NIST SP 800-171 Rev 3 Crosswalk of Assessment Objectives (XLSX Included)
On May 10, 2023, the National Institute for Standards and Technology (NIST) published a new draft of Special Publication (SP) 800-171. We’ve created a

On May 10, 2023, the National Institute for Standards and Technology (NIST) published a new draft of Special Publication (SP) 800-171. NIST plans to close the public comment period for the initial public draft of revision 3 on July 14, 2023. They expect to publish at least one more draft before the final publication in early 2024.
Creating Assessment Objectives from Rev 3
NIST SP 800-171A is the assessment guide to SP 800-171 security requirements. There are a total of 320 assessment objectives within Revision 2. NIST has not yet released an updated assessment guide for the initial public draft of Revision 3.
NIST provided a detailed analysis of the changes between Revision 2 and Revision 3, and a prototype CUI Overlay. All NIST published material around Revision 3 currently focuses on the practice level. A crosswalk of assessment objectives from Revision 2 to Revision 3 would provide:
- Mapping the existing 320 assessment objectives into Revision 3
- Quantifying the total number of assessment objectives in Revision 3
- Quantifying the number of new assessment objectives beyond the existing requirements
The initial public draft of Revision 3 is a derivative from SP 800-53 Revision 5. The assessment guide (SP 800-171A) will be a derivative of SP 800-53A. We set out to create the first draft of SP 800-171A based on the initial public draft of Revision 3.
We started by updating the mapping table of Appendix D in Revision 2 to the SP 800-53 Revision 5 controls. We mapped each of the current 320 assessment objectives to the corresponding determination statements found in SP 800-53A. This created the first half of the bridge we need to crosswalk SP 800-171 Revision 2 to Revision 3.
NIST provided the source SP 800-53 Revision 5 controls for each security requirement in the initial public draft of SP 800-171 Revision 3. We refined these mappings to identify how specific portions of new control statements map to controls from SP 800-53 Revision 5. For example, according to the initial public draft, 3.1.6 maps to AC-6(5) and AC-6(2).
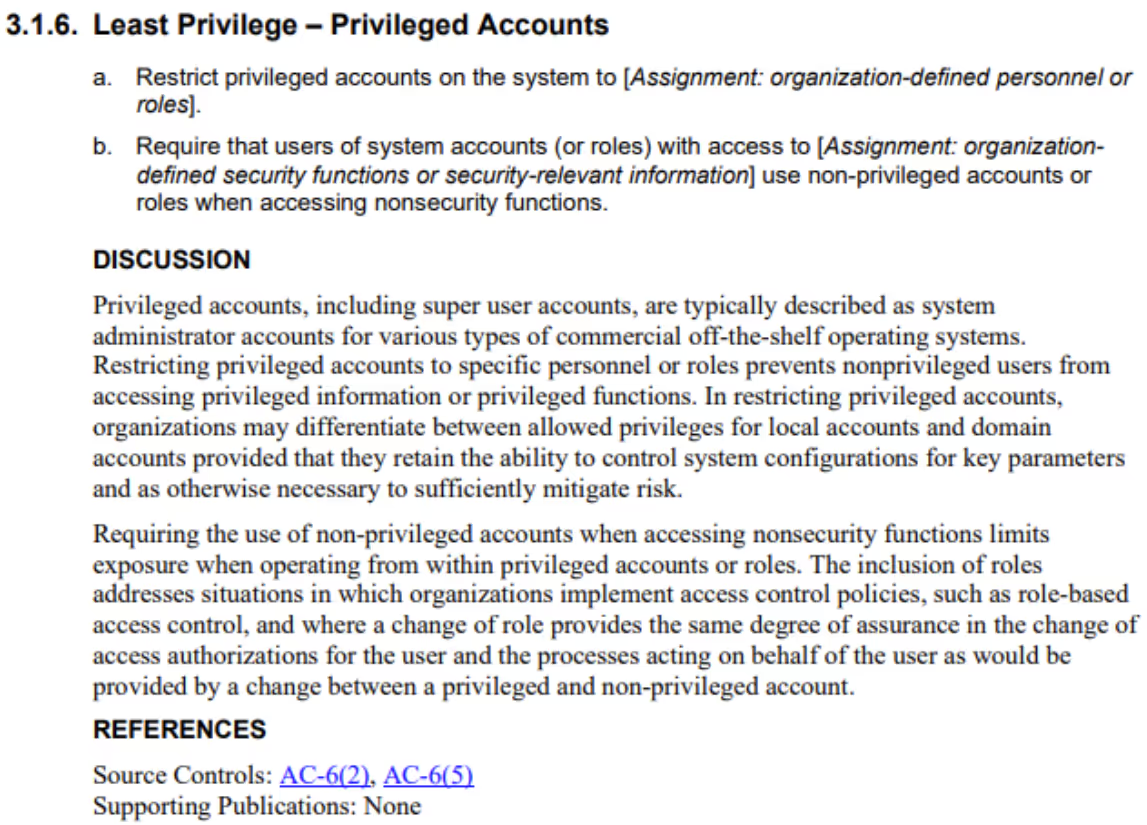
Image Source: NIST SP 800-171r3 initial public draft
We enhanced the mapping to show that (a.) maps to AC-6(5) while (b.) maps to AC-6(2):

This helped identify assessment objectives and organization-defined parameters (ODPs) from SP 800-53A. In the same example, the text within 3.1.6 matches exactly with the SP 800-53 control. So we related both ODPs (2) and assessment objectives (2) from SP 800-53A to 3.1.6.
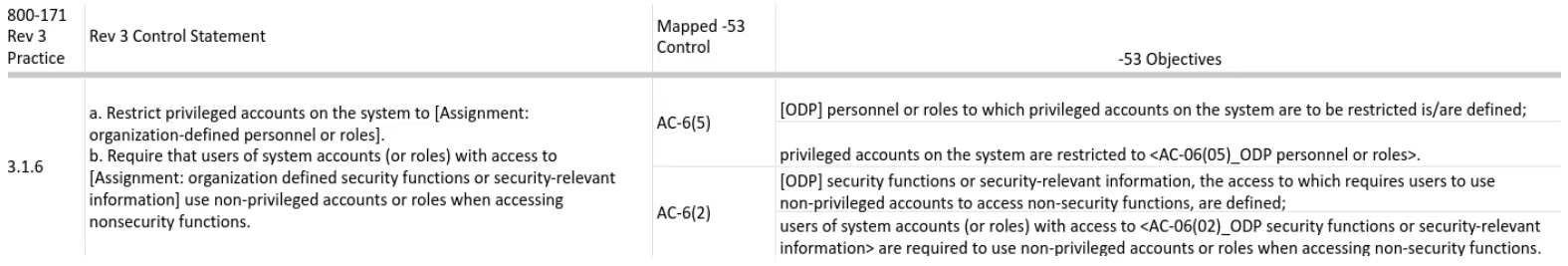
We used this logic to identify assessment objectives for each security requirement. Then, we went back and created a numbering scheme for the objectives. We followed the current SP 800-53A numbering scheme as we assigned them an identifier.
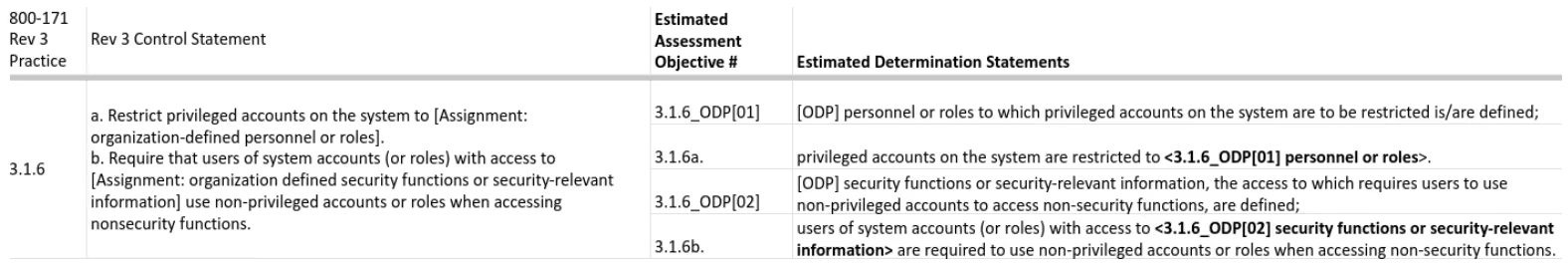

Mapping Assessment Objectives
The resulting crosswalk of derived assessment objectives was cumbersome. We wanted to create something that was easy to navigate and easy to understand. So we designed a lightweight excel-based tool.
There are two tabs. The first tab maps the existing requirements into the future requirements. We have limited visibility into a single practice at a time. This view helps to reference what you’ve already done in Revision 2 into what you might have to do in Revision 3. It also identifies requirements now considered not related to the confidentiality of CUI.

The other tab maps the new derived Revision 3 objectives back to the existing 320 objectives. This makes it easier to pull in work you’ve already done from Revision 2. It also helps you see what new requirements you may need to address.
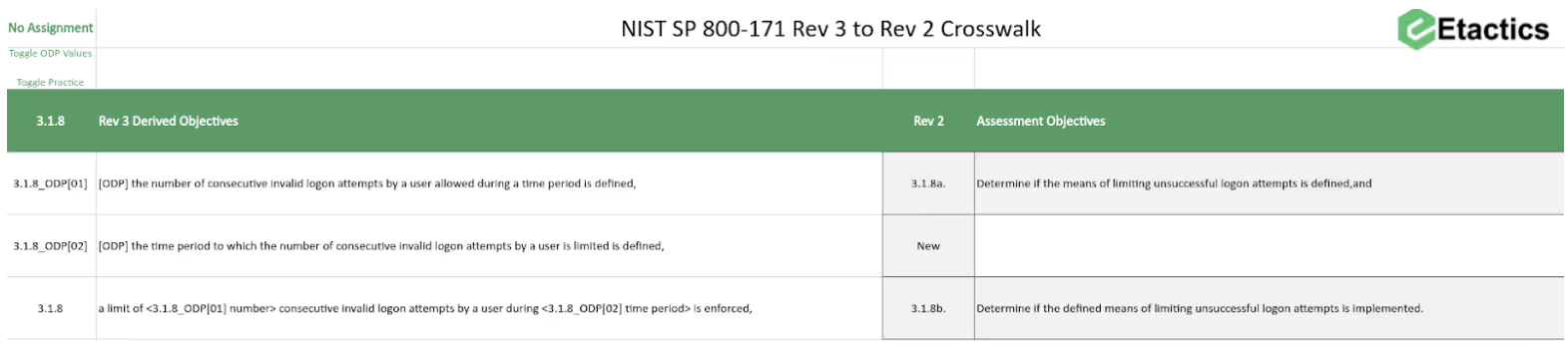
In either tab, you can select a practice in the upper left hand corner and the table below will update. This provides for an easier to use interface without the need for a complex master table. Feel free to create your own derivative work from what we’ve started.
Elaborating on the Summary of Significant Changes
The following sections explore the significant changes identified by NIST. For each summary point, we have added details from our analysis of the material.
Streamlined Introductory Information
We ran sections 1 and 2 through the Hemingway Editor and to quantify this statement.
- Revision 2 included 3,181 words written at a grade 13 reading level.
- The Revision 3 draft contains only 1,642 words written at a grade 12 reading level.
New tailoring of SP 800-53B
NIST modified the number of security requirements and their groupings. Here is a summary of the changes (Revision 2 to Revision 3):
- 14 Families to 17 Families
- 110 Security Requirements to 109 Security Requirements
- 320 Assessment Objectives to ~ 509 Assessment Objectives & ODPs
- 61 non federal organization (NFO) controls to 25 NFO Controls
NIST also introduced “not applicable” as a new tailoring category. They applied this tailoring to two entire domains. This included Program Management (PM) and PII Processing and Transparency (PT).
Eliminated basic and derived labels
Revision 2 obtained security requirements from FIPS 200 and SP 800-53 Revision 4. For example, the basic security requirement 3.1.1 comes from FIPS 200:

Revision 3 only uses SP 800-53 as the authoritative source. This is one of the reasons for significant changes within some of the controls.
Increased specificity to clarify assessment scope
The use of FIPS 200 in Revision 2 created a lack of specificity within the basic set requirements. Aligning Revision 3 to SP 800-53 reduces subjectivity in the requirements.
Introduced organization-defined parameters
NIST suggests that ODPs increase flexibility and helps better manage risk. Federal organizations may specify values for the designated parameters as needed. ODPs containing assignment and selection operations provide flexibility to customize the requirements. Once specified, the values become part of the requirements.
We inventoried 117 ODPs by compiling the crosswalk of Revision 3 to NIST SP 800-53A. The concept of using ODPs is not new to SP 800-171. In fact, we mapped 46 of the existing 320 assessment objectives into the 117 new OPDs. For example, 3.11.1a. states:
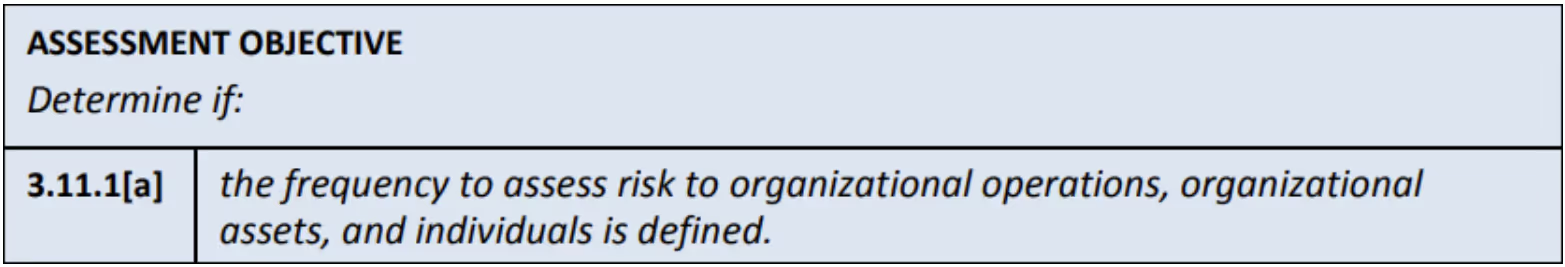
This objective becomes an ODP in Revision 3:

The initial public draft of SP 800-171 Revision 3 maps 3.11.1 to the RA-3 in SP 800-53 Revision 5. The assessment guide (SP 800-53A) provides the exact organization-defined parameter:

Here is where our crosswalk resource took an interesting turn. There is precedent for reciprocity between FedRAMP Moderate and NIST SP 800-171. FedRAMP defines some of the SP 800-53 ODPs required to meet the various baselines. We mapped 67 ODPs from Revision 3 to the FedRAMP Moderate Baseline.
We included the ability to use these values in our spreadsheet. You can toggle on the FedRAMP Moderate or High Baselines. This populates the ODPs and the objectives they appear within. For example, 3.6.3 as shown without defining any ODPs:
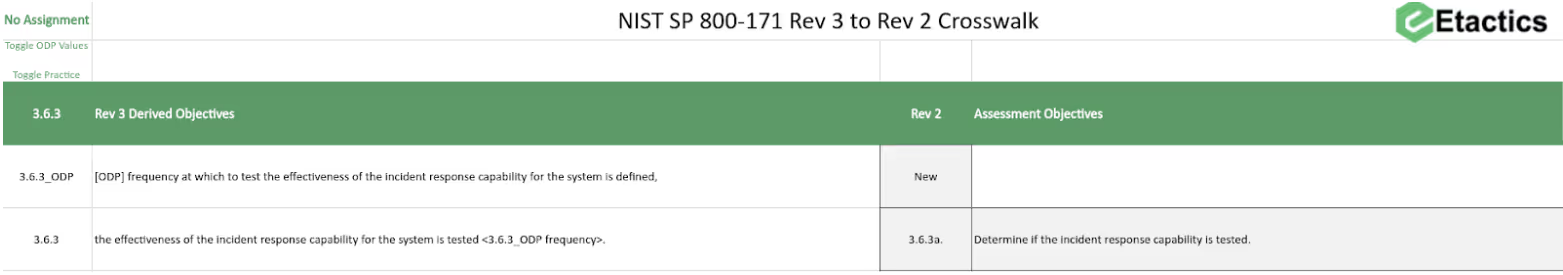
Toggling to the FedRAMP Moderate standard defines the ODP and updates the objective:
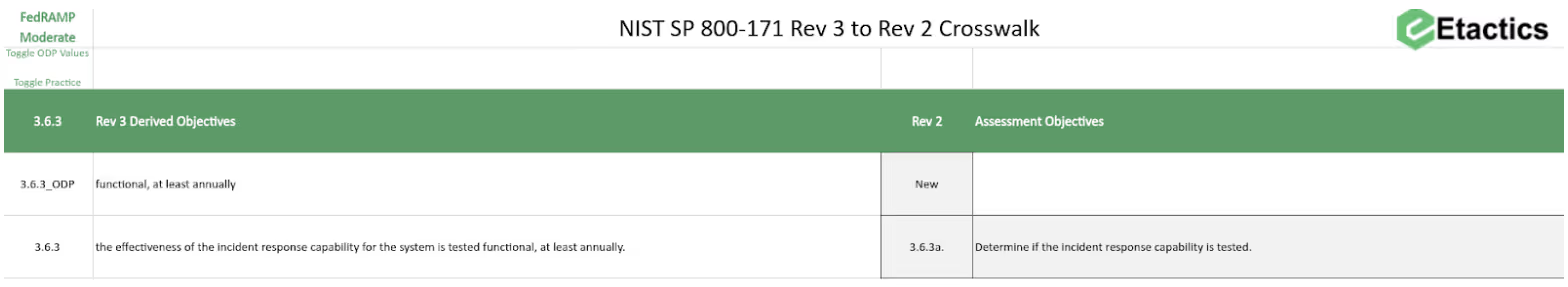
Many of these ODPs require you to perform tasks on a scheduled frequency. Frequencies can include weekly, monthly, or annual tasks. We’ve woven the ability to document these tasks into our compliance solution.
Grouping security requirements
Revision 3 reduces the overall number of security requirements from 110 to 109. As we discussed the number of assessment objectives and ODPs has increased. By grouping requirements and adding new ones, the number of objectives has increased.
Removed outdated and redundant requirements
Only 8 assessment objectives from Revision 2 do not map into an objective from Revision 3. Only 4 practices from Revision 2 do not map into Revision 3 requirements.
These include: 3.5.6; 3.5.8; 3.7.1; and 3.13.14
The only other objective that we could not map into Revision 5 was 3.14.5a.
Conclusion
The initial public draft of Revision 3 presents new series challenges. We hope this resource helps you map your current work into the next iteration of SP 800-171. We hope it helps you better understand new requirements that may arrive in 2024. We will continue to update this resource. If you’re open to exploring alternatives to excel, feel free to book a demo to learn about how K2 Compliance can help.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




![[ANSWERED] What is a Risk Register?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68acfd6e02390e12a4383c6f_whatisariskregister_1223.avif)