HIPAA Privacy Risk Assessment: Analysis & More
To protect from HIPAA violations such as unauthorized verbal disclosures. We will look at what it takes to perform a HIPAA privacy risk assessment.

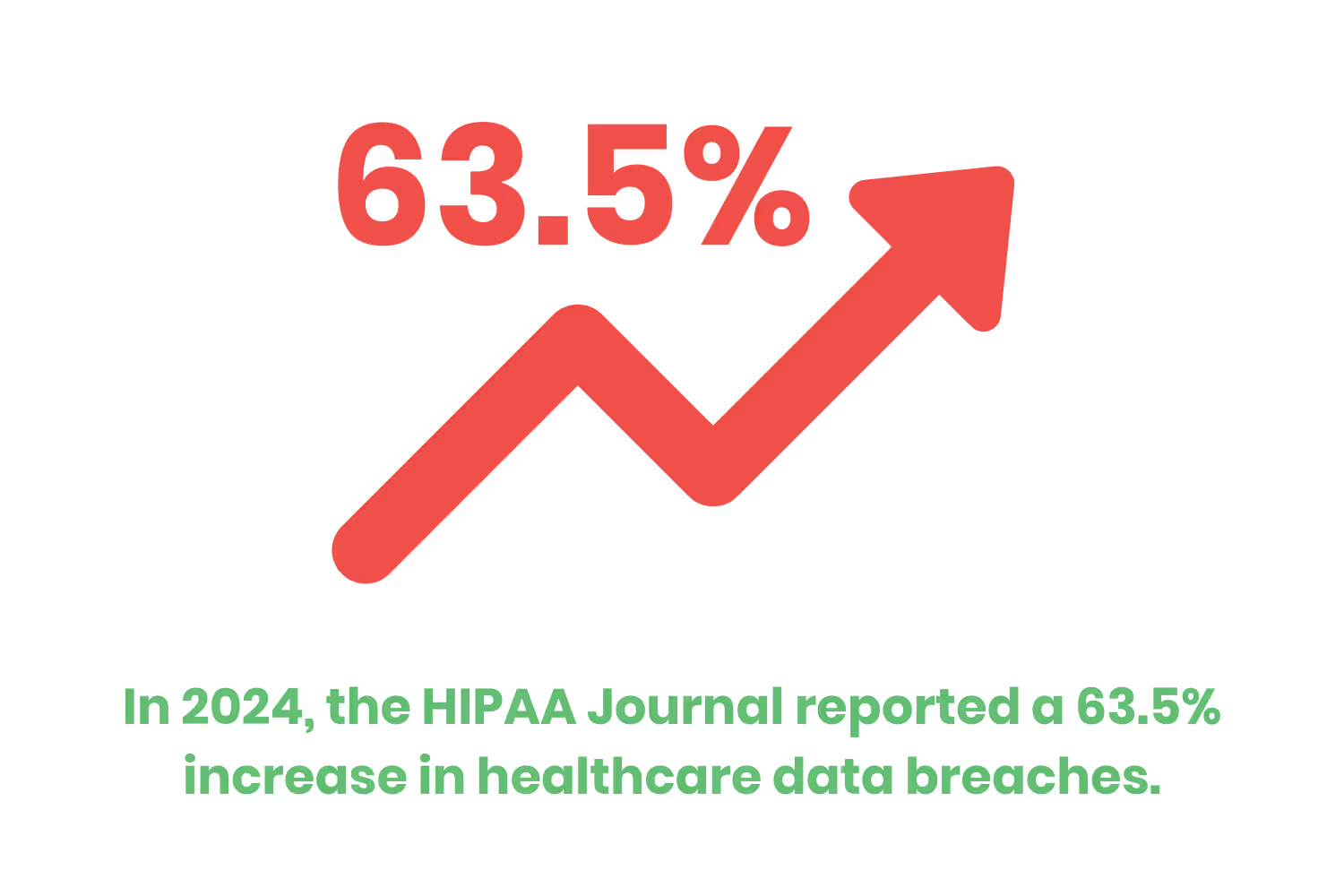
In 2024, the HIPAA Journal reported a 63.5% increase in healthcare data breaches. That’s a jump from 168 million to 275 million leaked records in just one year. The fact of the matter is that these data breaches aren't going away anytime soon. That's why organizations need to familiarize themselves with the Health Insurance Portability and Accountability Act (HIPAA).
The U.S. Department of Health and Human Services (HHS) issued this rule to address the use and disclosure of Protected health information (PHI). PHI is any health information that you can use to link to a specific individual. Anything from medical labs to birthdates and more. This data is extensive and therefore continues to be a prime target for cybercrime.
This is why your organization’s security measures need to be airtight. Educating you and your team on HIPAA training protocols helps to reduce risk. Coupled with an accurate risk analysis process, you're ahead of the game!
The requirement for covered entities to assess their security appears twice in the Administrative Simplification provisions of HIPAA. You can find them in the:
- The HIPAA Security Rule (45 CFR § 164.308 – Security Management Process).
- The HIPAA Breach Notification Rule (45 CFR § 164.402).
Due to the nature of healthcare work environments, it might be necessary to conduct further risk assessments. To protect from HIPAA violations such as unauthorized verbal disclosures. We will look at what it takes to perform a HIPAA privacy risk assessment. But first, let's go over the basics of HIPAA, what a risk assessment is, and how to perform one.
What is the HIPAA Security Rule?
Let's take a look at the HIPAA Security Rule. The HIPAA security rule requires businesses working with electronic protected health information (ePHI) to follow certain privacy and security standards. All electronic data created, used, received, or maintained by a covered entity falls under this rule. The current security management process includes the following:
- Administrative safeguards.
- Physical safeguards.
- Technical safeguards.
These safeguards help organizations comply with the security policy that HIPAA requires. These security rule standards are helpful when analyzing security rule compliance efforts.

What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule establishes national standards for protecting non-electronic PHI. It also covers patients' rights to access their PHI. Covered entities that handle this information must abide by these rules and regulations. While simultaneously facilitating the flow of healthcare data needed to provide quality care.
The rule creates a balance between the necessary use of health information and technical safeguards that prohibit inappropriate access. Because of the requirement for businesses to conduct security risk assessments, people sometimes overlook the necessity of privacy risk assessment. This is equally as important.

What is a HIPAA Risk Assessment?
HIPAA risk assessments analyze and help to reduce potential risks to PHI. It also helps to secure the information systems that store and transmit this data. The Office for Civil Rights (OCR) helps to enforce the security and privacy rule by providing further oversight and guidance.

Businesses utilize both the OCR and the Office of the National Coordinator for Health Information Technology (ONC) when it comes to performing risk assessments. More specifically, the two programs have jointly launched a HIPAA Security Risk Assessment (SRA) Tool.
Many healthcare practices find this useful in their journey to become HIPAA compliant. As we will see soon, the cost of a HIPAA breach is too great to ignore. Having a security risk assessment tool to help you assign risk levels to your business processes is vital.
There are three different types of HIPAA risk assessments:
- HIPAA Security Risk Assessment.
- HIPAA Breach Risk Assessment.
- HIPAA Privacy Risk Assessment.
As I mentioned, today we are going to focus on the privacy risk assessment and why it matters.

Why Does the Risk Assessment Process Matter for HIPAA Compliance?
Being able to effectively conduct a risk assessment is important for multiple reasons. Periodically evaluating the level of risk your business operations bring to the table can save you from costly violations. Failing to meet compliance with HIPAA standards can trigger an audit of your security program.
You can get stuck with fines, ruin your professional reputation, or even face jail time. Even if the data breach was due to an accident. Negligence is no excuse when it comes to an organization's security.
Who Needs to Conduct a HIPAA Privacy Risk Assessment?
Anyone who handles protected health information (PHI) needs to evaluate the risks to patient privacy. A HIPAA privacy risk assessment is not optional. Handling PHI includes whether it’s being created, shared, accessed, or stored.
Protecting patient privacy is a foundational part of maintaining compliance with the HIPAA Privacy Rule, which governs how PHI can be accessed, used, or disclosed.
Privacy risk assessments help organizations:
- Identify where PHI might be improperly accessed or shared
- Evaluate gaps in policy enforcement or staff behavior
- Strengthen safeguards around patient confidentiality
Regular privacy risk assessments are especially important in environments with high human interaction, such as front desks, call centers, or patient-facing staff. Even verbal disclosures or mishandled paper records can lead to violations. That’s why it’s so important to have an established risk management process.
Business Associate Privacy & Security Measures
Business associates (BA), vendors, and subcontractors must also adhere to HIPAA policies and procedures. They can also face fines and legal penalties if privacy and security measures to protect PHI are not met.
So it's essential for business associates to conduct a risk assessment based on security and privacy rule compliance standards.

Use the HICP Framework to Strengthen Both Security and Privacy
In addition to the OCR and ONC tools, the Health Industry Cybersecurity Practices (HICP) framework is another valuable resource. Developed by the 405(d) Task Group under the U.S. Department of Health and Human Services, HICP outlines real-world threats facing healthcare organizations and offers practical ways to reduce them.
The framework identifies the five most common cybersecurity threats, such as ransomware and phishing. It then pairs those threats with ten best practices tailored to the size of your organization. Whether you're a small clinic or a large hospital, HICP provides actionable steps that support HIPAA compliance and improve your overall cybersecurity.
Using HICP demonstrates proactive risk management, which is something extremely helpful in the event of an audit or data breach.
Using HICP helps your organization:
- Address real-world threats to PHI
- Reduce the risk of both external and internal breaches
- Demonstrate a proactive approach to HIPAA compliance
Even though HICP is voluntary, implementing its recommendations can bolster your risk management program and help you build an environment where both HIPAA Security Rule and Privacy Rule protections work together.
How Do I Conduct a Thorough HIPAA Risk Analysis
To conduct a thorough risk analysis, you should start with defining the scope. As well as identifying any hazards. For a privacy risk assessment, we suggest appointing a Privacy Officer.
This person should map the flow of PHI internally and externally. Also, they should note what devices house PHI and how the organization transmits it. Next, identify any gaps in security or potential weaknesses. Your Privacy Officer should do this by:
- Reviewing past or current projects,
- Performing interviews with anyone who handles PHI.
- Reviewing documentation.
Continue to regularly monitor the success of your risk management program. This ongoing risk assessment helps to continue to improve your processes. You want to be the first to find any weak points in your security or integrity.

Once you identify all potential risks, it's time to determine risk levels. Measuring the likelihood and impact of a threat helps your team prepare for the worst. Organizations tend to use scales, such as ranking likelihood and impact as 1 through 5. 1 being the least likely and 5 being extremely likely. Or in the case of impact, 1 being negligible and 5 being severe.
Once you assign those levels, you can better prioritize threats. The level of risk is highest when the threat is likely to occur and can have a large impact on your operations.
Make sure to document all of this. Also, regularly review and update your HIPAA risk assessment process. Employ an annual risk analysis to identify any weaknesses in your security measures. Especially if there is a change in processes or technology.
HIPAA Risk Assessments Are Non-Negotiable
Along with the rise in data breaches, the OCR is busier than ever. More investigations mean the greater likelihood that if you don't protect your PHI, you might get stuck with an audit. HIPAA violations and failed audits don't just cost money. They can also result in a weakened professional reputation.
If you feel your current security measures are not up to par, don't panic! The HIPAA Security and Privacy Rules hold the key to keeping your information security strong. Follow the tips in this blog and prioritize your staff's HIPAA training. By doing this, you can help ensure your organization's compliance.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




