[ANSWERED] Which is The Recommended Method for Verifying an Email's Legitimacy?
While hackers have many ways in which they create and send phishing emails, there are only a few key tips every user should know in order to stay safe. So, let’s take a look at the recommended method(s) for verifying an email’s legitimacy.

In case you haven’t heard, phishing is the latest (not really) and (not so) greatest form of cybercrime today. In fact, phishing is now the most common form of cybercrime producing approximately 3.4 billion spam emails every day.
This is a pretty wild number considering as of 2020, there are approximately 4 billion email users worldwide. So I’d wager to say most of us have come across a phishing scam at least once in our lives. Maybe you never noticed it and it just went straight to your spam folder. Or maybe you did open a strange email and had to learn about phishing and cybercrime the hard way.
I’m not here to judge. If that were you, just know that you’re not alone. That’s why I am writing this blog after all. However, there is good news. By following best practices and prevention, you can thwart these phishing attempts!
For those of us who don’t eat, sleep, and drink cybersecurity, have no fear… this blog post is here! While hackers have many ways in which they create and send phishing emails, there are only a few key tips every user should know in order to stay safe. So, let’s take a look at the recommended method(s) for verifying an email’s legitimacy.
What is Phishing?
Before we dive right into the verification process, I need to level-set a little bit.
So, let’s get into more detail about what phishing is and why it’s so dangerous. When we talk about phishing, we’re talking about a type of malware that takes advantage of both social engineering and technical subterfuge to steal user information.
Social engineering schemes fool victims into a false sense of security by pretending to be a legitimate party. Hackers will then send an email under the guise that they are the trusted party and oftentimes include links to fake websites. Then, they trick them into entering their username and password information.
Technical subterfuge works a bit differently, but it’s the same sort of idea. The difference is that this scheme plants malware onto a victim’s computer to steal their information directly without needing them to fill in their data.
Some examples of user information may include their usernames, passwords, phone numbers, and other personal identifying information.
Of course, there are a ton of other different phishing techniques out there but for the sake of this blog post, you get the picture.
Email Verification Steps
Most phishing attacks share commonalities that are identifiable if you know what to look for.
While you might feel comfortable deciphering between a legitimate email and one that is a scam, remember that it only takes one employee opening a compromised link for a phishing operation to be a success.
Everyone in your company must be aware of the signs that come with phishing emails.
#1 Inspect
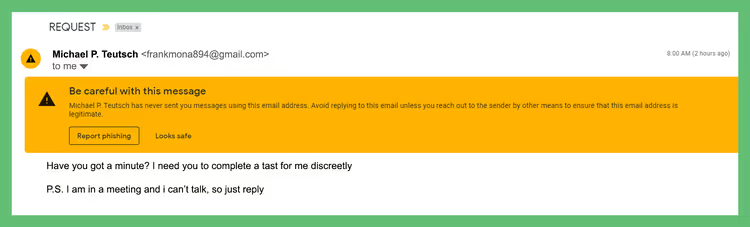
A great way to protect yourself from a phishing attack is to first validate the email address identity. Attackers may try to make their display name look similar to that of the person they’re trying to imitate.
By hovering over the display name with your cursor, you can find out if the email address matches the alleged sender or is a spoof.
You can compare this address with previous emails if it’s from someone you regularly communicate with. If the email is from a company, look up the company online and verify the address through the official site. If you can’t find that address, it’s likely the email is a scam.
#2 Domain Name
An email that’s coming from a legitimate organization will almost always have the company name in the.
One of the most obvious ways to clock a phishing email is when a large company has a domain name such as ‘@gmail.com’ or any other free email service provider.
You can also search for the domain name in a search engine such as Google. Search engines can be great for making scams visible when they have awareness of them. A quick search on the internet can help you find out if anyone else is experiencing the same issues.
#3 Misspellings and Incorrect Grammar
If you receive an email that sounds like artificial intelligence wrote it instead of your boss, it probably was. As humans, we all have our own unique manner of speaking. This often shows in the emails we send out every day.
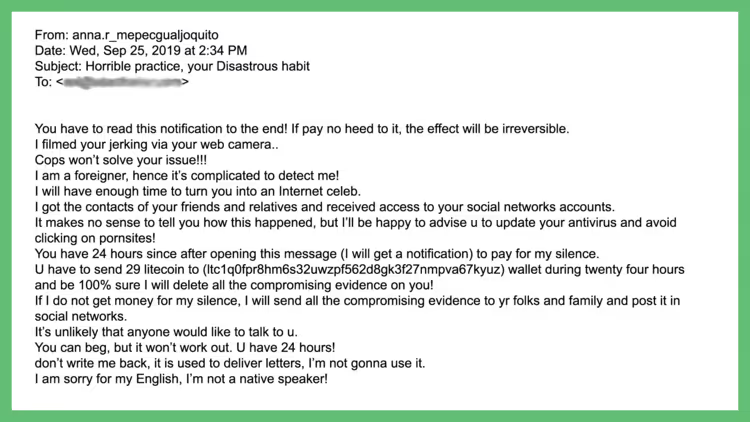
If you receive an email from someone you correspond with regularly and they have more grammatical errors than usual or misspellings, this could be a red flag. Phishers from other countries tend to use online translators, which as you can imagine don’t always return the perfect grammar or spelling. Legitimate companies will also use a spell-check feature before sending out emails.
#4 Subject Lines
A tactic that cybercriminals use when it comes to sending phishing emails is to leave the subject line blank. Doing this can help a hacker find out whether the email address they are trying to reach is legitimate. If it is not, they will receive an automated bounce-back email and will know to move on to another target.
According to an AtlasVPN report, about 70% of all phishing emails contain empty subject lines. Just be careful not to mistake Mom’s weekly inspirational quote for spam if she forgets to include a subject line again.
#5 Unsecured Sites
Make sure when dealing with website URLs, the site you are on starts with “https”. Also, if you cannot see a closed padlock icon next to the URL, don’t release any sensitive information or download any files from that site. This may not necessarily mean you are entering into a phishing scam, but it doesn’t hurt to side on the air of caution.
#6 Check Hyperlinks
Phishing emails may look normal at first glance, so it’s important to not jump the gun on anything. Take a moment to check out any links that may be in the email. By ‘check out’ I don’t mean immediately clicking on them! In fact, that’s exactly what hackers want you to do.
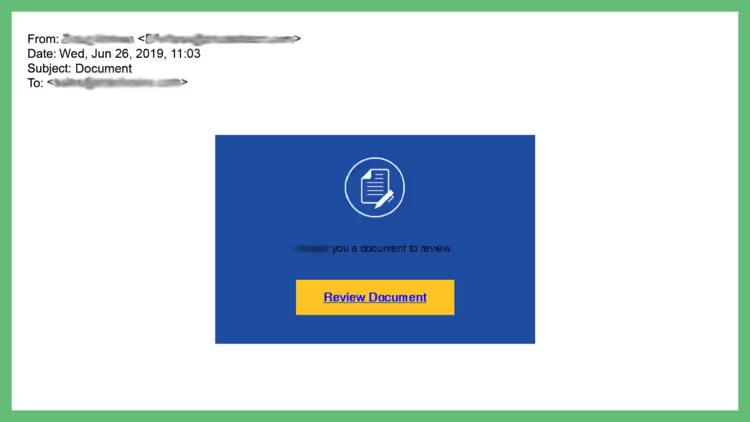
By clicking these links and following the instructions given, hackers can steal a user’s sensitive information and infiltrate their network. To avoid this, try hovering over links to verify the URL. Note any misspellings in the URL or inconsistencies between that link and the alleged company’s website URL. Whatever you are receiving from this company should match their website domain.
#7 Be Wary of Attachments
If you are not expecting an email with an attachment, here is probably one of the most important rules you can follow: don’t open any attachments until you are sure they are legitimate.
What does that mean? Do your best to reach out to the sender directly to make sure the email is legitimate. An attachment sent by a hacker can contain malware that once you open it, will expose your computer system and your private information.
The ESET 2022 Threat Report lists the top most prevalent malicious attachment types used in phishing attacks:
- Windows Executables (47%)
- Script Files (23%)
- Office Documents (19%)
- PDF Documents (6%)
- Shortcuts (4%)
#8 Question Urgency
There are two psychological tactics phishers tend to use to lure their victims with rewards or scare tactics. This urgency gets users to let down their guard for a moment and consider what they rationally might never do. The email may look like your boss needs you to randomly wire them some money. Or maybe you got another email from your old friend the Nigerian Prince, asking for help again.
If the message is pushy, asks for immediate action, or even sounds vaguely threatening you could have a phishing scam on your hands.
#9 Time and Date
The likelihood that your boss is going to ask you to pay an invoice outside of business hours is slim to none. Not impossible, I’m sure, but for the most part receiving urgent emails at 11:00 pm to open an invoice attachment should raise some flags.
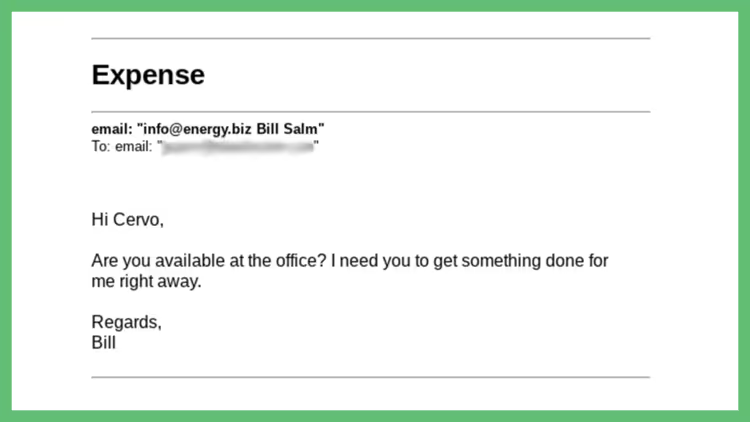
Take caution with any “work” or business-related emails that fall outside of your work hours. Phishers may work in a different time zone than you, so their bait could land in your inbox while you are sleeping.
This detail alone might not sound too incriminating, but pair it with any of the other red flags in this blog and you might have yourself a phishing attack. At the very least, follow up with the person who allegedly sent this out-of-character email at 1:00 am. Maybe they just really need your approval on an office order.
#10 Cut Out The Middle Man
When in doubt, just pick up the phone or walk down the hall and ask your coworker, client, or third-party vendor if they did in fact send you something. Chances are that if Phil from accounting is in the office, he probably didn’t send you that “I’m stuck in London, send money” email. Just be sure to use a verified phone number and not one from the email in question.
The Best Method
How did you enjoy that crash course in phishing?
Hopefully, you found some of these tips helpful! I will admit, I did list quite a few and in the moment of trying to decide whether an email is legitimate or not, you may not have time to come read through this blog again.
Luckily, there’s the SLAM method when it comes to determining whether an email is a phishing scam or not. The tips mentioned in this article can all fall under the acronym that is SLAM.
All you have to do is remember what SLAM stands for:
- S- Sender
- L- Links
- A- Attachments
- M- Messages
Conclusion
Successful phishing attacks can have major consequences for individuals and organizations alike. The following are a few examples:
- User Downtime
- Damage to reputation
- Loss of intellectual property
- Compliance fines
- Direct monetary losses
- Legal fees
- Loss of revenue and customers
Data loss is another major consequence of falling for a phishing scheme, but what data do hackers really look for? According to a Verizon study, credentials such as usernames and passwords makeup 63% of data stolen. Internal data like sales figures make up 32% and personal data, such as addresses and phone numbers, make up 24%.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




