What it Means to be HIPAA Compliant (It’s Surprising)
What does it mean to be HIPAA compliant? Let’s look at each part of the regulation to answer that question.

Did President Bill Clinton know the impact of signing the Health Insurance Portability and Accountability Act of 1996? Otherwise known as HIPAA. How would it affect healthcare organizations and their business partners?
Although he didn’t foresee so many people misspell the acronym and call it HIPPA, he did want to protect the privacy of Americans.
During one of his speeches on December 20, 2000, President Clinton went on about what he wanted to accomplish in signing HIPAA, “....the rules that we've released today have been carefully crafted for this new era to make medical records easier to see for those who should see them, and much harder to see for those who shouldn't.”
But what prompted this law to happen in the first place?
Well, the former President also highlighted instances of corporations invading American citizen’s medical privacy for their gain during the same speech. He wanted to protect health plan information. Namely, against the invasive marketing tactics of these companies.
He cited a survey of Fortune 500 companies that found that one-third of them factored medical history in who they hire.
Another story he narrated referenced a company in Pennsylvania. How the company didn’t run into any speedbumps when obtaining information on the prescriptions of their employees. The organization then discovered that one of their team members was HIV positive.
He went on to point out that pregnant mothers would receive marketing pamphlets in the mail for baby products before they’ve even announced the news to their friends and family. But this speech happened in the 90’s. What about now?
What does it mean to be HIPAA compliant? And how did HIPAA enforcement change the healthcare industry? Let’s look at each part of the regulation to answer that question.
What is HIPAA Compliance?
Before breaking down each section of the law, let me define a couple of things. Like what exactly is HIPAA compliance? It's the process of following HIPAA rules and regulations, which the Office for Civil Rights (OCR) enforces. Healthcare providers must be vigilant when it comes to handling health records if they want to fully comply with HIPAA.
The rule also applies to the following…
- Patients
- Covered entities
- Business associates
Of course, the patient is the most involved individual with HIPAA as its entire purpose is to keep their individually identifiable health information secure.
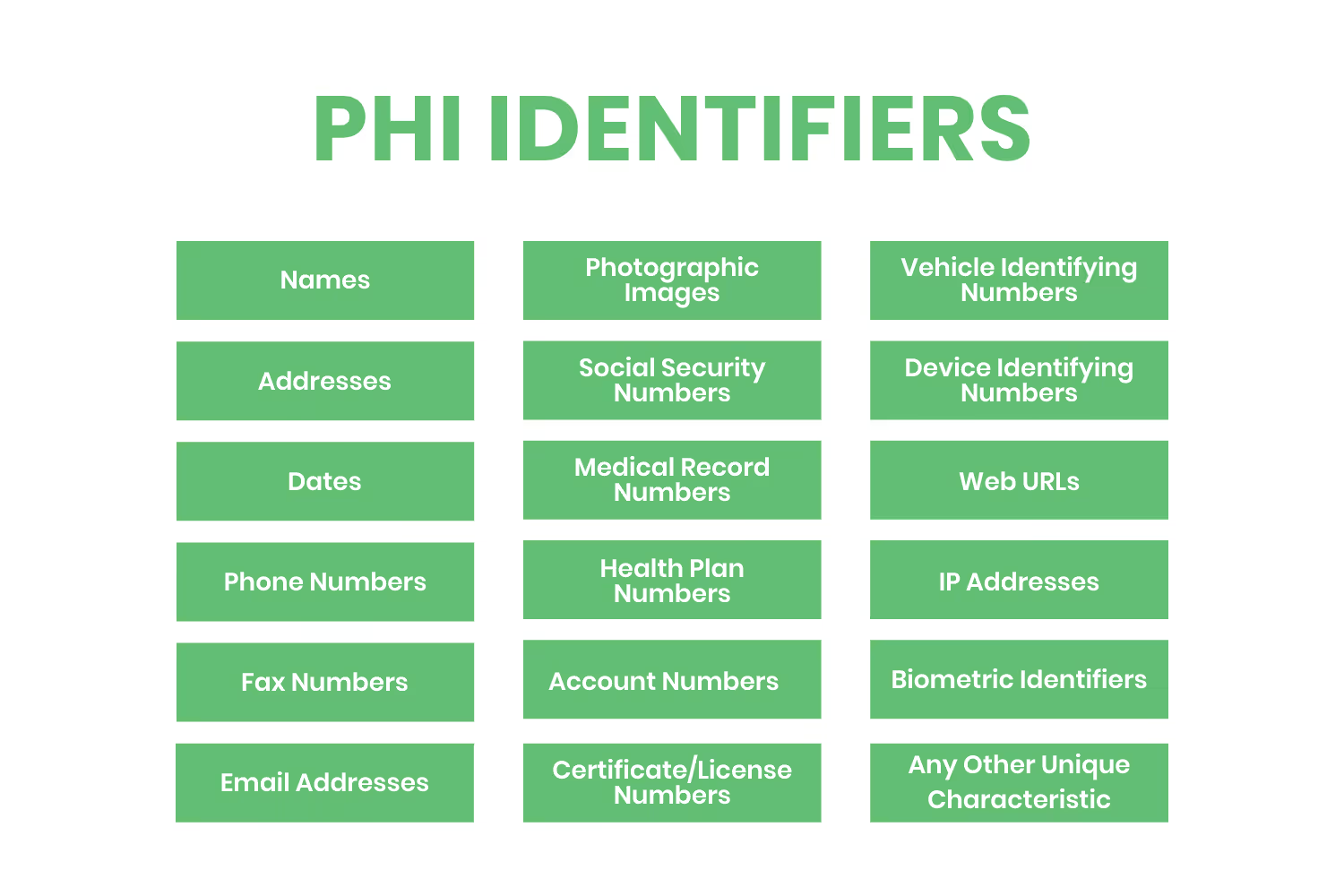
What is PHI?
PHI is also known as “HIPAA identifiers”, or information used to identify an individual. There are 18 different things that fall under PHI. There is also electronic protected health information (ePHI). This is sensitive health data that gets stored electronically on computers and other devices. We will go more into detail on this later.
A covered entity (CE) refers to any individual who gives treatment, installment and operations in human services. That’s a fancy statement for doctors and the facilities they work at.
What is a Business Associate?
Next is what’s referred to as a business associate (BA). Business associates are those who have access to PHI to help covered entities with those same categories; treatment, installment and/or operations. That’s another complex definition to reference companies who help doctors do their job.
Learning The Law
HIPAA Compliance Requirements & The HIPAA Rules
OK, now that we know the parties that the law refers to, let’s break down each section of the law. There are different policies and procedures bundled into sections that define HIPAA regulations.
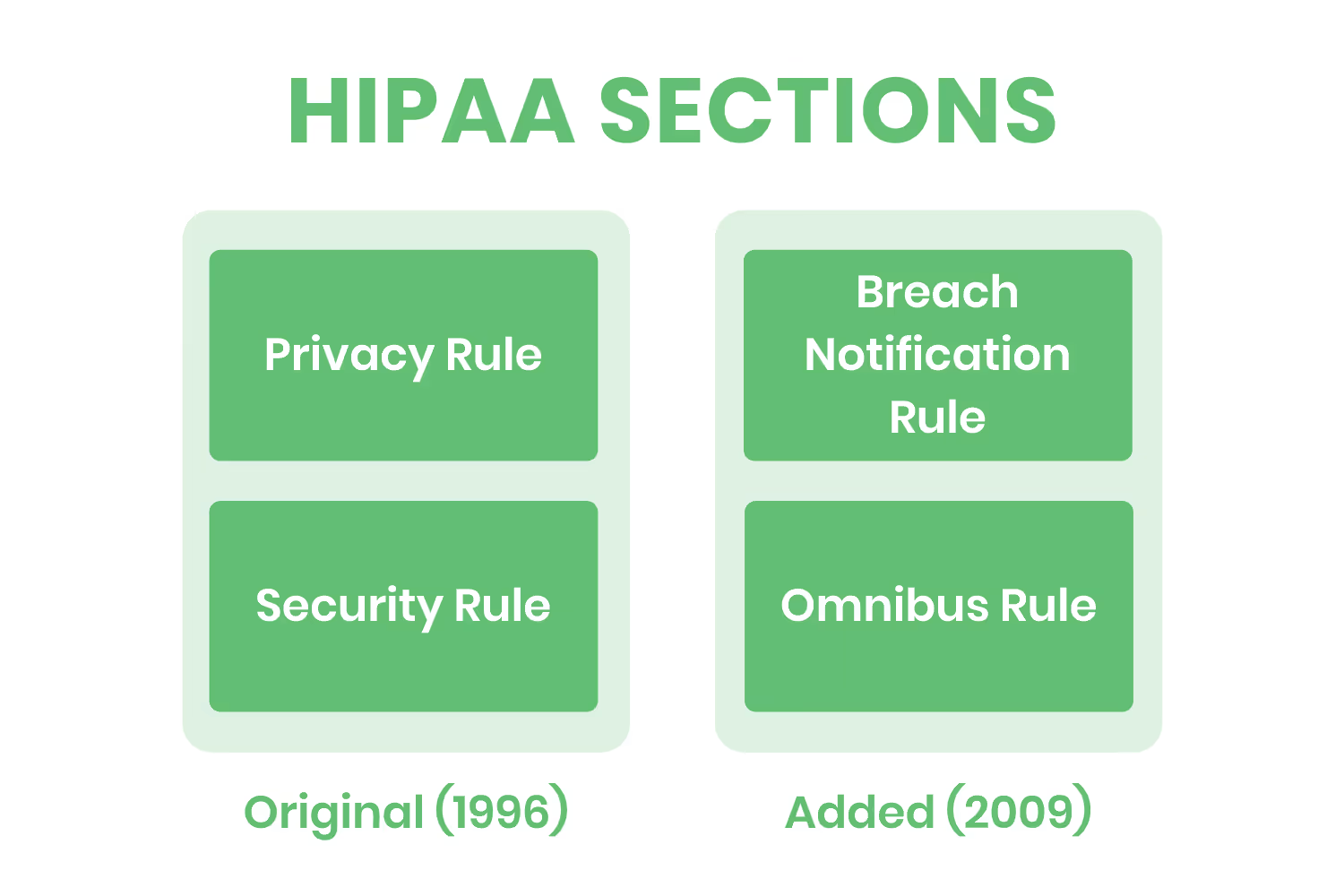
There are four sections within HIPAA...
- Privacy Rule
- Security Rule
- Breach Notification Rule
- Omnibus Rule
First, let's go over the privacy and security rules.
The HIPAA Privacy Rule
First, the Privacy Rule sets the standards for patients and their rights. It outlines patients’ rights to access PHI, healthcare providers’ rights to deny access to PHI, what Use and Disclosure forms should look like and more. The Privacy Rule only applied to covered entities at first, not business associates.
The HIPAA Security Rule
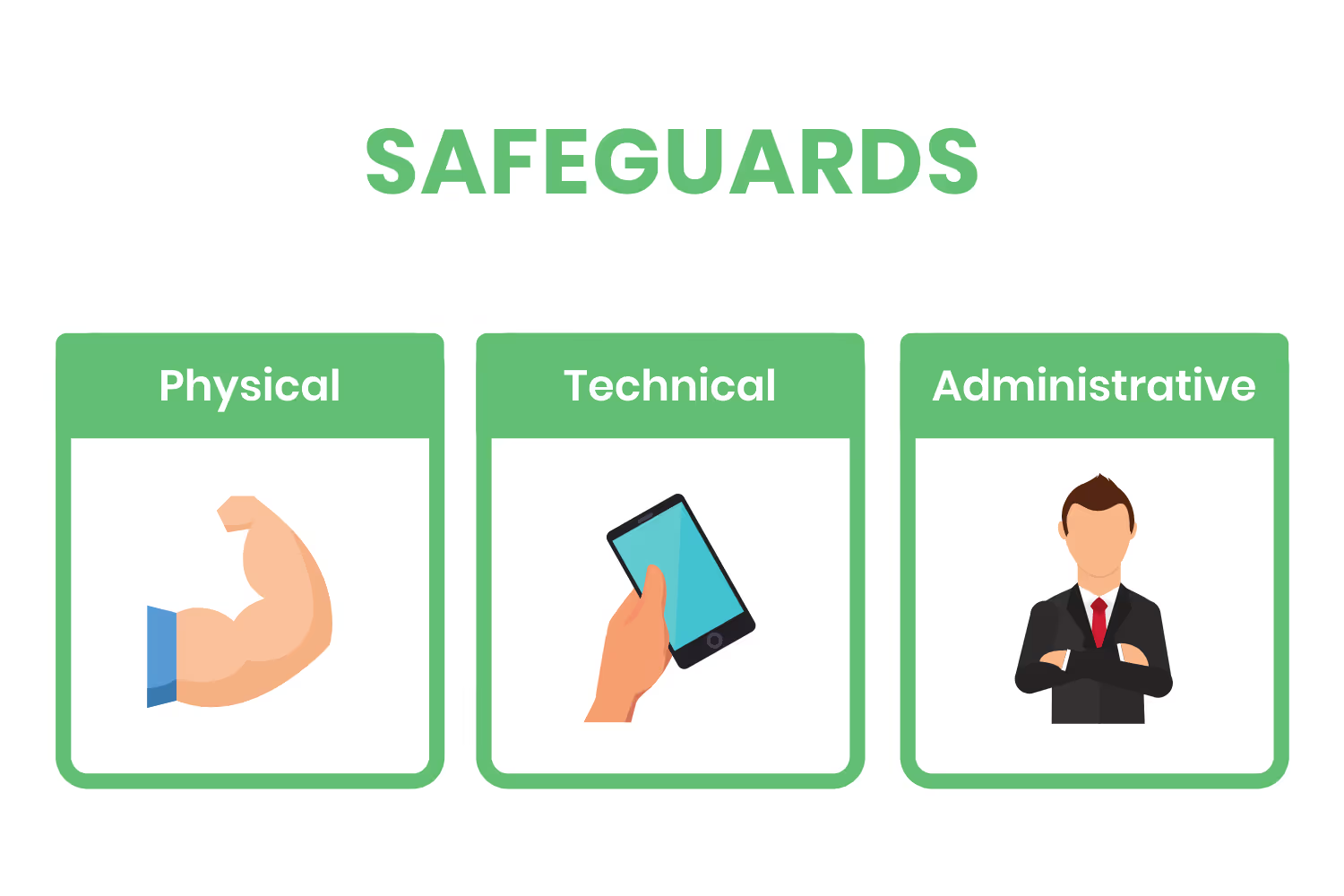
Second, the HIPAA Security Rule establishes principles that ensure the wellbeing of information created, received, maintained, or transmitted electronically. It introduces standards for the integrity and safety of electronic PHI (ePHI) through physical, administrative and technical safeguards. This section of the law has always applied to both covered entities and business associates.
Security Rule safeguards sound like complicated jargon but they’re literal in nature...
- Physical: Real-world barriers that limit access to the building
- Technical: Cyber barriers that only allow access to ePHI to those with proper authorization.
Administrative: Log tracking of activities to help find the source of violations.
The Breach Notification Rule
Third, the Breach Notification Rule, added in 2009, details what must happen in the event of leaked that PHI gets in the hands of unauthorized individuals either physically or electronically. It categorizes breaches into two sections; Minor Breaches and Meaningful Breaches.
Furthermore, it requires organizations to report all breaches to the Department of Health and Human Services Office of Civil Rights (OCR) regardless of their size. But reporting protocols change based on how the incident gets categorized. Both CE’s and BA’s need to adhere to this rule.
The Omnibus Rule
Fourth, the Omnibus Rule is an addendum, via the American Recovery and Reinvestment Act of 2009, to HIPAA to ensure that the entire law applied to business associates. Since this rule, business associates must be HIPAA compliant. They must sign also sign a government-mandated Business Associate Agreement (BAA) template provided by the covered entity. CE’s and BA’s must agree upon a BAA before the sharing of PHI or ePHI happens.
Why You Need To Be HIPAA Compliant
Part of being HIPAA compliant means that your organization stays that way. It would be nice if all you had to do as an organization was go through a checklist and receive a certification that states you’re a compliant business. Unfortunately, that’s not an attainable achievement.
Instead of thinking of it as something like an achievement, look at it as a way of conducting business.
In fact, I’d even venture insofar as to say that there’s no such thing as “HIPAA compliant” anything. Neither the healthcare facility that takes care of patients daily nor their business associates that provides them with technology to speed up their billing process can justifiably say that they’re 100% HIPAA compliant.

That might sound like an outlandish statement, but the law isn’t something that’s entirely defined. Both organizations can only meet the current regulations, which are in a constant state of a change and open to different interpretations.
Thus, being HIPAA compliant means following what the rules say and implementing continuous ways to improve.
The HHS created a great website that goes over this regulation and all of its requirements. So, you should be OK if you comply with everything listed on that website. However, you should still have your compliance environment reviewed by a certified professional.
At the end of the day, who determines whether or not you’re HIPAA compliant is a certified auditor. They’re the ones looking at and evaluating other similar organizations.
Certified authors will, of course, look to see if you’re following their interpretation of what’s required. However, they’ll also look at what you’re doing consistently.
Covered entities and business associates need to document regulatory standards and practices within their policies. They also need to train all of their employees on them on a “periodic” basis.

The law doesn’t come out and say that it’s a requirement to do it every year. Thus, an auditor may recommend that your organization hold HIPAA training sessions annually.
It’s also a requirement that CE’s and BA’s conduct a risk assessment on their organization. However, it doesn’t tell you what to do with it after you’ve completed it.
The objective of a risk assessment is to point out the weaknesses within your organization. What if you don’t fix them because you don’t have time?
That’s a scary thought, but it happens more than you might think considering how overworked doctors are these days.
Technically you might still be in compliant in this scenario. But, an auditor might require that you actively try to tackle the problems brought to life by your risk assessment.
My point after this section is to look at being HIPAA compliant as a road, not a destination.
The Consequences of a HIPAA Violation
It’s been almost 30 years since HIPAA’s enactment and we’re living in a totally different world. If you were cringing during any of those stories President Bill Clinton pointed to in his speech, you’re a product of modern healthcare. Don’t worry, that’s a good thing.
If any of those stories were to happen today, both of the organizations would face a massive fine. A HIPAA breach can spell disaster for even the most stable business.
The practice that gave the corporation access to prospective employees’ medical records would have to pay a lot of money today. They'd also have to fire the team member that went through with the sending.
The corporation would also face serious legal action against them, both from the Department of Health and Human Services (HHS) and their interviewee.
Patient record privacy, confidentiality and security has only gotten more important.
Whether it’s because hackers continue to target protected health information (PHI) to make money on the black market or because social media makes it easier to share unauthorized information, adhering to HIPAA will only become more critical.
But how can health care providers ensure their practices have the elements of an effective compliance program?
What is a HIPAA Compliance Program?
A HIPAA compliance program structures HIPAA training for organizations. It does so in a way that ensures they maintain compliance standards. They are also coupled with internal policies, safeguards, and procedures. These compliance solutions are often provided by third party organizations. Who takes over the burden of specializing in all HIPAA requirements.
Keeping up with what HIPAA requires can be chaotic. Since these requirements can change with time and technological advancements. By investing in an effective compliance program, you can rest assured that your team has coverage if any legal issues arise.
What Does It Mean to Be HIPAA Compliant?
The term “HIPAA compliant” is more a buzzword than anything else. It’s nearly impossible to hold an individual or company totally accountable for all of this regulation’s requirements.
Not even the most secure servers, detailed policies or strictest penalties can stop a disgruntled employee from snooping into the medical records of a celebrity. Likewise, you enabling two-factor authentication to all logins won’t stop hackers from bombarding servers and connections to find an unstable entry point.
So what does it mean to be HIPAA compliant? The answer to that question is easy once you look past all of the hocuspocus.
It means having dependable…
- Business Associate Agreements
- Policies
- Training
- Employees
So that you can ensure that your organization is doing everything it’s supposed to in order to protect patient data.
Of course, having a couple of reminders to promote awareness posted around the office still wouldn’t hurt.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




