CMMC-AB August Town Hall: 11 Unanswered Questions and Key Takeaways
The CMMC-AB had a lot to talk about during its town hall in August. Here are answers to unanswered questions and key takeaways.

Takeaway 1: Assessments At a Snail's Pace
- Question 1: When can we expect assessments to start?
In the Town Hall, Matthew Travis responded to this question upfront. He said that he still thought assessments could start by September 20th, 2021. He didn’t elaborate much and moved on to the next topic after providing this answer.
Organizations seeking certification (OSCs) may want more of an explanation.
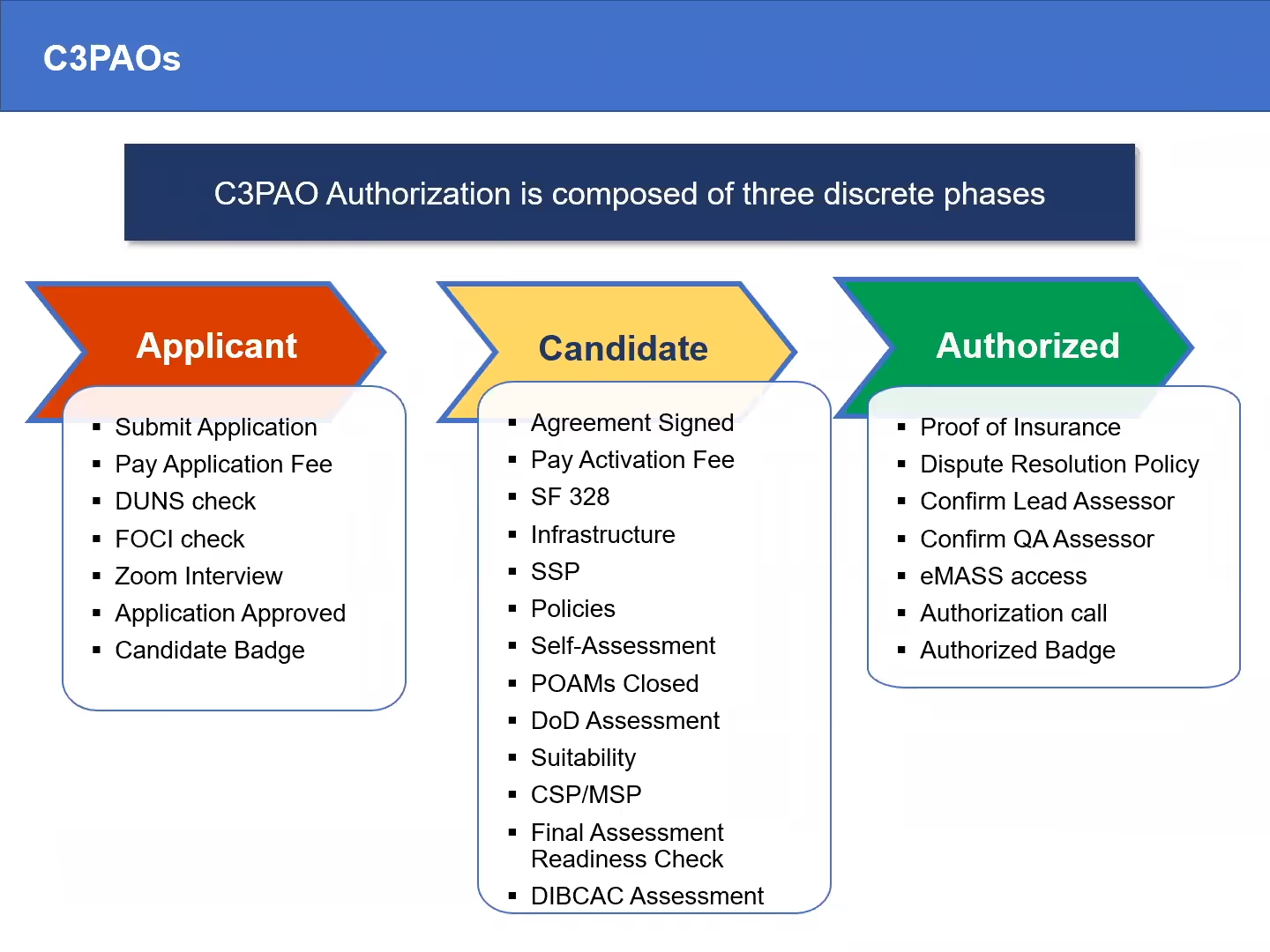
If an OSC wants to get assessed now, they must first contact the CMMC-AB. They then need to show that they’re bidding on a contract that contains CMMC requirements.
The AB will then get in touch with authorized C3PAOs. Kicking-off coordination with the OSC if they can assess with a provisional assessor.
There are few provisional assessors and even fewer C3PAOs. But, there's a small chance that you’ll have a provisional assessment completed by the end of this year.
There are over 500 companies that have registered to become C3PAOs.
About 180 still need to have their assessments completed.
DIBCAC assessments of C3PAOs have rolled out at a snail’s pace this summer. If DIBCAC could perform 110 C3PAO assessments per year, that would mean we could see about 55 authorized C3PAOs by February.

But we haven’t seen that pace so far since the authorization of the first C3PAO in June 2021. There are only 4 as of Sep 7, 2021. Based on this, we project there would be 25 or so by the time the first class graduates in February 2022.
The CMMC-AB hasn’t certified any assessors. Their training is on hold until DoD rulemaking occurs. We’re currently in the provisional assessment phase.
There are currently 106 provisional assessors listed in the CMMC marketplace.
The big disconnect is with provisional assessors. The majority of them don’t work for the authorized C3PAOs. The 4 authorized C3PAOs only have a combined 6 provisional assessors.
This is likely creating another bottleneck. C3PAOs will need to contract with provisional assessors to complete assessments.
So for a low estimate, we would say in October, there might be 20 to 40 OSC provisional assessments taking place. There’s a capacity for more.
If every provisional assessor completed two assessments in October, we could see as many as 200 completed. Many OSCs are probably better off waiting rather than paying a premium and rushing into provisionals. Especially given the scarcity of resources available to conduct the assessments.
Don’t expect any certifications issued before DoD rulemaking.
The outcome of these assessments will remain provisional until then. If the rule changes after the provisional assessment, OSCs will need to do a delta assessment. Yet another reason it’s probably better to wait.
Takeaway 2: Pausing Speculation
- Question: On Friday, General Skinner of DISA addressed Industry in a virtual Brown Bag session. He mentioned that DoD has paused CMMC. Can you speak to this, please?
This was the most asked but answered question.
We can confirm this event did occur on August 27, 2021. We’ve asked for a copy of the presentation to confirm General Skinner did say CMMC was on pause.
The presentation should be available on DVIDS within the next week or so. There does seem to be a disconnect between DoD and the CMMC-AB when CMMC rulemaking will occur.

When it comes to DoD’s timeline for CMMC, Wayne Boline of the Accreditation Board admitted in a later question “we could only speculate”.
Based on the history of missed deadlines, one could conclude that CMMC has paused new solicitation requirements. The CMMC-AB’s work continues to build the ecosystem with C3PAOs, RPOs, LTPs and LPPs.
Many OSCs are still working towards building their System Security Plans (SSPs) in compliance with NIST 800-171. Not to mention shrinking their Plan of Action and Milestones (POA&Ms).
Takeaway 3: MSP Scope of Assessment
Has there been any clarity on whether an IT service provider (MSP) will need to get certified at or above the same level that their client’s?
If an MSP has logical access to the information systems containing CUI then yes. In that case, you should consider the MSP as within the scope of an assessment.
Takeaway 4: Presidential and Congressional Actions
- Question: In May the President created an Executive Order on cybersecurity . It seems to point towards NIST & CISA taking the lead on governmental cybersecurity initiatives. In addition, there seems to be congressional review activity around CMMC. What are the risks and opportunities that could come from these executive/congressional actions and activities?
On May 12, 2021, President Biden issued the Executive Order on Improving the Nation’s Cybersecurity. This came in direct response to the Colonial Pipeline hack.following the Colonial Pipeline hack.
This order removed sharing information barriers. Especially between contractors and the Cybersecurity and Infrastructure Security Agency (CISA).
The Federal Acquisition (FAR) Council would receive a new contract language. Providers who collect cybersecurity information could share it with and cooperate with authorities.
In this order, CISA is the central collection agency for cyber incidents.
Section 2 goes on to state “standardizing common cybersecurity contractual requirements across agencies will streamline and improve compliance for vendors and the Federal Government.”

By July 11, 2021, the order called for a review. This review affected all agency-specific cybersecurity requirements and recommendations for standardization. The order then directs all agencies to remove any FAR duplicates. Thus, standardizing cybersecurity across all agencies.
Section 3 recommends the adoption of security best practices. It includes Zero Trust, cloud services, Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).
By July 11, 2021, it calls for agencies to develop a migration plan to Zero Trust. This call comes based on an outline provided by the National Institute of Standards and Technology (NIST).
In Section 4, NIST was also tasked with developing standards, tools and best practices to test software security. Including those developers in the software supply chain.
By May 11, 2022, it called for NIST to publish guidance on software security.
It also called for CISA to identify a list of categories of software “critical software” and, working with NIST, publish separate guidance applying practices of least privilege, network segmentation, and proper configuration.
This executive order does identify CISA and NIST as leading the Federal cybersecurity efforts. Yet, third-party auditing organizations would still supplement these agencies.
CISA’s role is for higher-level analysis of cybersecurity incidents. NIST'S role is to incorporate this analysis into standards and practices. Neither of which would interfere with the implementation of CMMC. Neither of which would interfere with the implementation of CMMC.
The most recent congressional review we could find happened on June 24, 2021. It took place in the Subcommittee on Oversight, Investigations, and Regulations.
In this hearing, Jonathan Williams of PilieroMazza PLLC, acknowledged implementing CMMC. But, cautioned that bottlenecks getting C3PAOs may “jeopardize certain contractors’ abilities to receive new contract awards if they are unable to receive timely approval of their application”.
Williams also acknowledged that although DoD released a proposed rule change. Also, they’ve stated that the final version may be different. The delay in issuing a final rule coupled with the slow C3PAO certification process doesn't help. It has contributed to many of his SMB clients taking a “wait and see” approach to preparation.
He posited several suggestions to assist small businesses:
- Enhancing the Small Business Administration (SBA) All Small Mentor-Protege Program (ASMPP). Providing financial and technical resources needed for certification.
- End the restrictions for small businesses to have only two mentors. Further enabling them to get help for different areas of their business (procurement, technical, CMMC)
- Unpopulated Joint Ventures shouldn't need CMMC. Instead, one of the partners that will handle the covered information should need CMMC.
- Enable Small Businesses to be fast-tracked for certification if they win a contract with CMMC requirements.
- Build-in Flow-Down Protections for small businesses. These stop prime contractors from requiring a higher level of CMMC than is necessary. Thus, enabling communications between the subcontractor and contracting officer.
- Encourage flexible approaches such as secure enclaves with CUI hosted by the prime contractor but accessible by a sub who only holds a Maturity Level 1 certification.
- Consider a grant for small businesses. These will help with strengthening cybersecurity hygiene and achieve the necessary level of CMMC.

Mr. Williams’ answers prove Congress' interest in making sure small businesses aren't hurt by CMMC.
The opportunities for improvement don’t change the published direction of CMMC. Thus, congressional nor presidential actions present any risk to the implementation of CMMC.
Takeaway 5: FedRAMP Reciprocity
- Question: Will CMMC have reciprocity with FedRAMP?
In a recent letter dated September 8th, 2021, the ITI, NDIA, and PSC, provided industry recommendations on how DoD should proceed with the CMMC.
One of the six points provided was to harmonize CMMC with existing cybersecurity frameworks, such as FedRAMP. They suggested granting reciprocity would avoid duplicate or inconsistent requirements.
Introduced in 2017, the foundational initiative of CMMC is DFARS 252.204-7012. Clause (b)(2)(ii) states “if the contractor intends to use an external cloud service provider then the cloud service provider must meet the requirements established by FedRAMP Moderate and comply with paragraph (c) through (g).”
Paragraph C through G refer to the cybersecurity forensic reporting requirements.
DIBNet identifies the information that organizations must submit to the government in the event there’s a breach.
Most available cloud service providers (CSPs) can’t provide the sources, methods, or tools used to identify the incident. For example, Intrusion Detection System and/or audit log analysis.
This spawned a new generation of cloud offerings such as Microsoft GCC and GCC High.
These solutions are more expensive than previous FedRAMP authorized solutions but they provide US-based support, which is important for ITAR compliance, and the ability to provide cybersecurity incident reporting.
However, most FedRAMP moderate solutions available today aren't CMMC compliant. Compliance using these tools requires the modification of many controls.
Thus the need for reciprocity would serve to end inconsistent and duplicate requirements.
Takeaway 6: Remote Connection Across Levels is Possible
- Question: Can a machine that is at a lower CMMC level, say Level 1, make a remote connection to an enclave that is a high level, say Level 3, if there are ample controls in place that nothing transfers from that higher level enclave?
In theory, this is possible using a web-based view-only client or virtual desktop infrastructure.
This option seems workable but scoping guidance would need to confirm that the controls around this method are enough. The endpoint viewing the CUI may not be within scope as long the technology prevents saving, copying and screenshots.
The Maturity Level 1 controlled environment would also need to prevent photos of the screen.
There isn’t a lot of incentive for Prime contractors to build this type of environment as there's a higher risk of submitting this solution for certification.
Advocates on behalf of the defense industrial base have been lobbying for this type of solution as it would reduce the cost and compliance burden of many small businesses currently working with CUI.
Those businesses would need to change how they interact with CUI and their Prime. But, the potential risk reduction and operational savings would likely drive that behavioral change among many smaller businesses.
Takeaway 7: CCP and CCA is Onsite and Virtual
- Question: Is it true that the CCP and CCA will not be self-studying? Are you required to sit through a training session?
Most of the LTPs are offering virtual instructor-led training but a handful show onsite or self-paced options.
As expected, all training for CCP is pending CMMC-AB approval.
There are currently 47 Licensed Training Providers (LTPs) in the CMMC-AB Marketplace. The accreditation board has left the modality of training up to the LTPs.
An unscientific analysis of their websites at the time of writing indicates...
- 19 out of 47 mentioned CCP training on their website
- 16 out of 19 had upcoming training to register for
- 2 of those 19 offered classroom training
- 3 of those 19 offered self-paced training
- 14 of those 19 offered a virtual instructor-led training
- 4 of those 14 also offered classroom training
Pricing for virtual instructor-led training ranges from $1,995 to $4,935 with an average under $3,225.
The earliest virtual instructor-led training dates published were in October 2021 but most were in November 2021.
Pricing was only shown for 2 of the self-paced training options, ranging from $199 to $2,500.
Terms for the $199 option were not immediately available on the LTP’s website.
During our research, we noticed an update from one that said CCA-1 will be a “fast follower” to CPP. No details were available on an expected launch date but the provider was optimistic that it would be available by the end of the year.
Takeaway 8: CUI Falls Under Definition
- Question: Does the Government mark CUI or do they direct the contractor to mark CUI if the contractor created it?
CUI is information that the government creates or possesses, or that an entity creates or possesses for or on behalf of the government, that a law, regulation, or government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.
CUI doesn’t include classified information.
Notice that the CUI definition doesn’t state the government creates the information. Information created for or on behalf of the government could qualify as CUI.
The NARA CUI Registry currently identifies 20 different categories of CUI. The CUI registry also provides specific examples of information that fall into those categories.
Relating to one of the categories listed in the CUI registry means the information falls under then it falls under the definition of CUI.
Takeaway 9: C3PAO's Don't Hold Evidence
- Question: What CUI would a C3PAO have? Would it be the evidence they collect during an assessment?
The only CUI a C3PAO should have as a result of conducting an assessment will be the final report generated after the engagement.
The C3PAO shouldn’t hold any evidence provided by the OSC.
Rather, the assessors should have access to the evidence through a hashed database to prevent tampering.
Takeaway 10: Moving CUI Still Requires Assessment
- Question: If a company has moved certain processes to a third-party provider’s cloud (FedRAMP), do we have to have internal processes in place still? Seems that should only be necessary if a company moves back to on-prem.
Moving CUI to a FedRAMP Moderate cloud service provider who also adheres to cybersecurity reporting requirements listed in sections C through G of DFARS 7012 will limit the scope of information systems.
The OSC would still undergo an assessment and provide written policies, practices and resourced plans to become certified at a Maturity Level 3.
Takeaway 11: Can Use Services That Aren't FedRAMP Moderate
- Question: If cloud services aren’t FedRAMP moderate, can we still use them if they meet the controls themselves (but don’t spend the $100k for the FedRAMP assessment)?
Yes, as long as the cloud service provider can show compliance with all requirements listed in NIST SP 800-171 and meet the reporting requirements listed in sections C through G of DFARS 7012. There isn't a need for contractors to only use FedRAMP Moderate cloud service providers.
Conclusion
The Accreditation Board did a much better job answering most of the questions during the August Town Hall.
The unanswered questions we’ve discussed here will hopefully be addressed once the DoD rulemaking occurs and these gray areas of CMMC are better defined.
Until then, continue to focus on growing your SSP and shrinking your POA&M.
On September 14, 2021, Dr. Christine Michienzi, the CTO for the deputy assistant secretary of defense, stated “continue on with what you're doing -- don't do any major changes -- but the guidance should be coming out shortly”.
Unanswered questions and a lack of communication by the DoD have led to some to hold off on investing in CMMC preparation.
Now, according to FCW, some of the official answers to these questions and concerns may arrive in the near term. Michienzi continued, “We will be finalizing any changes to CMMC very soon and we will be transmitting that to you".
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




