How to Spot a Phishing Email in 5 Ways
How are you supposed to sift phishing emails into your trash? It all starts by understanding how to spot a phishing email…sending awareness emails also helps but that’s a different story.

In 2021, the number of emails sent and received each day worldwide averaged about 319.6 billion. On top of that, advertising email has seen higher click-through-rates than social media. For reference, a click-through-rate (CTR) is the percentage of people who click provided advertisement links and visit a web page.
In particular, Statista Research Department reported that between 2019 and 2020 the CTR for email advertisements in Belgium had a rate of 5.45 percent. Meanwhile, the global average CTR for social media was only 1.3 percent in that same timeframe.

All this to say, emails are still one of the leading forms of communication despite new methods. This is especially true when it comes to advertisements. The rise of utilizing emails for remote work scenarios in a post-pandemic environment raises the risks associated as well.
According to the annual Internet Crime Report conducted by the FBI, the number of companies that filed complaints of phishing attacks jumped 182% between 2019 and 2021.
But with the average person receiving so many emails in a single day, how are you supposed to sift the phishing ones into your trash? It all starts by understanding how to spot a phishing email…sending awareness emails also helps but that’s a different story.
What is Phishing
Phishing is a fun word, but that’s about the extent of its positive connotation. In reality, phishing emails are malicious and aim to steal your information. This type of cyber attack looks to be an email from a reputable company at first glance but it’s a hacking strategy.
Cybercriminals send emails as bait in hopes of gaining access to personal information. This information can include passwords, social security numbers, credit card numbers, and more.
A “phisherman” will first use public resources to collect information about their target. The victim's name, job, or even interests and activities can help the hacker create a reliable email.
These emails may also have a link attached that connects victims to a malicious website. This is often included in the hopes that the user will click the link. If the user does click this link, it will lead them to a fake website where the hacker would then attempt to collect private information. These websites may impersonate the user’s bank, university, workplace, you name it.

Email phishing messages will usually have at least one of the following goals:
- Causing a user to click a link to a malicious website, which installs malware on their device
- Causing the user to download an infected attachment that deploys malware
- Causing the user to click a link to a fake website and reveal personal information
- Causing the user to reply to the email and provide their personal information
So, when it comes to any private information that could help steal your identity? A cybercriminal wants it and anyone can be a target. You may think that this should be easy to recognize and avoid. But last year 83% of businesses said they experienced a successful phishing attack.
How to Spot a Phishing Email
As one of the most prevalent cybercrime techniques today, you’ve likely come across at least one phishing email. I know my spam folder has tons of emails from addresses I’ve never seen. Some even seem to be impersonating social media sites.
That’s no coincidence.
The latest Brand Phishing Report for 2022 highlights brands that were most imitated by hackers in phishing attempts. So far LinkedIn holds 52% of all phishing-related attacks globally. Social media network emails have taken over previous methods of phishing. The industry has even overtaken shipping, retail, and technology categories.
Some phishing emails are evident from poor copywriting and improper use of fonts and logos. Yet cybercriminals continue to become more sophisticated. Hackers continue to strive to make more authentic-looking emails. Some even use professional marketing techniques.
Example 1: Empty Subject Line
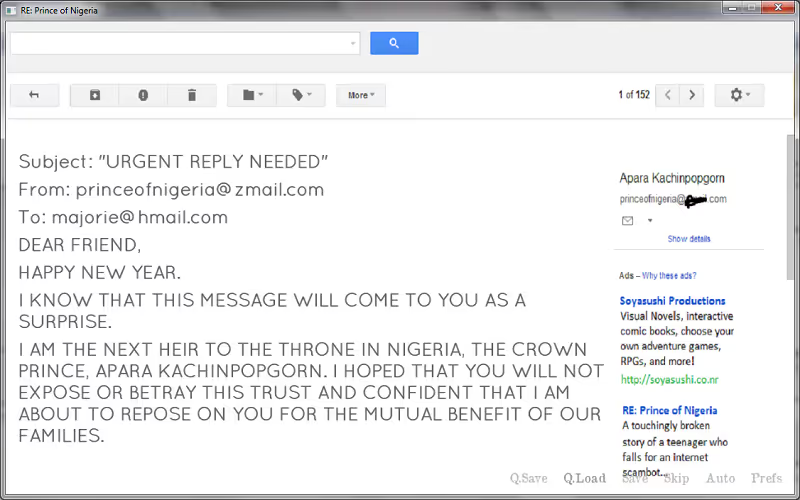
When receiving an email from a reputable source, you expect it to contain a subject line. Some sort of sign about what the email is going to contain. But what happens if you get an email without a subject line or even no content in the body of the email? Sounds suspicious, right?
According to the Expel Quarterly Threat Report 2022, 67% of scammers leave the subject line empty in malicious emails. This is one of the largest red flags when it comes to phishing.
Many cybercriminals do this to make sure an email account is legitimate before sending a phishing attack. The scammer will wait for an automated bounce response saying the email is not valid. If they don't receive one, they will assume the email is valid and launch more intricate attacks.
Example 2: Using Fear or Urgency
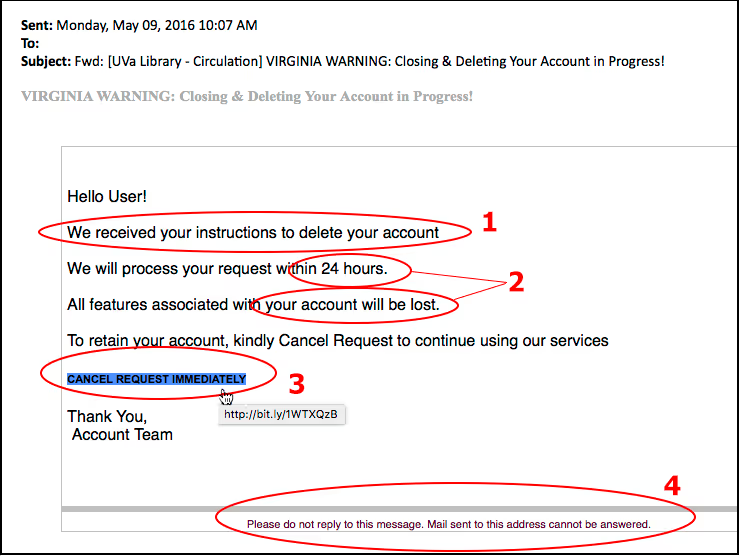
Phishing attacks are a form of social engineering. Cybercriminals will take advantage of psychology to manipulate users into giving their information. Using emotions like fear or excitement can motivate quick responses from humans.
These emails will express there is a threat of negative consequences if action by the user is not taken. Or that the offer sent to the user is only for a limited time and they need to act now.
Phishers know that the idea of bad news or missing out on something too good to be true are good ways to get someone to act quickly. Make sure to treat these types of emails with skepticism and take note of any other red flags the message may contain.
Example 3: Calls to Action

Be wary of emails from unknown domains that are asking you to do non-standard actions. For example, if an email from an unknown IT company asks you to download a software update but that is typically handled within your company.
One of the first phishing emails to appear on the scene was the infamous “Nigerian Prince” scam. You know, the one where a scammer poses as someone of wealth or importance and needs your urgent assistance. A tale as old as time.
Usually, they will say something along the lines of needing to transfer a large amount of money out of their country. In return, you will receive a part of their wealth. All they need is your bank account number and boom… your account is empty.
Example 4: Message Errors
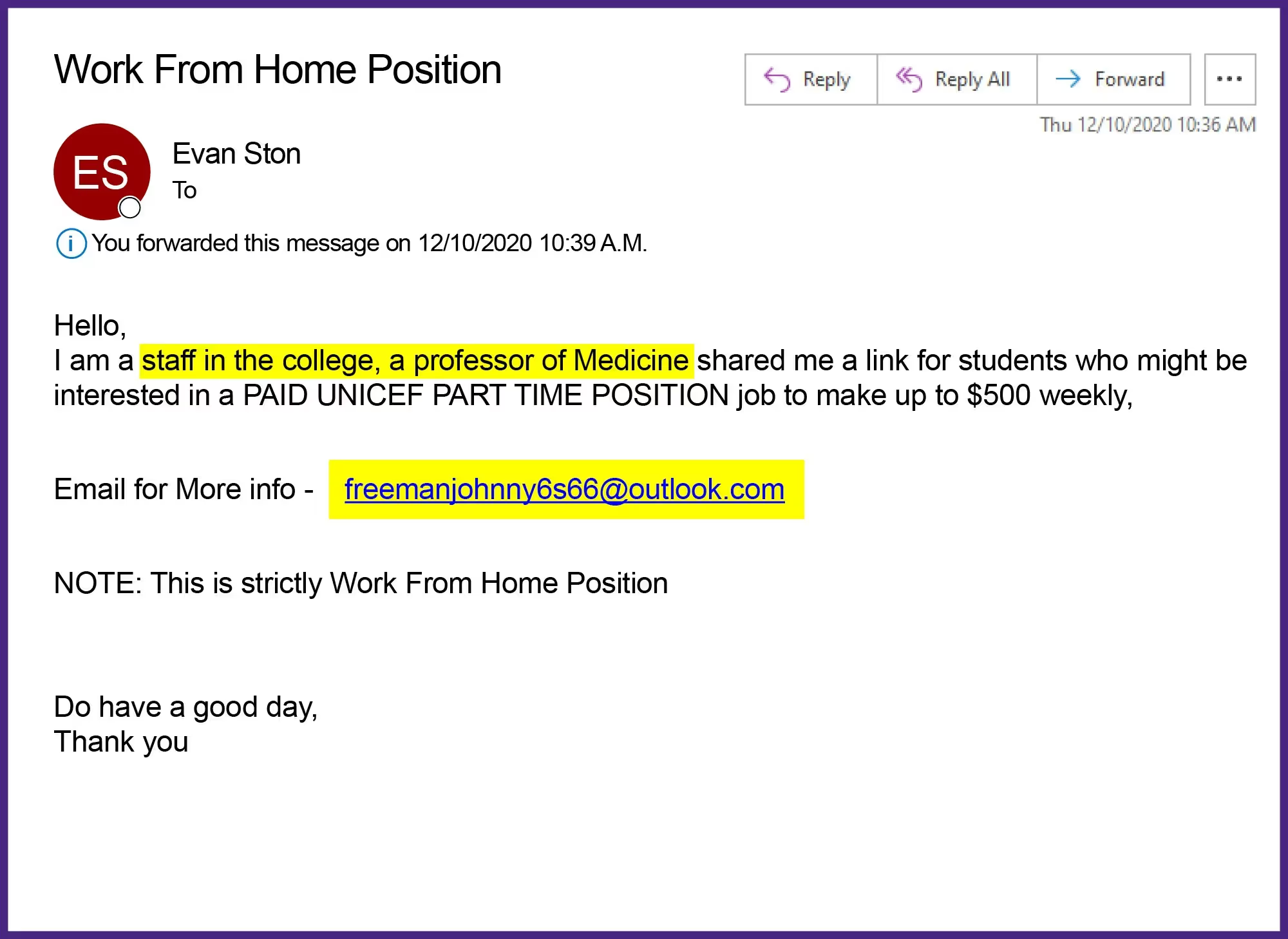
Poorly written emails and the use of bad grammar are one of the most common signs of a phishing scam. Many companies use a spell-check feature for their outbound emails. Seeing misspellings and grammatical errors should raise suspicion.
Some hackers will cause errors in their emails on purpose. This is to target and file away less observant people who make easier victims.
Along with this, be sure to tread lightly with emails that contain odd message styles. Like receiving an email that doesn’t sound consistent with the sender’s usual tone or language. If Jenny from work sounds a little too casual, or if your friend Billy comes off too formal, these are signs that something might not be right.
Example 5: Domain Redirect
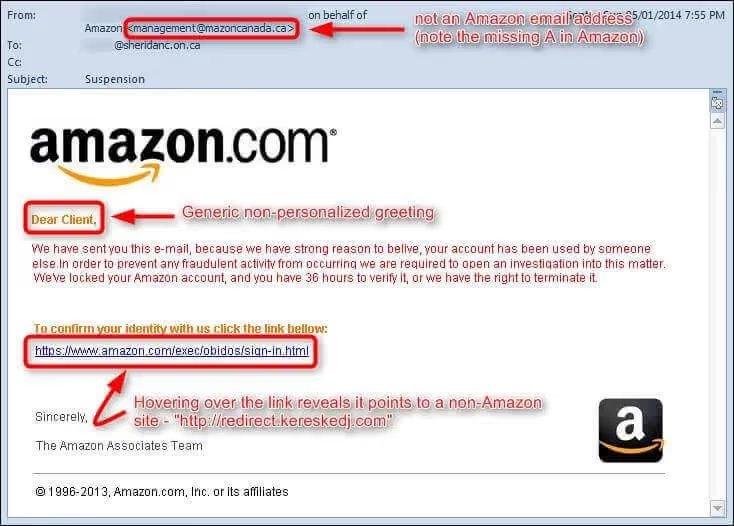
Last, be wary of emails from public domains such as Gmail. Also, note that phishing emails will use domains with slight differences in spelling and the use of symbols.
Most companies have their domain names. If you need to double-check, a quick google search will likely bring you to a company’s actual email address.
Conclusion
According to the Cyber Security Breaches Survey 2022, around 82% of senior management rate cybersecurity as a ‘very high’ or ‘fairly high’ priority. It’s important to be able to equip yourself and your employees with the proper tools and knowledge to avoid and report scams.
Sharing these phishing facts and statistics is helpful, no doubt. Unfortunately, it's nowhere near the proper phishing training an employee should have.
Phishing campaigns are becoming more prevalent and harder to detect. Malware in general is evolving at a rapid pace. But prioritizing training and educating your employees annually on cybersecurity compliance is the best defense strategy.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)