SOC 2 Compliance: Understanding SOC 2 Password Requirements
In this blog, we go over what SOC 2 is, its password requirements, how to implement this framework into your own organization, and more!

Did you know that 60% of Americans admit to reusing old passwords? Even though one of the riskiest practices in password compliance is to do just that. Using the same password for multiple applications is just asking for a hacker to steal your sensitive data.
Having a strong password is vital to prevent unauthorized access to your personal information. It also helps aid in security best practices for organizations across the country. After all, a single data breach can cost a single company millions of dollars.
However, password compliance requirements can be a bit more involved when it comes to companies. That's why The American Institute of Certified Public Accountants (AICPA) developed SOC 2 in 2010 to help auditors evaluate an organization's security protocols. These independent auditors measure a business's controls against the Trust Services Criteria (TSC).

There are five categories under the TSC that cover key pillars of data security:
- Security - Protects information and systems from unauthorized access. Also protects against vulnerabilities that could result in the jeopardization of the integrity, confidentiality, and privacy of information.
- Availability - Ensures that information and systems are ready and available to support the business's goals.
- Processing Integrity - Focuses on making sure the entity's system can process information in an effective way.
- Confidentiality - Limiting access, storage, and use of confidential information to preserve its integrity.
- Privacy - Manages private personal information.
Note that the security portion is the only one required for every SOC 2 audit. Although, depending on the scope of the organization and the services provided, additional criteria can be applicable. In this blog, we go over what SOC 2 is, its password requirements, how to implement this framework into your own organization, and more!
Overview of SOC 2 Type I & Type II
SOC 2, or Systems and Organization Controls 2, is a security framework which specifies how businesses should protect their customer's data. It is not a regulatory requirement, but it is a globally compliance benchmark. A SOC 2 report is a document that companies show stakeholders to demonstrate their security controls are in place and working. There are two types of SOC 2 reports:
- SOC 2 Type I - evaluates company's controls at a single point in time.
- SOC 2 Type II - assesses how controls function over a period of time. Usually 3-12 months.
Type I answers the question: are the security controls designed correctly? While Type II answers: do the security controls function as intended?

Why is Password security & Password Management Critical for SOC 2 Compliance?
Having a sound password is the most basic form of defense when it comes to cybersecurity. On the other side of the coin, this is why passwords are one of the most exploited controls by cybercriminals.
Unauthorized access and data breaches thrive in an environment with no security posture and weak passwords. Some examples of hackers compromising passwords include the following:
- Phishing Attacks - A type of cyberattack in which the cybercriminal tricks a user into revealing sensitive information, such as a password.
- Brute-Force Attacks - When a cybercriminal tries different combinations of characters to guess a user's password.
- Credential Stuffing Attacks - The use of stolen or leaked passwords from one site to log into another.
These all too real cyber threats are exactly why it is crucial to make sure you have a secure password. Enforce SOC 2 framework to help ensure your company strengthens its overall security. Let's look at some of the SOC 2 requirements which can help prevent potential security breaches.
What are SOC 2 Password Requirements?
SOC 2 requires companies to follow some general guidelines when it comes to enforcing strong passwords. While it doesn't specify exact steps to take towards maintaining SOC 2 compliance, it does name best practices based on the AICPA's Trust Services Criteria and the Committee of Sponsoring Organizations of the Treadway Commission's (COSO) framework. Let's go over a few requirements of the criteria together.
Password Length & Complexity
First up is password complexity and length. A robust password should consist of at least 12 characters. After all, the longer a password is, the harder it is to guess. Couple your minimum 12-character password with a mix of uppercase and lowercase letters, numbers, and special characters, and you've got a strong line of defense. You want to make your unique password as unpredictable as possible.
Password Rotation & History
Next up, we have password rotation and history. Like I mentioned at the beginning of this blog, reusing old passwords is a crime most of us are guilty of. But it can absolutely put you at risk for a data breach. No longer are you required to change your password every 90 days. Instead, only switch out your password in the event of a data breach.

This new requirement encourages the use of strong and complex passwords over the overuse of the same password with one extra character added to the end of it. Use a password manager to keep track of what passwords you are using for different systems. This can also help you avoid using the same one more than once!
Account Lockouts
Account lockouts are ideal for stopping brute-force attacks. After a certain amount of attempts (usually 3), an account will become temporarily disabled. This tactic stops actors from using multiple passwords until they find the right one. Although, this can be a downfall for those of us that aren't great at remembering their passwords. Enter multi-factor authentication (MFA).
Authentication & Authorization
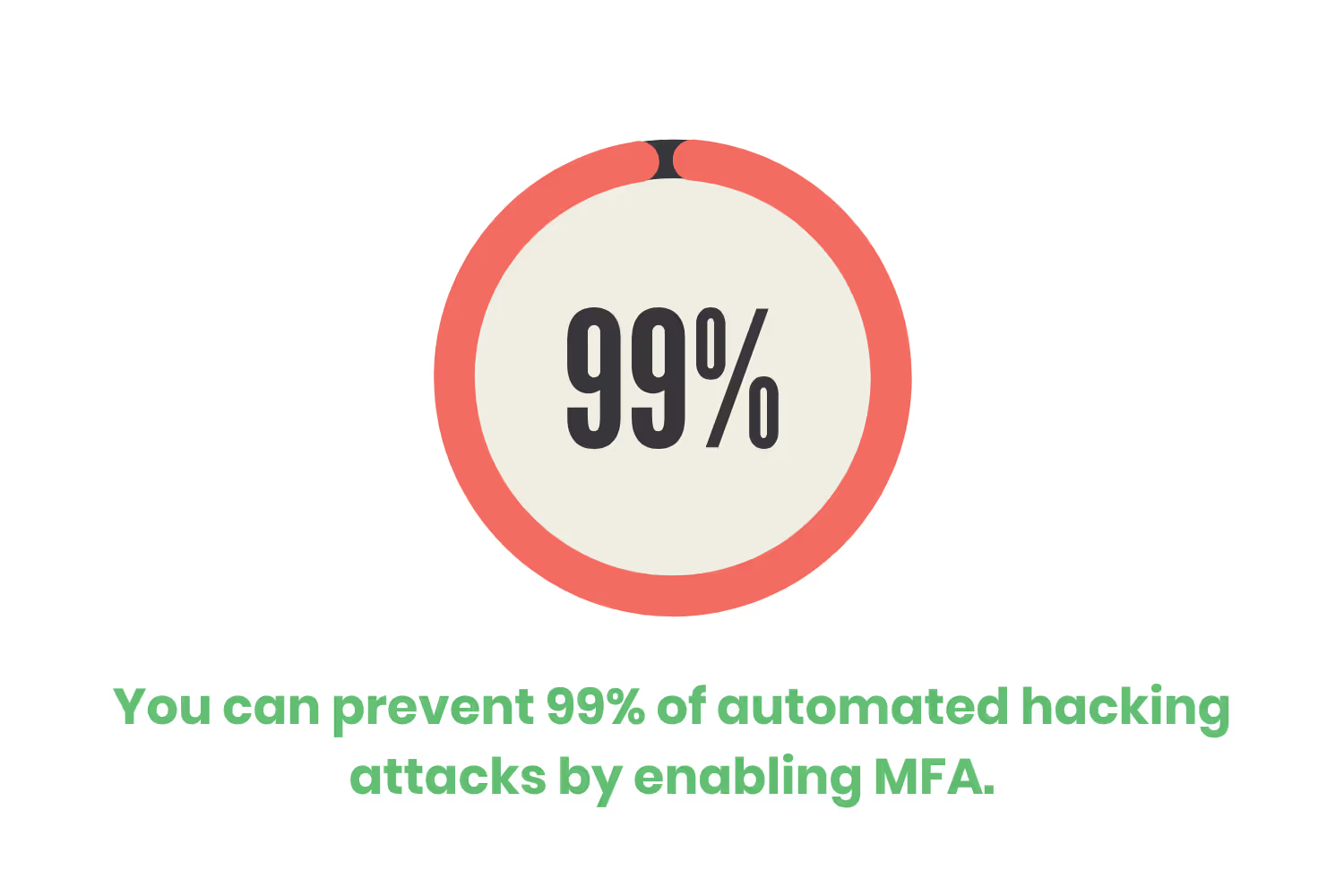
Users must use authentication software before accessing sensitive data or other systems. Such as a MFA. This method adds an extra layer of security. Demanding the user who is logging in to provide additional proof of identification. According to Microsoft, you can prevent 99% of automated hacking attacks by enabling MFA.
More Best Practices to Meet SOC 2 Password Requirements
In order to meet SOC 2 requirements, there are a few particular password practices recommended. First, the implementation of data encryption. It's a non-negotiable in today's day and age. With technology constantly evolving and automated hacking software on the rise, having an extra layer of security never hurts.
During transmission and processing of this data, encryption tools translate said data into a code that needs a particular key to decipher. So even if it gets into the wrong hands, they won't know what they are looking at.
Finally, training your employees to embrace strong password policies is critical for ensuring compliance. A significant fact in data breaches is simply human error. In fact, 74% of chief information security officers say that human error is their top cybersecurity risk.

Building a Culture of Compliance Through Password Policy Enforcement & Access Control
An essential aspect of SOC 2 compliance is to work cybersecurity into your company culture on a daily basis. Regular training with your team, as I mentioned before, is a great place to start. Next, take a look at your SOC 2 password policy. It should state clear requirements and best practices related to password storage. Your documentation should also address implementing strong passwords, password reuse, and secure password management.
Pay attention to how your company enforces password policies. Us tools to help you implement effective password policies such as those that flag password reuse. Having a good system will help you reduce human error while improving accountability. Also, consider tightening access control by using role-based permissions to reduce risk.

Final Thoughts on Meeting SOC 2 Compliance Password Requirements
While SOC 2 does not specify exact password requirements, it does expect some form of implementing robust password policies. Following the tips mentioned in this blog will help you stay on track while being flexible to evolving threats. Such as enforcing password complexity minimums and utilizing MFA features.
Incorporating tools and processes that support your security and compliance goals helps keep your team prepared. By adopting this strategy, along with regular training, you can easily exceed SOC 2 expectations. Keeping your organization out of trouble.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




