CMMC Level 1 Compliant Awareness Training: AC, MP, PE
In this blog, we’ll explore how training materials can help meet some of the objectives for Maturity Level 1.

A staggering 82% of breaches involve the human element according to the 2022 Data Breach Investigations Report published by Verizon.
It’s no wonder that cybersecurity frameworks have always included a training element for defending against social attacks, insider threats and misuse.
The Cybersecurity Maturity Model Certification (CMMC) requirement for organizations working in the defense industrial base (DIB) is no different.
The Department of Defense has published two levels of maturity for CMMC…
- Level 1: Organizations that work with Federal Contract Information (FCI)
- Level 2: Organizations that work with Controlled Unclassified Information (CUI)
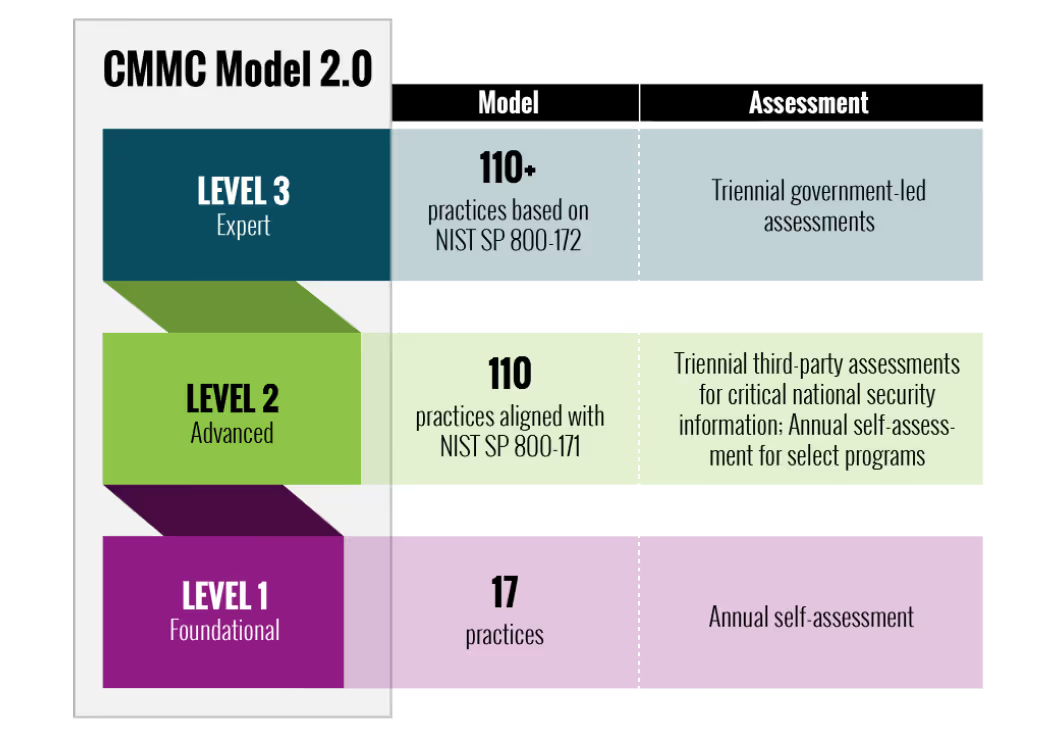
There will be a third level for integrators and organizations dealing with what DoD has deemed to be the most critical CUI but they have not published the requirements for this level yet.
As organizations prepare their cybersecurity program, they should document evidence demonstrating they meet the objectives within the practices.
We previously discussed how policies help address objectives that involve identifying, defining or specifying components of the requirements. In this blog, we’ll explore how training materials can help meet some of the objectives for Maturity Level 1.
Unfortunately, unlike the policy objectives, there are no consistent verbs that would indicate whether an objective is achievable through training. Training may also only partially meet the requirements of some objectives.
How do we know if training helps meet some of the objectives for Level 1?
The Level 1 Self Assessment Guide lists training materials as an artifact documenting compliance.

This is our first hint that some of the requirements contained in the Level 1 practices are achievable through training. Let’s look at the requirements closer and discuss those that have relevance to workforce training.
CMMC Level 1 Training Requirements
The practices within the Awareness & Training domain are not required until Level 2. But, there are a half-dozen objectives within Level 1 practices that relate to training and awareness.
AC.L1-3.1.20 - External Connections
The control statement reads “Verify and control/limit connections to and use of external information systems”.
The last two objectives inform you to:
“[e] control/limit connections to external systems; and [f] control/limit the use of external systems.”
This practice comes from control AC-20 within NIST SP 800-53.
NIST defines external systems as those for which the organization has no direct control over the implementation of controls or an assessment of their effectiveness. Examples of external systems include personal devices and devices in commercial or public facilities.
Organizations need to decide whether they will establish terms and conditions (policy), and/or physical controls to control or limit connections to and use of external systems. Employee training materials should incorporate guidance from DoD Instruction 5200.48 that states…
“Personnel will not use unofficial or personal email accounts, messaging systems, or other non-DoD information systems, except approved or authorized government contractor systems, to conduct official business.”
AC.L1-3.1.22 - Control Public Information
The control statement reads “Control information posted or processed on publicly accessible information systems”.
The second objective informs you to…
“[b] identify procedures to ensure FCI is not posted or processed on publicly accessible system.”
The potential artifacts referenced include training materials and security awareness training records but none of the objectives reference training. In this instance, it is helpful to look at the source for this practice.
This practice comes from control AC-22 within NIST SP 800-53. The second objective under AC-22 states…
“train authorized individuals to ensure that publicly accessible information does not contain nonpublic information”.
To accomplish this objective, an organization must identify individuals authorized to make information publicly available and train them to ensure non-public information is not made publicly available. Hence, the artifacts of the training and training records are applicable here.
MP.L1-3.8.3 - Media Disposal
The control statement reads…
“Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse”.
The two objectives inform you to…
“[a] sanitize or destroy system media containing FCI before disposal; and [b] sanitize system media containing FCI before releasing for reuse”.
Potential artifacts referenced include the procedures addressing media sanitization as well as the personnel with media sanitization responsibilities. There is no reference to training in the objectives or the evidence for this practice, so why do we believe training is still required?
This practice references NIST SP 800-88 guidelines for media sanitization, which states…
“it may be more cost-effective (considering training, tracking, and verification, etc.) to destroy media rather than use one of the other options”.
There are three methods to verify confidentiality through the sanitization and disposal process.
The first relates to the equipment, the last relates to the results but the second relates to the personnel competencies. Organizations should ensure that their operators are competent to perform sanitization functions.
You should train all employees on the system media protection policy but you should also train those individuals with media sanitization responsibilities in order to verify their competencies conducting the sanitization.
PE.L1-3.10.1 - Limit Physical Access
The control statement reads…
“Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals”.
The last three objectives inform you to…
“[b] limit physical access to organizational systems to authorized individuals; [c] limit physical access to equipment to authorized individuals; and [d] limit physical access to operating environments to authorized individuals”.
Physical access controls such as keys, proximity cards or biometric authentication are often employed to meet these requirements. However, these are vulnerable if authorized employees allow unauthorized visitor access. You should train all employees to recognize and report unauthorized persons accessing organizational environments.
If neither security guards nor access control vestibules are in use, you should train employees to not allow piggybacking or tailgating when entering the facility.
PE.L1-3.10.3 - Escort Visitors
The control statement reads…
“Escort visitors and monitor visitor activity”.
The first objective informs you to…
“[a] escort visitors”.
All employees should receive training on the visitor access policy and how to report incidents. The training of all staff on visitor access policy and incident reporting could constitute one safeguarding procedure that addresses physical access control.
PE.L1-3.10.4 - Physical Access Logs
The control statement reads…
“Maintain audit logs of physical access”.
The only objective informs you to…
“[a] maintain audit logs of physical access”.
All employees should receive training on the procedures used to track employees and visitors entering and exiting the facility. You may choose to keep logs manually using paper sign-in sheets or automatically using badges or key cards.
CMMC Level 1 Training Summary
We’ll see in the CMMC Level 2 Compliant Awareness Training Program blog that awareness and training are on a continuum.
All users should be security aware but beyond the cybersecurity essentials, training should become role-based. Let’s summarize the training requirements in terms of where they fall along this spectrum.
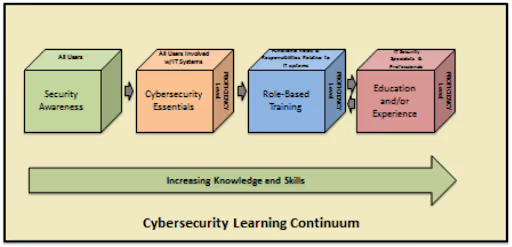
Security Awareness for All Users
- PE.L1-3.10.1:Train all employees to recognize and report unauthorized persons accessing organizational environments.
- PE.L1-3.10.3: All employees should receive training on the visitor access policy and how to report incidents.
- PE.L1-3.10.4: All employees should receive training on the procedures used to track employees and visitors entering and exiting the facility.
Cybersecurity Essentials for All Users of IT Systems
- AC.L1-3.1.20: Make users aware they are not to use non-approved systems to conduct official business involving FCI.
- MP.L1-3.8.3: Train all employees on the system media protection policy.
Role-Based Training
- AC.L1-3.1.22: Train individuals authorized to make information publicly available to ensure non-public information is not made publicly available.
- MP.L1-3.8.3: Train individuals with media sanitization responsibilities to verify their competencies.
Delivering and Documenting Awareness & Training
When evaluating security awareness and training options you will undoubtedly find the acronym SCORM, which stands for Shareable Content Object Reference Model.
SCORM is a set of technical standards that tell software programmers how to write their code so that it is compatible with eLearning software.
SCORM dates back to version 1.0 released in 2000 following Executive Order 13111 which set out to establish standards and specifications for eLearning. SCORM allows browser-based eLearning with plug-and-play portability, reusability, and sequencing of self-paced content.
Another acronym you will find is LMS, which stands for Learning Management System. A Learning Management System is eLearning software that delivers content to users and tracks when users complete assignments.
This is helpful when the training is undertaken by an organization to meet a compliance requirement because the LMS can archive records of completed training and issue certificates of completion.
K2 Akademy by Etactics
Born out of our own requirements to train Etactics employees on the HIPAA Privacy and Security Rule, K2 Akademy is a LMS capable of delivering SCORM-based training on a number of topics including Cybersecurity, HIPAA and Human Trafficking Awareness.
In line with the requirements outlined above for organizations seeking to comply with CMMC Level 1, our Cybersecurity Awareness course will help you document annual compliance with the five objectives listed above for all users.
Role-based training is available as well for any users responsible for either ensuring FCI is not made publicly available or sanitizing media that contained FCI.
K2 Akademy makes it easy to distribute SCORM-based training to users with a unique link sent to each individual. Users will not need to create a username or password to complete the training.
We offer monthly and annual subscription plans with discounts provided to those organizations also using K2 Compliance to document their entire cybersecurity program.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




