Ransomware: How to Avoid it and Protect Yourself
Ransomware is one of the newest, most trendy types of cyber attacks that hackers rely on to trick companies into paying them money. Here’s how to avoid them yourself.

According to a survey by Sophos, 66% of healthcare organizations report experiencing a ransomware attack in 2021. This was a 34% increase from 2020. In just one year, that is a 94% increase in cybercrime.
Ransomware is a fast-growing form of malware that can cost your business large sums of money if no prevention plan is in place. In fact, only 50% of small US businesses have a cybersecurity plan. That leaves companies open to large financial losses.
No company is immune to the devastating repercussions of ransomware attacks. Take for example the attack on Colonial Pipeline. This multi-billion dollar energy company lost $4.4 million to a ransomware attack in 2021. More on that later.
So what is one of the biggest risks when it comes to falling victim to a cybersecurity attack? 82% of data breaches involve a human element, according to Verizon’s 2022 Data Breach Investigation Report.

It comes down to people like you and me, which is both a good thing and a bad thing. Bad because who wants that kind of pressure? I know I sure don’t want to cost the company I work for millions of dollars. But, the good news is that there are simple ways we can prevent errors and misuse of company information. Your first line of defense starts with your employees.
What is Ransomware?
We should go over what ransomware is before getting into the nitty-gritty details.
Ransomware is a form of malware that targets home users, businesses and government networks. This type of cyberattack denies users access to files on their computers. Hackers then keep these files until the victim pays a set ransom for their return.
This can lead to…
- Permanent loss of sensitive or proprietary information
- Disruption of regulation operations
- Financial losses incurred to restore systems and files.
In the case that an attack is successful, the screen of the infected device will usually provide instructions for the victim to follow.
Yes, this can include a countdown timer to prompt action or else risk losing data. Even though that sounds like something out of a movie, it does happen.
Ransomware Techniques
I wish I could be the bearer of good news, but unfortunately, things tend to get worse from here.
Ransomware attacks can happen to anyone.
What that means is that hackers aren’t focused on a specific industry, but instead on how much money a company is willing to pay to get their data back.

The steps after a hacker successfully infect a system are encryption, data theft, and communication. Let’s go over each of these steps.
Encryption is the practice of denying users access to their data. By doing this, a hacker can then demand payment. This is what makes a piece of malware “ransomware”.
To help incentivize victims to pay the ransom, most ransomware variants now include a data theft component. This means that ransomware will search for valuable data and send copies to the attacker before encrypting the files.
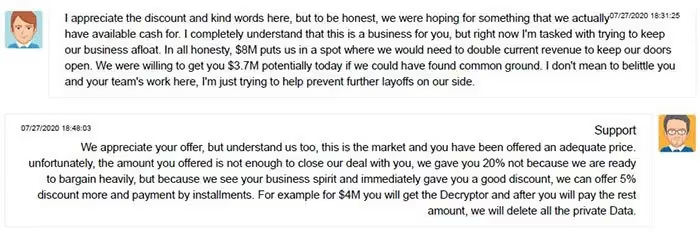
The last component, communication, is pretty self-explanatory. Once the hacker gathers all your data and locks your systems, they’ll usually place a chat window on your screen to communicate with them.
A good example of this step happened when aviation company, CWT Global fell victim to a ransomware attack back in 2020. Hacker group, Ragnar Locker, shut down CWT Global’s entire system, except for making a chat window. Although CWT Global was able to negotiate down Ragnar Locker’s initial $10 million ransom, the organization still forked over $4.5 million to the group.
There are different kinds of ransomware techniques to look out for. One of the most common techniques you may have heard of already is phishing. There is also exploiting poor access management, exploiting unpatched vulnerabilities, “drive-by” downloads, and physical devices.
Phishing
Last year 83% of businesses said they experienced a successful phishing attack, according to a Proofpoint report.
Phishing is the unlawful practice of sending emails while impersonating a company to convince someone to reveal their personal information. This information can include things such as passwords, social security numbers, and credit card numbers.
These emails also use a sense of urgency to prompt users to act quickly without being able to think the decision through.

Exploiting Poor Access Management
Poor access management is another common issue that allows hackers to successfully complete ransomware attacks. Many security breaches come from within a company, so it’s important that your employees only have basic access to the resources required to perform their job.
Avoid having your employees share credentials with each other and have a plan to address access rights for an employee’s tenure.
A few more examples of security risks are; not keeping your accounts up to date, weak passwords, and neglecting to change your passwords.
Keeping outdated accounts that still have access to company systems is an easy entry point for an attack.
On May 7th of 2021, the Colonial Pipeline Company shut down its pipeline system in response to a ransomware attack. The Colonial Pipeline Company provides gas, home heating oil and other petroleum products. Their service extends to communities and businesses throughout the South and Eastern US.
An infamous hacker group called DarkSide preyed on an instance involving the company's poor access management. The group used leaked login credentials for an outdated account to access company information. The login credentials existed on the dark web.
Due to this security breach, the pipeline was offline for 6 days and the company had to pay a ransom of $4.4 million.

Exploiting Unpatched Vulnerabilities
Security is continuously scanning, identifying, and providing the necessary patches around new vulnerabilities.
But, the software will always hold risk in that it is always changing. This is why cybersecurity teams must always address vulnerabilities promptly. Neglecting to address unpatched software allows an easy route for hackers to get your information.
An unpatched vulnerability is any weakness in a system that allows hackers to use a known security bug to run malicious code.
There was a 29% growth in new unpatched vulnerabilities in 2021 according to Ivanti’s “Ransomware Spotlight Year End 2021 Report”. In parallel, 56% of the 223 older vulnerabilities identified before 2021 continued to be active as well.

"Drive-by" Malicious Package Downloads
“Drive-by'' malicious package downloads are…downloads. They happen after a user unknowingly visits an infected website.
Hackers will either embed malicious code in the website or redirect the victim to another site that they control, which hosts software known as exploit kits.
Exploit kits give hackers the ability to silently scan the visiting device for its specific weaknesses. This allows them to execute malicious code without the user even clicking anything.
Physical, Removable Media Devices (USBs)
Sometimes the risk can be right in front of you. Ransomware found in USB and/or removable media is another technique used by hackers.
Many instances have already taken place where hacker groups mailed out USB drives in hopes that recipients would plug them into their PC and install ransomware.
These groups will impersonate legitimate organizations in hopes of gaining a victim’s trust.
Using physical devices, hackers will impersonate legitimate organizations in hopes of gaining information. For example, there have been reports of hackers impersonating the US Department of Health and Human Services. This cybercrime group would gather data by claiming the USB sent was a COVID-19 warning.

Tips to Avoid Ransomware
Here are some of the best practices to protect yourself from a ransomware attack…
- Back up your data and verify its integrity.
- Focus on awareness and training.
- Patch the operating system, software, and firmware on devices.
- Ensure antivirus and anti-malware solutions are set to update and conduct scans.
- Disable macro scripts from Office files transmitted via email.
- Install software restriction policies. This can prevent the execution of programs in common ransomware locations.
- Use best practices for use of remote desktop protocol (RDP). This includes auditing your network for systems using RDP, closing unused RDP ports, and applying two-factor authentication wherever possible.
- Implement application whitelisting. This helps only authorized software to execute on company servers and endpoints.
- Use virtualized environments to execute operating system environments or specific programs.
- Require user interaction for end-user applications communicating with websites uncategorized by the network proxy or firewall.
Conclusion
Ransomware is a growing concern when it comes to cybersecurity. The good news (finally) is that by taking the necessary precautions listed above, you can avoid becoming a statistic!
A 2020 study measured the impact of security awareness training and its lasting effect over time. The results showed that employees forget training over time and subjects that went on longer without retention training performed worse in testing.
Knowing the techniques and strategies that hackers use is a great first line of defense. Knowledge is power as they say. Yet, making sure to offer regular training to your employees is crucial to reduce the risk of a security breach. By offering annual training, employees can be better equipped to prevent ransomware attacks and keep data safe.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




