170+ Phishing Statistics: Open Rates, Victims and Impact
Here is our list of over 170 phishing statistics. The information will help illustrate the breadth, depth, and severity of cybercrime.

Social engineering often takes the form of phishing scams. This type of cyber attack is one of the most prevalent and dangerous types of cybercrime.
Not only is it effective for hackers to gain sensitive information, but the majority of organizations around the world face attacks regularly.

Here is our list of over 170 phishing statistics. The information will help illustrate the breadth, depth, and severity of cybercrime. More specifically, the statistics below will showcase the frequency of phishing attacks, delivery methods, and victim profiles. We will also discuss how hackers get their victims hooked and trick them into clicking on attachments or website links.
The Frequency of Phishing Attacks
Many companies around the world saw an increase in email phishing attacks since March 2020. The threat of phishing is very real, and businesses feel the fear every time they get an email in their inbox.
Yet very few companies offer phishing awareness training to their employees. Sometimes the training is only offered once an employee starts working for the company. About 1 in 5 organizations give employees phishing training once a year.

Needless to say, the majority of the workforce lacks awareness when it comes to phishing, leaving companies vulnerable to the threat. In turn, this leaves companies vulnerable to data breaches and attacks.
Vishing, smishing, and pharming, which are all forms of phishing, were some of the most prevalent threats in 2020 to US companies. Non-payment/non-delivery, exertion, personal data breach, and identity theft are next in line.
Since the top three cybersecurity threats are forms of phishing, it is important to explore the frequency of phishing attacks. How often do they occur? How many people are potentially affected? Are emails really the main form of phishing attacks? Let’s find out…
- The FBI found that phishing was the third most common type of reported scam. (Proofpoint)
- This remained true regardless of size, industry, or location.
- In 2019, 1 in every 99 emails is a phishing attempt. (Verizon)
- In 2020, 54% of all digital vulnerabilities involve phishing emails. (Statistia)
- Around 91% of data breaches happen because of phishing. (Deloitte)
- Phishing attacks might increase 400% year-over-year. (FBI)
- 22% of data breaches involve some type of phishing. (Verizon)
- 90% of IT decision-makers believe that phishing attacks are a top security concern. (PhishMe)
- 36% of breaches involve phishing. (Verizon)
- 85% of breaches involve a human element. (Verizon)
- The average employee will receive 14 malicious emails per year. (Tessian)

- Email scams target some industries more than others. (Cisco)
- For example, retail workers receive an average of 49 emails per year.
- Phishing attacks against cryptocurrency companies represent 6.5% of all attacks. (APWG)
- 42% of workers say that they took questionable actions regarding cybersecurity and failed to follow phishing prevention best practices. (Proofpoint)
- Dangerous actions include…
- Clicking on an unknown link
- Downloading a file
- Exposing personal data
- Dangerous actions include…
- In 2018, 83% of organizations said they experienced phishing attacks. (ProofPoint)
- This is up from 76% of organizations in 2017
- Phishing attacks increased 510% from January 2020 to February 2020. (Webroot)
- Business Email Compromise scams (BECs) targeted around 31,000 organizations in Q1 of 2020 alone. (Semantec)
- The most common attacks against organizations were BECs. (Armorblox)
- These occurred 53% of the time.
- Next on the list are phishing messages with malware infections that occur 49% of the time.
- The third most common type of attack was account compromises which happened 47% of the time.
- Throughout 2020, 1 in every 4,200 emails was a phishing attempt. (Semantec)
- Organizations with 1–250 employees will experience 1 malicious email for every 323 safe emails. (Semantec)
- Organizations with 1001–1500 employees, will experience 1 malicious email for every 823 emails. (Semantec)

- In 2020, 84% of organizations witnessed at least one phishing or ransomware attack. (Proofpoint)
- 35% of breaches in North America involved social engineering. (Verizon)
- 70% of breaches in the Asian Pacific involved social engineering. (Verizon)
- 93% of social engineering attacks are phishing-related. (Symantec)
- Roughly 65% of cyber attackers used spear phishing emails as their primary attack vector. (Semantec)
- 45% of all email is spam. (Statista)
- Some researchers believe that number to be closer to 75%
- According to a survey, phishing incidents rose by 220% after the pandemic. (IRONSCALES)
- The same survey found that 81% of IT directors/managers experienced more phishing email attempts since the start of the COVID-19 pandemic.
- 90% of IT professionals say that email phishing is one of their top concerns. (IRONSCALES)
- Over 60% of surveyed security professionals say that phishing campaigns increased more dramatically during the pandemic compared to other cybersecurity schemes. (Microsoft)
- Social engineering (including phishing) continued on its upward trajectory, accounting for 30% of all attacks. (APWG)

- 69% of breaches within the realm of public administration involved social engineering. (Verizon)
- There were 366 healthcare data breaches in 2018. (ModernHealthcare)
- This translates to the exposure of over 13 million records
- A sextortion botnet sent up to 30,000 emails an hour at the end of 2019. (BBC)
- Someone will discover 90% of phishing attacks in an environment that uses an SEG. (Cofense)
- Phishing tends to peak around holiday times. (Cisco)
- Researchers found that phishing attacks soared by 52% in December.
Phishing Delivery Methods
The majority of social engineering attacks come in the form of phishing emails. A third of IT professionals report that they experienced an increase in social engineering attacks in the form of non-emails. This includes video conferencing platforms, workforce messaging platforms, cloud-based file-sharing platforms, and SMS.

The largest form of phishing is something called Software-as-a-Service, abbreviated as (SaaS). These types of attacks are responsible for over a third of phishing attempts. But this is just one of many types of phishing delivery methods. Below are some phishing statistics that can shed light on delivery methods.
- Some experts estimate that 1 in 99 emails is a phishing attack. (SIBS Paywatch)
- This equates to a ~1% attack rate
- 25% of phishing emails manage to make their way into Office 365 email inboxes. (AVANAN)
- Office 365 represents one of the most commonly used email clients
- They have 60 million commercial users and 50,000 small business customers worldwide.
- Other experts estimate that 1.2% of emails are malicious. (Valimail)
- This corresponds to 3.4 billion fake emails sent per day.
- 96% of phishing attacks arrive by email. (Verizon)
- Another 3% of phishing attacks come from malicious websites
- 1% of phishing scams happen via phone
- Roughly 15 billion spam emails make their way across the internet every day. (Semantec)
- This means that spam filters are so overloaded that they become liable to permit malicious phishing emails to slip through
- In 2019, almost 74% of phishing attacks involved credential phishing. (IC3)

- 65% of targeted attacks in 2019 involved spear phishing tactics. (Symantec)
- The motivation of 96% of these targeted attempts was for gathering intelligence
- 65% of active groups conducting targeted attacks relied on spear phishing as the primary infection vector. (Semantec)
- Next in line are…
- Watering hole websites (23%)
- Trojanized software updates (5%)
- Web server exploits (2%)
- Data storage devices (1%)
- Next in line are…
- Around 32% of phishing websites used HTTPS during 2020. (Webroot)
- That means that 1/3 of phishing websites are going the extra mile to maintain an image of security.
- More than 71% of targeted attacks involve some form of spear phishing. (Symantec)
- Website domains that end in “.com” still account for 50% of credential phishing attacks. (Symantec)
- Mining is one of the main forms of phishing since 1 in 258 emails is malicious. (Symantec)
- Next in line are…
- agriculture, forestry, and fishing (1 in 302)
- public administration (1 in 302)
- Next in line are…

- 86% of breaches within the mining, quarrying, and oil & gas extraction industries involved social engineering. (Verizon)
- Sextortion impacted over 7 million email addresses. (Cofense)
- $1.5 million in payments took the form of bitcoin payments to bitcoin wallets related to sextortion schemes. (Cofense)
- 84% of phishing sites examined in Q4 of 2020 used SSL. (APWG)
- The use of SSL increases by 3% year over year
How People Are Getting Hooked
About a fifth of people have clicked on a phishing email at least once. Not only do people open the email, they often click on the link leading to a fake webpage or a file laced with malware. Of the people who click on the malicious links, about two-thirds of them enter their credentials into the website’s prompts.

In a nutshell, this means that over 1 in 10 people are likely to give away their password to a fraudulent phishing site. But why are people falling for these emails? Why are they giving away their passwords, credit card numbers, and social security numbers?
Subject Lines
Luckily for employees and everyone else with emails and phones, hackers do have behavioral patterns. This means that the subject lines of phishing emails are often similar and follow a variety of recognizable patterns.
Hackers capitalize on the use of subject lines, in two main ways.
First, most organizations around the world continue to embrace a remote or hybrid workforce approach. This type of working environment leads to new and unfamiliar cloud technologies that hackers can exploit.

Second, more and more people are turning to digital entertainment and virtual communication problems. When we live in a world of social distancing, we use digital and virtual platforms to stay in touch with loved ones and colleagues.
- Nearly 70% of all email phishing attempts contain an empty subject line. (AtlasVPN)
- Some of the most common subject lines cybercriminals use include…(AtlasVPN)
- “Fax Delivery Report” 9% of the time
- “Business Proposal Request” 6% of the time
- “Request” 4% of the time
- “Meeting” 4% of the time
- In 2019, the top five subject lines for BEC attacks were: (Semantec)
- Urgent
- Request
- Important
- Payment
- Attention
Attachments and Links
Hackers who send phishing emails want you to take one of two actions: click on a link that leads to a fake website or download a file laced with malware.

The hackers do this to get your banking information, impersonate you to access a source of wealth, steal your identity, or some other form of motivation. Below are some phishing statistics related to the attachments and links inside the email.
- In Q3 of 2020, the most common types of malicious files attached to phishing emails were… (Tessian)
- Windows executables 74% of the time
- Script files 11% of the time
- Office documents 5% of the time
- Compressed archives 4% of the time
- PDF documents 2% of the time
- Java files 2% of the time
- Batch files 2% of the time
- Shortcuts 2% of the time
- Android executables >1% of the time
- PDF and HTML extensions are some of the most common filename extensions for phishing attachments that reach users in SEG-protected environments. (Cofense)
- PDF file extensions account for around 35% of threats
- HTML file extensions account for 30% of threats
- Employees will open 30% of phishing emails. (Verizon)
- Opening phishing emails increases the probability of someone will unintentionally click on a malicious link or download a document laced with malware
- According to research, 76% of malicious emails do not contain an attachment. (Sonic Wall)

- 66% of malware instances get onto computers via malicious email attachments. (Verizon)
- This malware often includes ransomware
- CVE-2017-11882 is a common vulnerability in Microsoft Office software that uses remote code to execute the attack. (Microsoft)
- Roughly 12% of malicious attachments exploit this vulnerability in Microsoft code
- 38% of phishing emails use links to malicious websites to hack the computer. (Cofense)
- This is slightly more than the 36% of phishing emails that contain malicious attachments
Brand Impersonation
In the last few years, the world saw an increase in organizations relying on Microsoft's suite of cloud applications. This trend started at the beginning of the COVID-19 pandemic, so it's easy to see why attackers are exploiting various cloud services.
To exploit cloud services, many hackers will impersonate brands. However, before the pandemic, fewer people worked in the cloud. Therefore many hackers impersonate banks, retail stores, and universities.

Below are some statistics about how phishing scammers try to impersonate brands.
- 71.8% of brand impersonation incidents are about brands in the technology sector. (INKY)
- The top 5 most impersonated brands are… (Webroot)
- eBay
- Apple
- Microsoft
- Steam
- Microsoft impersonating phishing emails occurs 43% of the time. (INKY)
- Impersonations of DHL occur 18% of the time
- Impersonations of Linkedin happen 6% of the time
- Amazon Impersonations happen 5% of the time
- Roughly 19% of social media accounts that seem to come from a top brand are fake. (Proofpoint)

- 47% of all social media phishing attempts relate to LinkedIn. (Sonic Wall)
- There were 897 fake Amazon sites active on Prime Day in 2022. (AtlasVPN)
- Between March to July 2020, phishing website links impersonating Netflix increased by 646%. (Webroot)
- Hackers spend $3 to $12 for a custom phishing web page. (Semantec)
- Windows executable files made up 66% of malicious email attachments. (ESET)

- Microsoft impersonating phishing emails accounted for 70% of all brand-related phishing attempts in 2020. (INKY)
- From the start of 2022 to July 12 of that year, professionals detected 1,633 fake sites. (AtlasVPN)
Internal Threats
Most bad actors don’t wear hoodies, tinted sunglasses, balaclavas, or Guy Fawkes masks to make their evil intentions more terrifying. External threats are most likely normal people who are simply good at coding and understanding technology.

In reality, there is a great deal of collusion between employees at a company and hackers. Sometimes the threat is the employee themselves. This is what people would call an inside threat. Below are some phishing statistics about threat actors.
- 34% of businesses revealed that the fraudulent activities involved some collusion between their employees and bad actors. (BDO)
- 21% of businesses said that their employees had been behind the fraud
- 85% of data breaches occurred because of some type of involvement with a human element. (Verizon)
- 97% of people cannot identify whether or not an email, ad, or message is a phishing scam. (IntelSecurity)

- Only 60% of organizations offer formal cyber security education to their users. (Proofpoint)
- This means that there is a strong likelihood that someone will accidentally allow a cybersecurity incident.
- Over 40% of employees assumed that the phishing emails in their inbox came from senior executives of their company. (Statistia)
Who The Victims Are
Small and midsize businesses are just as at risk of a cyber attack as high-profile businesses. The difference is that small and midsize businesses don’t have the infrastructure or resources to defend themselves properly against attacks.
Hackers see these organizations as “low-hanging fruit”.
Businesses around the world report that they have suffered from fraud since 2020. In the UK, the average loss of an attack was 245,000 pounds.
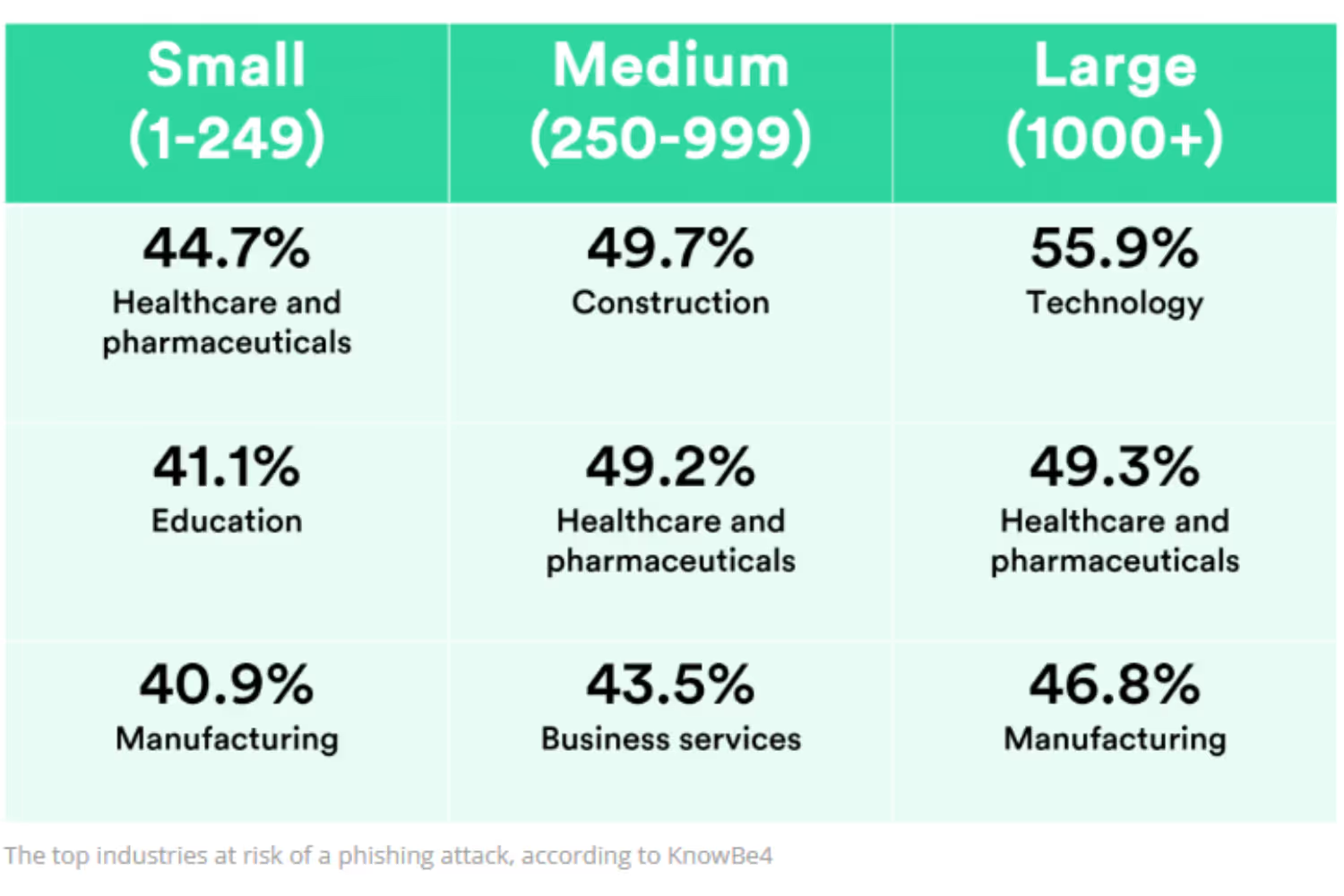
Some industries are more at risk than others. Which industries should bolster their defense systems against hackers because they are a larger target? The statistics below can answer that question.
- When it comes to phishing attempts, the most targeted sectors in history include… (IBM)
- Financial institutions
- Social media enterprises
- SaaS/webmail services
- Retail vendors
- Financial services are the most targeted by phishing attacks, with 60% more attempts than higher education. (SonicWall)

- The US energy sector was a prime target for spear phishing attacks in 2016. (CISA)
- The cyber attackers staged malware to gain remote control of the US energy Sector’s systems
- After gaining access, hackers moved laterally to collect information regarding the Industrial Control Systems.
Impact of a Phishing Attack
If you read this blog up to this point, then you probably realize how devastating phishing attacks are to organizations. If businesses fall victim to hackers, there are several ways the hackers can harm the business. They can steal money, data, and identities.
But there are also costs such as…
- User downtime
- Remediation time
- Damage to reputation
- Loss of intellectual property
- Direct monetary losses
- Compliance fines
- Response and remediation costs
- Loss of revenue and customers

In addition to direct and indirect financial losses, companies can also face legal consequences. They have to pay for lawyers, spend time in courts, pay fines about data security, pay remediation settlements, and other types of fines imposed by a judge.
To better understand the severity of a phishing attack, below are some useful statistics.
- The average data breach costs businesses around $3.68 million. (IBM)
- Data from 2020 found that BECs are the most costly form of cybercrime. (IC3)
- BECs resulted in the loss of over $1.8 billion yearly
- 95% of BEC attacks resulted in a loss between $250 and nearly $1 million. (Verizon)
- In 2018 alone, ransomware attacks using a phishing method cost businesses over $8 billion. (Verizon)
- Phishing was the second most expensive attack vector when it comes to remediation efforts in 2021. (IBM)
- Phishing attack remediation costs organizations an average of $4.65 million.

- In 2021, the total average cost of a data breach was $4.24 million. (IBM)
- This is up from $3.86 million in the previous year.
- When asked about the impact of successful phishing attacks… (Proofpoint)
- 60% of security leaders stated that their organization lost data
- 52% experienced credential compromise
- 47% of organizations contended with ransomware
- 93% of organizations have some type of method to measure the cost of phishing attacks. (Proofpoint)
- The average time it takes to completely contain a phishing threat is 290 days. (IBM)
Current Phishing Trends
In the last two years, the world saw a massive change in the way we work. We migrated to a remote office and then back to in-person office meetings. The world dealt with rapid digital transformations and more AI technologies than ever before.

2021 and 2022 saw more cyber threats than ever before. This means more data breaches, more money stolen, more fraud, and more phishing campaigns. Below are some statistics from this year and 2021 that help shed light on the dire situation.
- 86% of organizations and businesses had at least one user attempt to connect to a phishing website in 2021. (Cisco)
- 83% of organizations in 2021 reported experiencing at least one phishing attack. (Proofpoint)
- The data suggest that an additional 6 billion attacks may happen in 2022
- Only 37% of organizations say that they believe they were effective in counteracting 11 of 17 attacks. (Osterman)
- It's 11 out of 17 because there are 17 types of most common security incidents
- 63% of organizations believe they were highly effective against 10 or less of these threats
- The average wire transfer requested in a BEC attack increased from $75,000 in 2020 to $106,00 in 2021. (APWG)
- People opened around 30% of phishing messages in 2021. (Verizon)
- This is up from 23% in previous years
- Malicious bad actors admit that 96% of their primary motivation continues to be intelligence gathering. (Semantec)
- In BEC attacks, 68% of attackers requested payment through gift cards in Q4 2021. (APWG)

- In 61% of breaches, credentials are the most common form of stolen data. (Verizon)
- In 2021, experts identified roughly 214,345 unique phishing websites
- This is double the number of phishing attacks since early 2020. (APWG)
- There was a 7.3% increase in email-based attacks between May and August 2021. (ESET)
- The majority of them were part of phishing campaigns
- Other popular forms of payment include… (APWG)
- Payroll diversion (21%)
- Wire transfer (9%)
- In Q2 2021, 24% of BEC attacks tried to divert employee payroll deposits. (APWG)
- In Q3 2021, over 500,000 unique phishing websites popped up in a record surge. (Statistia)
- Direct transfers are less common in Q3 2022. (APWG)
- In Q2 2022, direct transfers accounted for 22% of all scams

- In the last 17 years, 2021 was the costliest year for data breaches. (APWG)
- Experts predict that there might be another 6 billion attacks throughout 2022. (Proofpoint)
- 92% of Australian organizations suffered a successful attack in 2021. (Proofpoint)
- This is a 53% increase from the year prior.
- In the same timeframe, less than 60% of Spanish organizations experienced phishing or ransomware campaigns.
- Tech support fraud increased by 171% from 2019 to 2021. (FBI)
- This resulted in over $146 million in losses.
- 84% of US-based organizations state that their security awareness training successfully lowered phishing failure rates. (Proofpoint)
- Projections show that the global cybersecurity market will reach $345.4 billion by 2026. (MarketsandMarkets)
- The growth is set to rise at a CAGR of 9.7% between 2021 and 2026
Conclusion
The phishing statistics above showcase the harrowing reality of how fragile people's information can become.
The reality is that there isn’t a quick fix to email security. There’s no perfect cybersecurity defense system. However, there are some basic things you can do to make sure that you as a person, and the company you work for, don’t end up as part of the statistics above.
Although this isn’t a solution for all types of email-related scams, many companies employ a secure email gateway, also known as SEG, to monitor inbound and outbound emails. SEGs can scan for malicious content and quarantine any detected threats. This way, the alleged phishing attempts never get to the intended recipient.
Cloud email security is another tool to help a company’s email network stay safe from malicious content. Like SEGs, it also monitors all inbound and outbound emails. Cloud solutions employ AI and machine learning to identify communication patterns and alert the network of any anomalous behavior. Unlike SEGs, this type of security can detect spear phishing attempts from corrupting a server.
Lastly, since people are the number one liability for any company, security awareness training should become mandatory and frequent. Employees play a critical part in an organization’s cybersecurity defense strategy. Security awareness training, like the one Etactics provides to companies, delivers engaging material combined with a series of questions to assess if the viewer understood the key takeaways. Etactics also provides phishing awareness training and other, more in-depth training modules.
Training can help your organization transform employees from potential targets into a secure line of defense against digital threats. Employees who complete a security awareness training program are far more likely to report a suspicious email than those who haven’t. This greatly reduces the time it takes to detect and remediate an attack.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.



![[ANSWERED] What to do if your email is on the dark web?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adc0209238d61bc357cb8d_EmailonTheDarkWeb_1224.avif)
![[ANSWERED] What is Dark Web Monitoring?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68adbe4fe3e9533f2c658048_WhatisDarkWebMonitoring_1224.avif)