The Definitive NIST SP 800-171 Self Assessment Template
Here is our definitive NIST SP 800-171 self assessment template.

Control Statements vs Determination Statements
Both 32 CFR Part 2002 and DFARS 252.204-7012 point to NIST SP 800-171 to protect controlled unclassified information (CUI). This special publication is 113 pages long with 110 controls from 14 domains. Is this the best guide to self-assessing the implementation of each control?
Each practice includes a control statement, which is in bold text next to the control ID number. These control statements describe the capabilities but they only summarize what is being done. They provide little insight into how to implement the control effectively. For example:

This control statement is somewhat vague. Even with the guidance provided in the discussion, it is difficult to break down the control into more granular components.

You would have a hard time trying to conduct a self-assessment of these controls using only NIST SP 800-171. To assess implementation, another part of the document exists called NIST SP 800-171A. This is the guide to assessing the implementation of the NIST SP 800-171 controls. Although not referenced in the CFR or DFARS clauses, NIST does point to this document on the landing page for NIST SP 800-171.
This publication expands upon the 110 practices by creating 320 determination statements. These are the more granular parts of the controls that assessors will check when evaluating a practice.
For example, we can identify 15 determination statements from the before-mentioned practice 3.4.7:
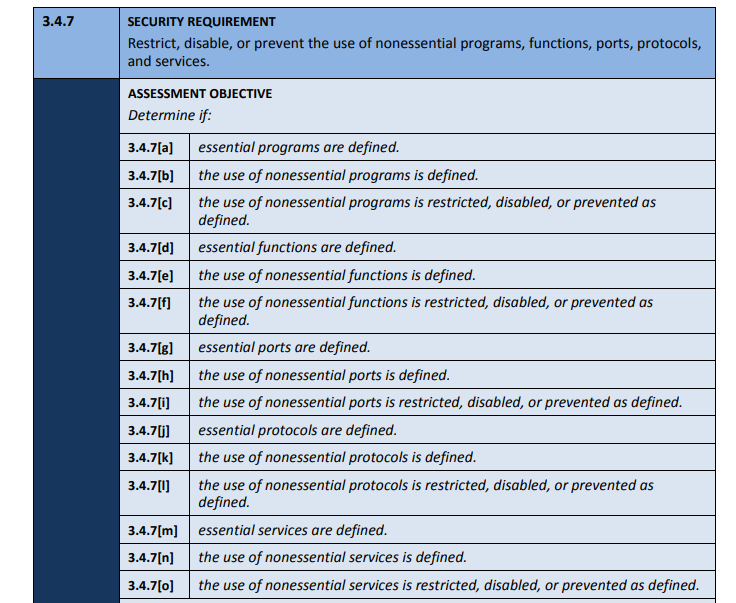
Notice that the security requirement is the same as the control statement from NIST SP 800-171 Rev 2. Below the security requirement is the assessment objective, which in this practice, consists of the 15 determination statements, listed [a] through [o].
These are the statements assessors will check for each practice. To meet the security requirement, all determination statements need to be either met or N/A for all assets within scope.
Self-assessing a control without looking at its determination statements is like playing scrabble without a dictionary. Sure you could do it, but there is no authority to reference.
How do I determine the scope of NIST SP 800-171
Now that we have a better idea of what we need to put in place, let’s talk a little bit about the application of these controls to your environment.
Let’s start with the NIST guidance under section 1.1 Purpose and Applicability:

The first sentence points to reference 9, which states:

This is a great start to understanding the scope of NIST SP 800-171. Consider this as guidance to defining a boundary. This boundary separates what is relevant to NIST SP 800-171 from what is not. Assessment Objects is a term used by NIST to describe the objects encircled by this boundary. Let’s look at how NIST defines assessment objects:

SP 800-171 lists computers, operating systems, and applications as examples of information systems. The definition of assessment objects also incorporates activities, individuals and physical facilities. Scope refers to not only assets (technology, people and facilities) but activities and processes as well.
Assessment objects fall into one of two categories:
- Those assets that process, store, or transmit CUI (CUI Assets)
- Assets that provide security protection for CUI Assets (Special Protection Assets)
CUI Assets include people, technology, or facilities that process, store or transmit CUI. Likewise, special protection assets also include people, technology, or facilities that provide security functions for CUI Assets. Security protection assets do not need to process, store or transmit CUI themselves.
Now that we know we need to look for more than computers, let’s go back and focus on the second part of the guidance, which discusses security domains.

You can create a separate security domain for CUI with physical or logical isolation, or both. Let’s talk about physical isolation first.
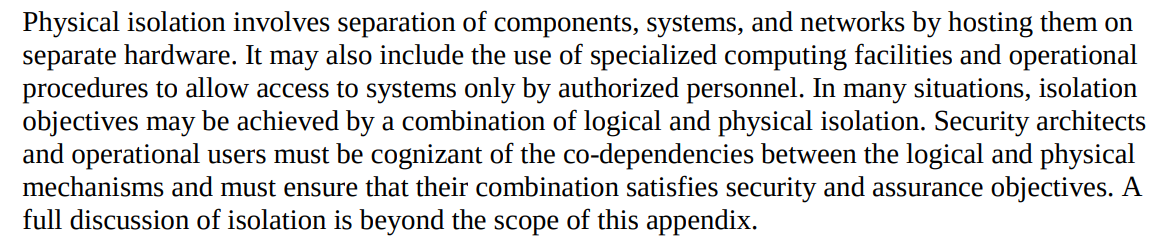
Physical isolation occurs when security domains are not connected (wired or wirelessly). Systems are "air-gapped" if they are not connected and data transfer is only possible through human interaction.
Logical isolation exists within a system by using tools to control information flow. A logically isolated system connects to another but uses mechanisms to create isolated processing environments.
Is the Scope the Same for CMMC Level 2?
If you’re researching NIST SP 800-171, your CUI may originate from a DoD contract. Accordingly, you might be preparing for a third-party assessment of these controls in your environment.
In December 2021, DoD released the CMMC Assessment Scope Level 2 guide. Under CMMC 2.0, the implementation of NIST SP 800-171 controls may either be self-assessed or assessed by a certified assessor. The bifurcation of contracts that will require a third-party assessment vs those that will not is still unknown. DoD has advised that it will relate back to a risk assessment conducted on the criticality of the CUI in relation to national security.
The Level 2 Scoping Guide is useful as it provides more clarity on the segmentation of scope. We’ve already discussed CUI Assets and Special Protection Assets based on the NIST SP 800-171 definitions. These are the primary assets assessed in CMMC as well but there is one slight change we’ll make to the definition of Special Protection Assets.
As defined in NIST SP 800-171, Special Protection Assets provide security functions to CUI Assets. Under the CMMC guidance, Special Protection Assets also provide security functions for contractor risk-managed assets and specialized assets.
Contractor risk-managed assets do not need separation from CUI assets. Instead, these assets are not intended to handle CUI through the use of a policy, procedure, or practice. They remain in the CMMC Assessment Scope but they haven’t assessed all controls. Control 3.12.4 still requires documentation of these assets in the system security plan (SSP).
Specialized assets do not need separation from CUI as some may even process, store or transmit CUI. They are also included in the CMMC Assessment Scope and not assessed against any practice other than 3.12.4. These assets include several sub-categories, including:
- Government property
- Internet of Things (IoT)
- Operational Technology (OT)
- Restricted information systems
- Test equipment
CMMC provides us with two categories of exceptions that were not present in the original NIST SP 800-171. CMMC appears to expand the scope of security protection assets to anything that provides security functions to non-isolated assets.
Scoring Using the Supplier Performance Risk Portal (SPRS)
Under DFARS Case 2019-D041, suppliers must conduct an assessment of NIST SP 800-171 on covered information systems. An accompanying scoring method reflects the net effect of requirements not yet implemented. Results uploaded into the Supplier Performance Risk System (SPRS) verify the supplier's scores are not more than three years old.
You’ll need access to the Procurement Integrated Enterprise Environment (PIEE) and your Commercial and Government Entity (CAGE) Code. Following the instructions provided in the quick entry guide will allow you to enter your assessment score.
There are three levels of assessments that an organization can perform:
- Basic - self-assessment completed by the supplier
- Results in a low confidence level
- Medium - involves government review of the SSP
- Results a medium confidence level
- High - assessment completed by the government through review of evidence
- Results in a high confidence level
The choices for assessment scopes include:
- Enterprise - the entire company’s network is under the CAGEs listed
- Enclave - standalone under Enterprise CAGE as a business unit
- Contract - contract specific SSP review
You will only need to provide a summary level score. Please keep in mind that your summary score is CUI, so restrict access accordingly.
As we have discussed before, there are a total of 110 controls within NIST SP 800-171. A perfect score would be 110 points. Annex A of the DoD Assessment Methodology provides a point scale (1, 3, or 5) for each control. The scores reflect the impact the control has on the security of the network or data. For each control not implemented, subtract the value of that control from 110. The lowest score is -203 but without an SSP, any assessment is incomplete and non-compliant with DFARS clause 252.204-7012.
There are 42 controls with a score of 5 points. Failure to put in place these security requirements poses a high risk of exfiltration of DoD CUI. It is also likely that these will not be eligible for POA&M under CMMC 2.0. These controls include:
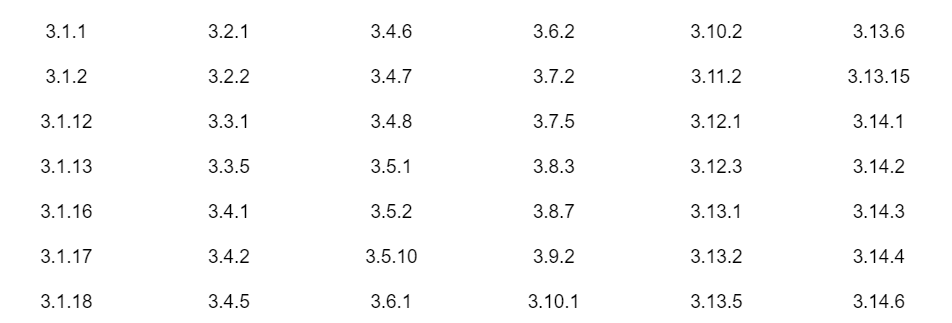
Partial implementation of the following two controls mitigates their scoring impact:
- 3.5.3 Multi-factor authentication (MFA) - If implemented for remote and privileged users but not general use, only subtract 3 points. If MFA is not implemented for any user, subtract 5 points.
- 3.13.11 FIPS validated encryption - When required, if employing encryption that is not FIPS 140-1 or -2 validated, subtract only 3 points. If required but not employed, subtract 5 points.
There are 14 controls that have a score of 3 points, including:

Control 3.12.4 is not worth any points. Without it, however, any assessment is non-compliant with DFARS clause 252.204-7012.
That leaves 51 controls that are worth 1 point each.
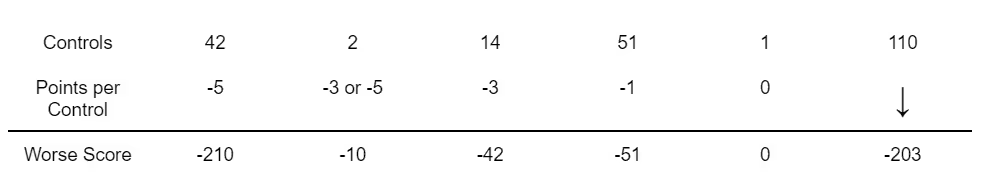
Having a plan of action & milestones (POA&M) is not a substitute for a completed practice. You may assess controls as implemented even if they have temporary deficiencies as long as you address them with a plan of action. This might include those requiring corrective actions (patches) but showing progress towards implementation. There is no standard duration for a temporary deficiency but you should resolve them in a reasonable amount of time.
Some controls may not be relevant to the supplier. For example, if remote access is not allowed, score practice 3.1.12 as not applicable or not implemented and deduct no points. A policy or procedure should still exist to ensure that these types of capabilities are not enabled.
Suppliers may receive a determination from DoD CIO that an alternative security measure is as effective as one in NIST SP 800-171. Consider security controls approved as not applicable through alternatives as implemented. Suppliers should include any DoD CIO assessments in the SSP.
What are the NFO Controls?
At the very end of NIST SP 800-171 Rev 2 is Appendix E, Tailoring Criteria. This appendix provides a list of controls from NIST SP 800-53 Rev 4 and FIPS 200 that were not included in NIST SP 800-171 for one of three reasons:
- FED - the control or control enhancement is federal (i.e., the responsibility of the federal government)
- CUI - the control or control enhancement is not related to protecting the confidentiality of CUI
- NFO - nonfederal organizations (NFO) should routinely satisfy the control without specification.
NIST supplements the phrase routinely satisfied… without specification with the cautionary note on page 8:

In the CMMC-AB Town Hall from January 25, 2022, CEO Matt Travis dispelled a rumor that CMMC 2.0 does not require written policies and procedures. He first references Appendix E on a slide titled "CMMC Rumor Control".
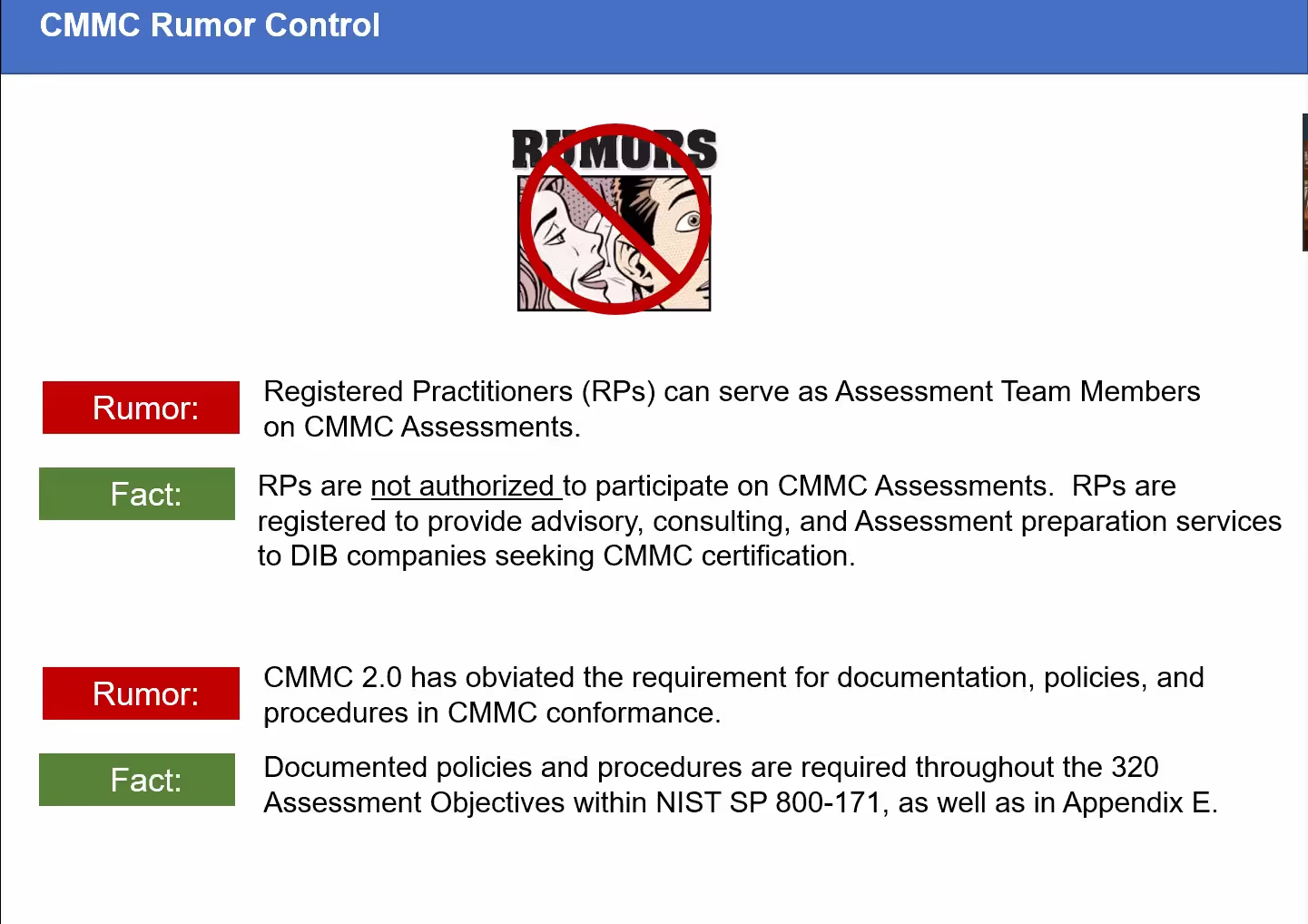
Matt provided his own interpretation of Appendix E during the question-and-answer part of the meeting. He believes the NFO controls are in play but acknowledged that DoD should elaborate on the question. There is a great thread on LinkedIn started by a CMMC Provisional Instructor. Several other provisional assessors back his conclusion that NFO controls are out of scope.
Before you start reading through the NFO controls, it is important to note that NIST updated SP 800-53 Rev 4 to Rev 5. This update moved and consolidated some of the controls listed in Appendix E.
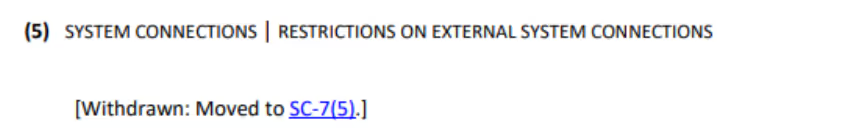
For example, NFO control CA-3(5) from NIST SP 800-53 Rev 4 stated:

NIST withdrew this control in Rev 5 and moved to SC-7(5).
The updated control in Rev 5 states:
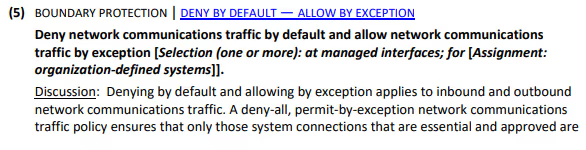
If we look at Table D in NIST SP 800-171 for SC-7(5), we find that this control is already mapped to control 3.13.6
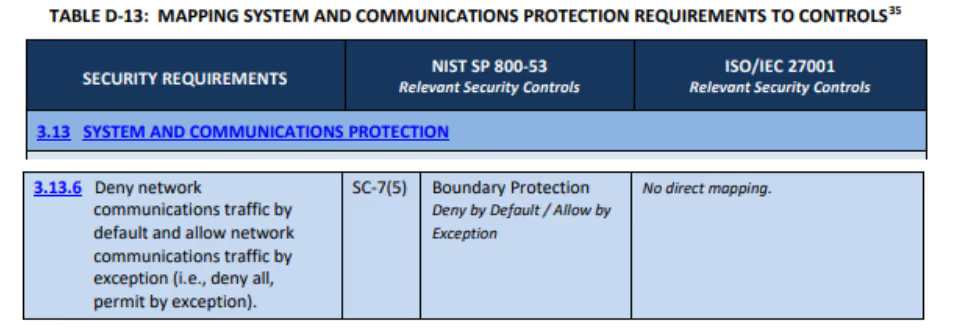
Reading the control in NIST SP 800-171, we find:

Similar updates have removed the following 6 NFO controls:
Original Rev 4 NFO ControlNew Control in Rev5Mapping to NIST 800-171CA-3(5)SC-7(5)3.13.6CM-2(1)CM-23.4.1 & 3.4.2CM-8(5)CM-83.4.1 & 3.4.2MA-4(2)MA-43.7.5PL-2(3)PL-23.12.1, 3.12.2, 3.12.3 & 3.12.4RA-5(1)RA-53.11.2 & 3.11.3
According to Rev 5, MA-4(2) split into MA-1 and MA-4.
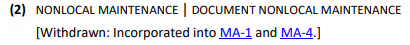
According to NIST SP 800-171, MA-4 maps to 3.7.5 but MA-1 is an existing NFO Control.
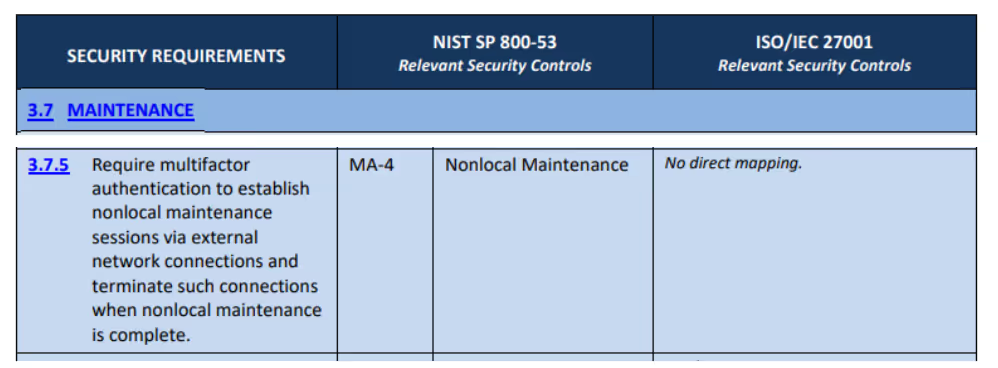
There were a total of 61 NFO controls listed in Appendix E of NIST SP 800-171. After reviewing the updates from these controls in NIST SP 800-53 Rev 5, we can remove 6, leaving us a total of 55.
There are determination statements associated with these controls as well. To find these, we need to look at NIST SP 800-53A Rev 5.
In addition to determination statements, NIST SP 800-53A also uses organization-defined parameters (ODPs). These ODPs either assign a defined value (e.g. frequency) or select operations from one or more options provided.
The table below summarizes the NFO controls as well as the number of corresponding ODPs and determination statements for each.
What about the Delta 20 Controls?
Delta 20 refers to 20 controls added to NIST SP 800-171 in the initial launch of CMMC. The introduction of CMMC 2.0 removed these 20 requirements to bring the requirements back in line with SP 800-171.
However, that doesn’t mean you should completely take these controls off your radar. There is value in reviewing these security controls and determining if you should be performing them.
The primary focus of NIST SP 800-171 is to protect the confidentiality and integrity of CUI. Some of the Delta 20 practices, such as those in the Recovery domain, address the availability of information. New threats spawned the development of others, such as the implementation of advanced email protections in SI.3.218 and SI.3.219.
Inside Cybersecurity reported shortly after the announcement of CMMC 2.0 that NIST plans on updating SP 800-171 Rev 2. Based on the time horizon of CMMC 2.0 rulemaking, it is likely Revision 3 will occur before the implementation of CMMC. We expect NIST to incorporate some, if not all, of the Delta 20 controls into the third revision of NIST SP 800-171.
Conclusion
This started out as a discussion about a template to self-assess NIST SP 800-171. We discussed that although there are 110 practices, the assessment guide lists 320 determination statements.
First, we discussed the need to scope not only information systems in the traditional sense, but security protection assets, people, facilities, and processes. Second, we touched on how to self-assess using the DoD assessment method.
Third, we took a look at Appendix E and the 61 NFO controls that when tailed using the latest guidance from NIST SP 800-53 equate to 55 controls.
Finally, we explained the Delta 20 controls, which NIST may incorporate in the next release of SP 800-171.
We couldn’t produce a self-assessment template if we didn’t discuss these factors first. Because a useful template should account for each of these variables.
A basic template should allow you to choose between a full NIST SP 800-171 self-assessment or a CMMC Level 1 assessment of the FAR 52.204-21 requirements. A better template should start with the determination statements and roll up compliance to the control statements.
A good template should calculate your SPRS score based on the implementation status of the determination statements.
A great template should account for all 663 determination statements found in the 55 NFO controls.
A well-thought-out template should give you the option to assess your implementation of the Delta 20 controls using their determination statements.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




