What is CMMC Compliance: An Authorized C3PAO Perspective
We sat down with a C3PAO, Kompleye, for an interview on what it takes to achieve “CMMC compliance”.

At the time of writing this blog, there are currently 29 CMMC 3rd Party Assessor Organizations (C3PAOs) listed in The Cyber AB Marketplace.
These organizations have passed a third party assessment. In other words, they've verified the implementation of NIST Special Publication (SP) 800-171.
Up to 80,000 contractors and suppliers within the Defense Industrial Base (DIB) will set out to achieve the same in the coming years. I recently had an opportunity to speak with Patricio Garcia, CEO of one of the most recent authorized C3PAOs, Kompleye Attestation
I wanted to learn more about their experience and document lessons learned for the benefit of the community at large.
About Kompleye
Kompleye formed in late 2019. The founders were information security assessors. Ultimately, they wanted wanted to provide a better experience to their customers.
They started by providing SOC 2 services as a Certified Public Accounting firm. That offering evolved into a range of cybersecurity, compliance and assurance services including…
- International Organization for Standardization (ISO) 27001
- Health Information Trust Alliance (HITRUST)
- Federal Risk and Authorization Management Program (FedRAMP)
- StateRAMP
- Security Trust Assurance and Risk (STAR) Program for Cloud Services
- Security Assessment Scheme for Government Information Systems (ISMAP)
The CMMC Compliance Journey
Purpose
Kompleye’s decision to pursue CMMC accreditation had two driving factors.
First, their team had previous experience conducting NIST SP 800-171 assessments. Second, Patricio felt compelled to contribute his skills to increase our national security. He’s a naturalized citizen and his patriotism was a motivating factor in his pursuit to CMMC compliance.
Establishing and Resourcing a Plan
The project plan included several important decisions.
First, Patricio had to find the right person to manage the project. The firm’s leadership was too busy with other projects to lead the effort. So, they prioritized finding the right person. Next, they equipped the project manager with the resources needed to meet the requirements.
Leadership required all stakeholders to respond to requests made by the project manager.
Investing in The Team
The Chief Information Security Officer (CISO) led the project management team.
The Chief Technology Officer (CTO) and two other individuals with information technology and security experience supported the project.
Together, they spent about a year working on implementing and documenting the requirements. They were able to leverage prior technology investments. But, their total labor costs approached $200k for the project.
Applying for Their Assessment
Kompleye submitted their application to become a C3PAO in January, 2021.
They attested that they had a few practices remaining on a plan of action and milestones (POA&M). They didn’t hear back from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) team for the next 12 months.
In February of 2022, they informed the Cyber AB that they had closed out all POA&M items. In March, the Cyber AB scheduled their assessment with the DIBCAC for the last week of September, 2022.
Scoping for The Assessment
The team at Kompleye followed its typical assessment process. It resembled the recently released draft CMMC Assessment Process (CAP).
People
There were a total of six individuals considered within scope of their CUI boundary.
Kompleye employs some non-US citizens abroad. Their non-US citizens couldn’t have access to the sensitive information they would process as a C3PAO.
This created a need for them to create a separate environment (enclave).
Technology
Kompleye’s team looked at how sensitive information would flow within the enclave.
This helped to identify assets (infrastructure, applications, people, etc.). These assets help with sensitive information through…
- Processing
- Transmitting
- Storing
Its environment consisted of two CUI Assets and a handful of Security Protection Assets…
CUI Assets (Process, Store or Transmit CUI)
- Microsoft 365 Government G5
- Endpoints (laptops)
Security Protection Assets
- Anti-malware software
- Endpoint management solution (InTune and Jamf)
- Multi-factor authentication (Duo and Microsoft Authenticator)
Facilities
Kompleye took two steps to limit their facilities scope. First, its technology was cloud-based. Second, Kompleye did not allow printing. Those two considerations meant that none of its facilities were in scope.
Kompleye inherited the physical protection controls from their external cloud service providers.
Planning
They first evaluated the potential to inherit practices from their cloud vendors. They inherited about 20 controls and partially inherited another 75 controls.
These controls leveraged FedRAMP moderate external cloud service providers. After inheriting some practices, there remained a considerable gap of controls to put in place.
They conducted an initial inventory of policies and procedures. Based on the requirements, they created a list of gaps they needed to work towards completing.
Fieldwork
They methodically went through each domain and discussed the implementation of the controls.
When evaluating each practice, they asked the same set of questions…
- What are they doing?
- How are they doing it?
- When are they doing it?
- Who is responsible?
Since their scope included several asset types, detailed procedures sometimes varied by asset. They created work instructions to document these variances within objectives at the asset level.

Reporting
They conducted two mock assessments using external resources.
The external assessors identified some gaps and made recommendations on how to remediate them. Part of the mock assessment was to test each procedure and work instruction.
When DIBCAC scheduled their assessment, they performed a final internal review. They reviewed their responses within the access control and configuration management domains. This review process took two weeks.
In their experience, those domains are more difficult to prove during an assessment.
Expediting The Assessment Through Documentation
Creating a System Security Plan (SSP)
Kompleye wasn't organized and aligned to NIST SP 800-171 prior to its CMMC compliance journey.
Its team created their CMMC SSP by documenting their implementation of the required practices.
They created a separate SSP for their commercial system. They used the FedRAMP template and detailed how they met each requirement at the determination statement level.
Their resulting CMMC SSP was 449 pages long.

They identified whether each practice was internally met, inherited, shared or not applicable.
For example, they inherited all physical protection requirements for their cloud infrastructure. Practices related to wireless access points and mobile devices (phones and tablets) weren’t applicable.
Engagement with The DIBCAC Assessment Team
The DIBCAC assigned a project manager for Kompleye’s assessment.
This individual remained involved during and after the assessment project. They provided a link to Kompleye that facilitated secure submission of their documentation.
DIBCAC also asked them to submit whether each practice was internally met, inherited, shared or not applicable.
Organization of Supporting Artifacts
Kompleye uploaded their body of evidence, including their SSP and information security notebook. The notebook contained all their policies, processes, procedures and work instructions.
The SSP made references to artifacts contained within the notebook for each requirement. The first chapter of the notebook included the following sections…
- Information Security Charter
- Information Security Program Plan
- Timeline and Deliverables
- Information Security Policy
- Program Disclosures
- Information Compartmentalization Policy
- Weekly System Review Checklist
- Quarterly Controls Review
- System Security Plan
- Domain Interdependency Map
- Meeting Minutes (dating all the way back to May 2021)
They organized subsequent chapters following the fourteen domains within NIST SP 800-171.
Within each, the workbook included a policy, related processes, procedures and work instructions.
They depicted processes using simple relational diagrams.
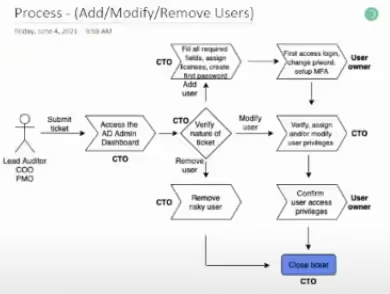
They detailed procedures with instructions describing the activities performed and responsible owners.
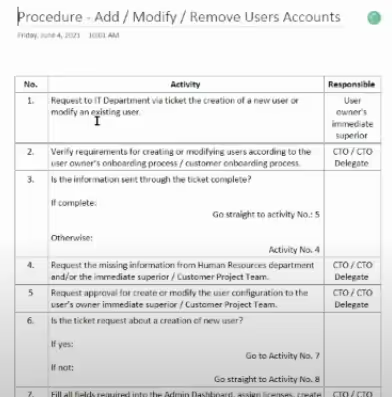
The SSP and notebook expedited the assessment process. Both resources provided the DIBCAC team with a clear picture of how Kompleye implemented NIST SP 800-171. This limited the extent of the actual assessment to verify their processes.
During the assessment, they requested screen shots and conducted interviews. Through this, they verified the Kompleye had implemented their procedures and work instructions.
The Assessment Process
The schedule of the assessment plan included a full week.
Each day included an assessment of specific domains and interviews with various Kompleye team members.
A total of eight DIBCAC team members participated in scheduling and conducting the assessment. The DIBCAC team completed their assessment in two half-days.
On the third day, they reviewed the findings of the assessment with Kompleye.
Lessons Learned
Contractor Risk Managed Assets in DIBCAC Assessment
Kompleye tried to classify its endpoints as contractor risk managed assets.
Thus its team implemented technical controls. These controls disabled the downloading of information on these assets. They identified a risk during a mock assessment that allowed the downloading of information.
Kompleye assessed this as a low risk and proceeded into the DIBCAC assessment with their endpoints listed as contractor risk managed assets. But, classified their endpoints as contractor risk managed assets.
During the readiness review, the DIBCAC assessment team didn’t accept Kompleye’s mitigation of risk on the endpoints. This led to the reclassification of these endpoints as CUI assets and subject to the full breadth of applicable NIST SP 800-171 controls.
We discussed the topic of CRMA through the lens of NIST SP 800-171 in a previous blog.
SC.L2-3.13.3 - Role Separation
Kompleye’s privileged user accounts in Microsoft 365 each had a license. Those licenses provided access to Microsoft applications that could access CUI.
A potential threat would involve a privileged user receiving an email that compromised the system. Thus, Kompleye implemented technical controls. These controls blocked privileged user accounts from receiving emails to mitigate this threat.
To the team’s surprise, blocking access to these applications didn’t mitigate the risk. Privileged user credentials could still access these applications through a web browser.
The solution was to unassign licenses to privileged users. That way, they didn't have any Microsoft products associated with them. They assigned a separate account to the privileged users for operations purposes.
This satisfied objective (c) which requires separating user functionality from system management functionality.
FedRAMP Approved Security Protection Assets
During the fieldwork phase, Kompleye documented the inheritance of practices. Its team discovered that one of their cloud-based security protection assets was not FedRAMP moderate.
Looking back, they should have identified this during the planning phase. They had to find another solution to provide those security capabilities.
RP vs CCP Training
Two of Kompleye’s team members took a Certified CMMC Professional (CCP) training course from a Licensed Training Provider (LTP).
Prior to that training, the team had also taken Registered Practitioner (RP) training.
After the release of CMMC 2.0, the LTP and Cyber AB delivered updated Delta training. The most relevant material in preparing for the assessment actually came from the Cyber AB provided Delta RP training.
Importance of Having an External Assessment
External assessors are more likely to find overlooked issues.
There’s a higher degree of impartiality using external assessors.
When hiring external assessors…
- Prepare yourself to hear news that you don’t like
- Commit to resolving those issues
Conducting Readiness Reviews
When engaging a C3PAO for services, they’re bound by the code of professional conduct.
The code of conduct states…

Within the range of services provided, C3PAOs can conduct pre-assessment readiness reviews.
These reviews assess whether an organization has implemented and documented the CMMC practices. The reviews must stop short of providing consulting defined as, “direct assistance to the creation of processes, training, and technology required to meet the intent of CMMC controls and processes.”
An organization seeking certification (OSC) can still use a C3PAO to conduct their assessment. Such a situation is only possible if the readiness review doesn't provide consulting. C3PAOs are otherwise able to provide consulting services. They can do so as long as they don’t provide certification assessments to any company they’ve consulted for.
The advantage of hiring a C3PAO is that they’ve walked the talk. They’ve passed their own certification assessment and proven understanding of necessary requirements. They’ve also documented implementation of these controls and defended their body of evidence to a third party.
If you’re able to afford their services, there’s considerably less risk hiring a C3PAO.
With less than 30 C3PAOs authorized, they’re less of a commodity than consultants. They’re all listed on the Cyber AB Marketplace. The ones we’ve talked to, including Kompleye, are working to scale their operations to meet the growing demand.
If you’re interested in learning more about Patricio’s CMMC compliance experience, he’s available pat@kompleye.com.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




