The SLAM Method for Fighting Phishing
The SLAM Method sounds, well, aggressive. And I guess you could say it is, but in the sense that you will be better able to defend yourself against cybercriminals. Here’s everything you need to know about the SLAM method for fighting phishing.

Approximately 8 out of 10 data breaches include a human element.
This is according to Verizon’s 2022 Data breach investigation report and is one of many. Many reports that point the finger at the human error when it comes to cybersecurity issues, that is.
That’s a little offensive, right? But it makes sense.
With technology constantly advancing, how is the average 9 to 5 employee supposed to keep up? Especially when 30% of employees don’t think they personally play a role in maintaining their company’s cybersecurity.
But, what your employees may not know is that cybersecurity practices reach far beyond making sure to not share passwords. Something as innocent as opening attachments in an email can result in a company-wide security breach.
Emails from cybercriminals can look just like any ordinary email you might receive. Some of them may even mimic people you know or coworkers. Clicking links or attachments in these emails allows hackers to easily infiltrate your system and collect sensitive information.
If you have never heard of phishing before, this is exactly what the practice looks like.
What is Phishing?
Phishing is a type of cyber attack that’s malicious in nature and aims to steal sensitive information. Sensitive information in this case may look like passwords, social security numbers, credit card numbers, and everything else you would never want a criminal to have access to.
Phishing is one of the most popular methods hackers will use to obtain data today. In fact, according to the 2022 IBM report, phishing is the second most common cause of data breaches at 16%. This follows compromised credentials at 19%. Not to mention, the costliest cause at $4.91 million in average costs for responding companies.
To get a true understanding of the dangers associated with phishing, let’s quickly go through a few of the most notorious real-world examples.
Example 1: Ubiquiti Networks
Spear phishing is an incredibly dangerous form of phishing. In most cases, spear phishing takes the form of “CEO Fraud”.
CEO Fraud spear-phishing attacks take advantage of their target by sending them an email that appears to be from a known or trusted sender…in most cases their boss.
Cybercriminals know that most employees are eager to please the CEO of their company or another high-level executive. This is why this form of phishing tends to be quite successful when it comes to requests for money transfers.
An employee at Ubiquiti Networks in California learned their lesson the hard way. Because they fell for a CEO fraud scam, the company lost $39 million dollars.
Example 2: Fortune 500s
This next example sounds like something out of a movie. Evaldas Rimasauskas would carry out one of the largest phishing scams to this day. In 2017, Lithuanian authorities arrested him on some pretty wild accusations.
Evaldas in the years prior had sent fake invoices to large companies including Google and Facebook. Over these years the man ended up stealing over $120 million dollars in these fake payments.
Large companies tend to handle large amounts of transactions in a day, so the idea that he was able to sneak in these invoices throughout the years isn’t entirely unbelievable! Evaldas even had the money transferred to his own bank accounts.
In the end, the authorities regained about half of the stolen money in the scam. Rimasauskas would face a sentence of 5 years in prison, with 2 years of supervised release. This along with a court order to pay back the rest of the stolen money.
Example 3: Ukraine's Power Grid
This phishing attack is one of the most famous of all time. In 2015, a cyberattack took down Ukraine’s power grid. An unidentified hacker took direct control of an operator’s system in a control center responsible for providing power to Ivano-Frankivsk residents.
This attack left hundreds of thousands of people without electricity. The incident was especially detrimental considering it took place during the month of December in freezing temperatures.
The cyberattack affected businesses and individuals and involved a long-standing campaign of phishing emails used to steal information from system administrators. Ukraine looked to Russia first as the attack created a blackout across the country, though the perpetrators still remain at large.
With this costly security threat on the rise, there are ways to combat cyber attacks in your day-to-day routine. Let’s go over the SLAM Method!
What is The SLAM Method in Phishing?
The SLAM Method sounds, well, aggressive. And I guess you could say it is, but in the sense that you will be better able to defend yourself against cybercriminals.
Think of this as a crash course in cyber security training.
Of course, this should never substitute actual training, but instead offers an easy way to remember some basic security practices.
SLAM is an acronym that helps remind you of what to look for when it comes to possible phishing emails. When you are able to easily identify these threats, your likelihood of costing your company (or even you personally) financial loss is greatly diminished. So listen up!
SLAM stands for…
- S- Sender
- L- Links
- A- Attachments
- M- Messages
This mnemonic device can help you and your employees target any suspicious email that comes your way. Just follow the cues in the acronym!
Sender
“S” stands for sender, or in other words the person who is sending you the email. Phishers are smart in that they lure in their prey by acting as a reputable sender. They could act like a legitimate company, your boss, another coworker, etc.
This is why the first step when looking for suspicious activity in your inbox is to analyze a sender’s email address before you open it. An easy way to inspect an email address without having to open the email itself is by hovering your mouse over the sender’s name.
Doing so will reveal the email address of the sender, letting you know where it came from and allowing you to inspect for any misspellings or inconsistencies. A valid email address should have no misspellings or strange characters.
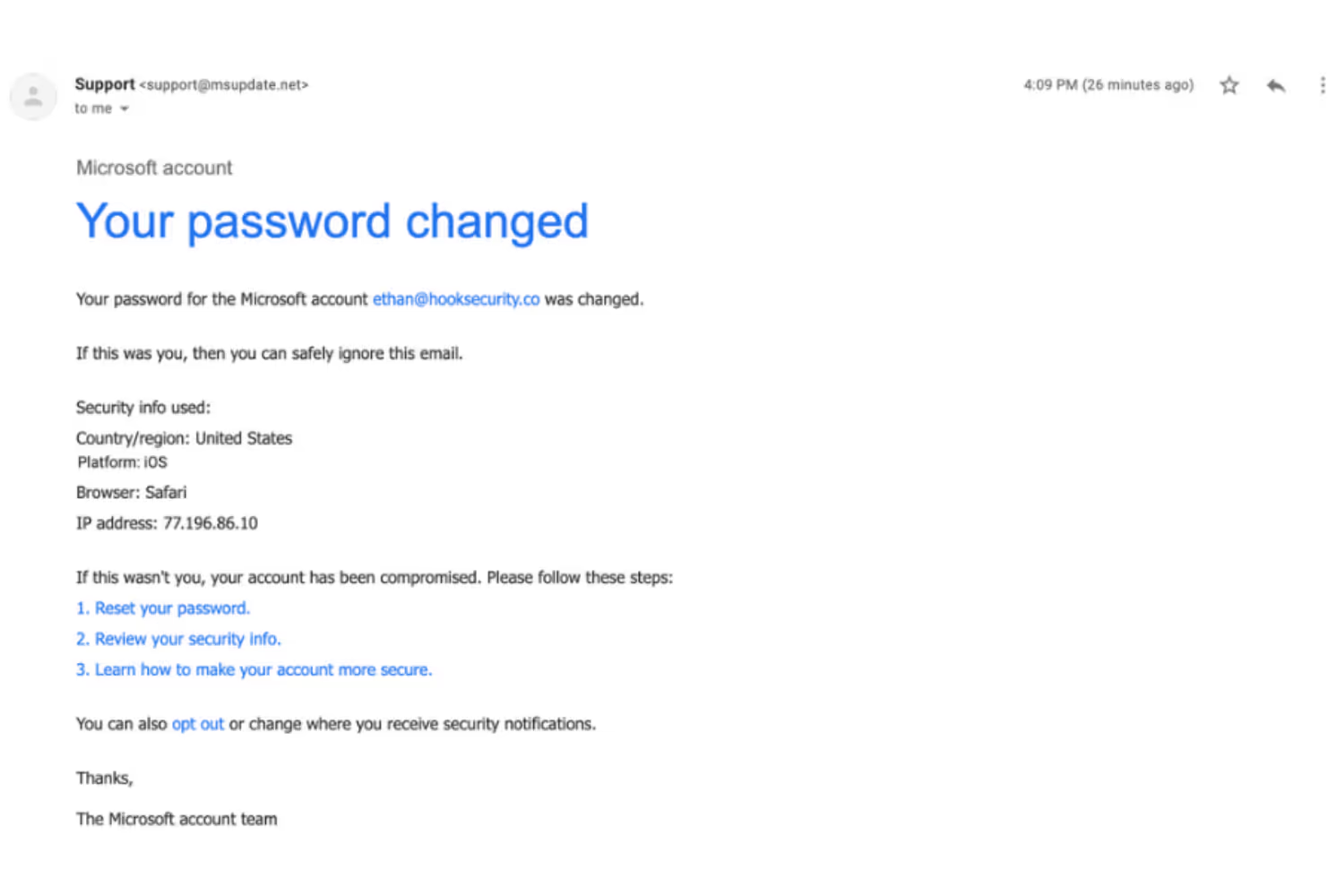
An email that’s coming from a company (in most cases) should have the company name in the domain. For example, an email that is coming from support@msupdate.net is not an actual Microsoft email address.
Links
Phishing emails often have links that enable a hacker to steal a user’s login information. By clicking on these links and following the instructions given, hackers can easily obtain sensitive information and infiltrate the desired network.
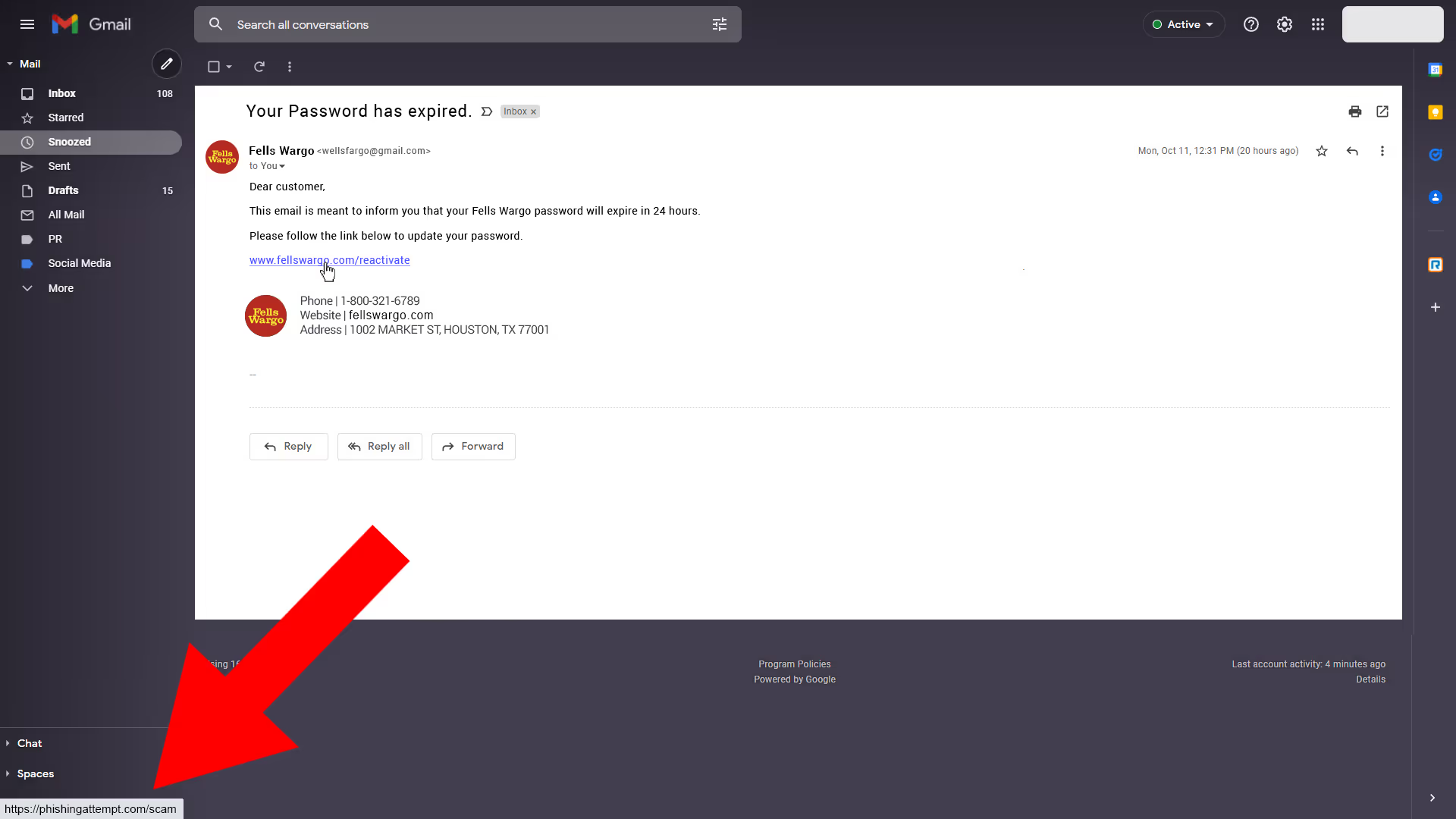
You can hover over these links without clicking them to further investigate the URL and find out where it’s directing you. Misspellings in the link address and inconsistencies between that link and the alleged company’s website URL is another red flag. Whatever link you’re receiving from a valid company should have the same domain as their website.
If you’re unsure if a link sent to you is legitimate, manually input that company’s website into your browser to compare. Or you can contact the company/sender by phone for confirmation that the email is valid.
Attachments
Similarly to links within an email, you should avoid opening email attachments from senders you do not know. If you think you do know the sender, still practice caution while opening an unsolicited attachment. We know that hackers are smart enough to use reputable senders when infiltrating a user’s system. Remember the “S” in sender!
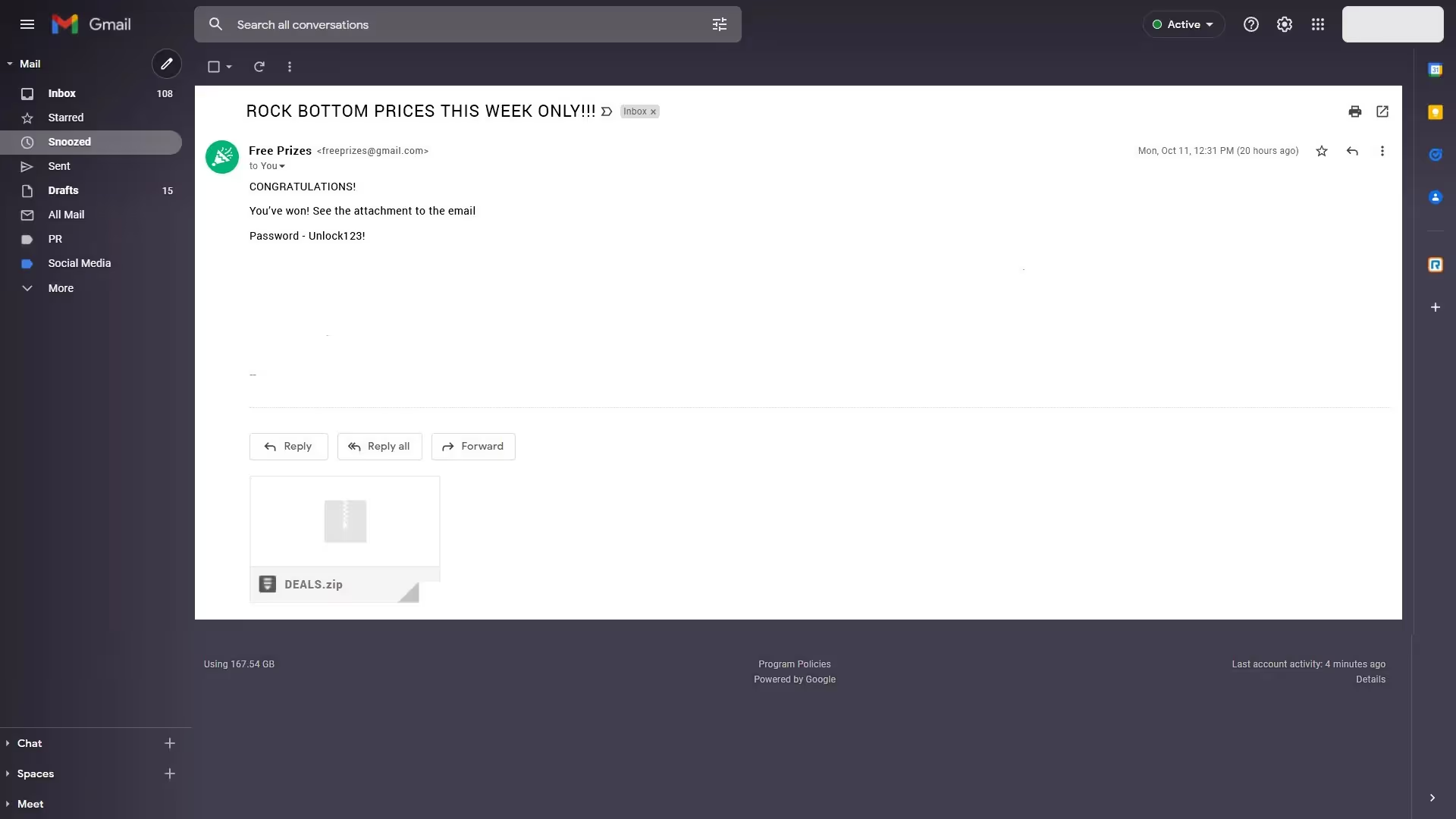
If possible, reach out to the sender directly to confirm the attachment is legitimate. Especially if it is an email that is business related. There is a chance that an attachment is unsafe even if it’s from the correct sender. This could be due to the hacking of the sender’s address or a configuration problem.
Attachments can contain malware, ransomware, and/or other devastating computer viruses.
Here are a few questions to ask yourself before opening an attachment sent to you from anyone, really:
- Does this person usually send you attachments?
- Does the name of the attachment match up with previous submissions from this sender?
- Is the attachment format the same as the previously sent attachments?
If the answer to any of these questions is no, it is best practice to pick up that phone (or walk down the hall) to verify the email is legitimate.
Message
When in doubt, pay attention to the content within these suspicious emails. Oftentimes your answer as to whether the sender is authentic or not is in the details of the message sent. These details might include generic greetings, grammatical errors, strange wording, and misspellings among other things.
Companies will often use a spell-check feature before sending out emails. Because of this, if you see misspellings or grammatical errors you should be suspicious of possible fraud. Another red flag when it comes to dealing with a possible phishing email is the lack of a subject line.
Cybercriminals will often leave a subject line empty on purpose to make sure the account they are targeting is legitimate. If they do not receive an automated bounce response saying the email is not valid, they can send the phishing email.
What to Do When You Recognize a Phishing Email
Okay, so you used the SLAM Method and discovered that you have come into contact with a phishing email. What should you do now? Here are some steps to take after identifying this cybersecurity risk:
- Mark the email as spam.
- Report the email to your management team so they can alert the company.
- Report the phishing attempt to your IT department so they can blacklist the domain address of the sender.
- Do not forward the email to anyone and do not open any links or attachments.
No matter your position within a company, you hold the responsibility to stop a cybersecurity threat from spreading like wildfire. The sooner you raise the alarm of a suspicious email, the better.
Conclusion
While utilizing the SLAM Method for phishing is a handy tool, it cannot take the place of practicing cybersecurity compliance and attending regular training. Learning how to protect your business from cybersecurity breaches and how to mitigate them if they happen can save you from needlessly losing money.
Industry standards and regulations are always changing and evolving, so taking annual training allows you and your employees to stay up to date with the latest policies. Making sure to invest in a cybersecurity program offers you:
- Reputation protection and maintains client trust
- Builds customer loyalty
- Helps identify and prepare for data breaches
- Protect Intellectual Property such as trade secrets and software code
Think of cybersecurity as having a safety net but also, a competitive advantage.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




