Did you know that 1 in 4 businesses see losses up to $500,000 a year from cyberattacks? This lost revenue often relates to:
To avoid potential data leaks, companies today rely on information security management systems (ISMS). These framework policies reinforce risk management habits that help keep your information assets safe. Having a solid risk assessment process through a strong ISMS has multiple benefits.

First and foremost, it can save you from revenue loss, as I mentioned before. Once you identify risks and vulnerabilities, your company is better able to implement a risk treatment plan. These plans addresses threats and vulnerabilities by directly addressing:
One of the most notable frameworks is ISO 27001. Being able to show your stakeholders and clients that you received your ISO 27001 certification is key. Today, we will go over what exactly ISO 27001 consists of, how to perform an ISO 27001 compliant risk assessment, and more!
ISO/IEC 27001 is an international standard for data security. Implemented by the International Organization for Standardization (ISO) in partnership with the International Electrotechnical Commission (IEC). It actually is a part of a larger set of standards, from the ISO/IEC 27000 series. But today, let's just focus on this smaller section. While it is smaller in comparison to the entire series, it is by no means a small undertaking to go through.

ISO 27001 is a security framework that protects companies' information on an international level. Both companies and individuals are able to complete certification through an audit (company) and a course/exam (individual). According to this framework, the goal of an ISMS should be to protect these three aspects of information:
To address these aspects, you must first perform a risk assessment. This highlights any vulnerabilities and helps predict what potential security incidents could happen. Then, follow up by implementing a risk treatment plan. This directly addresses and works to prevent said incidents. Finally, apply appropriate controls to mitigate future risks. Let's start with how to perform a risk assessment.

The official ISO 27001:2022 standards document includes clauses that list requirements for organizations to meet before becoming ISO 27001 certified. Specifically, clauses 4-10 go over these information security standards. I'll go over the basics of these sections and how they affect ISO 27001 risk management:
While this is all important in regards to becoming ISO 27001 compliant, this goes far beyond performing a risk assessment. So let's get back on track.

After you have defined the project, the security requirements, and your ISMS scope, it is now time for you to perform your risk assessment. This is the core of ISO 27001 as it requires you to delve into your current security procedures.
Section 6.1.2 of the ISO 27001 standard states this process must establish and maintain information security risk criteria, ensure risk assessments are repeatable and produce consistent results.
Also, it calls for the identification of risks associated with the loss of confidentiality, integrity and availability for more information within the scope of the ISMS. As well as the need to identify the owners of those risks. Finally, analyze and evaluate all information security risks.
Let's go over these steps in more detail, so you can ace your information security risk assessment!

Decide how you want to go about identifying potential risks. As well as who you will assign risk ownership to and how those risks impact confidentiality, integrity, and availability of the information. A risk assessment and treatment plan need to cover the following:
Identify any risks that might affect your data. Again, be sure to take confidentiality, integrity, and the availability of that data in mind when covering risk identification. While this can be one of the more time-consuming parts of your risk assessment process, it's not one you can skip. Follow an asset-based risk assessment process for best results. Developing an asset management list allows you to have something to refer to. Information assets might include:
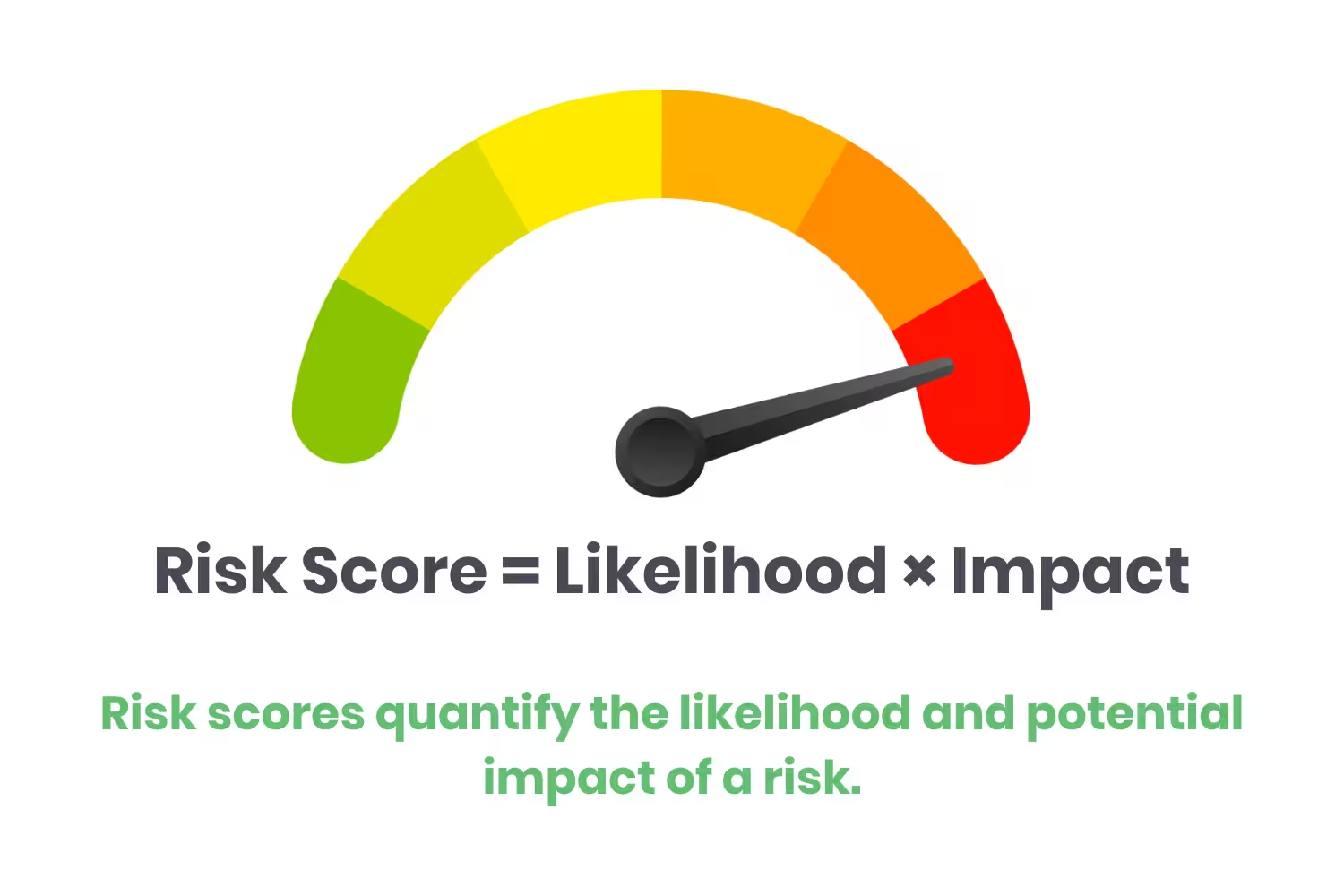
When you have a complete list of your assets, analyze risks associated with each one. Assign a risk score for each. Risk scores quantify the likelihood and potential impact of that risk. The formula is as follows:
Risk Score = Likelihood × Impact
Document these in a risk register.
Once you have your risk register, you'll want to assign each item to a risk owner. This individual is in charge of managing a specific risk. They will help to assess, identify, and implement any mitigation strategies.
Organizations must evaluate risks against the predetermined level of accepted risk. Then prioritize which they should address first, in order of most pressing to least pressing. Risk treatment options include:
When you conduct an ISO 27001 risk assessment report, you can choose to If you choose to modify your risk through implementing controls. These information security controls are processes and policies you put into place to mitigate a risk.
The criteria comes from The 2022 revision of ISO 27001 Annex A, which lists 93 controls. Organized into 4 sections numbered A.5 through A.8. A statement of applicability (SoA) states which ISO 27001 controls are in place, in accordance with the Annex A control set. Let's go over these safeguards briefly with examples included.
The Organizational section houses 37 controls. The focus on the policies, procedures, responsibilities and other organizational measures. They define the expected behavior from users, equipment, software, and systems.
Example: Inactive users are automatically deactivated after a certain amount of time.
When talking about risk profiles, human error is one of the biggest threats. This section houses 8 controls which ISO 27001 require as best practice for incident management and prevention. This section includes employee background checks and regular security training operations. By providing your team with knowledge and skills, you can enable them to complete their daily tasks in a secure way.
Example: Keeping your employees up to date on cybersecurity training.
Protecting physical information means not only taking tangible assets into consideration, but also the environment it is in. Wherever you store your data, you need to follow this section's 14 controls to keep it safe. Physical controls might include storage and disposal protocols and entry and access systems.
Example: Installing an alarm system for your office.
Technical controls define how your company handles IT systems. This section houses 34 controls which help ensure your IT infrastructure is secure. Managing who can access source code and how to maintain network security are a few ways to implement this control.
Example: Keeping your antivirus software up to date.

So why buy into all of this? I already mentioned that being ISO 27001 certified comes with quite a few benefits. Including saving on lost revenue from security incidents. Let's go over a few more business benefits you can expect from implementing this ISMS:
At the end of the day, the benefits don't just stop at keeping sensitive information safe. There are plenty of reasons why all companies handling data should aim for ISMS compliance. Companies must assess the likelihood and impact of information security risks to effectively prevent them.
Following a clear guide to the ISO 27001 framework gives you an advantage. It helps ensure you have a strong information security risk management system. When it comes to implementing ISO 27001 requirements, it's not just about a certificate. It's about understanding your risks, your team's work ethic, and the organization's security awareness as a whole.
Auditors look beyond just written policies and documentation when assessing your ISMS. They want to see that your risk assessment guide translates into effective controls that operate consistently in practice. Whether you are working with an effective risk management system like ISO 27001 or SOC 2, making sure you practice your risk assessment methodology is only the beginning.