An Explanation of All 15 Required CMMC Level 1 Practices
Protecting information is crucial to the continuity of Department of Defense (DoD) missions. CMMC verifies safeguarding of nonpublic information within the defense industrial base (DIB).

Purpose
Protecting information is crucial to the continuity of Department of Defense (DoD) missions. CMMC verifies safeguarding of nonpublic information within the defense industrial base (DIB). The DIB consists of over 220,000 companies that handle nonpublic information. The DoD cannot scale assessments of all contractors and subcontractors every three years. Their existing capability is best suited for only assessing contractors supporting high-priority programs.
CMMC Program
CMMC verifies cybersecurity standards for companies entrusted with Federal Contract Information (FCI). The standards depend on the type and sensitivity of the relevant information. The CMMC Program provides for three levels. Level 1 starts with basic safeguarding of FCI. Level 2 incorporates broad protection of controlled unclassified information (CUI). Level 3 includes higher-level protection against risk from Advanced Persistent Threats (APTs).
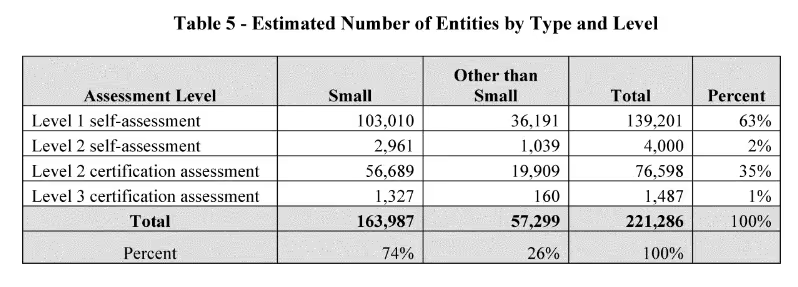
Level 1 allows for self-assessment and attestations for 15 security requirements. Implementation requires meeting all corresponding objectives defined in NIST SP 800–171A. Level 2 verifies the 110 requirements in NIST SP 800–171 R2. Organizations may meet Level 2 via a self-assessment or certification assessment. CMMC Third-Party Assessment Organizations (C3PAOs) conduct certification assessments. Level 3 verifies 24 selected requirements from NIST SP 800-172. Organizations seeking Level 3 certification must first pass a Level 2 certification assessment. The Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) conducts Level 3 assessments.
DoD will enforce CMMC requirements the same way regardless of the organization's size. DoD has declined to delay implementation of CMMC due to national security concerns. Delaying implementation increases the risk for exfiltration of nonpublic information from nonfederal systems. This may result in the loss of technological advantages in DoD's warfighting capabilities.
Phased Implementation
The DoD’s timeline to begin implementing the CMMC requirements remains FY2025. DoD estimates that implementation of CMMC will occur over seven years. DoD has proposed a 4-phase implementation plan over a three-year period.
Phase 1 commences when the 48 CFR part 204 CMMC Acquisition rule takes effect. DoD will include requirements for Level 1 (Self) or Level 2 (Self) for all DoD solicitations. DoD may include requirements for Level 1 (Self) or Level 2 (Self) as a condition to exercise an option period. DoD may also include Level 2 (C3PAO) requirements for applicable DoD contracts.
Phase 2 begins one calendar year after the start date of Phase 1. DoD intends to include requirements for Level 2 (C3PAO) for applicable contracts. DoD may delay requirements for Level 2 (C3PAO) to an option period. DoD may also include requirements for Level 3 (DIBCAC) for applicable contracts.
Phase 3 begins one calendar year after the start date of Phase 2. DoD will expand Level 2 (C3PAO) requirements for all option periods. DoD intends to include requirements for Level 3 (DIBCAC) for all applicable contracts. DoD may delay requirements for CMMC Level 3 (DIBCAC) to an option period.
Phase 4, or full implementation, begins one calendar year after the start date of Phase 3. DoD will include CMMC requirements in all applicable DoD contracts and option periods.
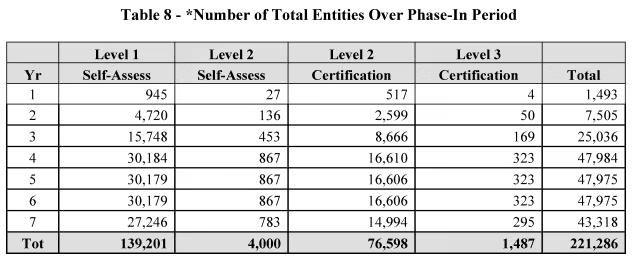
The phase-in plan does not prohibit certification assessments before the CMMC Acquisition rule.
Contracting
The 48 CFR part 204 CMMC Acquisition rule implements CMMC Program requirements. Solicitations for DoD contracts will specify the CMMC Level and assessment type. Program Managers will determine which CMMC Level and assessment type will apply. Factors used to determine which CMMC Level include:
- Criticality of the associated mission capability
- Type of acquisition program or technology
- Threat of loss of the nonpublic information shared or generated in relation to the effort
- Impacts from exploitation of information security deficiencies
- Other relevant policies and factors, including Milestone Decision Authority guidance
DoD intends on requiring compliance with CMMC as a condition of contract award. DoD may include CMMC requirements before the CMMC Acquisition rule becomes effective. Doing so requires bilateral contract modification after negotiations. There are no CMMC requirements for reviewing FCI or CUI solicitation material. FAR part 2.101 defines the term Commercial off-the-shelf (COTS). CMMC requirements do not apply to contracts limited to the delivery of COTS products.
Flowdown
CMMC requirements apply to contractors and subcontractors throughout the supply chain. Prime contractors and subcontractors must follow and flow down CMMC requirements. Applicable CMMC level and assessment type for each subcontract are as follows:
- If a subcontractor handles FCI (and not CUI), they must meet Level 1 (Self).
- If a subcontractor will handle CUI, they must meet Level 2 (Self).
- If a subcontractor handles CUI and the prime has Level 2 (C3PAO) requirements, they must meet Level 2 (C3PAO).
- If a subcontractor handles CUI and the prime has Level 3 requirements, they must meet Level 2 (C3PAO).DoD made a risk-based decision not to flow down Level 3 requirements unless they direct the prime to do so.
Subcontractors are responsible for submitting their own assessment and affirmation in SPRS. SPRS will include an indicator of the currency of the credentials. Contracting Officers and Program Managers need only to review scores and validity periods.
Contractors will only send FCI and CUI to organizations that meet CMMC requirements. The DoD encourages contractors to flow down CUI only when appropriate. Contractors will not have access to subcontractor’s information in SPRS. The DoD expects contractors to share their CMMC status when making teaming arrangements. Prime contractors should communicate with prospective subcontractors to confirm current CMMC status.
Level 1 Requirements
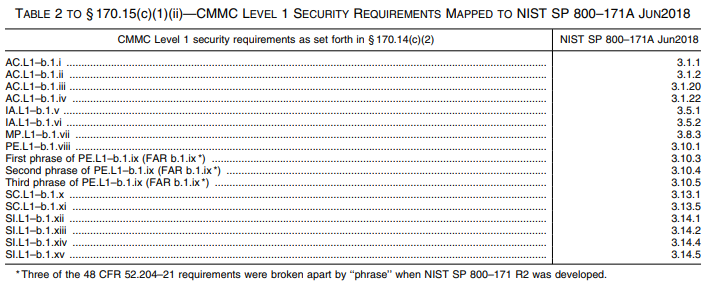
The Federal Acquisition Regulation (FAR) prescribes protections for Federal Contract Information. FAR clause 52.204–21 focuses on ensuring a basic level of cybersecurity hygiene. CMMC Level 1 does not add any new security requirements. The FAR requires compliance with 15 security basic cybersecurity requirements. FAR clause 52.204–21 (b)(1), items (i) through (xv) identify these requirements. These security requirements map to 17 security requirements in NIST SP 800– 171 R2. NIST split one part into 3 parts, while the other 14 align.
Level 1 Scoping
Organizations may achieve Level 1 for an enterprise or an enclave. Organizations must specify the CMMC Assessment Scope before completing an assessment. Organizations should consider the people, technology, facilities, and External Service Providers (ESP). Components processing, storing, or transmitting FCI are within scope. The CMMC Level 1 scoping guide discusses defining the CMMC Assessment Scope.
Any data that meets the definition of FCI, is subject to CMMC Level 1. Section 4.1901 of the FAR defines FCI. FCI is information not intended for public release. It includes information provided by or generated for the Government under a contract. Contracts may include those to develop or deliver a product or service. FCI does not include information provided by the Government to the public. This excludes information on public websites and simple transactional information to process payments.
Information systems processing, storing, or transmitting FCI are in scope for Level 1. They are self-assessed against applicable CMMC security requirements. Out-of-Scope Assets and Specialized Assets are not in scope for Level 1. Out-of-Scope Assets include those not processing, storing, or transmitting FCI. You may be unable to secure Specialized Assets. This includes Internet of Things devices and Industrial Internet of Things devices. It also includes Operational Technology, Restricted Information Systems, and Test Equipment.
Services provided by an ESP are in the organization’s assessment scope. If you're using an ESP to meet any of the CMMC requirements, then it becomes part of the assessment scope. Organizations must verify compliance of the ESP.
Level 1 Implementation
We've written a series of blogs discussing the implementation of Level 1 requirements. Use the links below for guidance on implementing CMMC Level 1 requirements:
- AC.L1-b.1.i - Authorized Access Control
- AC.L1-b.1.ii - Transaction & Function Control
- AC.L1-b.1.iii - External Connections
- AC.L1-b.1.iv - Control Public Information
- IA.L1-b.1.v - Identification
- IA.L1-b.1.vi - Authentication
- MP.L1-b.1.vii - Media Disposal
- PE.L1-b.1.viii - Limit Physical Access
- PE.L1-b.1.ix - Manage Visitors & Physical Access
- SC.L1-b.1.x - Boundary Protection
- SC.L1-b.1.xi - Public-Access System Separation
- SI.L1-b.1.xii - Flaw Remediation
- SI.L1-b.1.xiii - Malicious Code Protection
- SI.L1-b.1.xiv - Update Malicious Code Protection
- SI.L1-b.1.xv - System & File Scanning
Two other resources that may help accelerate your Level 1 efforts include:
Level 1 Self Assessments
Complying with CMMC Level 1 requires your organization to conduct a self-assessment. Your organization must achieve a MET result for all security requirements. Conduct the self-assessment using the assessment objectives defined in the Level 1 Assessment Guide. Scoring is not calculated for CMMC Level 1 since you must meet all requirements. Score self-assessment results as MET or NOT MET in their entirety. The SPRS entry for CMMC Level 1 is a binary selection between Yes and No based on meeting all Level 1 requirements. DoD does not permit Plans of Action & Milestones for CMMC Level 1 requirements.
An organization may complete as many self-assessments as desired. There is no required time-frame between self-assessments and updating CMMC Status in SPRS. Organizations can perform the annual self-assessment themselves or with a third-party. Use of a third party is still considered a self-assessment resulting in a CMMC Status of Final Level 1 (Self). An organization may engage an authorized C3PAO to perform the Level 1 self-assessment. The organization retains all the responsibilities and liabilities of the affirmation.
DoD requires new assessments when there are significant architectural or boundary changes. Examples include expansions of networks or mergers and acquisitions. DoD does not mandate a new assessment for operational changes. This may include adding or subtracting resources.
Meeting CMMC Level 2 satisfies CMMC Level 1 for the same CMMC Assessment Scope.
Level 1 Affirmations
Affirmations state that your organization has implemented Level 1 within the assessment scope. You should also state the organization will maintain the implementation. Annual affirmations verify that changes have not taken your organization out of compliance.
The Level 1 self-assessment results in SPRS will include the following items:
- CMMC Level.
- CMMC Status Date.
- CMMC Assessment Scope.
- All industry CAGE code(s) associated with the system(s) addressed by the CMMC Assessment Scope.
- Compliance result.
DoD requires affirmation of the Level 1 (Self) CMMC Status for all Level 1 self-assessments. An Affirming Official must affirm the continuing compliance of the specified security requirements. The Affirming Official is the senior level representative from within each organization. They are responsible for ensuring compliance with the CMMC Program requirements. They have the authority to affirm the organization’s continuing compliance.
The Affirming Official submits an affirmation attesting to continuing compliance with Level 1. This affirmation occurs at the completion of the assessment and each year thereafter. Each CMMC affirmation should include the following information:
- Name, title, and contact information for the Affirming Official; and
- Affirmation statement attesting that:
- the organization has implemented and
- will maintain implementation
- of all applicable CMMC security requirements to their CMMC Status
- for all information systems within the relevant CMMC Assessment Scope.
Level 1 Artifact Retention
There are no explicit documentation requirements for a CMMC Level 1 self-assessment. You must keep artifacts used in assessment for six years from the status date. Organizations are not required to generate hashes for self-assessment artifacts. Hashing is only required for Level 2 or Level 3 assessments by C3PAOs and DCMA DIBCAC.
Conclusion
CMMC is a critical initiative for safeguarding the sensitive DoD information. The tiered approach validates standards based on the sensitivity of the data. Level 1 serves as the foundational baseline. It forms the essential building block for the more rigorous requirements of Levels 2 and 3. The phased implementation balances national security urgency with scaling compliance across the DIB. The success of CMMC will depend on all stakeholders to uphold these standards.
Emphasize your product's unique features or benefits to differentiate it from competitors
In nec dictum adipiscing pharetra enim etiam scelerisque dolor purus ipsum egestas cursus vulputate arcu egestas ut eu sed mollis consectetur mattis pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus mauris aliquam ornare nisl purus at ipsum nulla accumsan consectetur vestibulum suspendisse aliquam condimentum scelerisque lacinia pellentesque vestibulum condimentum turpis ligula pharetra dictum sapien facilisis sapien at sagittis et cursus congue.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Incorporate statistics or specific numbers to highlight the effectiveness or popularity of your offering
Convallis pellentesque ullamcorper sapien sed tristique fermentum proin amet quam tincidunt feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.

Use time-sensitive language to encourage immediate action, such as "Limited Time Offer
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
- Pharetra curabitur et maecenas in mattis fames consectetur ipsum quis risus.
- Justo urna nisi auctor consequat consectetur dolor lectus blandit.
- Eget egestas volutpat lacinia vestibulum vitae mattis hendrerit.
- Ornare elit odio tellus orci bibendum dictum id sem congue enim amet diam.
Address customer pain points directly by showing how your product solves their problems
Feugiat vitae neque quisque odio ut pellentesque ac mauris eget lectus. Pretium arcu turpis lacus sapien sit at eu sapien duis magna nunc nibh nam non ut nibh ultrices ultrices elementum egestas enim nisl sed cursus pellentesque sit dignissim enim euismod sit et convallis sed pelis viverra quam at nisl sit pharetra enim nisl nec vestibulum posuere in volutpat sed blandit neque risus.
Vel etiam vel amet aenean eget in habitasse nunc duis tellus sem turpis risus aliquam ac volutpat tellus eu faucibus ullamcorper.
Tailor titles to your ideal customer segment using phrases like "Designed for Busy Professionals
Sed pretium id nibh id sit felis vitae volutpat volutpat adipiscing at sodales neque lectus mi phasellus commodo at elit suspendisse ornare faucibus lectus purus viverra in nec aliquet commodo et sed sed nisi tempor mi pellentesque arcu viverra pretium duis enim vulputate dignissim etiam ultrices vitae neque urna proin nibh diam turpis augue lacus.




