An In-Depth Look Into CMMC Level 3 Requirements
Since we’ve already provided a breakdown of all 17 CMMC Level 1 controls, it only makes sense that I move onto Level 3. Yes, there are Level 2 controls and requirements. However, Level 2 is more of a temporary designation given to organizations that are in pursuit of Level 3. With that, let’s go over CMMC Level 3 Requirements.

Doing business with the Department of Defense (DoD) might be one of the most lucrative opportunities in the United States.
What I just wrote may sound like it’s a bold statement. Yet, Lockheed Martin made $50.7 billion in revenue from DoD contracts in 2017 alone. The defense contractor also landed a 60-year deal for the F-35 Joint Strike Fighter jet, valued at an estimated $1 trillion back in 2019.
Although there’s a lot of money on the table, it does come at a cost.
When you think of doing business with the government, you might think of movies like 2005’s Lord of War starring Nicholas Cage or 2016’s War Dogs featuring Jonah Hill and Miles Teller. Both of those movies are loosely based on true stories about arms dealers from the 80s to early 00s scheming their way into landing massive deals with the DoD.
If you haven’t seen either of those movies, they’re worth a watch. Lord of War arguably has one of the best title sequences in cinema.
The moral of both of those stories is that crime doesn’t pay and their schemes eventually catch up with the main characters. However, it was extremely easy to conduct business and win contracts with the DoD in both blockbusters.
In War Dogs alone, all the main characters had to do to win a contract with the DoD was login into FedBizOps.gov, find a massive contract and convince government leaders to work with them.
If you’ve seen that movie and didn’t know, FedBizOps.gov, more commonly known as FBO, was an actual website that housed all of the DoD’s contract bids. It still exists today but is now known as sam.gov.
The way that those movies portray landing DoD contracts is accurate based on the years that they take place. Yet, modern-day contractors will tell you that it isn’t nearly as easy as it used to be.
And doing business with the DoD is only going to get more difficult, especially once CMMC 2.0 arrives.
Of course, what I’m referring to is the upcoming rulemaking of the Cybersecurity Maturity Model Certification (CMMC).
If you have any existing contracts with the DoD, you’ve probably heard the acronym “CMMC” whispered throughout your office, fueled by a general sense of fear. Maybe that’s what ultimately led you to this blog post.
The fear throughout your office is justifiable. After all, if your organization fails to meet the criteria provided within CMMC, you can kiss all of your DoD contracts goodbye. In other words, the DoD will soon only be contracting with companies that are compliant with CMMC.
To make matters worse, the way that CMMC categorizes different contractors into levels isn’t as straightforward as some might hope. Don’t get me wrong, the Office of the Undersecretary of Defense for Acquisition and Sustainment provides a fantastic guide that lays out everything about the requirements.
Yet, sometimes it’s easier to understand requirements in chunks of information, written in plain English.
Since we’ve already provided a breakdown of the Level 1 and Level 2 controls, it only makes sense that we move onto Level 3.
With that, let’s go over CMMC Level 3 Requirements.
It All Adds Up
If you’re at this point in your CMMC pursuit, you’ve already achieved what’s enforced for Level 1 and Level 2. After all, each Level builds on top of one another gradually
In other words, you can’t skip straight to Level 3 without first proving that you’ve met every requirement laid out in Levels 1 and 2. It’s almost like grade school.
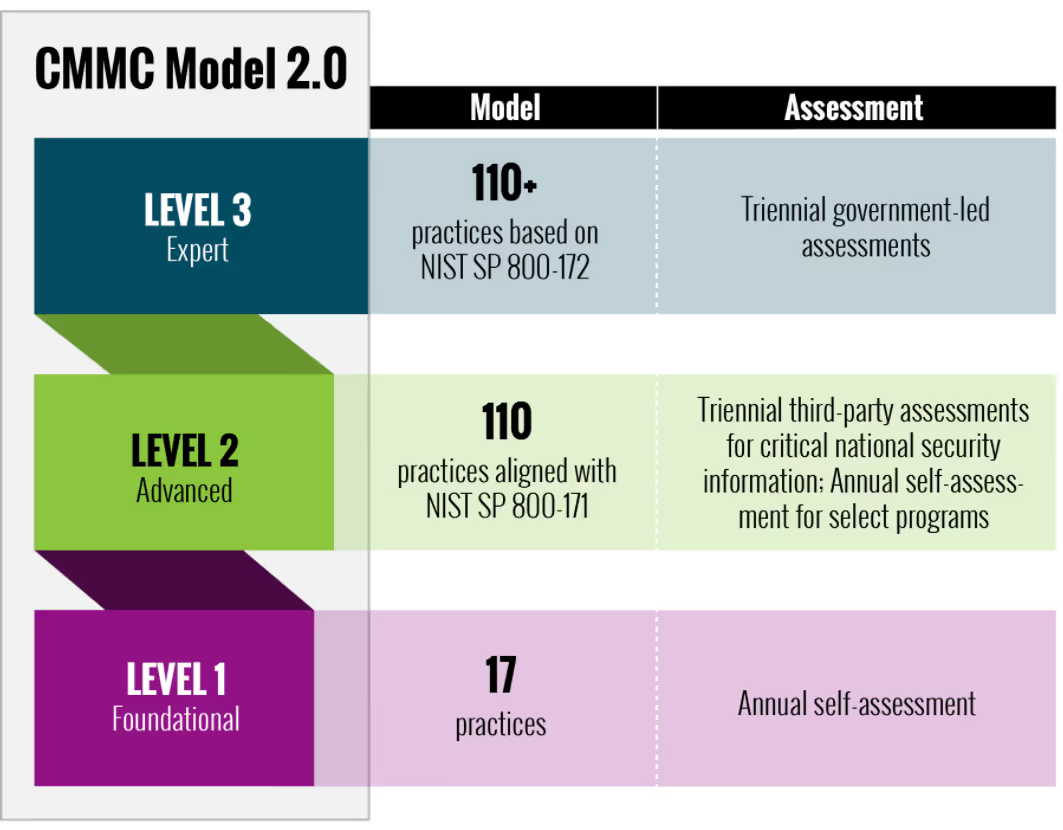
From their simplified description, before an organization can even consider pursuing a Level 3 designation, they need to be able to demonstrate the implementation of practices specified for both Level 1 and Level 2.
What are the practices I’m referring to?
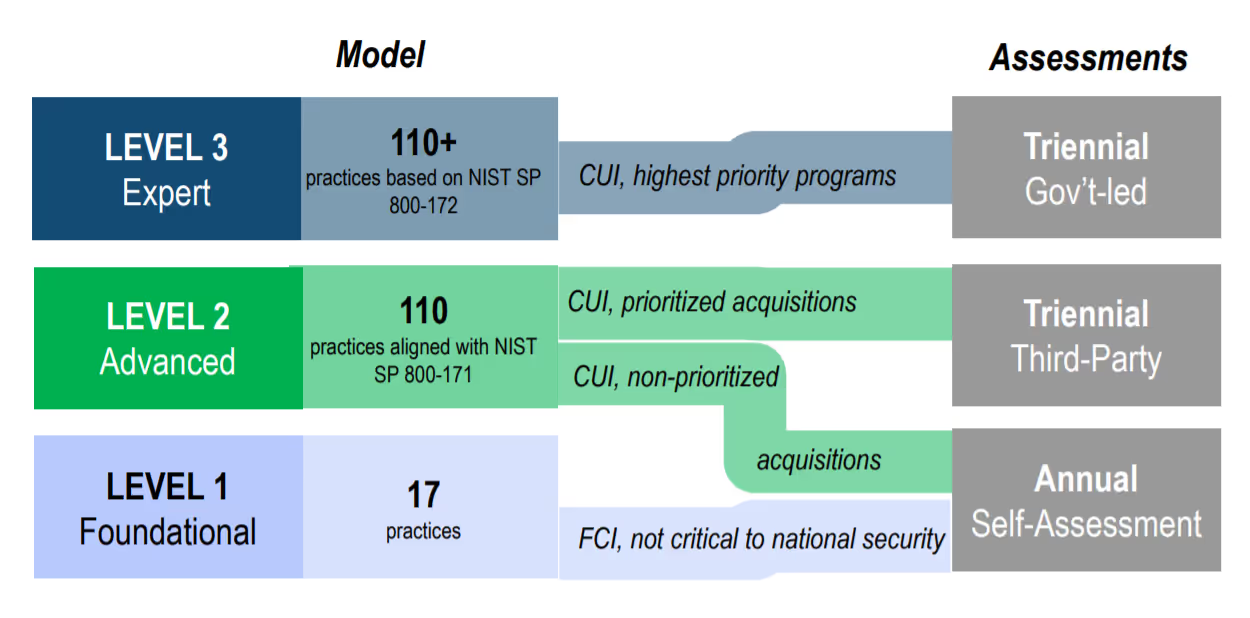
Well, the DoD created another great graphic that helps show how the number of practices compounds as the certification Level increases.
Level 1 is also known as “Foundational” and Level 2 as “Advanced”. To reach…
- Level 1: 17 required practices
- Level 2: 93 additional practices for a total of 110 practices
Under the current CMMC 2.0 guidance, you must pass an assessment conducted by a certified third party audit organization (C3PAO) at Level 2 before you try to pursue the CMMC Level 3 requirements. The Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) will conduct Level 3 assessments and evaluate the implementation of the Level 3 controls.
What are the requirements for Level 3
The most challenging level to achieve will be Level 3, the “Expert” level. This level is for contractors dealing with the CUI in the highest priority programs.
Level 3 builds on the preparatory work of the prior two Levels. In short, its main focus is achieving expert CUI confidentiality and integrity by incorporating NIST SP 800-171 Rev 2 plus other protections.
We don’t yet know what additional practices will add, but DoD has said that they will come from the Enhanced Security Requirements for Protecting CUI called NIST SP 800-172.
Who will need a Level 3 Certification?
Based on the guidance provided by DOD, the majority of contractors will self-assess at Level 1 if they only handle federal contract information (FCI) or have a C3PAO assess their program for Level 2 if they also handle controlled unclassified information (CUI).
If we look back at the original DoD estimates (courtesy COACT), we can align their projections for the number of prime and subcontractors using the consolidated levels of CMMC 2.0…
- Level 1: 59.9% (77,789 companies)
- Level 2: 40.0% (51,860 companies)
- Level 3: 0.1% (160 companies)
According to this preliminary estimate, there would only be around 160 Level 3 contractors total for Level 3. Meanwhile, there will be about 130,000 Level 1 and Level 2 contractors.
If these estimates hold true under CMMC 2.0, you’re most likely going to fall under one of the first two levels considering that was the projection for 99.9% of all DoD contractors.
However, in the abstract of SP 800-172, NIST recommends these enhancements to protect CUI associated with critical programs and high-value assets. This definition may broaden the scope of applicability for Level 3 from the preliminary estimates to a larger population of up to 2,000 contractors and suppliers working on advanced war-fighter solutions.
Required CMMC Level 3 Controls
Alright, perhaps there is a better chance that your organization might fall under CMMC Level 3 than you may have originally thought. If you’re in this camp, your team probably has experience with NIST SP 800-171 and hopefully, you’re already feeling confident about the implementation and documentation of these controls.
As we take a look at the anticipated controls for Level 3, there are two statements that will guide our analysis…
- OUSD A&S: “Level 3 will incorporate a subset of NIST SP 800-172 requirements”
- Ron Ross from NIST: “SP 800-172 is in good shape right now and [NIST] has no plan to update it in 2022”
From these statements, we can conclude that all Level 3 requirements will come from NIST SP 800-172 and NIST doesn’t plan on adding any new controls to that framework this year. That gives us a potential for 35 additional practices and 98 assessment objectives from NIST SP 800-172.
The original CMMC model sourced 15 practices from NIST SP 800-171B, which was still a draft NIST publication at the time. NIST has since finalized SP 800-171B and published it as SP 800-172 with the assessment guide (NIST SP 800-172A) still in draft status. We looked back at the Level 4 and Level 5 practices from 171B in CMMC v1.02 and found those same 15 practices still match the NIST SP 800-172 publication from February 2021.
15 NIST SP 800-172 Controls from CMMC v1.02
Access Control
- 3.1.3e Employ secure information transfer solutions to control information flows between security domains on connected systems.
Awareness & Training
- 3.2.1e Provide awareness training [frequency] focused on recognizing and responding to threats from social engineering, advanced persistent threat actors, breaches, and suspicious behaviors; update the training [frequency] or when there are significant changes to the threat.
- 3.2.2e Include practical exercises in awareness training for [organization-defined roles] that align with current threat scenarios and provide feedback to individuals involved in the training and their supervisors.
Configuration Management
- 3.4.3e Establish and maintain an authoritative source and repository to provide a trusted source and accountability for approved and implemented system components.
Incident Response
- 3.6.1e Establish and maintain a security operations center capability that operates [frequency].
- 3.6.2e Establish and maintain a cyber incident response team that can deploy within [frequency].
Risk Assessment
- 3.11.1e Employ [sources of threat intelligence] as part of a risk assessment to guide and inform the development of organizational systems, security architectures, selection of security solutions, monitoring, threat hunting, and response and recovery activities.
- 3.11.2e Conduct cyber threat hunting activities [select one or more (frequency); (event)] to search for indicators of compromise in [systems] and detect, track, and disrupt threats that evade existing controls.
- 3.11.5e Assess the effectiveness of security solutions [frequency] to address anticipated risk to organizational systems and the organization based on current and accumulated threat intelligence.
- 3.11.7e Develop a plan for managing supply chain risks associated with organizational systems and system components; update the plan [frequency].
Security Assessment
- 3.12.1e Conduct penetration testing [frequency], leveraging automated scanning tools and ad hoc tests using subject matter experts.
System and Communications Protection
- 3.13.4e Employ [ select one or more: (physical isolation techniques); (logical isolation techniques)] in organizational systems and system components.
System and Information Integrity
- 3.14.1e Verify the integrity of [security critical or essential software] using root of trust mechanisms or cryptographic signatures.
- 3.14.2e Monitor organizational systems and system components on an ongoing basis for anomalous or suspicious behavior.
- 3.14.6e Use threat indicator information and effective mitigations obtained from [Assignment: organization-defined external organizations] to guide and inform intrusion detection and threat hunting.
Other Potential Practices
CMMC 2.0 delegated the grouping of practices for Maturity Levels 1 and 2 to the creators of the frameworks. For example, the 17 cybersecurity practices at Level 1 come from the framework created by FAR 52.204-21. DoD removed the delta 20 practices to bring the framework for Level 2 in line with NIST SP 800-171.
So, when we read the current guidance that Level 3 will be a subset of NIST SP 800-172, this would seem to conflict with the strategies taken for Levels 1 and 2. We believe DoD may ultimately adopt all 35 practices from NIST SP 800-172 to be the basis of the framework for Level 3.
Until rulemaking occurs (July 2022 to December 2023), we may not know what practices will be in Level 3. If your long term plan is to achieve Level 3, we would recommend treating NIST SP 800-172 as the complete framework to implement.
Am I Ready for Level 3?
As we mentioned before, a prerequisite for any company that wants to certify at Level 3 with a DIBCAC assessment, will be a certification from a C3PAO at Level 2 first. Having successfully completed this exercise, you’ll be well-positioned to take on Level 3 by methodically documenting the implementation of these expert practices.
If you’re interested in a solution that would help you build an assurance case by documenting evidence for each scoped asset and relevant assessment objective, take a look at our hosted compliance management solution.

Conclusion
If CMMC existed back when David Packouz and Efraim Diveroli were still arms dealers for the DoD, they would’ve been in big trouble.
You’re (hopefully) not in the same scenario as they were in the movie War Dogs so you don’t have any fraudulent/legal issues to worry about. However, you still need to start thinking about how you’re going to receive CMMC accreditation by the end of 2025.
Otherwise, you risk losing the ability to bid on DoD contracts.
Depending on how much CUI you work with daily, there’s a good chance that you fall in CMMC’s Level 3 designation. If that’s the case, at least you now know its requirements.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




