How to Implement Cybersecurity Awareness Training For Your Employees
Let’s go over some of the non-negotiables when it comes to training your employees.

Cybercrime is on the rise. In 2024, Amazon’s Chief Information Security Officer C.J. Moses reported the company seeing 750 million attempts per day. The craziest part? This was up from 100 million attempts from about 6 months prior.
He also attributes the rise to cybercrime to the now widespread use of artificial intelligence (AI). Generative AI provides access to hackers who previously did not have software-development expertise. Now anyone can attempt a malware attack.
It’s not just large companies that need to be on the lookout for cyber threats, but small businesses as well. These evolving threats are a concern for organizations of all sizes and all industries.

One of the best ways to protect your business is by implementing a comprehensive cybersecurity awareness training program for your employees. This will help keep your employees aware of cybersecurity threats. As well as how to properly manage them.
A robust training program can help strengthen your cyber workforce. While improving risk management details within your organization. Let’s go over some of the non-negotiables when it comes to training your employees.
What is Cybersecurity Awareness Training?
Cybersecurity awareness training helps employees recognize and respond to common cyber threats. Such cyber threats could be any of the following:
- Phishing emails.
- Ransomware.
- Viruses.
- Spyware.
- And many other types of malware.
There are many benefits from taking the time to implement a good program. For one, you can reduce human risk by teaching your team to avoid social engineering tactics. A simple yet effective way to strengthen your first line of defense. Having everyone on board when it comes to data privacy and physical security is key. Especially when it comes to a secure business foundation.
Avoid potential revenue loss and legal fees by preventing a data breach from happening in the first place with exemplary training! So what are the basics when putting together a cybersecurity training program?

Cybersecurity awareness content and training must include:
- Recognizing all of the different types of malware.
- How to safely navigate online and verify secure websites.
- Safety when opening emails/avoiding phishing emails.
- Protecting personally identifiable information (PII).
- Using strong password practices.
- Utilizing authentication methods, such as multi-factor authentication (MFA).
- Understanding parallel compliance training responsibilities.
Combining these factors helps to cover the expanding problem that is cybercrime. And it helps better educate your end users. Administrators, employees, and contractors should all take this training. Anyone who has access to your sensitive data should complete training at least once a year.
Why is Security Awareness and Training Essential for Organizations?
Training is essential in today’s day and age as most of our work, and therefore data, is now stored on some type of digital database. Cyberattacks that are successful can expose this information and cost your company millions of dollars. As well as tarnish your professional name and reputation.
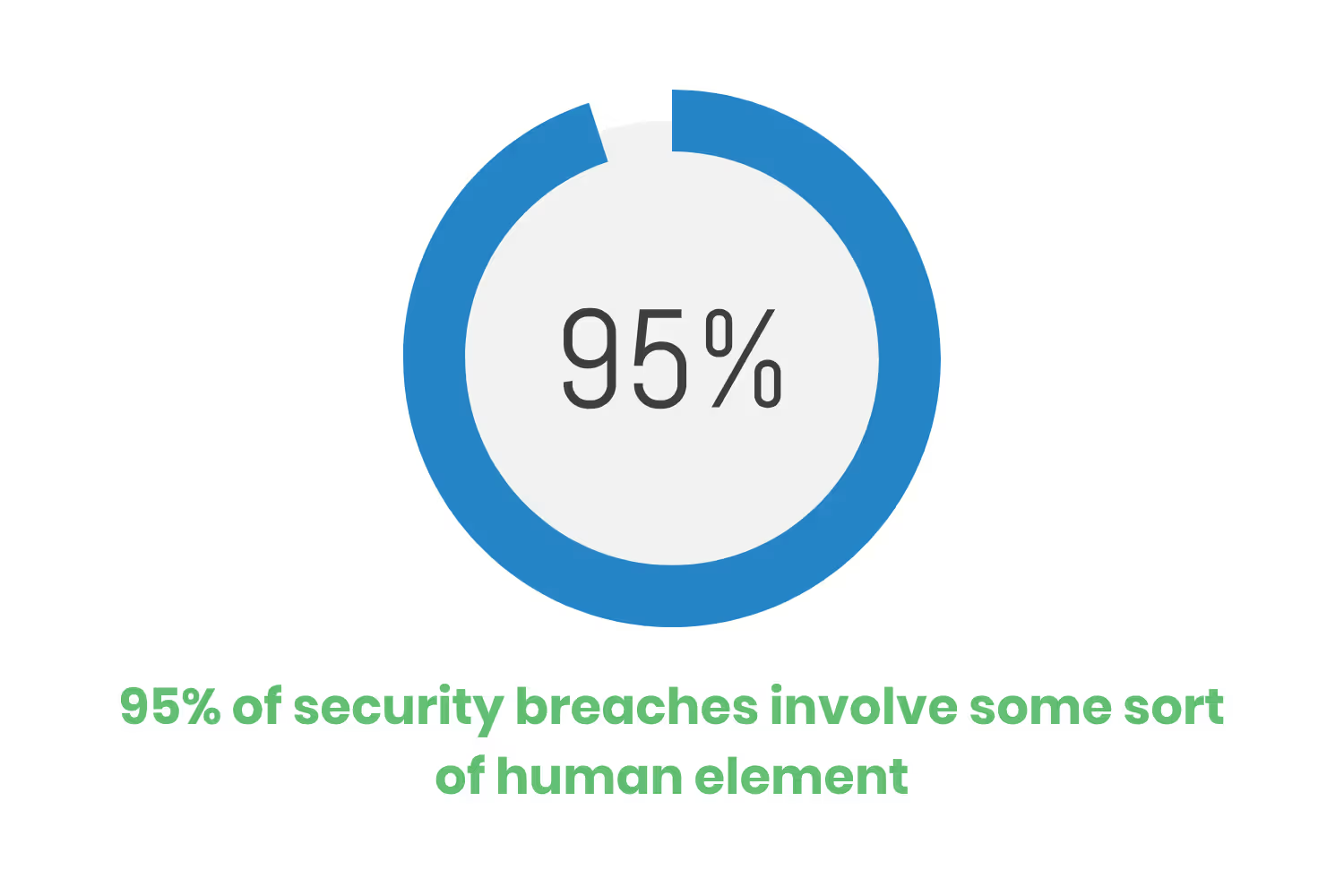
Did you know that 95% of security breaches involve some sort of human element? By training your cyber workforce annually, you can reduce the likelihood of human error. You improve your organization’s baseline security by implementing employee training. As well as help to meet regulatory and compliance requirements. Requirements such as the National Institute of Standards and Technology (NIST), the Health Insurance Portability and Accountability Act (HIPAA), the Gramm-Leach-Bliley Act (GLBA), etc.
Key Components of a Comprehensive Training Program
There are certain key components to keep in mind when putting together your company’s cybersecurity training. The first is an effective training program which includes role-based training.
Everyone needs the basic cybersecurity training experience. But depending on job role, there may be some extra or specialized training involved! Remember that specific job functions may require specific training topics.
You should also always make sure to incorporate periodic updates to address new cybersecurity threats on the rise. The Cybersecurity & Infrastructure Security Agency (CISA) is a great resource to take advantage of when it comes to staying up to date with threat advisories, public alerts, and actionable vulnerability disclosures.

Engage your team by implementing interactive cybersecurity awareness training content into their workload. This makes sure your employees aren’t just mindlessly clicking through training slides without paying attention. Also, having self-paced online training modules for your team to work through at their own pace is key. This way, they can get their training done no matter where they are.
You should also supplement your training with real-time activities, such as simulated phishing emails and incident response drills. You can send these out multiple times a year, keeping your staff alert in between standard training sessions.
How to Choose the Right Training Courses and Providers
To choose the best cybersecurity training vendor, make sure you prioritize an all-in-one platform. These are helpful as they not only offer the training aspect, but also reporting and assessments. Bonus points if they have a phishing simulation component included, too.
You also want to make sure the program you are using supports your state and local government compliance needs. As well as any other further regulatory requirements you must meet in regards to your industry.
A good program will also prioritize updating their content to reflect changes in the latest cybersecurity threats.
Measuring the Effectiveness of Your Program
When tracking your employee’s performance to ensure your training is working, here are some factors to consider:
- Pay attention to progress reports and engagement through your learning platform.
- Have post-training assessments for your team.
- Monitor reductions or influxes in security incidents.
- Conduct incident response drills to evaluate your employees’ real-time readiness to threats.
Remember, you can also implement periodic phishing simulations as a form of evaluating your team. This is real-time feedback on how well your employees recognize and respond to cyber threats in the workplace.
Phishing is also one of the most common cyber threats to date. An improvement, which would be a lower open rate for simulated phishing emails, is a strong indicator that the training is working!

You can also send out post-training surveys to gather feedback directly from the source. Employee feedback can help you better understand which topics they understand. And which need more clarification. Improving your cybersecurity system is a living and breathing process. This insight will make it easier for you to tailor and improve your training!
Another way to track progress is by documenting the speed at which your employees report incidents. And how accurately, too. A fast and appropriate response to a threat is a fantastic sign that the current training modules are working.
Finally, compare cybersecurity audits. Use audits before implementing training and after to find any differences in productivity.
The Importance of a Cybersecurity-Awareness Culture
With the increase in cyberattacks, keeping your employees aware is vital. Generative AI is giving cybercriminals more of an edge. As threats become more serious, cybersecurity awareness training can no longer be a passing thought.
Create a culture within the workplace that fosters responsibility for security. Help employees understand why they shouldn’t share sensitive information. Your risk management strategy depends on delivering a comprehensive curriculum. All-in-one cybersecurity training solutions allow you to fully invest in keeping your employees up-to-date.
From phishing attacks to ransomware, your employees are your first line of defense. Without proper training, they can be your greatest vulnerability. Choosing the right training modules and learning management system (LMS) is the first step to reducing risk.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




![[ANSWERED] Is Zelle HIPAA Compliant?](https://cdn.prod.website-files.com/67e2b8210878abcba6f91ae6/68ad098bff78a96fcbd12339_IsZelleHIPAACompliant_224.avif)