CMMC Level 2 Compliant Awareness Training Program: AC, MA, MP, PE
If your organization is employing a separation strategy to segment the CUI scope (people, facilities, technology), fewer Individuals within your organization may require this advanced training. Let’s review the requirements for CMMC level 2 awareness training.

Now that we’ve reviewed the training requirements under the CMMC Level 1 practices, let’s discuss those found in Level 2.
It’s important to remember that the CMMC Levels are cumulative. Organizations handling CUI will need to perform these practices in addition to those we already discussed for Level 1.
All employees should take the CMMC Level 1 training but that may not be the case for CMMC Level 2.
If your organization is employing a separation strategy to segment the CUI scope (people, facilities, technology), fewer Individuals within your organization may require this advanced training.
Let’s review the requirements…
AC.L2-3.1.21 - Portable Storage Use
The control statement reads, “Limit use of portable storage on external systems”.
The last two objectives inform you to…
“[b] define the limits on the use of portable storage devices containing CUI on external systems; and [c] limit the use of portable storage devices containing CUI on external systems as defined”.
You can limit the use of portable storage devices on external systems. This happens either through the use of a written policy or technological control. Technological controls can limit the portable storage device to operate only on systems that it can authenticate.
When employing a policy instead of a technological control, you should train all users on the policy. The policy may either completely prohibit the use of such devices or define how you limit their use in external systems.
AC.L2-3.2.1 - Role-Based Risk Awareness
The control statement reads, “Ensure to make users of organizational systems aware of the security risks associated with their activities and of the applicable policies, standards, and procedures related to the security of those systems”.
The last two objectives inform you to…
“[c] make managers, systems administrators, and users of the system aware of the security risks associated with their activities; and [d] make managers, systems administrators, and users of the system aware of the applicable policies, standards, and procedures related to the security of the system”.
Potential artifacts referenced include…
- Security awareness and training policy
- Procedures addressing training implementation
- Training curriculum
- Training materials
- Training records
This practice references NIST SP 800-50. Specifically in regards to, building an information technology security awareness program. In reading SP 800-50, you will find it is a companion publication to NIST SP 800-16. Or, a role- and performance-based model of information technology security training requirements.
NIST SP 800-16 explains that awareness is not the same as training. Awareness presentations focus attention on a topic (e.g. security) and reach a broad audience. Training involves a more active learner and focuses on building knowledge and skills to perform a job.
Section 4.1.1 from NIST SP 800-50 lists topics covered through awareness campaigns, including…

Chapter 4 of DRAFT SP 800-16 Revision 1 illustrates a continuum of learning. It starts with security awareness, moves towards cybersecurity essentials. From there it then heads towards role-based training and education and/or experience.
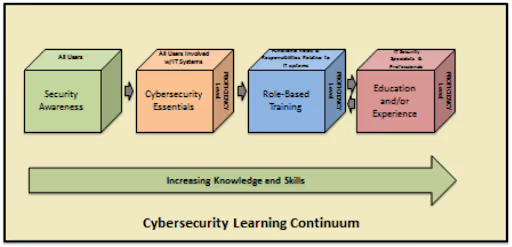
Employees involved with IT Systems should receive security awareness and essential cybersecurity training. Role-based security training becomes focused only on those individuals assigned specific roles.
According to NIST SP 800-16, security awareness applies to all employees and should accomplish the following…
- Build the foundation of cyber security terms and concepts for future role-based training;
- Inform users of the threats and vulnerabilities to their environment;
- Communicate policies and procedures they need to follow and outline disciplinary actions imposed for noncompliance;
- Explain the rules of acceptable use of information and information systems.
If we tailored the NIST SP 800-16 cybersecurity essential concepts and principles to the AT.L2-3.2.1 we would...
- The technical basis of cybersecurity and its terminology
- Common information and system security vulnerabilities
- Common cyber-attack mechanisms and their consequences
- Intrusion, types of intruders, and techniques
- Virtual computing environment vulnerabilities
- Social engineering and its implications for cybersecurity
AC.L2-3.2.2 - Role-Based Training
The control statement reads, “Train personnel to carry out their assigned information security-related duties and responsibilities”.
The last objective informs you to…
“[c] Train personnel adequately to carry out their assigned information security-related duties, roles, and responsibilities”.
Potential artifacts again reference…
- Security awareness and training policy
- Procedures addressing security awareness training implementation
- Security training curriculum
- Security training materials
- Training records
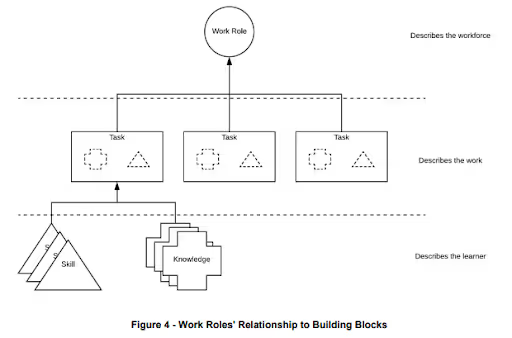
This practice references NIST SP 800-181 which provides guidance on role-based IT training in the workplace. SP 800-181 uses the National Initiative for Cybersecurity Education (NICE). NICE provides a set of building blocks that describe the Tasks, Knowledge and Skills needed to perform cybersecurity work.
The Task is the work, or what the organization needs done to achieve an objective. In order to complete the Task, an individual or group of individuals must apply Knowledge and Skills. The NICE Framework is helpful when describing the Tasks performed, the people who carry them out, and the relevant training.
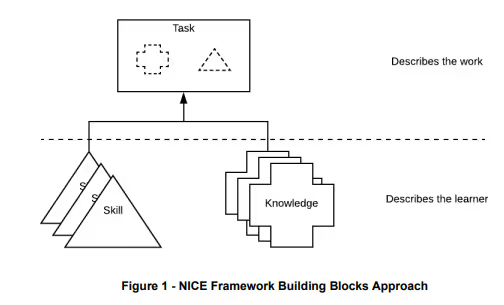
Tasks are statements of the required activities. Task statements do not contain the objectives, which may vary based on need. The associated Knowledge and Skill statements explain the complexity of a Task.
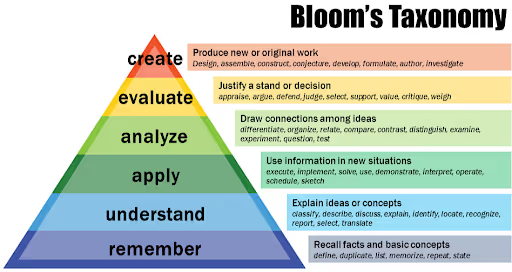
Knowledge statements define either specific or foundational concepts required to complete the Task. A single Task may require many Knowledge statements or many Tasks may draw upon the same Knowledge statements. When writing Knowledge statements, consider the different levels of knowledge and expertise as described in Bloom’s Taxonomy.
Skills are the capacity to perform a simple or complex observable action. They relate a Task or Task to an individual or group of individuals able to perform them. A single Task may require multiple Skill statements or multiple Tasks may draw upon the same Skill statements
Competencies are groups of Task-Knowledge-Skill (TSK) statements. Organizations create competencies to describe an assessment of an individual. This could include…
- Evaluating candidates during the hiring process
- Determining whether an individual has achieved a set of Skills and Knowledge for a credential
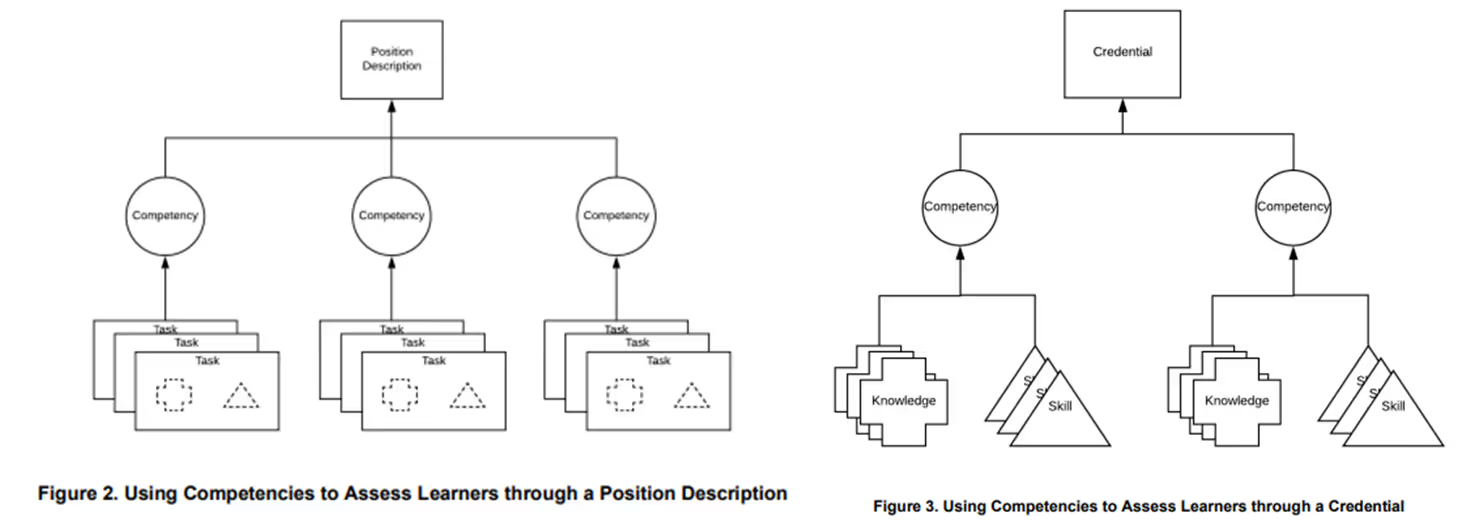
Work Roles are a way to describe a grouping of tasks or work that someone is responsible or accountable for.
Job titles and occupations may coincide with work roles but they are not synonymous. Depending on an organization’s use of job titles, some titles may apply to many work roles and some work roles may apply to more than one title.
The CMMC Level 2 Assessment Guide lists some titles that organizations should provide security-related technical training tailored for their assigned duties. We referenced this list of titles and matched them to work roles from the supplement NICE specialty areas and work roles.

Organizations can use this NICE supplement to identify all associated Knowledge and Skills required to perform the security-related Tasks associated with these work roles. If you’re looking for training to credential individuals in these roles, the NICE Framework Resource Center has a listing of training providers who map their courses to the Knowledge, Skills and Task statements.
AC.L2-3.2.3 - Insider Threat Awareness
The control statement reads, “Provide security awareness training on recognizing and reporting potential indicators of insider threat”.
The last objective informs you to…
“[b] Provide security awareness training on recognizing and reporting potential indicators of insider threat to managers and employees”.
Potential artifacts again reference security awareness and training policy, procedures addressing training implementation, curriculum, and materials.
The discussion of the control suggests that organizations may consider tailoring training for managers to focus on specific changes in behavior while training all employees on more general observations, such as…
- Long-term job dissatisfaction
- Attempts access to information not required for their job
- Unexplained access to money
- Bullying or sexual harassment
- Workplace violence
- Other serious violations
Aside from raising awareness to recognize potential indicators of insider threats, the training should also cover reporting on these potential indicators. This is why the insider threat policy and procedures are also listed as artifacts an assessor may examine.
MA.L2-3.7.3 - Equipment Sanitization
The control statement reads, “Sanitize equipment removed for off-site maintenance of any CUI”.
The only objective informs you to…
“[a] sanitize equipment to be removed from organizational spaces for off-site maintenance of any CUI.”.
Much like MP.L1-3.8.3 that we covered in Level 1, this practice references NIST SP 800-88 guidelines for media sanitization. You should not only train all employees on the system media protection policy but you should also train those individuals with media sanitization responsibilities in order to verify their competencies in conducting the sanitization.
MP.L2-3.8.1 - Media Protection
The control statement reads “Protect (i.e., physically control and securely store) system media containing CUI, both paper and digital”.
The four objectives inform you to:
“[a] physically control paper media containing CUI;
[b] physically control digital media containing CUI;
[c] securely store paper media containing CUI;
[d] securely store digital media containing CUI”.
You should train users with access to CUI stored on media (paper and digital) on the procedures to physically secure it. This includes where and how you store it as well as the procedures to check out and return it.
This practice also references the NIST SP 800-111 guide to storage encryption technologies for end-user devices. This publication informs you to…
- Make users aware of their responsibilities for encrypting CUI on removable media
- Train users to promptly report any loss or theft of media containing CUI
- Train users to not store authenticators in close proximity to the media they protect
MP.L2-3.8.4 - Media Markings
The control statement reads, “Mark media with necessary CUI markings and distribution limitations”.
The two objectives inform you to…
“[a] Mark media containing CUI with applicable CUI markings; and
[b] Mark media containing CUI with distribution limitations”.
You should train employees handling CUI on how to mark digital and non-digital media in accordance with the CUI Marking handbook and CUI Notice 2019-01 published by the National Archives.

MP.L2-3.8.8 - Share Media
The control statement reads, “Prohibit the use of portable storage devices when such devices have no identifiable owner”.
The only objective informs you to…
“[a] Prohibit the use of portable storage devices when such devices have no identifiable owner”.
Potential artifacts referenced include…
- Rules of behavior
- Suggesting that you should make users aware of the system media protection
- System use policies as well as procedures addressing media usage restrictions
This practice comes from control MP-7(b) within NIST SP 800-53. In contrast with 3.8.1, 3.8.8 restricts the use of certain types of media on systems, specifically media with no identifiable owner.
Requiring identifiable owners for portable storage devices reduces risk. It allows organizations to assign responsibility for addressing known vulnerabilities in the devices. Training users on these restrictions is especially important.
PE.L2-3.10.6 - Alternative Work Sites
The control statement reads, “Enforce safeguarding measures for CUI at alternate work sites”.
The first objective informs you to…
“[a] Define safeguarding measures for CUI for alternate work sites”.
This practice references NIST SP 800-46 guide to enterprise telework, remote access, and bring your own device security. Section 5.1.3 highlights the importance of training users on how to detect and handle phishing and social engineering attacks.
This practice also references NIST SP 800-114 user’s guide to telework and bring your own device security. Section 4 recommends making users aware of the risks of using external networks and the procedures for connecting their telework devices to the organization’s network. Section 5.2.3 discusses the importance of using a password-protected session lock and its limitations.
Section 5.4 recommends training teleworkers to avoid using any files coming from unknown sources. Section 5.4.2 suggests training users on what to expect using a personal firewall and the notifications they may receive. Section 5.5 recommends users consider configuring applications for optimal security using a NIST Security Checklist.
Organizations should review these two NIST special publications when drafting security policies for…
- Bringing your own device
- Remote work
- Alternate work sites
They should make sure their employees are aware of these policies and training as well.
CMMC Level 2 Training Summary
As we’ve discussed from NIST SP 800-16, awareness and training exist on a continuum. All users should be security aware. Those who use information technology systems should receive essential cybersecurity training.
Beyond cybersecurity essentials, training should be role-based. It should focus on building knowledge and skills that enable the completion of required tasks. Let’s summarize the training requirements we’ve discussed in terms of where they fall along this continuum.
Security Awareness Training for All Users
AT.L2-3.2.1 - Multiple points to cover for all employees, including…
- Establishing a foundation of cyber security terms and concepts
- Informing users of the threats and vulnerabilities to their environment;
- Communicating policies and procedures they need to follow and disciplinary actions for noncompliance;
- Explain the rules of acceptable use of information and information systems.
AT.L2-3.2.3 - Make users aware of the potential indicators of insider threats and train them on how to report on these potential indicators.
MP.L2-3.8.1 - You should train users with access to CUI stored on paper media on the procedures to physically secure it. This includes where and how you store it as well as the procedures to check out and return it.
MP.L2-3.8.4 - You should train employees handling CUI on how to mark media in accordance with the CUI Marking handbook and CUI Notice 2019-01 published by the National Archives.
PE.L2-3.10.6 - Make users aware of how to detect and handle phishing and social engineering attacks.
Cybersecurity Essentials for All Users of IT Systems
AC.L2-3.1.21 - Train users on the portable storage device policy and the limits of their use on external systems.
AT.L2-3.2.1 - Multiple points to cover for users of IT systems, including:
- The technical basis of cybersecurity and its terminology
- Common information and system security vulnerabilities
- Common cyber attack mechanisms and their consequences
- Intrusion, types of intruders, and techniques
- Virtual computing environment vulnerabilities
- Social engineering and its implications to cybersecurity
MA.L2-3.7.3 - You should train all employees on the system media protection policy
MP.L2-3.8.1 - Multiple points to cover for users of IT systems, including:
- Make users aware of their responsibilities for encrypting CUI on removable media
- Train users to promptly report any loss or theft of media containing CUI
- Train users not to store authenticators in close proximity to the media they protect
MP.L2-3.8.8 - You should train users on these restrictions using portable storage devices that have no identifiable owner.
PE.L2-3.10.6 - Multiple points to cover for users of IT systems, including:
- Making users aware of the risks of using external networks and the procedures for connecting their telework devices to the organization’s network.
- Train users on the procedures for connecting their telework devices to the organization’s network
- Make users aware of the importance of using a password-protected session lock and its limitations.
Role-Based Training
AT.L2-3.2.2 - Match titles referenced in the CMMC Level 2 Assessment Guide to the NICE specialty areas and work roles for guidance on knowledge and skills needed to perform required security tasks.
MA.L2-3.7.3 - You should train individuals with media sanitization responsibilities to verify their competencies conducting sanitization.
Delivering and Documenting Awareness & Training
Whether you’re seeking certification under CMMC Level 1 or Level 2, you should plan on documenting your training ecosystem.
The use of a Learning Management System (LMS) helps you in many ways. More specifically, it helps distribute training, track completion, and store evidence of completion.
We have two solutions that help you with what we’ve covered so far. First, our K2 Akademy LMS for training purposes. Second, K2 Compliance helps you document all aspects of CMMC compliance.
For more information on how this solution can help you prepare for a third-party assessment, contact us today.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




