives. If you believe there’s a real danger, you may act out of fear without first determining if the email is legitimate.
Most often, threatening phishing emails will request some form of payment through blockchain. They do this because it’s untraceable. Threatening anyone in this way is harassment and illegal so they request blockchain as a way to make their crime untraceable.

Outside of their threatening nature, both of these attempts use a similar format…
- Threat
- If you try anything other than paying, you’ll lose
- Pay using this link
- Specified timelimit to induce panic
- Odd disclaimer
If you’re ever faced with a threatening email and believe that it might be real, reach out to your local law enforcement.
Conclusion
Email services will typically filter dangerous emails into spam folders, but that isn’t always the case. Always check that the email address is one that you trust before replying or clicking any links.
If the email is suspicious, contact your compliance officer. Flag these emails as spam, too, so that in the future they get sorted into your spam.
Not all emails that go to your spam folder are phishing attempts, but be cautious when clearing it out. Don’t reply and don’t click their links.
Poor judgment with skeptical emails could hurt your company if attackers gain access to computer systems.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)