80+ Sickening Statistics on Cybersecurity
Understanding the situation regarding cybersecurity is the first step in preventing it from happening to you. After all, if you can learn from other people’s mistakes, you’re less likely to replicate them. Here are over 80 statistics on cybersecurity that shed light on the different aspects of IT security.

If you watch the news consistently, it probably feels like a breach occurs every day. It often seems like hundreds of thousands of accounts become compromised regularly.
The situation can seem so overwhelming that you may think to yourself, “Is cybersecurity even worth it?”
Simply put…yes.
Breaches occur all the time and they can seem inevitable. However, you should still do everything in your power to prevent one from happening to you.

Enduring a hack can be incredibly expensive. Not only do operations halt, but you also need to spend precious resources and time repairing the hacked network. Loss of revenue and unforeseen costs is a bad combination and can end in disaster for your organization.
Understanding the situation regarding cybersecurity is the first step in preventing it from happening to you. After all, if you can learn from other people’s mistakes, you’re less likely to replicate them.
Here are over 80 statistics on cybersecurity that shed light on the different aspects of IT security.
General Statistics
There are so many forms of malware that the concept of cybersecurity can be overwhelming.
These include, but are not limited to…
- Virus
- Worm
- Ransomware
- Trojan Horse
- Botnet
- Logic Bomb
- Rootkit
- Phishing
- Adware
- Smishing
- Spyware
- Vishing
- Grayware
- Keylogger
After seeing this list, you are probably shaking in your boots. All these types of attacks are intimidating and scary.

Most breaches involving these types of malware are financially motivated. Other bad actors may have a vendetta against the government or the specific business. But all breaches have something in common: they attack vulnerabilities in a company’s network.
Below are some statistics on cybersecurity incidents that may help shed light on what you’re up against.
- 5,258 confirmed breaches occurred in 2021. (CSO)
- 86% of them were financially motivated.
- Organizations that upgrade security technologies every quarter are 30% more likely to keep up with cyber threats compared to those that upgrade every few years. (Cisco Secure Study)
- 90% of security executives reported that their organizations added at least one security tool in the last 12 months. (Foundry)
- 85% of cybercrime occurs due to some form of a human element. (Verizon 2021 Data Breach Investigations Report)
- Compromised credentials were the initial attack vector for 20% of breaches. (IBM 2021 Report)
- Compromised credentials were the most common attack vector.
- Organizations with more advanced cloud modernization strategies contained breaches an average of 77 days faster than companies still in the early stages. (IBM 2021 Report)
- It takes an average of 102 days for most companies to apply a patch. (Check Point)
- 16% of CISOs believe employees in their organizations are not held accountable for vulnerabilities and breaches. (Accenture Security Cybercrime Study)
- Over 23,000 vulnerabilities are publicly reported each year. (Check Point)
- 39% of security technologies used by businesses classify as outdated. (Cisco Secure Study)
The Cost of Poor Cybersecurity
There are many variables at play when it comes to analyzing the cost of poor cybersecurity and breaches.
Businesses need to stop production and other activities in order to address the event that occurs. This loss in revenue is one such cost of the breach.

Another major source of costs associated with a breach involves analyzing your infected systems. Doing so helps you understand what became compromised in the first place. Many companies pay for credit monitoring services, among other cleanup costs, adding to the total.
Patching the breached system is also quite costly. So, is purchasing the necessary security so that it does not happen again.
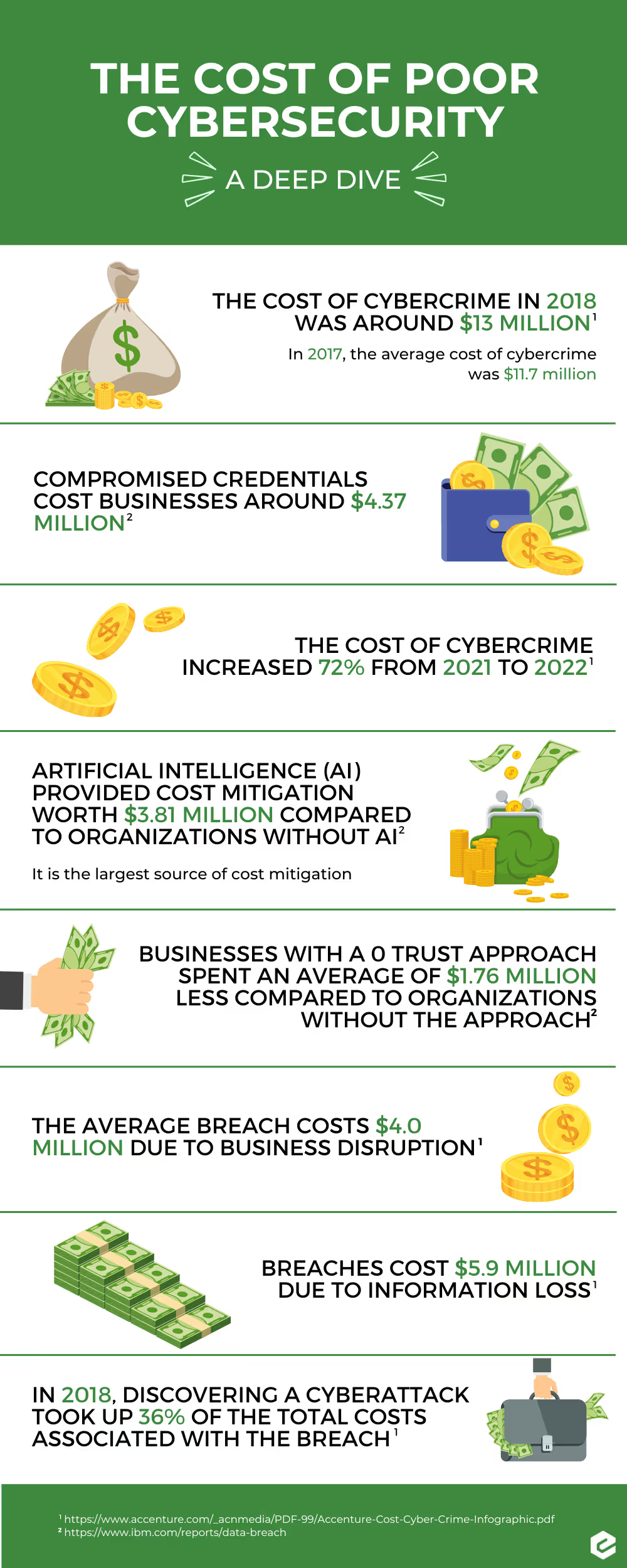
Let’s take a deeper dive into the cost of poor cybersecurity practices…
- The cost of cybercrime in 2018 was around $13 million. (Accenture Security Cybercrime Study)
- In 2017, the average cost of cybercrime was $11.7 million.
- Compromised credentials cost businesses around $4.37 million. (IBM 2021 Report)
- The cost of cybercrime has increased 72% in the last year. (Accenture Security Cybercrime Study)
- Artificial intelligence (AI) provided cost mitigation worth $3.81 million compared to organizations without AI. (IBM 2021 Report)
- It is the largest source of cost mitigation.
- A breach costs $4.0 million due to business disruption. (Accenture Security Cybercrime Study)
- Businesses with a zero-trust approach spent an average of $1.76 million less compared to organizations without the approach. (IBM 2021 Report)
- Breaches cost $5.9 million due to information loss. (Accenture Security Cybercrime Study)
- In 2018, discovering a cyberattack took up 36% of the total costs associated with the breach. (Accenture Security Cybercrime Study)
Cybersecurity Changes During COVID-19
Many people started working from home during the COVID-19 pandemic. This led to a variety of new vulnerabilities. Companies simply didn’t have time to properly secure all the work-from-home laptops, desktops, and networks.
Many companies also used new platforms for virtual meetings and utilized the cloud to share files. Many of these new tools did not have the proper encryption to prevent hackers from gaining access. Therefore, the stay-at-home order left companies in a vulnerable position.
On the bright side, many organizations used the pandemic as an opportunity to invest in better cybersecurity practices. On the downside, many scams related to COVID-19 appeared to try to steal money from people and businesses.
But just how much of an effect did the COVID-19 have on cybersecurity?
- Breaches involving COVID-19 remote working conditions cost an average of $1.07 million more compared to those with no remote work involved. (IBM 2021 Report)
- 68% of organizations are planning to increase their cybersecurity spending after the pandemic. (Atlas VPN)
- As companies move to the cloud to compensate for remote working conditions, 75% of companies reported concern about cloud security. (Check Point)
- Projections estimate that 99% of cloud security incidents through 2025 will be the customer’s fault.
- Zoom became a popular digital conference application during the pandemic, but over 530,000 accounts had login credentials for sale on dark web hacker forums. (CPO Magazine)
- The credentials were being sold for a fraction of a cent, mostly as a convenience fee.
- The public made 28,500 complaints related to COVID-19 w to the Internet Crime Complaint Center (IC3). (FBI 2022 Internet Crime Report)
- During the pandemic, ransomware attacks grew by over 40%. (CSO)
- The FBI recorded more than 12,000 COVID-related scams. (CNBC)
Rate of Cybercrime
You know the age-old adage, “Crime doesn’t pay?” Well, if you’ve heard about some of the more recent cyber attacks, you would see massive payouts. Especially on the ransomware side.
With companies wiring millions of dollars to hacker groups to gain access back to their systems, who wouldn’t want to become a hacker?
The point I’m trying to make is that the rate of cybercrime is increasing…most likely due to the payouts involved in successful attacks.
In fact, this type of illegal activity is happening so frequently that companies are having a hard time keeping up. Even federal agencies that help track and mitigate cybercrime feel overwhelmed.

As the rate of digital fraud targeting businesses increases, all employees should be aware of the growing threat.
- A cyberattack occurs about every 39 seconds. (Security)
- Cybercrime rates increased 67% in the last five years. (Accenture Security Cybercrime Study)
- IC3 received more than 2,000 complaints per day. (FBI 2022 Internet Crime Report)
- 79% of executives agree that new business models introduce technological security vulnerabilities at a faster rate than can be properly secured. (Accenture Security Cybercrime Study)
- Computers used in a study conducted by the University of Maryland had an attack 2,244 times a day. (Security)
- The number of security breaches in 2018 was 145. (Accenture Security Cybercrime Study)
Industry-Specific Cybersecurity Statistics
Hackers don’t care what industry your organization works in. If you have data that’s sensitive to your clients or how your business operates, hackers want it.
They know that they can either shut your access off and force you to pay a ransom, or sell your information on the dark web. In their eyes, it’s a win-win.
Healthcare
Hospitals, doctor offices, and clinics are common targets for bad actors. Healthcare organizations are a target because they contain lots of sensitive information. Additionally, they are more likely to pay a ransom since any disruption to their services can cause accidents and death.
- Cybercrime against hospitals increased by 45% worldwide in the fourth quarter of 2020. (Check Point)
- The healthcare industry will spend around $125 billion between 2020 and 2025 on cybersecurity defense systems. (Cybercrime Magazine)
- Breaches in September 2020 exposed over 9.7 million healthcare records. (HIPAA Journal)
- This is 348% more than the number of records exposed the month prior.
Government
Many local governments are a target of cybercriminals due to their lack of resources and cybersecurity infrastructure. This includes the administrative departments of towns, cities, counties, and other smaller governments.

However, because many of these smaller administrations do not have the resources to install proper cybersecurity defenses, it is up to the federal government to provide protection. As such, we need to analyze federal organizations since they impact local vulnerable municipalities.
- In 2021, the Department of Defense (DOD) requested a budget of $9.85 billion for cybersecurity. (Atlas VPN)
- This accounts for 52% of federal expenditures on cybersecurity.
- The Department of Homeland Security (DHS) requested $2.6 billion for cybersecurity efforts in 2021. (Atlas VPN)
- This accounts for 13% of the total requested budget.
- The 2021 request increased 1.17% compared to that of the previous year.
- The 2020 presidential budget allotted $17.4 billion to cybersecurity-related activities. (Cybercrime Magazine)
- This is a 5% increase compared to the 2019 estimate.
Type of Breach Statistics
I alluded to this earlier (and you likely already knew it beforehand), but hackers rely on different types of attacks.
They’re like malicious magicians with hundreds of different tricks up their sleeves in hopes that someone will fall victim.
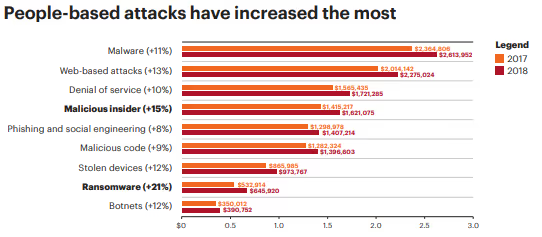
Ransomware
Ransomware is a form of malware that hackers use for the purpose of financial gain. Bad actors hack into networks and shut down everything. They demand an amount of money and will release control of the networks once paid.
More recently, these bad actors will release sensitive information to the dark web in small increments to increase the pressure on companies to pay the ransom.

Ransomware leads to a loss of data, loss of revenue, huge costs, and interruption of services. The best way to prevent a breach is to train employees about ransomware. However, in the meantime, learning about the situation is a good start.
- 10% of breaches in 2021 involved ransomware. (Verizon 2021 Data Breach Investigations Report)
- 2021 had twice the number of ransomware breaches compared to the previous year.
- The IC3 received nearly 2,500 reports of ransomware incidents (FBI 2022 Internet Crime Report)
- This resulted in over $29 million in financial loss.
- Ransomware was responsible for $20 billion in costs in 2020. (Check Point)
- The costs of ransomware increased 75% from 2019 to 2020.
- In 2018 alone, ransomware cost businesses over $8 billion. (Clearedin)
- The average ransom payment peaked at around $234,000 in September 2020 (Webroot)
- The average ransom paid increased by over 170% from 2019 to 2020. (CSO)
- During that time, the highest-paid ransom ever recorded doubled from $5 million to $10 million.
Phishing
Phishing is an attempt to access sensitive information through deceitful fraud. This is often done through emails, but it also happens through phone numbers.
They often try to gain access to website accounts that host financial information. This includes bank accounts, Amazon accounts, payment services, and other such digital destinations.

Although many phishing email attempts end up in a spam folder, sometimes they get through to a person’s inbox. The best way to protect your organization is to understand what phishing emails could look like. Proper phishing awareness training can also help protect your network.
In the meantime, below are some statistics to help you understand the situation regarding phishing attempts.
- The IC3 received over 241,000 phishing, vishing, smishing, and pharming reports in 2020. (FBI 2022 Internet Crime Report)
- This is up from about 20,000 reports four years prior.
- These attacks resulted in over $54 million in financial loss.
- 97% of people would not be able to identify a phishing scam. (Clearedin)
- Employees opened 30% of fishing scams, up from 23% in previous years.
- Phishing was one of the most common types of cyberattacks in 2021. (Check Point)
- It was the third most common type of scam reported to the FBI last year. (Clearedin)
- 36% of all breaches in 2021 had some form of phishing component. (Verizon 2021 Data Breach Investigations Report)
- 2021 had 11% more phishing attacks than the previous year.
- 83% of organizations reported experiencing a phishing attack in 2021. (Clearedin)
- This is up from 76% reporting the same in 2020.
- Experts expect another 6 billion attacks to occur in 2022.
- Bad actors created 6.95 million new phishing and scam pages in 2020. (CSO)
- One in 99 emails is a phishing scam. (Clearedin)
- Experts determined this after analyzing 55 million emails.
- The IC3 received almost 20,000 Business Email Compromise and Email Account Compromise complaints. (FBI 2022 Internet Crime Report)
- These resulted in a loss of over $1.8 billion.
Malware
Malware and human error go hand in hand.
After all, employees are one of the main reasons why breaches occur in the first place. All it takes is one careless mistake and then… Boom!

One of the best ways to prevent this type of human error is to know how prevalent it actually is.
- There were about 1,400 cases of malware, scareware, and viruses reported to the IC3. (FBI 2022 Internet Crime Report)
- This totaled an estimated $7 million in financial loss.
- In 2020, 46% of companies reported an employee installed malicious mobile malware disguised as an app. (Check Point)
- 66% of malware gets downloaded onto a computer because it was well disguised as an email attachment. (Clearedin)
- From 2019 to 2020, email malware attacks grew by 600%. (CSO)
Conclusion
No matter how many measures you take to prevent a breach, you could still become a victim of a cyberattack.
Hackers are becoming increasingly bold and daring. They can attack any type of organization of any size…at any time.
Breaches cost companies across the US millions of dollars. During the COVID-19 pandemic, these costs affected organizations more acutely due to other financial stressors. The pandemic also created new vulnerabilities for companies, some of which include the security of employees’ home networks.
At the end of the day, training is one of the most effective ways to prevent a breach. The more aware your workforce becomes of the various methods bad actors use to install malware, the less likely you will endure a breach.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)