Cybersecurity Basic Training: 5 Must-Have Topics
If you want a thorough training course, you need to cover a variety of topics to cover your basics. Here are five topics you should keep in mind when selecting a company to provide a “cybersecurity basics” training course for your company.

The global cost of cybercrime will rise from $8.44 trillion in 2022 to $23.84 trillion in 2027. In other words, the financial impact will almost triple in five years.
If a breach compromises the data in your network, the consequences could be disastrous. Your company information would fall into the hands of cybercriminals. Assets, operations, and other sensitive information could fall into the hands of your competitors.

By exploiting vulnerabilities in an organization's system and network, you can never predict what hackers will do with the valuable information.
The first line of defense comes in the form of training. A “Cybersecurity Basics” training module is a good place to start. This type of training module should briefly cover a variety of topics, followed by more in-depth modules to reinforce the lessons in the introductory module.
But where do you start to look for a training module and what should it cover?
If you want a thorough training course, you need to cover a variety of topics to cover your basics. Below are five topics you should keep in mind when selecting a company to provide a “cybersecurity basics” training course for your company.
Topic 1: Why Cybersecurity is Important
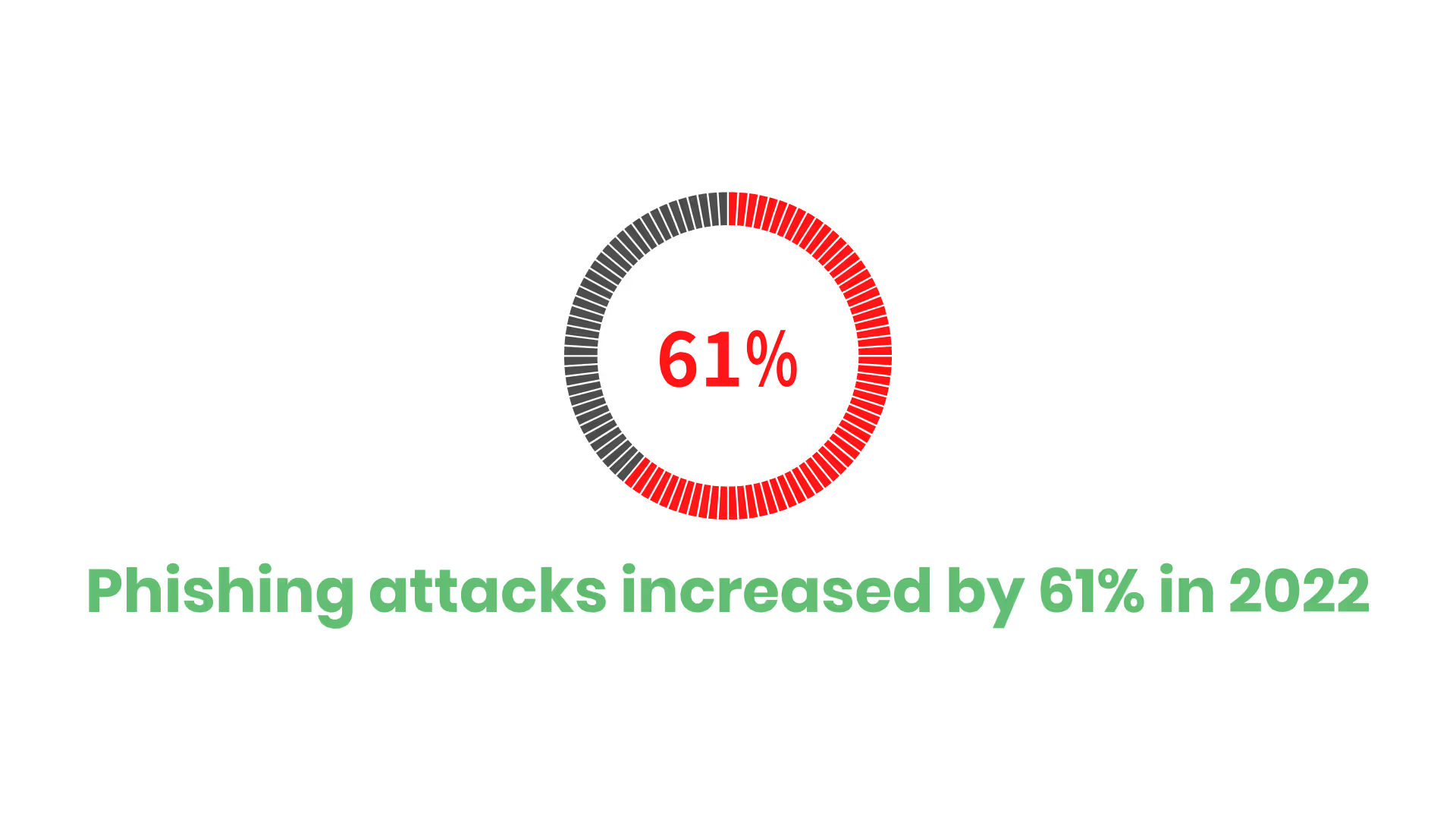
The first part of your “cybersecurity basics” training module should create a sense of urgency because it’s just that…urgent. To put it into perspective, phishing attacks increased by 61% in 2022.
Statistics like that help make sure your employees understand why cybersecurity is critical to the welfare of the business and their daily life on the job.
You’re the biggest risk to your organization. I know, I know…bold statement. But this is actually true for every employee, regardless of where they work. A human element was the root cause of 82% of breaches in 2022. The fact of the matter is that the biggest cybersecurity threat to any business in the U.S. comes from employees. Hence why training is so important.
Cybersecurity is a field that’s forever evolving at a rapid rate. It constantly poses new challenges for companies, government agencies, and individuals.
You might assume that cybersecurity means protecting computers from malware and viruses. But, that’s only one aspect of cybersecurity. It’s a bit more complicated than that.
Cyberattacks and breaches are more common today than ever before. They’re no longer limited to large corporations with deep pockets. This means that small companies, schools, and local municipalities have targets on their backs.

A “cybersecurity basics” training course exists to help prevent cyber attacks from affecting where you work. After all, you don’t want to be the person to accidentally click on a phishing email that shuts down your entire organization’s network. It also exists so you don’t become a victim of a social engineering scam that results in giving sensitive information to a bad actor.
Knowing some cybersecurity basics and putting them into practice will help you protect your employer and reduce the risk of a future cyber attack.
Topic 2: Safe Internet Habits
The next crucial element of any good basic training course should cover safe internet habits. If employees know what to do and what not to do, then you’ll minimize your chances of experiencing a breach.
First, passwords, passwords, passwords! Don’t use the same passwords more than once.

If a hacker gets their hands on your password for one account and you use that same password for other websites (like your bank account), then every single place where you use that same password gets compromised. Under no circumstance should you use the same password more than once.
Safe browsing techniques are another topic that should be present in your basic training course.
Does the image below look familiar to you? If it does, then there’s a good chance you visited a website built by a hacker to try and infiltrate your network and steal your data.
These warnings are here to protect you. They don’t completely prevent you from going to the website, but they at least give you some insight into the dangers ahead if you continue forward.
It’s still possible for you to visit a malicious website or accidentally click on something you shouldn’t. Hackers are constantly creating new methods to install malware onto your computer or steal your credentials.
The third safe internet habit to include in your cybersecurity basic training program is keeping your software and operating system up to date.
The older the software, the higher the chance there’s a vulnerability that a hacker can exploit to gain access. This is why when you get the notification to update your software, you should install it right away.

There are thousands of other good practices when using the internet. Covering all of them in a single training model is virtually impossible. Especially in the module that should cover all of the basics.
Other safe internet habits that you should look out for when selecting a training package include…
- Be careful what you post online
- Make online purchases from secure sites
- Be selective of what you download
- Use a secure internet connection
- Keep privacy settings on
- Use personal and/or business information sparingly
- Use two-factor authentication
Topic 3: Identifying Social Engineering
Social engineering is a term used to describe a variety of malicious activities accomplished through human interaction. As I mentioned before, the biggest risk to your organization is the people who work there. Hackers can trick and manipulate them into a cyber incident.
This is why your “cybersecurity basics” training module should definitely cover social engineering briefly.
Social engineering uses psychological manipulation to trick victims into making calculated security mistakes.

The hacker will contact them using a hook. They will spin a story to engage their target and control the interaction. They will then play their victim to obtain more information during the interaction.
The social engineer will naturally cut ties with their victim to avoid arousing suspicion. The hacker will remove any spyware, cover their tracks, and go off with your information.
Your training module should briefly cover that there are five main types of social engineering attacks:
- Baiting
- Scareware
- Pretexting
- Phishing
- Spear phishing
Each type is similar, with key differences that separate one from another. You don’t need to go in-depth with each one in the module covering the basics.
Topic 4: Safe and Secure Use of Social Media
Unless you’re in marketing or sales, there’s a good chance that you aren’t using social media for work purposes.
In fact, 80% of employees admit to using social media on the job. This is why you need to include something about social media in your “cybersecurity basics” training course.

Safe and secure social media practices go hand-in-hand with the safe internet habits mentioned above. All of the suggestions mentioned before also apply to social media usage. That said, there are still a few things that I need to mention about social media usage specifically.
You need to read your organization’s social media policy. As boring as this might be, you need to adhere to the rules set in place by your employer. These rules exist to protect the business from cyber threats.
You also need to pay attention to the information you share. The last thing you want is to share confidential company information for bad actors to use against you. The entire goal of social media platforms is to share information with the world, so once information is out there, it never truly goes away. Don’t share sensitive information with the world.

Just like safe internet habits, you need to be careful of links posted on social media. Social media accounts are prone to hacks. Someone can impersonate your friend or coworker to gain access to your network. Therefore, you need to be aware of what you’re clicking.
There are many more tips and rules you can include in this section of your cybersecurity basics training module. These apps are part of our daily lives, so it’s important to be thorough with this topic.
Topic 5: How To Spot Insider Threats
The last thing your organization wants is a “mole” working for you while leaking information to your competitors. There’s no way one of your coworkers is leaking information and trade secrets for their own personal gain… right? That’s like something out of a movie!
Unfortunately, this does happen.
Although you might not think insider threats and cybersecurity go together, they do. Much of your organization’s information is likely stored online. The theft of this information is a cybersecurity breach, even if someone physically came in with a hard drive.

Teaching employees about the signs of an insider threat is vital to the health of the organization. That’s why you must cover it in your cybersecurity basics training module.
There are eight key signs that could suggest someone has turned into an insider threat:
- Poor performance reviews
- Outwardly voicing disagreements with company policies
- Arguments with coworkers
- Financial distress
- Unexplained or random financial gains
- Strange working hours
- Frequent overseas travel
- Leaving the company
Some of these are more apparent than others. If you see a cluster of signs and suspicious activities, voice your concerns to your superiors.
If you ever suspect that an employee might be leaking company information, discuss it with your manager. Explain to them the situation, what you noticed about the employee in question, and provide any evidence you collected. After that, your manager should conduct an investigation.

Insider threats happen. Because they can have a massive impact, they’re important to understand. But this doesn’t mean you shouldn’t trust any of your coworkers. Definitely don’t start profiling them.
Conclusion
With more and more organizations falling victim to cyberattacks, the importance of cybersecurity cannot be overstated. The best way for businesses to stay protected is not just through technology; it’s also by understanding that your employees are a major security risk.
Investing in employee training can mean all the difference between staying safe or becoming another data breach statistic.
If you’re looking to train your employees on cybersecurity basics, consider Etactics. In our K2 Akademy cybersecurity training module, we will cover all of the topics listed above and more, including (but not limited to)...
- Identifying phishing attempts
- Avoiding phishing attempts
- Remote work practices and policies
If you’re in the market to purchase training for your employees, learn more by clicking here.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




