What CMMC Stands For and Why You Need Know It
If you’re a DoD contractor, you’re probably wondering to yourself, “Why do I need to care about CMMC?” Luckily for you, the rest of this blog post explains what CMMC is and why you need to know it.

This blog contains updated information regarding the CMMC 2.0 updates from November 4, 2021.
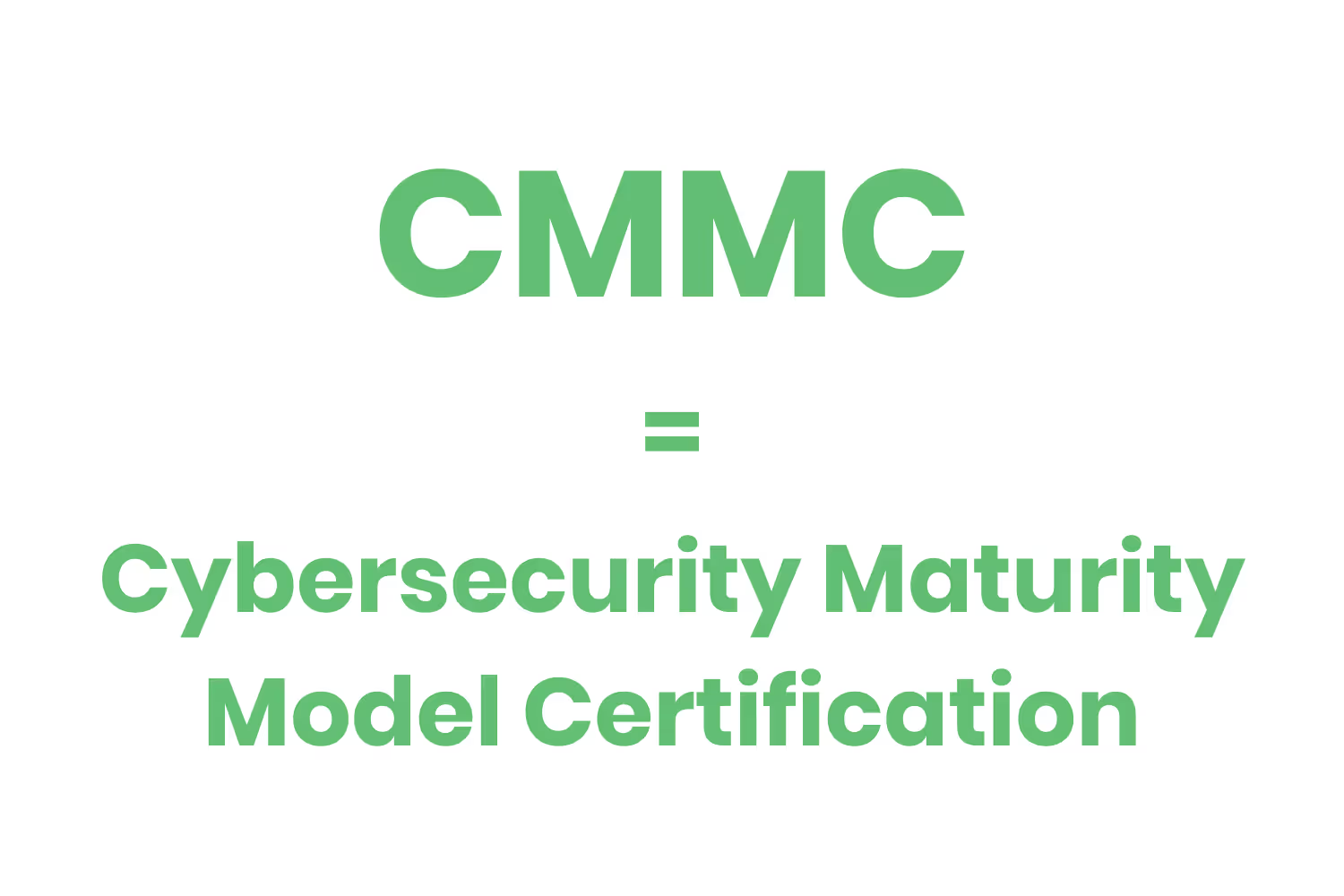
CMMC stands for the Cybersecurity Maturity Model Certification. Although a simple acronym, it’s not an easy regulation. It’s an upcoming standard that’s placed on the Defense Industrial Base (DIB).
At the time of writing, writing and deliberating the standard is still happening in Washington. As such, there are a lot of rumors and misinformation swirling around the topic.
However, even with all of the confusion, there are still a few definitives we can retrieve.
The first, and most important, absolute is that the Department of Defense is the governing body that’s mandating CMMC. The DoD plans on enforcing it from now until 2026, steadily increasing the number of contracts that contain CMMC as a requirement.
The second absolute is that the baseline requirements exist around NIST SP 800-171. As the field of cybersecurity matures, it’s likely that new practices will get added. But, the 110 practices that make up NIST 800-171 and the nonfederal organization (NFO) controls listed in Appendix E are the established baseline of CMMC.
The CMMC Accreditation Body (AB) is the accrediting authority within the ecosystem. The CMMC-AB will be accrediting all certified third-party assessors (C3PAOs). They will also accredit CMMC Assessors and Instructors Certification Organization (CAICO), who will in turn, be accrediting assessors and instructors.
Alright, within just a few small paragraphs we now know what CMMC stands for and the authorities that govern the ecosystem.
Even after all of that, though, you’re probably still wondering to yourself, “Why do I need to care about CMMC?”
Luckily for you, the rest of this blog post explains what CMMC is and why you need to know it.
You'll Likely Need to Follow It
If you’re completing or bidding on any contracts dealing with Federal Contract Information (FCI) or Controlled Unclassified Information (CUI) for the DoD, there’s a high chance that you’re going to have to follow CMMC. That’s just the reality.
You see, the only contractors who don’t need to worry about CMMC are those who provide commercial off-the-shelf (COTS) products. In other words, these contractors don’t make any modifications to the products that they’re selling to the DoD. Civilians could purchase the same exact product that the COTS contractor provides to the government.
To put it simply, COTS contractors don’t need to adhere to CMMC because they don’t deal with or modify their products from what is commercially available.
COTS isn’t a free pass to be able to win contracts with the DoD. These products still need to meet the definitions listed under FAR 2.101 and DFARS 204.7304(c) to be eligible.

The CMMC requirements for suppliers dealing only with FCI are really no different than they are today with Federal Acquisition Regulation 52.204-21. They will get asked to self-assess and attest that they are meeting the basic cybersecurity requirements much like they do today.
CUI is really the key delineation between a contractor who needs to worry about CMMC and one who doesn’t.
You see, the government has always placed a special emphasis on safeguarding classified information (rightfully so). Even though CUI doesn’t have a classified designation, safeguarding is still required by Federal and DoD guidance (DFARS 252.204-7012).
In the past, the guidance on CUI was more or less based on good faith. The safeguards existed and the DoD trusted that the DIB was following them.

On July 23, 2019, the DoD published the results of an audit on the protection of CUI on contractor-owned networks and systems. The audit looked at a nonstatistical sample of 26 of 12,075 contractors with DoD contracts worth $1 million or more. From that sample, the DoD selected and evaluated 9 contractors.
Needless to say, the report found that the contractors didn’t consistently implement mandated system security controls in 11 different areas.
A little over 6 months later and CMMC was born to ensure that the DIB adheres to and has an approved third-party assessor attest to safeguarding CUI via mandated controls.
Your Level Determines Your Requirements
There are 3 levels involved with CMMC 2.0. Each level builds on one another and requires adherence to stricter controls as it increases.
To break it down…
- Level 1: 17 practices based on FAR 52.204-21
- Level 2: 110 practices based on NIST SP 800-171
- Level 3: 110+ practices based on NIST SP 800-172
You can see how things start getting a lot more complicated depending on where you fall within the CMMC ecosystem.
One of the best questions to ask yourself is exactly that, “What level of CMMC is my organization?”
From a high level, the answer is simple.
What level you fall within CMMC depends whether you deal with FCI or CUI.

For example, let’s say that your organization manufactures nuts and bolts. It just so happens that one of your biggest clients purchases your nuts and bolts in building their torpedo propulsion system. Your client then has a client who installs their propulsion system into a state-of-the-art torpedo. There are a lot of partnerships happening in this example, stay with me.
In this instance, your client’s client is likely the highest CMMC level (aka prime). They’re scoring massive deals for a wide variety of DoD products. Your client is an important piece, but they’re smaller scale. You happen to be the last part of the puzzle and are the smallest.
So, where do you fall in this example? Even though your materials aren’t sold directly to the DoD, you’re within the supply chain and CUI flows down for you to perform your portion of the contract. The presence of CUI indicates you would be a candidate for Maturity Level 2 as well.
This is the unfortunate scenario you’ll need to deal with because CMMC’s requirements also flow down to subcontractors.
To be specific, the flow down requirement exists within DFARS clause 252.204-7021.

What a headache, right?
Luckily, CMMC Level 2 requirements are the same requirements you are self-attesting to today with DFARS 252-204-21. The only difference with the introduction of CMMC will be the possibility that a certified third-party assessor organization will audit your cybersecurity practices to confirm that you are complying with this current requirement. Not all Maturity Level 2 certifications will require a third-party audit, DoD will prioritize those deemed critical to national security.
You Need to Get Started Now
I’m sure after reading all of the previous sections in this blog post, you’re understanding the sense of urgency I’ve tried to instill.
I need to come clean, though. The reality is that rulemaking is what controls CMMC’s implementation. The rulemaking will affect...
- Part 32 of the Code of Federal Regulations (C.F.R.)
- Defense Federal Acquisition Regulation Supplement (DFARS) in Part 48 of the C.F.R.
The current estimate for final rulemaking is between July 2022 to October 2023.
However, that doesn’t mean that it’s something to put off.
You see, there are a lot of steps involved with complying with CMMC…
- Implement and assess information security processes
- Improve processes and submit Supplier Performance Risk System (SPRS)
- Identify your scope
- Schedule a GAP assessment with a third-party
- Address GAP assessment findings
- Vent and choose a C3PAO
- Undergo the CMMC assessment
Once you complete that step-by-step process, it’ll be 4 years in the future. I’m being facetious.

However, this is a great place to note that the recommended waiting period between an application and certification audit scheduling is at least six months.
To slow things down even more, organizations seeking certification (OSCs) have a maximum of 90 days to resolve any issues that the C3PAO finds during their assessment.
Also, a cultural component to it.
Registered Practitioner, Ty Whittenberg from Rea and Associates stated, “When the assessors come in, they're not looking just for, ‘do you have a written policy?’ They’re looking to see if your culture matches.
I haven’t even mentioned the broad scope of the CMMC ecosystem. The DoD conducts business with over 300,000 contractors.
At the time of writing, the CMMC-AB marketplace only lists…
- 562 Registered Provider Organizations
- 2,062 Registered Practitioners
- 35 Provisional Instructors
- 123 Provisional Assessors
- 54 Licensed Training Providers
- 19 Licensed Partner Publishers
- 0 Certified CMMC Professionals
- 196 C3PAO Candidates
- 5 Authorized C3PAO
In other words, there simply isn’t enough manpower out there to speed up the CMMC certification process. Thus, getting started now is the best option for you.
You Might Have a Hard Decision to Make
By now, you realize and agree with me that CMMC isn’t a small undertaking.
It’s something that every organization that plans to continue to bid on DoD contracts needs to put resources towards. Otherwise, winning bids just isn’t going to happen.
However, your organization may be in a situation where you need to make a hard business decision.

Maybe you don’t conduct enough business with the DoD to justify spending all of this time, money and effort toward achieving a CMMC certification.
After all, you don’t want to end up putting your organization in a tough financial position just so that you have a better chance to win contracts.
Achieving the CMMC-compliant designation doesn’t guarantee you business, it grants you the ability to win it.
Conclusion
To reiterate the entire purpose of this blog post, CMMC is an acronym that stands for the Cybersecurity Maturity Model Certification.
It’s a big-time requirement that’s coming down the DIB pipeline from the DoD.
You need to know it because it will hamper your ability to win bids on defense contracts if you don’t achieve it.
However, since it’s not easy to achieve and there currently aren’t enough resources, contractors need to start preparing for the certification now.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




