The Ultimate Guide to CMMC Level 2 Requirements
Even though CMMC isn’t set in stone yet, it’s going to be a requirement listed on contracts with the DoD. With that, let’s take a look at CMMC Level 2 requirements.

As if working in the Defense Industrial Base (DIB) wasn’t stressful enough already, the entire ecosystem is in the midst of a massive shake-up. Of course, what I’m referring to is the Cybersecurity Maturity Model Certification (CMMC).
If this is the first time you’ve heard that phrase, I wouldn’t say you’re “in trouble”...you still have a little bit of time to prepare. That preparation window is starting to close, though.
Maybe you’re already familiar with the acronym and heard that the DoD recently pushed out the massive update, CMMC 2.0.
Or, you knew what level your organization needed to pursue in the first version, saw the changes proposed in the second and don’t know where you land anymore.
If the DoD hasn’t finalized CMMC yet, is it even worth putting energy towards figuring it out right now? That’s a great question and the answer is…yes.
The point I'm trying to make with all of this is that CMMC is something you need to start figuring out now.

Even though CMMC isn’t set in stone yet, it’s going to be a requirement listed on contracts with the DoD. In its first iteration, the DoD planned to place it on its contracts by October 1, 2025.
As it stands now after the introduction of 2.0, the original cutoff date no longer exists. All we know is that final rulemaking could happen between July 2022 and December 2023.
Even without a new date, if the DoD originally gave a 5-year window for its contractors to achieve the certification…it takes a long time to achieve it. Hence why you need to start now.
However, you can’t start your journey towards CMMC without understanding what level you need to achieve.
This is a great place for me to say that Level 3 is now Level 2. If you don’t know what that means, don’t worry…just know that the majority of DIB organizations are going to fall under Level 1 or Level 2.
With that, let’s take a look at CMMC Level 2 requirements.
Overview of CMMC 2.0
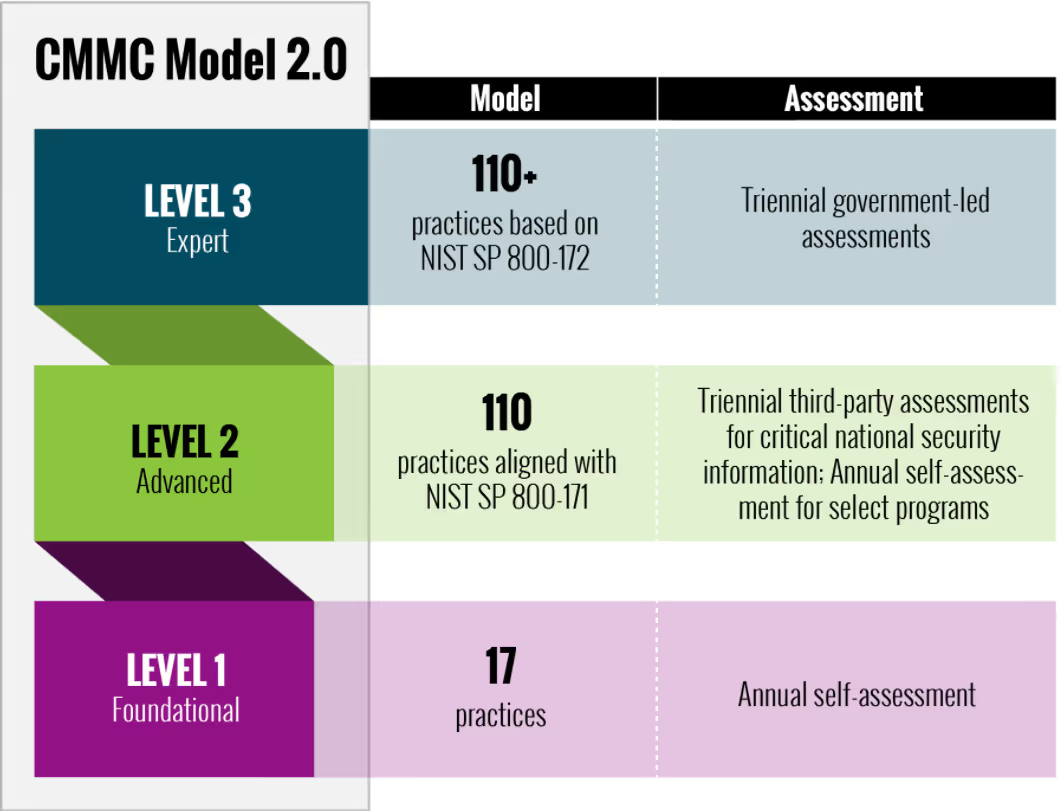
The CMMC 2.0 model categorizes contractors and suppliers into levels. Levels change based on the types of information involved in performing the contracts. There are 3 Levels in CMMC 2.0.
Let’s look at the differences.
Under CMMC 2.0, companies will most likely need to hire a certified third-party assessor organization (C3PAO). C3PAO's certify implementation.
Level 1 is for any contractor or supplier who receives Federal Contract Information (FCI). The basic cybersecurity requirements for Level 1 are currently listed in FAR 52.204-21.
Level 2 requirements are for any contractor or supplier who receives or generates Controlled Unclassified Information (CUI). The advanced requirements come from the 110 practices in NIST SP 800-171.
Level 3 will add a subset of expert requirements from NIST SP 800-172. But, it will only be for large integrators who receive or generate CUI deemed most critical to national security. A team of assessors from the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) will certify the implementation of these expert controls. DoD estimated that as few as 160 companies will fall into this category.
With that, let’s go over CMMC Level 2 requirements.
What to Expect with Level 2
The Level 2 Scoping Guide released in December 2021 is a good starting point.
Identifying the people, facilities and technologies within the scope is a key part of your journey. Doing so ensures that you’re including documentation for all assets that are within scope as you document practices.
There are 110 controls for CMMC Level 2 that come directly from NIST SP 800-171.

However, assessors will evaluate the implementation of these controls using NIST SP 800-171A, That version contains 320 assessment objectives derived from these 110 controls.
Some objectives refer to specific categories of assets within scope, including…
- People
- Facilities
- Equipment
- Processes
Meanwhile, other objectives cover multiple categories.
CMMC Level 2 Practices
The practices listed in CMMC Level 2 come from NIST SP 800-171 Rev 2, which grouped 110 security controls into 14 domains.
- Access Control (AC): 22 practices
- Awareness Training (AT): 3 practices
- Audit and Accountability (AU): 9 practices
- Configuration Management (CM): 9 practices
- Identification and Authentication (IA): 11 practices
- Incident Response (IR): 3 practices
- Maintenance (MA): 6 practices
- Media Protection (MP): 9 practices
- Personnel Security (PS): 2 practices
- Physical Protection (PE): 6 practices
- Risk Assessment (RA): 3 practices
- Security Assessment (CA): 4 practices
- System and Communications Protection (SC): 16 practices
- System and Information Integrity (SI): 7 practices
Each practice has a short name identifier for quick reference. Practices are also identified using the following identification number format (DD.L#-REQ).
- DD: the two-letter abbreviation of the practice domain
- L#: the maturity level that introduces the practice
- REQ: is the NIST SP 800-171 Rev 2 control number
Within each practice are one or more assessment objectives. These get listed alphabetically beginning with (a).

To mark a practice as complete, an OSC must meet all corresponding assessment objectives. The practice statement describes the culmination of all corresponding assessment objectives within the practice.
Who conducts the assessment?
CMMC introduced the concept of using C3PAOs to conduct assessments for organizations seeking certification (OSC) at Level 2.
The CMMC-AB marketplace lists all authorized C3PAOs who’ve passed a Level 2 certification assessment.
C3PAOs employ or contract with certified assessors and certified professionals who are the individuals authorized to conduct the actual assessments. Only certified assessors can lead an assessment team.

CMMC 2.0 also allows self-assessment. This only happens based on how the DoD considers the nature of the CUI involved in a contract. More specifically, if the CUI is less critical to national security than other prioritized contracts.
The best guidance available may be the statements made by Buddy Dees, the Director of the CMMC Program Management Office at the DoD. During the impromptu November 2021 Town Hall, he discussed the department’s thoughts on bifurcating Level 2 assessments based on risk and criticality of CUI.
What is the cost?
After all of this, you’re likely wondering the cost associated with all of this. We have an entire blog post that breaks down CMMC 2.0’s cost.
We updated the government-provided figures with the guidance and came up with the following estimates…
- Level 2: $18,058
- Level 3: $371,786 - $482-874
We also referenced some unverified self-reported assessment quotes discussed on Reddit. These ranged from $30k to $381k for a single (now Level 2) assessment.
We believe the government figures for Level 2 may be in line with the smallest possible scopes. But as scopes increase in size and complexity, so will the cost of an assessment.

How is the assessment conducted?
Below is an outline of the CMMC assessment process at a high level:
- OSC submits documentation to the assessment team
- Kick-off meeting to review scope, schedule and process
- Drafting of Security Assessment Plan - defining the actual steps to conduct an assessment
- Includes proposed tools and review techniques
- Drafting of Rules of Engagement - defines the proposed steps for the assessment
- Includes outside testing, interview conduct and inspection requirements
- Approval of Security Assessment Plan and Rules of Engagement
- Assessment conducted
- Interview Key Personnel
- Observe the processes and security controls in action.
- Conduct a security walk-through
- Test system with tools defined in Security Assessment Plan
- Review tool findings with OSC for interpretation and evaluation to remove any “false positives” that are externally mitigated.
- Drafting of Security Assessment Report
- Review Security Assessment Report with OSC for final remediation
- Deliver certification recommendation with Security Assessment Report
Understanding Assessment Procedures
Assessment procedures consist of an associated set of methods and objects for each assessment objective. To evaluate an objective, an assessor applies a method to an assessment object.
Assessment objects identify items within the scope of the objective, including…
- Specifications - document-based artifacts associated with an information system.
- E.g. Policies, procedures, plans, specifications, designs
- Mechanisms - specific hardware, software, or firmware safeguards employed within an information system.
- Activities - protection-related actions supporting an information system involving people
- E.g. Conducting system backup operations, monitoring network traffic
- Individuals or groups of individuals - people applying the specifications, mechanisms or activities described above.
Assessors will use 2 of 3 potential assessment methods to evaluate each assessment objective…
- Examine: Review of documents such as policies, procedures, plans, diagrams, inventories, configurations, rule-sets, and system logs.
- Interview: Discussions with individuals to facilitate understanding, achieve clarification, or identify the location of evidence.
- Test: Hands-on work with systems and networks to identify vulnerabilities and measure levels of compliance in areas such as configuration or patch management and password policy.
Is CMMC ready for me?
As I mentioned in the introduction, CMMC is still in the process of becoming a rule.
To reiterate, the DoD estimates rulemaking to happen sometime between July 2022 and December 2023. The rulemaking will make CMMC a requirement within Titles 32 and 48 of The Code of Federal Regulations (CFR).
Furthermore, DoD hasn’t outlined how the DoD will roll out CMMC 2.0 requirements into new solicitations. Under the initial guidance, the DoD planned to introduce requirements over a 5-year period.
The governing body of CMMC is currently lobbying DIB organizations. Specifically, it wants volunteers for assessments during this interim period before rulemaking.
The CMMC-AB recently alluded to conversations with the DoD to offer incentives for organizations to seek certifications before rulemaking.
Should I request a pilot assessment?
Your organization might be the perfect fit for a pilot assessment if…
- It already documents its compliance with NIST 800-171 requirements
- You’re confident that the documentation demonstrates appropriate implementation
Passing a pilot assessment may come with an undisclosed incentive.
Failing a pilot assessment has little downside other than the time and resources expended conducting it.

You could consider this allocation of resources as an investment. It would either…
- Identify deficiencies in the implementation of specific controls
- Verify the satisfactory implementation and documentation of controls
Passing a pilot assessment may not yield a tangible certification at this time. But it might remove most obstacles towards achieving one. Thus, placing you at the front of the line to receive one once rulemaking occurs.
Are most organizations compliant?
We have yet to see any published averages of SPRS scores that would indicate the self-assessed adherence to NIST SP 800-171. But, anecdotally we consistently hear that very few organizations have a perfect score.
For example, as we noted in our October 2021 blog, out of 33 C3PAOs assessed by the DIBCAC, 21 didn’t pass their Level 2 assessment.
Considering that C3PAOs have considerable resources and expertise in cybersecurity, with nearly a 66% failure rate among this highly capable and motivated control group, we would expect to see a much worse performance in the larger DIB.
What if I'm still getting ready?
We expect most organizations are still in the process of preparing for an assessment. Our most popular blog and downloaded resource has been the Fool-Proof, Unofficial CMMC 2.0 Compliance Checklist.
If you don't have the internal expertise or bandwidth for an assessment, what should you do? Consider visiting the CMMC-AB marketplace. More specifically, look at Certified Professionals (CP) and Registered Practitioners (RP) to assist.

If you decide not to wait and want to hire an RP now, you can. Just make sure you’re looking closely at their credentials outside of CMMC to ensure they possess the relevant domain knowledge.
Anybody with $500 could become an RP. The designation does not confer accreditation. It simply means they passed a series of quizzes related to the CMMC model and a basic background check.
Building an Assurance Case
An assurance case is a body of evidence (compiled from a variety of activities) organized into an argument that demonstrates the security controls are operating as intended and producing the desired outcome.
The assurance case starts with specifying the organization’s information security needs. This is often accomplished by defining information security policies. Policies should also address the organization’s roles and responsibilities, processes, and documentation requirements.
The processes should be repeatable and documented throughout the implementation of each security control and tailored to meet the assessment objectives.

Since the documentation review is the starting point for the assessment, organizations seeking certification should have a strong assurance case complete with well-documented policies, procedures and processes for each practice.
We’ve worked with some of the top consultants in the space to develop a compliance management solution that’s affordable and granular.
We help organize artifacts by…
- Correlating them to the assessment objectives
- Tracking who created or modified artifacts
- Tying the artifacts to scoped assets
Presenting evidence in this manner establishes a foundation for the assessment team. With it, they can build on it during the assessment process as they obtain more.
Conclusion
Certifying as compliant with CMMC requirements is a significant undertaking.
From documenting policies and procedures to implementing controls, it's incredibly difficult and time-consuming.
Fortunately, there is still plenty of time to improve your readiness posture. That doesn’t mean you should procrastinate. Becoming compliant early will only improve your chances of landing another DoD contract.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




