CMMC-AB March Town Hall: Key Takeaways
Let’s take a look at some of the key takeaways from March’s CMMC-AB town hall meeting.

This month’s CMMC-AB Town Hall included a special guest from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Nick DelRosso, the Supervisory IT Cybersecurity Specialist at the DIBCAC, stole the show and spoke for about forty minutes. He used his time to address a litany of questions that have lingered since the announcement of CMMC 2.0.
Even the CMMC dab hands of Discord, a difficult audience to impress, came away more positive than usual. Let’s take a look at some of the key takeaways from this month.
Newly Authorized C3PAOs
There were two new C3PAOs announced. The first was Monarch ISC, a Maine-based information security consulting firm. The second was Guernsey, an engineering, architecture and cybersecurity consulting firm based out of Oklahoma City. Together they became the seventh and eighth authorized C3PAOs in the CMMC-AB Marketplace.
In a press release, president Joe Kurlanski noted that Monarch ISC is the only C3PAO in the Northeast. Monarch ISC has already begun conducting readiness assessments of DIB companies. Naturally, it's those who wish to be among the first group to certify under the voluntary program prior to DoD rulemaking.
Director of Cyber Security Consulting with Guernsey, Timothy Fawcett, noted that their journey to becoming the first and only C3PAO in Oklahoma began with an application in October 2020. They look forward to helping other companies implement Level 2 requirements.
Exams for Certified CMMC Professionals (CCP)
The CMMC-AB is limiting access to CCP exams into two categories. First, they'll only be for those who took training from authorized Licensed Training Partners (LTPs). Second, those who took training from the CMMC-AB (e.g. provisional assessors).
The CMMC-AB will restrict access to a Beta exam at the end of August to about 300 users . Those eligible for the Beta exam will receive their invitations by late June.
Individuals not invited to the Beta exam will be able to take the exam starting October 19th. We know from the February Town Hall that about 600 individuals have already completed CCP training from LTPs. There was also around 150 provisional assessors trained by the CMMC-AB.

Assessing Personal Residences, When Invited
The last time representatives from the DIBCAC appeared in a CMMC-AB Town Hall was in October of 2021, shortly before the announcement of CMMC 2.0.
They're still working towards finding a solution for assessments in personal residences.
We received their resolution on this issue during this Town Hall. Assessors may include personal residences when they are…
- Within scope
- DCMA (or a certified assessor working on behalf of a C3PAO) would be willingly invited.
It’s also worth mentioning Nick’s additional point. Further scoping considerations may eliminate the need for on-site assessments of personal residence.
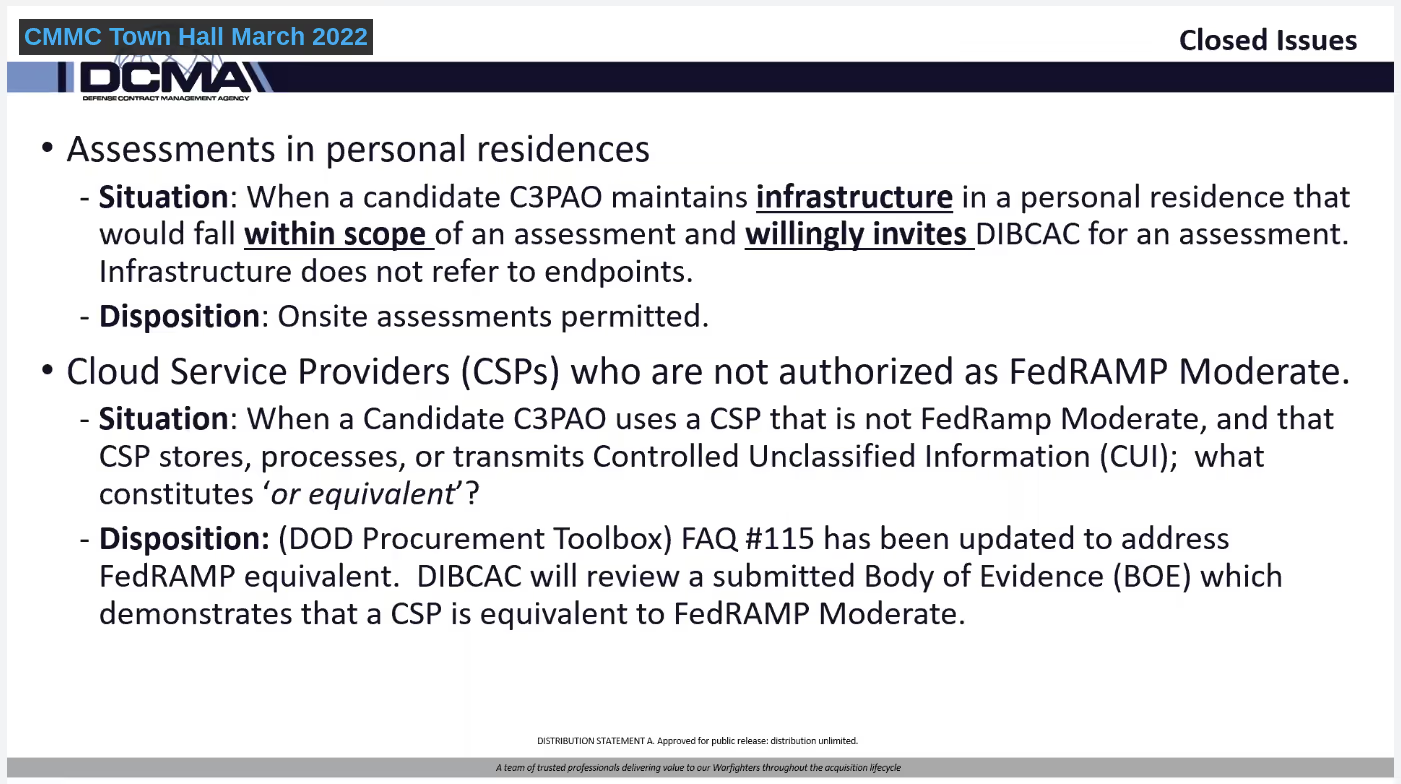
Assessing FedRAMP Moderate Equivalency
The second issue that DIBCAC resolved was in regards to FedRAMP moderate considerations. The Government’s disposition is that DIBCAC (or presumably a certified assessor acting on behalf of a C3PAO) will review a submitted Body of Evidence (BOE) to determine if that Cloud Service Provider (CSP) is equivalent to FedRAMP Moderate.
Nick referenced the DoD Procurement Toolbox frequently asked question (FAQ) Q115 in support of this determination. He stated that DIBCAC would talk to the C3PAO to understand how they’ve made a FedRAMP equivalency determination. Evaluation of a BOE, should detail the system environment in relation to the FedRAMP Moderate baseline controls.
However, self-attestation by the CSP may not be enough. Either a contractor or an independent third party assessment organization (3PAO) should perform some type of check and include documentation to that effect in the BOE.
In addition to the BOE, the DIBCAC will review a…
- Customer Responsibility Matrix (CRM)
- Customer Implementation Summary
- Placemat
These define what controls the contractor is responsible for to maintain FedRAMP compliance.
Cloud-based virtual machines must comply with all requirements of NIST SP 800-171 (including vulnerability scans). The CRM should delineate the responsibilities of the CSP hosting them or the DIB company managing them.


Consequences of Major Deficiencies
There are four levels of Corrective Action Requests (CARs) referenced in DCMA Manual 2303-04.
Nick gave a scenario wherein a contractor has a Plan of Action & Milestones. But, there are no historical benchmarks to show that they’re making any effort to close any of those items.
One possible remedy for the Government is a Level 3 CAR.
This is case, the Government…
- Reduces payment to the contractor
- Disallows costs
- Revokes government assumption of risk of loss
- Disapproves business management systems

Medium Assessments are Still Rare
A Medium Assessment involves the DIBCAC reviewing a company’s SSP. But, only after they have submitted their self-assessment in the Supplier Risk Performance System (SPRS). DIBCAC will initiate the request on a Monday and ask the supplier to provide their SSP by that Friday. Their review will assess the implementation of each requirement. Ultimately, they want to identify if any descriptions don't address security requirements.
There is one main purpose of these medium assessments. They help understand the real implementation of cybersecurity requirements within the DIB.
DIBCAC will select from a variety of industries and SPRS scores to gain a better understanding of compliance within the community.
DIBCAC has a limited number of assessors, probably between 125 and 274 across the nation. When asked how many medium assessments the DIBCAC has performed, Nick acknowledged that look to start in the next couple of months, which may indicate that the priority at this point is conducting Level 2 assessments for the queue of 200 candidate C3PAOs.
After the assessor portion of the ecosystem is stood up, we expect DIBCAC will conduct around 500 medium assessments per year. Out of the estimated 100,000 DIB companies required to report through SPRS (for CMMC Level 2), your odds are comparable to guessing Wordle on the first try. Just like with Wordle, the more others cheat, the better your odds will become.
Acceptable Use of AUPs
An Acceptable Use Policy (AUP) can help guide what administrators can and cannot do. Nick provided the following logic for determining whether or not an AUP is appropriate for your organization:
- If you’re using administrative controls for some of the requirements, an AUP can cover multiple requirements.
- If you don’t have an AUP, then you’ll probably need to stipulate constraints in another administrative control.
- If you don’t use administrative controls, then you’ll need to use technical controls.
If you’re not using any of these three, then you would not meet certain controls (e.g. 3.1.6 and 3.2.1). In other words, it’s probably a best practice to use Acceptable Use Policies. Especially, if you're using using administrative controls.
Beginning to Understand VDI Endpoints
The purpose of most Virtual Desktop Environments (VDI) is to push the device management over to the CSP. Ensuring that data cannot transfer to the endpoint is the first thing that an assessor will look at. Next, an assessor will want to see how you’ve defined the inherent risk for the endpoint and mitigating activities.
This guidance opens the door for CSPs to provide turnkey solutions that address the technical requirements of CMMC. Of course, by using a cloud hosted secure enclave.
One company that we’ve followed closely offering this solution is Ascolta. This solution can be a perfect fit for small manufacturers, software developers and single persons consulting or conducting research for DoD.
Tips on When to Use FIPS
Federal Information Processing Standards (FIPs) Pub 140-3 is the current standard for any validated cryptographic modules. NIST SP 800-171 security requirement 3.13.11 specifies using FIPS-validated encryption to protect controlled unclassified information (CUI). Many solutions have FIPS mode but enabling this feature often has tradeoffs.
According to Nick, when encryption is not required to protect the confidentiality of CUI, then it is not required to be FIPS-validated.
He did provide an extreme example. Stating that if you are in a secure room within a secure facility and data doesn't leave the room, you wouldn't need to use FIPS-validated encryption.
Remediation Cutoffs
When DIBCAC conducts a C3PAO assessment, there appears to be a little wiggle room to fix controls. According to Nick, C3PAOs can correct any controls provided it does not impact the assessment that was already conducted.
You will need to have another assessment if the changes involve…
- An extension of the scope
- Adjusts to the duration of the assessment
- Alterations to your architecture
As for future organizations seeking certification (OSC) assessments by C3PAOs, Nick acknowledged that this is in discussion within rulemaking as some practices will be eligible for POA&M as long as implementation occurs within six months of the assessment.
Implementation Timeline
Nick declined to address bifurcation of Level 2. He only stated that the matter was being discussed in rulemaking.
Matt Travis, CEO of the CMMC-AB, took the opportunity to weigh in by reminding the community about CMMC's original intent. Of course, its purpose was to scale an ecosystem to support assessments within the DIB by 2025.
He also believes that DoD rulemaking will conclude by May 2023. But, that DoD would refrain from inserting CMMC requirements into all contracts. Instead, it will take a more measured approach to their implementation.
On a separate webinar earlier in March, Matt had discussed his opinion on the CMMC 2.0 rollout over the coming years. He stated with the voluntary assessment program. He he believes it will begin later this spring or summer.
Conclusion
We saw last month that inclusion and coordination from DoD stakeholders bolsters the messaging from the CMMC-AB.
As the ‘original’ CMMC assessors, DIBCAC plays an important role in fine tuning the assessment policies and processes.
This month’s resolution on a number of open items leaves little left unanswered prior to the start of the voluntary assessment program.
The last obstacle revolves around the CMMC Assessment Process (CAP). It must be near completion if LTPs will incorporate it into their updated CMMC 2.0 training. We anticipate that this should be available by the end of May or early June.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




