Ransomware attacks happen all of the time. As of 2019, 85% of managed service providers (MSPs) reported it as the most notable malware threat.
Since they’re so common, chances are that you already know what ransomware is. But in case you don’t, let me explain.
Hackers use this type of malware to hold a victim’s information hostage. They block access to data using encryption, and the victim can only unlock the data if they pay a ransom.
But even when a victim does pay, the attackers still might not restore access. This results in huge monetary losses and more system downtime.
Because of these consequences, your team must know what these cyberattacks are and how to prevent them. If you don’t know how to ensure this, don’t worry. You’re in the right place.
One of the easiest ways to educate staff is by sending ransomware awareness emails.
Table of Contents
Explain What it is
A survey found that 37% of employees don’t know what ransomware is. Even worse, 32% who had experienced an attack still said they don’t know what it is.
After hearing those statistics, it isn’t shocking why employees pose a huge threat to organizations. Without knowing what these attacks are, people won’t be able to identify risks or attempts to prevent them from occurring.
This is where training comes in. Of course, your company needs to provide ransomware training so everyone knows what it is. But people may forget what they learned, so they’ll need reminders throughout the year.
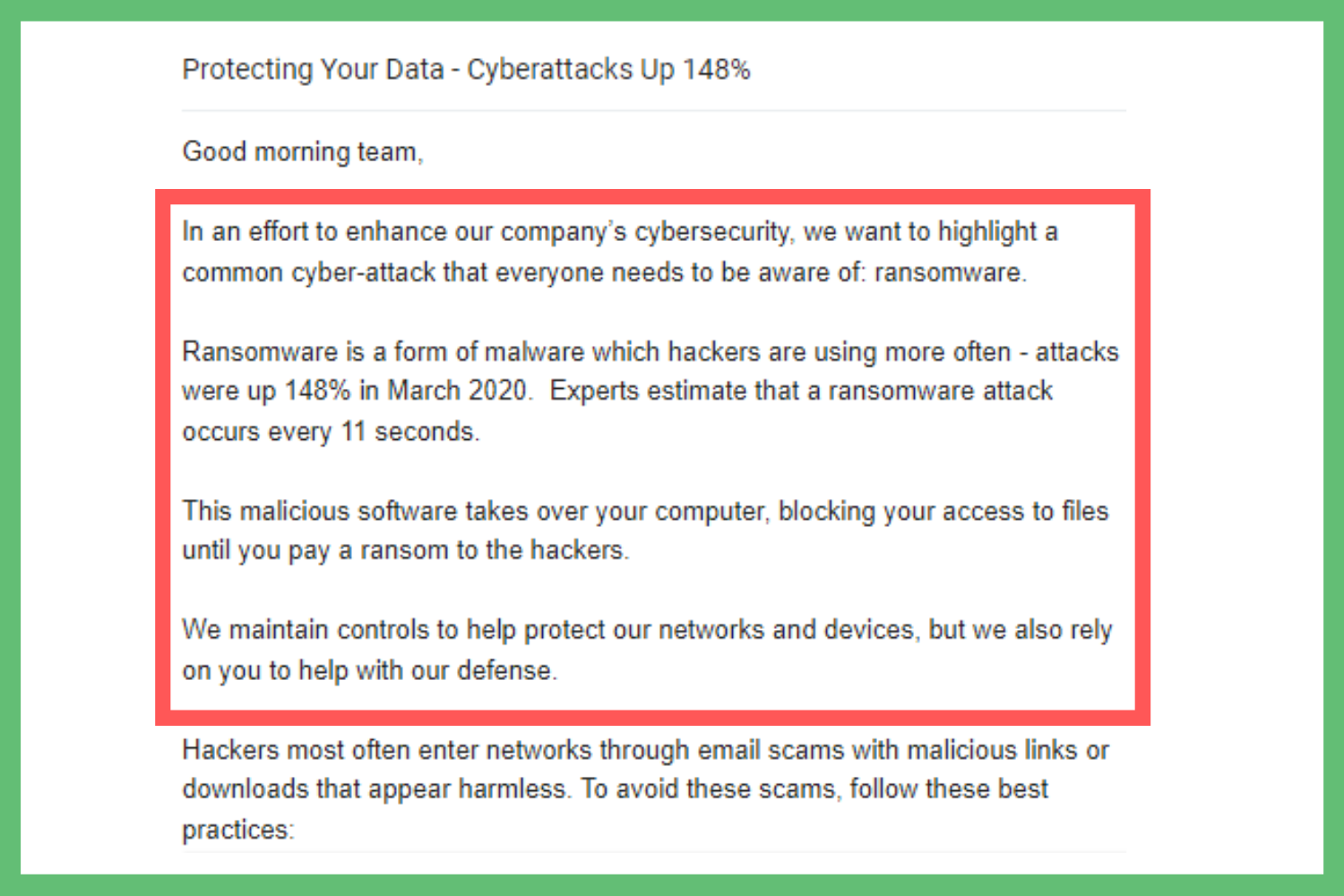
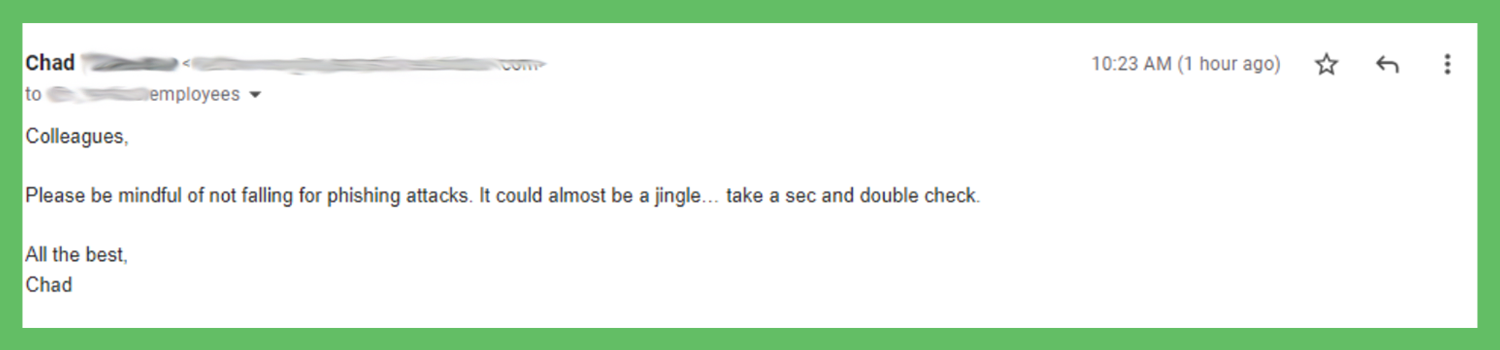
The most basic yet effective ransomware awareness emails to send explain this type of malware. Even if you’ve trained staff on it already, this reiterates what they already learned. They can also refer back to this email if they’re ever unsure and need to clarify anything.
So what should this explanation email include?
Since almost 40% of people don’t know what it is, the first step is to define it. Like I did in the introduction of this blog, you should explain…
What ransomware is
Why hackers use it
Consequences of an attack
But just as importantly, describe common techniques which hackers use to exploit data. Employees will be more likely to avoid attacks if they know what risks to watch for, such as phishing attempts.
How to Avoid Attacks
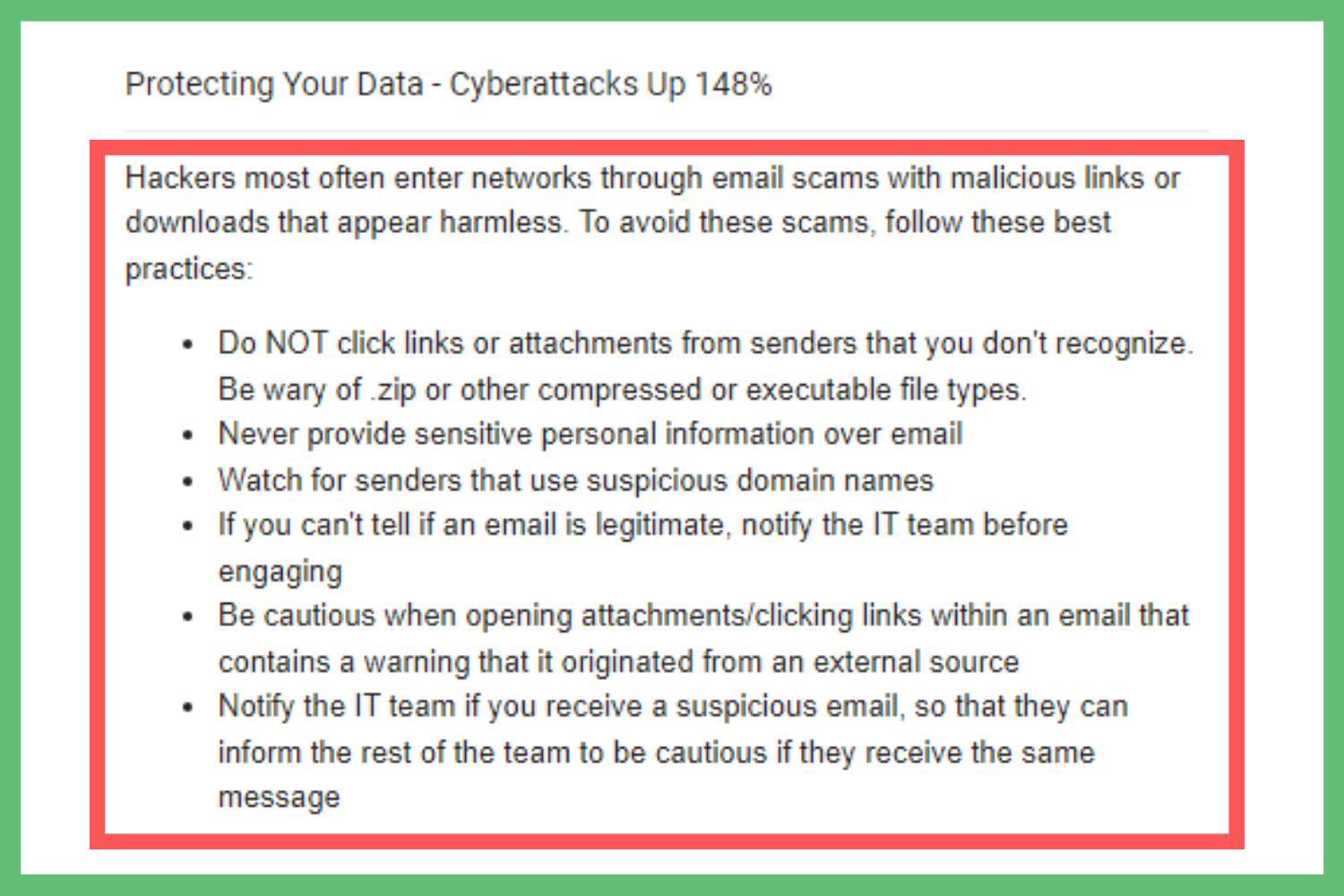
Once employees understand what ransomware is and the techniques that hackers use, they need to know how to avoid those attempts. Without knowing how to prevent attacks, they’d still occur even if your workforce knows that this type of threat exists.
Because of this, your organization’s ransomware awareness emails should also include these steps.
This example only includes a few of the ways to identify and avoid attacks.
These emails are also a good place to provide specific prevention methods your team has, such as protocols for notifying the IT team of an attempt.
Describe The Consequences
Describing the consequences of an attack in these ransomware awareness emails can also help your team. This emphasizes why they need to pay attention to this type of cybersecurity threat and how to identify and prevent attacks.
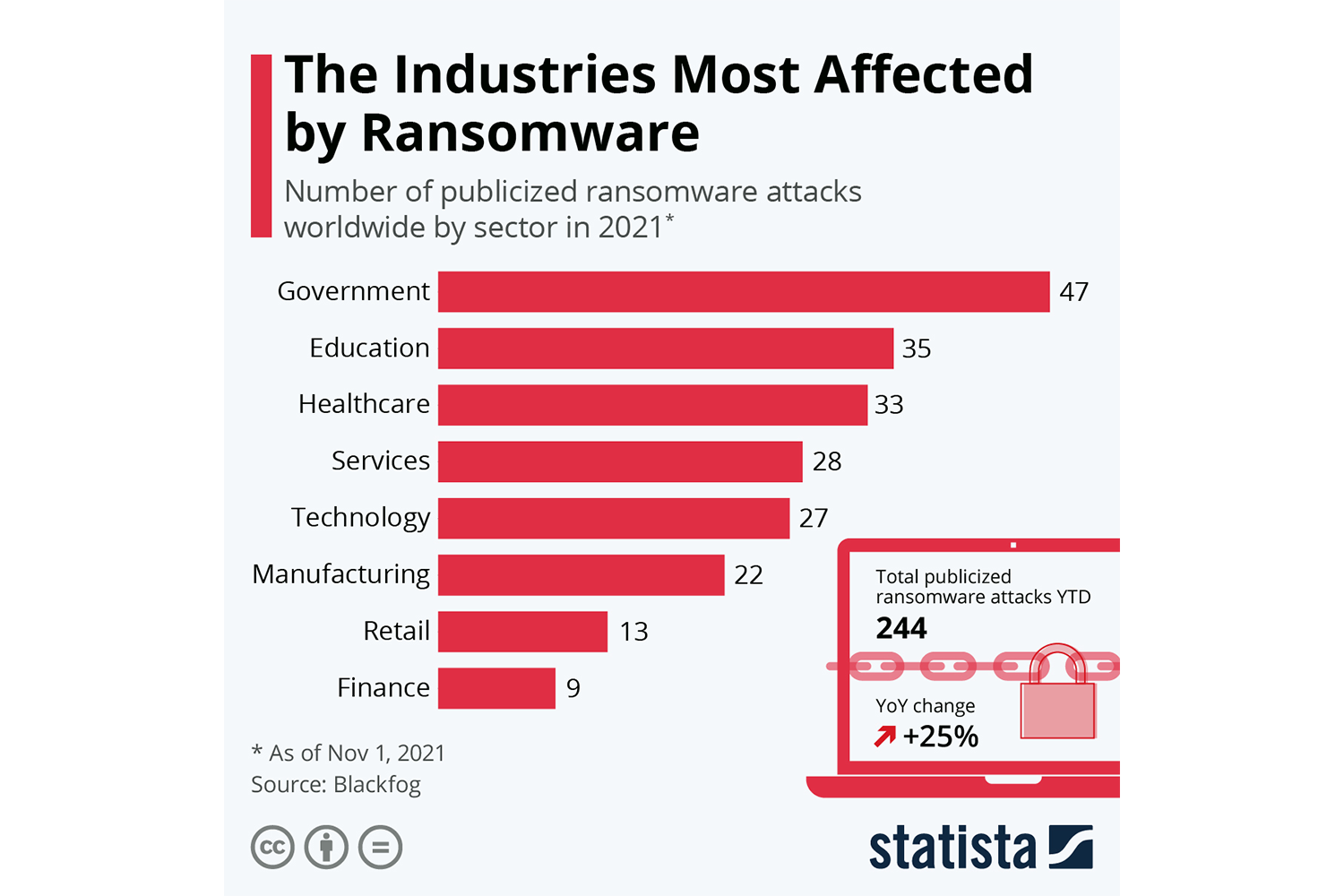
A majority of attempts are successful. 71% of targeted organizations get infected, and half of the successful attacks infect at least 20 of the victim company’s computers.
Companies experience an average of 21 days of downtime after a successful attack. This leads to major financial impacts. Monetary losses are due to downtime expenses, lost business from damaged reputation, and/or paying the ransom.
Small businesses can lose at least $713,000 per incident, on average. These attacks are getting more expensive as hackers demand more in ransom. From 2018 to 2020, the average requested fee increased from $5,000 to $200,000.
Hackers demand more from companies that deal with a lot of sensitive information. They know that companies can’t afford to lose data or business, so they target organizations that will most likely pay ransoms. And they demand far more money from them.
Thinking back to the spring of 2021, you might remember the Colonial Pipeline attack. This had people panicking over gas shortages across the East Coast. The United State’s biggest refined products pipeline had to pay hackers $4.4 million in ransom.
But there was an even higher payout in 2021. One of the US’ largest insurance companies, CNA Financial, paid hackers $40 million after an attack. This is far cheaper than the $60 million that the hackers originally demanded. After calculating all financial losses including downtime and lost business, the totals can be far greater.
Now, I’m not trying to say you should scare your staff. But it’s much more effective for them to understand the risks of attacks if they know the potential negative outcomes. Seeing real-world examples reiterates the importance of identifying and avoiding these attacks.
Steps for Responding to an Attack
Alright, at this point your staff understands what ransomware is, how to identify attacks and how to avoid them. Even after all of that though, they can STILL happen.
After all, 95% of all breaches occur due to human error.
Because of this, your organization should also send awareness emails that explain what to do if an attack does occur. This will help keep employees from panicking if they notice suspicious activity. That wouldn’t help anyone.
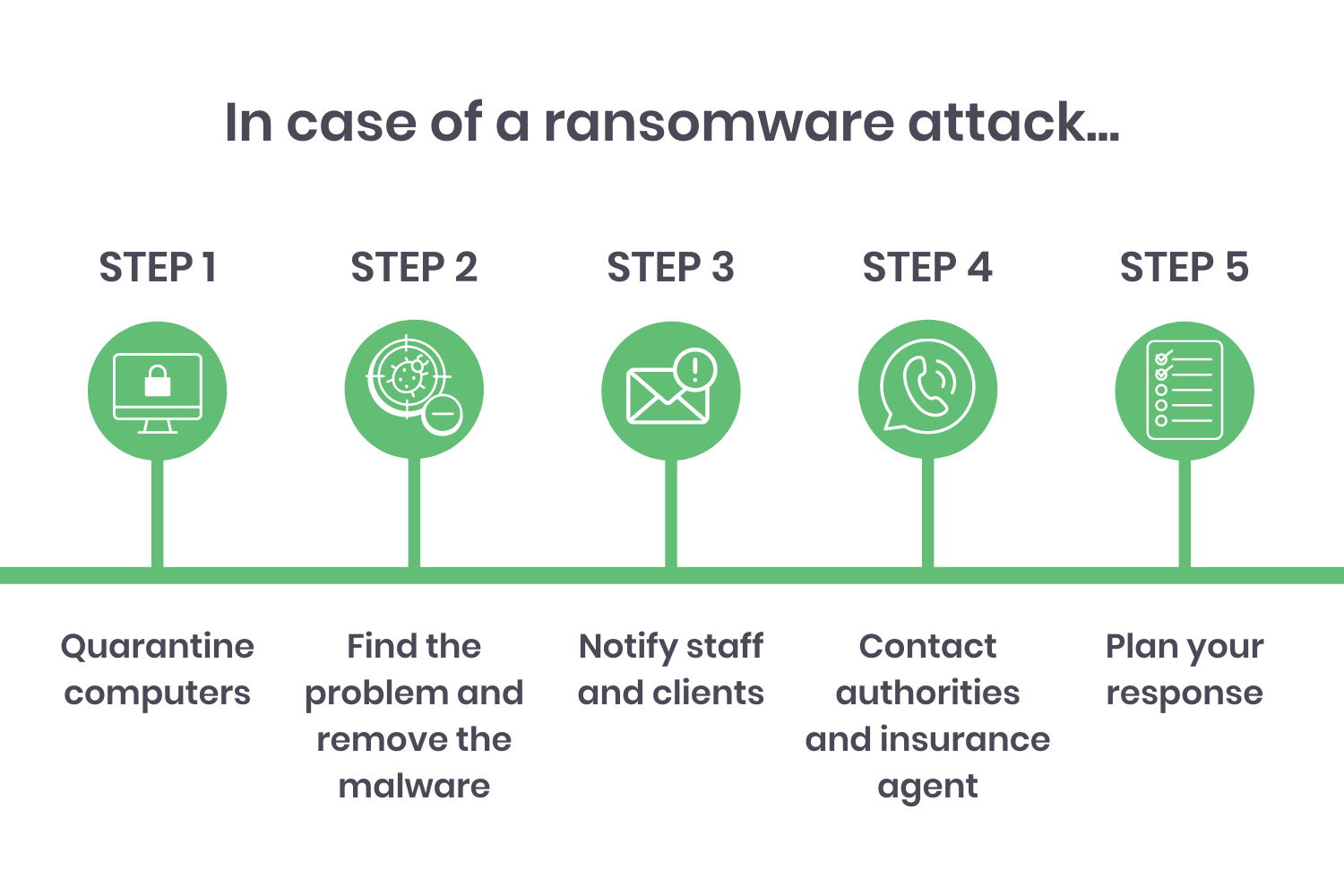
Instead, use these emails to inform them of response protocols such as who to report an incident to. This will maximize the time that your IT team has to respond to an attack before more data gets compromised.
The first two steps for a ransomware attack are time-sensitive. The longer it takes to quarantine computers, find the problem, and remove the malware, the more time the hacker has to infiltrate the system. Because of this, employees need to know what to do immediately when they identify that there’s been an attack.
Inform Staff of Attempts and Attacks
Likewise, you should also notify employees of suspicious activity. This includes both attempts or successful attacks.
You shouldn't leave anyone in the dark when it comes to an attack on your company’s systems. Employees would start to wonder why they can’t access data and start to panic if they’re unable to assist clients.
It’s also necessary to notify them of all active attempts. I mentioned earlier that hackers often target users through malicious emails. If someone from the organization receives one of these attempts, everyone in the company should get notified. The hacker will likely target others as well.
You want everyone to know that there are active attempts so they can be cautious of them and remember to be vigilant with skeptical emails.
Simulate an Attempt
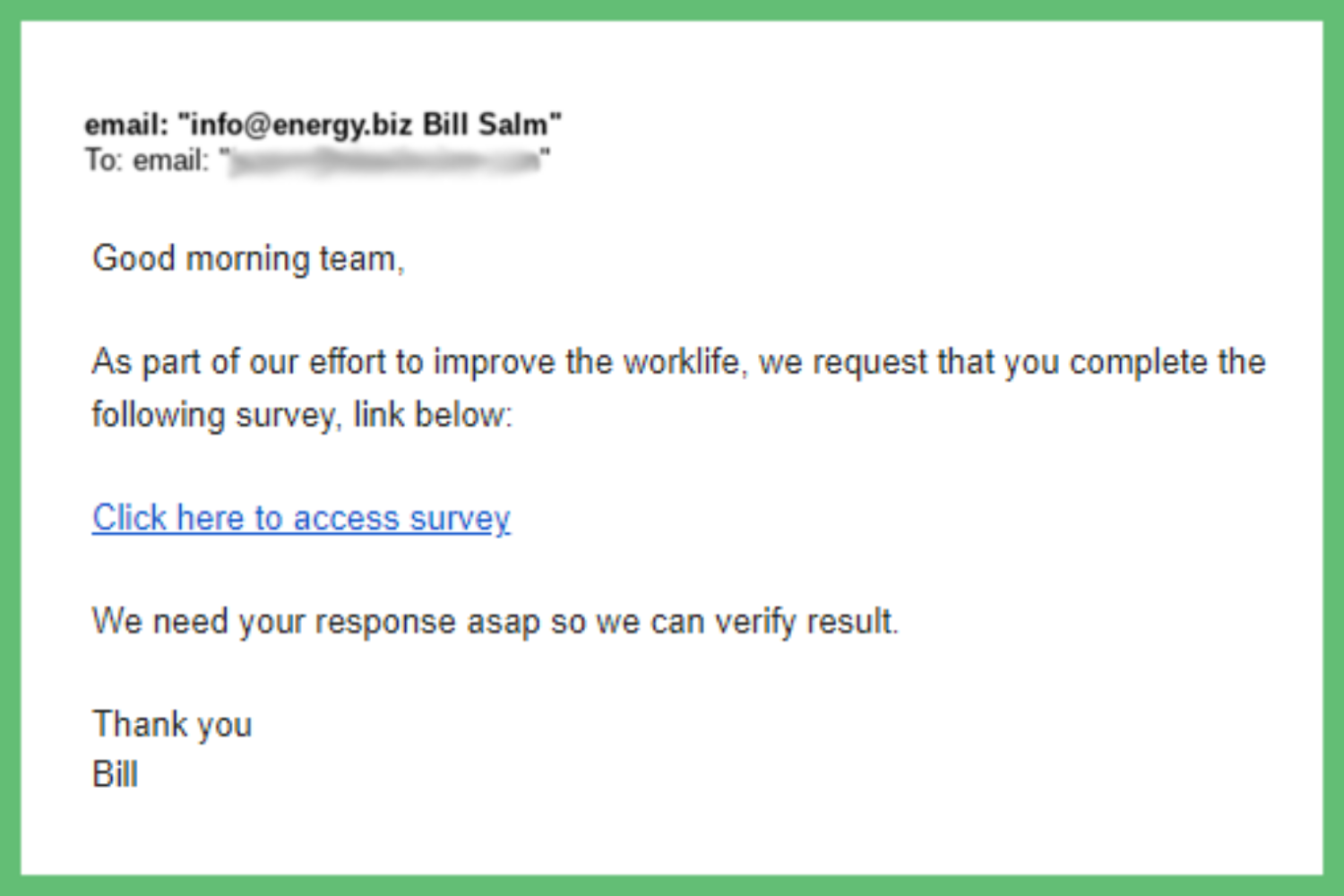
Part of your ransomware awareness email campaign could be a simulation of an attempt. Yes, you read that right.
Send out an email to your employees pretending to be a hacker. This will help you identify who isn’t paying attention to the helpful content you’re sending because they aren’t following the precautions.
If you do this, management and the IT team need to be on the same page. You wouldn’t want the IT team thinking that an attack is happening when it’s just management sending out a fake email. Communicate the steps of this simulation before proceeding.
You can do this by creating a fake email account that looks like it’s a trusted employee but has a different email address than that person. The email should mostly be unsuspecting but include a red flag such as a few typos. When recipients click on the included link, your team gets notified.
That way, you can easily identify who clicked the link before checking who the email came from. And you’ll know those most prepared if they inform the IT team that they suspect it’s a possible phishing attempt.
Since ransomware and phishing usually go hand in hand, the simulation emails you incorporate into your campaign can also accomplish the goals of your phishing training.
Conclusion
With how often ransomware attacks occur, it’s startling how many people don’t know what they are, even if they’ve already experienced one.
If you deal with sensitive data, then chances are you already provide some cybersecurity training. If you don’t, then it’s only a matter of time before a breach occurs.
Even if you do, there’s still a risk. No system or team is perfect, and mistakes can happen. But you want to take every step possible to prevent these attacks since they have such major consequences.
This is why you should use ransomware awareness emails to reiterate what employees should have learned in their training. They can refer back to these at any time for ways to identify, avoid, and properly respond to an attack. If they can’t remember who to contact first when they notice suspicious activity, these awareness emails will be their resource to find who that is.
And if you’re unsure if employees understand and are following your guidelines, then you can even use emails as an attack simulation. This will confirm for you who needs more prevention training, and who has benefited from your ransomware awareness emails.